Technical Advisory: Critical Remote Code Execution Vulnerability in Microsoft SharePoint Server (CVE-2025-53770)

Bitdefender analysis confirmed active, widespread exploitation of a critical remote code execution (RCE) vulnerability, CVE-2025-53770, affecting on-premises deployments of Microsoft SharePoint Server. This deserialization flaw, with a CVSSv3.1 score of 9.8, enables unauthenticated attackers to execute arbitrary code across affected networks, leading to full system compromise.
Bitdefender's combined MDR (Managed Detection and Response) investigations and Bitdefender Labs' telemetry research have confirmed the active exploitation of this vulnerability in the wild, with detections observed from numerous countries, including the US, Canada, Austria, Jordan, Mexico, Germany, South Africa, Switzerland, and the Netherlands.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog due to the observed "ToolShell" exploitation campaign.
This vulnerability acts as a bypass to previously issued patches for CVE-2025-49704 and CVE-2025-49706, and immediate action is required for all organizations with on-premises SharePoint Server.
Affected Products
The following on-premises versions of Microsoft SharePoint Server are known to be vulnerable:
- Microsoft SharePoint Server 2016 (fixed in KB5002760)
- Microsoft SharePoint Server 2019 (fixed in KB5002754)
- Microsoft SharePoint Server Subscription Edition (fixed in KB5002768)
For SharePoint Server 2016, closely monitor Microsoft's official channels for the release of the patch. Implement interim mitigations without delay and apply security update KB5002760 immediately.
Note: Microsoft SharePoint Online (Microsoft 365) is NOT impacted by CVE-2025-53770.
Technical Deep Dive
CVE-2025-53770 exploits a weakness in how Microsoft SharePoint Server handles the deserialization of untrusted data. Attackers are leveraging this flaw to gain unauthenticated remote code execution. The "ToolShell" attack chain observed in the wild involves the exfiltration of ASP.NET MachineKeys (specifically ValidationKey and DecryptionKey). Attackers achieve this by deploying malicious ASP.NET web shells that programmatically extract these sensitive cryptographic keys. These stolen keys are then used to craft and sign malicious __VIEWSTATE payloads, which SharePoint servers accept as legitimate, thereby establishing persistent access and enabling the execution of arbitrary commands.
__VIEWSTATE is a hidden field that ASP.NET web applications, like SharePoint, use to maintain the state of a web page across different requests. In simpler terms, when you interact with a web page (e.g., fill out a form, click a button), the page often needs to remember what was there before it was submitted or reloaded. __VIEWSTATE is a mechanism that stores this information (like the values in form fields or the state of certain controls) on the client-side (in the user's browser) and sends it back to the server with each request. This allows the server to reconstruct the page's previous state without having to store all that information on the server itself.
Bitdefender Labs has confirmed multiple attempts to exploit this vulnerability globally. These attacks are typically opportunistic rather than highly targeted, demonstrating a broad scanning and exploitation effort aimed at compromising vulnerable systems wherever they are found. This kind of initial RCE exploitation often serves as a beachhead, with the actual follow-up attack (e.g., ransomware deployment) occurring days or even weeks later.
We typically observe that less than 24 hours pass between the publication of Proof-of-Concept (PoC) code and its integration into automated scanners used to compromise vulnerable systems. This is one of the trending ransomware practices, as detailed in our whitepaper: Ransomware: A Comprehensive Guide to Prevention and Response.
Analysis of Observed Exploitation Payload
Bitdefender has observed the deployment of specific ASP.NET web shell payloads following initial exploitation. This C# code, embedded within an ASP.NET page, is designed to execute when the page is loaded. Its primary function is to programmatically access and extract the MachineKey configuration from the compromised SharePoint server.
<%@ import="" namespace="System.Diagnostics">
<%@ import="" namespace="System.IO">
The code specifically targets a part of SharePoint's internal programming that handles critical security settings, including the "Machine Keys." Once accessed, the code immediately reads out the "ValidationKey" and "DecryptionKey" and outputs these stolen keys directly into the web page's response. This means the attacker, who initiated the request to this malicious page, receives the critical keys back, allowing them to forge future requests and maintain control over the SharePoint server.
By obtaining these MachineKey values, attackers can then craft valid __VIEWSTATE payloads from an external location, effectively bypassing authentication and executing arbitrary commands on the SharePoint server, even after the initial vulnerability might be patched if the keys are not rotated. This highlights why MachineKey rotation is a critical post-exploitation remediation step.
