What Is Lockdown Mode on iPhone and Mac? How Apple’s Spyware Shield Works – and When to Use It

In an age where our phones harbor nearly everything about us – our photos, private messages, financial data, and even health information – security isn’t just about keeping nosy friends out anymore. It’s about defending against professional spies, hackers, and digital mercenaries who can secretly compromise a device without the user ever tapping a link.
Apple’s Lockdown Mode isn’t your everyday security feature. It was unveiled in 2022 in direct response to a wave of sophisticated attacks using zero-click exploits – hacks that don’t require you to do anything at all.
These attacks have targeted high-profile people around the world, from journalists and activists to politicians and royalty. Apple designed Lockdown Mode to reduce the “attack surface” of its devices, effectively sealing off many of the tools hackers exploit to gain entry.
But Lockdown Mode isn’t for everyone. Enabling it comes with trade-offs – certain apps and features stop working or are heavily restricted, adding friction to the experience. For the average user, that can feel like overkill. So, how exactly does it work? What kind of threats does it protect against? And how do you know if you’re the kind of person who actually needs it?
Let’s break down what Apple’s Lockdown Mode really is, explore the real-world attacks that inspired it, and help you decide when (or whether) to turn it on.
What Lockdown Mode does
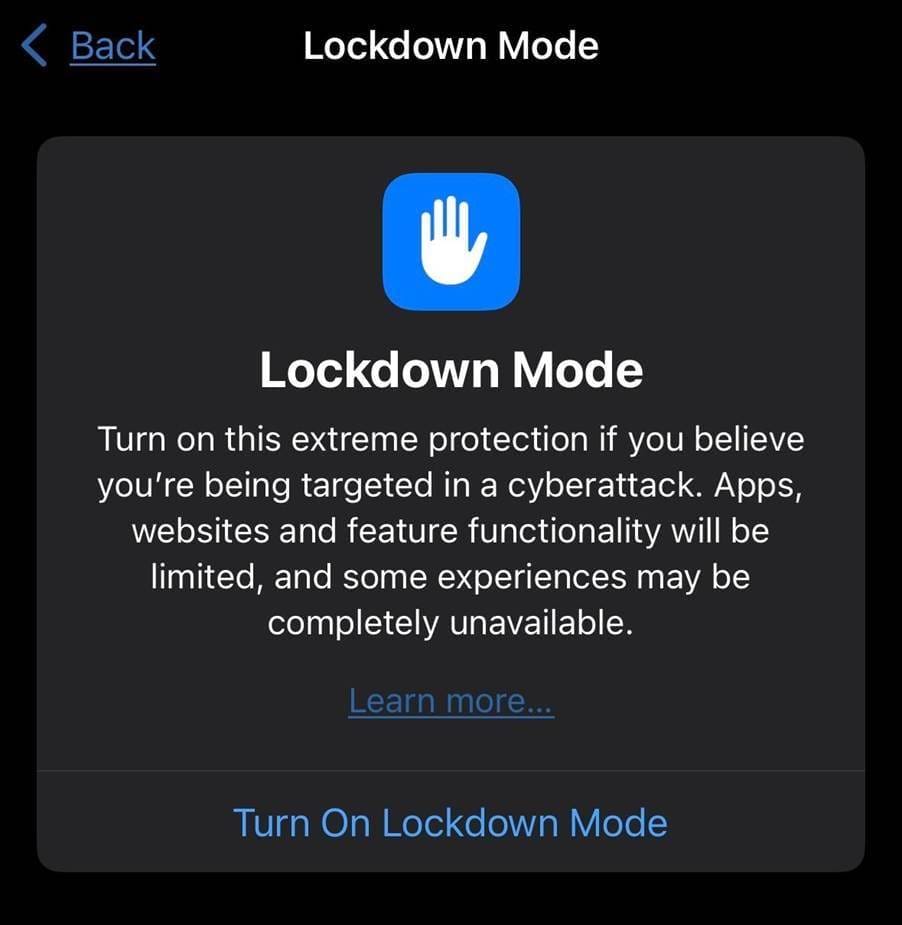
The Lockdown Mode toggle can be found (both on iOS and macOS) at: Settings -> Privacy & Security (scroll to the very bottom) -> Lockdown Mode.
When you enable Lockdown Mode, Apple applies a strict set of rules that block or limit the riskiest paths attackers use to get in:
- Messages: Most attachment types are blocked; link previews and some features are disabled.
- FaceTime & invites: Incoming calls and invitations from people you haven’t previously contacted are blocked.
- Web browsing: Certain complex web technologies (like JIT compilation) are restricted – you can whitelist trusted sites if needed.
- Apple services & sharing: Shared albums, wired connections to computers/accessories, and some device management features are limited.
- Broader coverage: Additional protections arrived with iOS/iPadOS 17, macOS Sonoma, and watchOS 10; turning it on from an iPhone can apply it across your Apple devices.
This “hardened profile” trades convenience for security. In hands-on testing, it’s usable but can be occasionally annoying – which is exactly the point when you’re prioritizing security over comfort.