Indicators of Compromise (IoCs)
Organizations should actively hunt for the following indicators, which have been observed by the Bitdefender MDR team:
- Presence of suspicious .aspx files, such as C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx
- POST requests to _layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx with an HTTP Referer header set to _layouts/SignOut.aspx
- Process w3wp.exe spawning cmd.exe with the command line cmd.exe /c powershell.exe -EncodedCommand [...]
- Observed malicious IP addresses
- 162.159.140[.]229
- 172.66.0[.]227
Bitdefender Recommended Actions
While initial compromise is typically done within the first 24 hours after PoC code is available, it can take some time before the next stage of the attack (e.g., ransomware deployment, data exfiltration) is executed. This window of opportunity is a crucial time for defenders to act and prevent further damage.
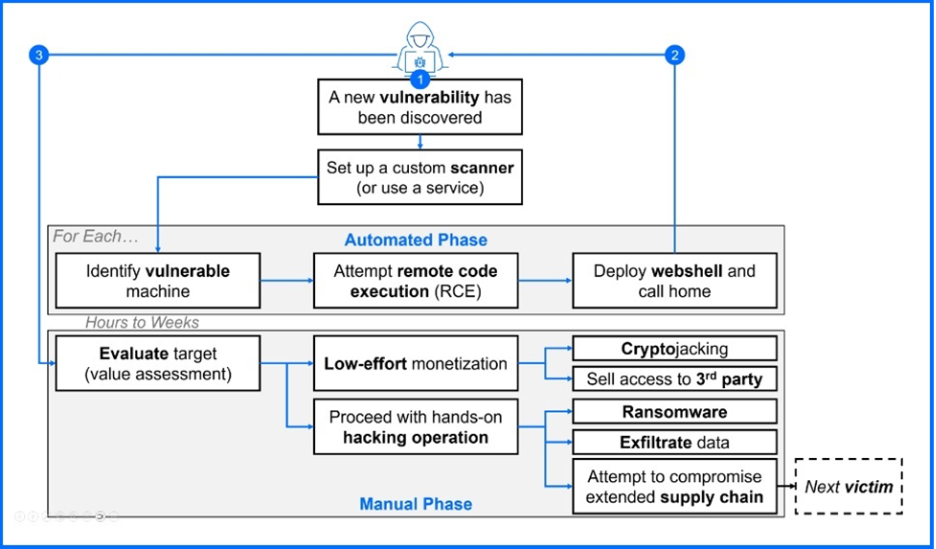
Edge device zero-days, such as this SharePoint vulnerability, provide a "beachhead" for rapid initial access, often weeks before a major follow-up like ransomware; a pattern Bitdefender observed with a record ransomware month linked to a prior exploit. Source: Ransomware: A Comprehensive Guide to Prevention and Response.
Given the critical nature and confirmed active exploitation of CVE-2025-53770, Bitdefender urges all affected organizations to take immediate and decisive action:
1. Prioritize Patching:-
- For SharePoint Server 2019, apply security update KB5002754 immediately.
-
- For SharePoint Server Subscription Edition, apply security update KB5002768 immediately.
-
- For SharePoint Server 2016, closely monitor Microsoft's official channels for the release of the patch. Implement interim mitigations without delay.
-
- Via Central Administration: Navigate to Monitoring > Review job definition, then locate and run the "Machine Key Rotation Job."
-
- Restart IIS: Following key rotation, execute iisreset.exe on all SharePoint servers to ensure the new keys are in effect.
-
- Prevention - GravityZone PHASR has detections for scenarios like this, including the execution of encrypted PowerShell commands.
-
- Protection - Make sure that Advanced Threat Control (ATC) is enabled, as it is the module specifically designed to block similar zero-day attacks based on continuous monitoring of process behavior.
-
- Detection - Pay close attention to the observed process execution chain (w3wp.exe -> cmd -> powershell encodedcommand) and the creation of suspicious .aspx files as strong indicators of compromise.
5. Incident Response Readiness: Assume potential compromise if your internet-facing SharePoint servers were exposed before patches could be applied. Initiate a thorough incident response investigation to identify and eradicate any attacker presence, including a review of logs, user accounts, and system configurations for anomalies. Consider engaging cybersecurity experts if internal resources are limited.
This is a rapidly evolving threat. Bitdefender will continue to monitor the situation and provide updates as more information becomes available.
tags
Author
Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