Why Apple built it: real-world attacks

Lockdown Mode is Apple’s answer to a decade of increasingly sophisticated, state-level or state-sponsored attacks:
- Pegasus (NSO Group): Researchers documented multiple zero-click iMessage chains – including FORCEDENTRY – that compromised iPhones without a tap. They targeted activists and journalists worldwide.
- Operation Triangulation: In 2023, Kaspersky detailed a complex, zero-click iMessage exploit chain used against iOS devices – again, no interaction required.
- Predator (Intellexa): Investigations and threat-intel reporting show Predator spyware remains active against iOS and Android targets, including journalists, with infrastructure resurging in 2024–2025.
These are the key attack classes Lockdown Mode aims to blunt by shutting the usual doors attackers use.
Apple’s threat notifications
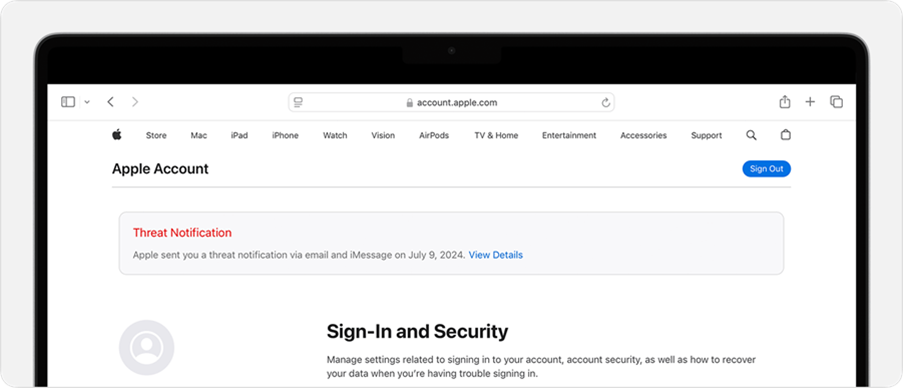
Credit: Apple
If Apple believes your Apple ID has been targeted with mercenary spyware, you may receive a threat notification via email/iMessage and on appleid.apple.com. In April 2024, Apple alerted users in 92 countries. Overall, between 2021 and April of 2025, it had notified users in over 150 countries. If you receive such a notice, treat it seriously and consider enabling Lockdown Mode immediately!
‘Should I use Lockdown Mode?’
- Turn it on if you handle sensitive work that might attract targeted surveillance (investigative reporting, human-rights advocacy, high-stakes legal or political activity, executive roles in sensitive sectors), especially if you’ve received a threat notification or have reason to suspect targeting.
- Probably skip it if you’re an average consumer without signs of targeted interest. Lockdown Mode imposes friction (e.g., blocked attachments, reduced web features) you’re unlikely to want day-to-day, and it’s not necessary against routine cybercrime like phishing, scam calls, or run-of-the-mill malware.
How to enable Lockdown Mode (quick steps)
On your iPhone, iPad, or Mac, go to Settings → Privacy & Security → Lockdown Mode → Turn On (device restarts).
Starting with iOS 17 and watchOS 10, enabling it on iPhone can apply across your devices, including Apple Watch.
Keep your OS fully updated first to get the latest protections.
What Lockdown Mode doesn’t do
Lockdown Mode does not clean infections already on your device, and it won’t catch typical scams, social-engineering, or password reuse. It’s a preventive hardening layer designed specifically for highly targeted attacks. It’s not a general antivirus or fraud shield.
If you’re not high-risk (a practical alternative)
For most people, a better balance is to practice everyday cybersecurity hygiene and run a purpose-built security app. Look for a reputable security tool that offers:
- Malware detection
- Anti-phishing/web protection across browsers and apps
- Malicious link and SMS filtering
- Breach monitoring (alerts if your email/phone appears in data leaks)
- Wi-Fi/network checks and VPN to reduce exposure on public networks
Pair that with good habits – update promptly, use passcodes/biometrics, enable two-factor authentication, use a password manager, and be skeptical of urgent links/attachments.
These steps align with Apple’s guidance that most users are unlikely to face mercenary spyware – the most common risks are scams and credential theft, which can be thwarted by mainstream security suites and good online practices.
Bottom line
Lockdown Mode is like putting your phone in a blast bunker: fewer windows, fewer doors, far less risk – but less sunlight. If you ever have reason to believe you’re a target of spyware operators, turn it on and keep your device fully updated. Otherwise, focus on robust day-to-day protection – don’t visit shady corners of the web, apply updates quickly (especially when Apple flags the addressed issues as high-risk), use strong authentication logging into your accounts, and consider deploying a trusted security tool to watch your back.
You may also want to read:
Five Ways Your iPhone Can Be Hacked – And How to Prevent It
5 Sophisticated Scams Everyone Should Know About – And How to Spot Them
Beyond Free Antivirus: 5 Reasons Smart Consumers Choose Full-Strength Protection for Their Devices
tags
Author
Filip has 17 years of experience in technology journalism. In recent years, he has focused on cybersecurity in his role as a Security Analyst at Bitdefender.
View all postsYou might also like
Bookmarks
