Find out How Much of Your Personal Info is Exploited Online

A heavy dose of "cyber-realism" can help you stay safe online in the long run. Your financial, professional, and emotional well-being may very well depend on having a realistic view on the ups and downs of technology.
And the first step is to find out just how much of your personal information can be exposed, trafficked and exploited online.
How Your Personal Information Gets Exposed
“Technology is a complex thing and its various layers have vulnerabilities that bad and smart guys can exploit.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
This simple truth basically states three things:
- technology, data and their complex interactions mirror society, with all the good and the bad
- you cannot expect your online information to be protected by default
- you should take charge of your online privacy and be proactive, as every little action you take in the digital world has consequences.
Scammers and malicious hackers may be harvesting and using your exposed personal information right now.
They can do that freely because it has probably been exposed in multiple places on the Internet and contrary to popular belief you do not have to be rich or famous to be a valuable target - you just need to have private data they can exploit.
“We need to make a distinction between targeted attacks and mass hacks. And when I say mass hacks, I refer to cyber-criminals launching a wave of attacks spanning the entire Internet space.
They take each little website and each IP address on the Internet, and they try to attack it in various ways. They also generate large lists of email addresses or harvest them from private data leaks.
I’m sorry to say, but almost everybody’s email address on this planet has been leaked on the Internet one way or another.“
Alex "Jay" Balan (Director of Security Research, Bitdefender)
To plan and launch these mass hacks, all an attacker needs is a place to start. Most frequently, your email is the first data point they use, but your phone number or social security number work just as well.
With billions of email addresses leaked on the Dark Web, it is fairly easy for them to get a foothold in your (digital) life.
Every additional piece of information helps hackers map out your digital footprint, effectively finding new doors they can use (accounts on social, health or insurance platforms) and the right keys to unlock them (passwords, dates of birth, maiden names, pet names and other details that can answer security questions you set).
Additionally, sharing personal information may leave you exposed to threats like digital identity theft and social media impersonation. But all is not lost. Understanding the risks and increasing your level of awareness can help you better deal with fraud, scams, and cyber-threats.
Besides hackers, who go after your data on purpose, there is another element in our hyper-connected world that keeps feeding the unstoppable flow of exposed personal information.
“A lot of websites get hacked on a daily or weekly basis – big websites, small websites. And, in many cases, they don’t even know they’re hacked. And their databases of user data – that sometimes includes even the contents of the messages exchanged by users – are traded on the Internet, sometimes on the Dark Web but sometimes even in the clear net.”
Alex "Jay" Balan (Director of Security Research, Bitdefender)
Websites that have your personal information often get hacked because of mismanagement, misconfigurations, and human error. It might seem hard to believe but some of the biggest data leaks in history happened because somebody forgot to protect a database with a username and password.
Personal information that can be exposed online |
|||
Online shopping data | Social media data | Personally Identifiable Information | Smartphone data |
Email address Home address Phone number Credit card details | Date of birth Pet names Photos & videos of your home and belongings (including deleted ones) Messages you sent & received Files you shared & received | Social security number Medical history Bank account details Tax & insurance records Real estate ownership records Criminal record Age Ethnicity | Live location data Fingerprints and/or facial features List of contacts Usernames & passwords Apps you run |
With this level of detail, you can see how easy it is for attackers and scammers to craft emails, messages and websites that trick you into acting against your better judgment.
Massive data breaches that expose billions of records on the Internet “instantly create a disturbance in the force”, as Alex "Jay" Balan, Director of Security Research at Bitdefender, candidly puts it.
“The concept of one big cyber-crime event, one big breach in a particular moment in time that can be reused for years to come” is a reality we have seen multiple times and that is bound to happen again. The effects of disproportionately large data leaks do not go away – they just accumulate and get reused for years.
How Your Exposed Data Fits in the Cybercrime Food Chain
“One thing that nobody tells you about data breaches is how important they are for you in the longer run. A data leak will affect you in the next two to three years, not just in the short run when cybercriminals get the information they want from you.
For instance, when you’re a victim of a data breach, you may lose significant finances or access to important information. You may also become subject to defamation or cyberattacks that target additional accounts you own. For example, a leaked email address can become a key piece in phishing schemes that will bomb your email for the next two to three years.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
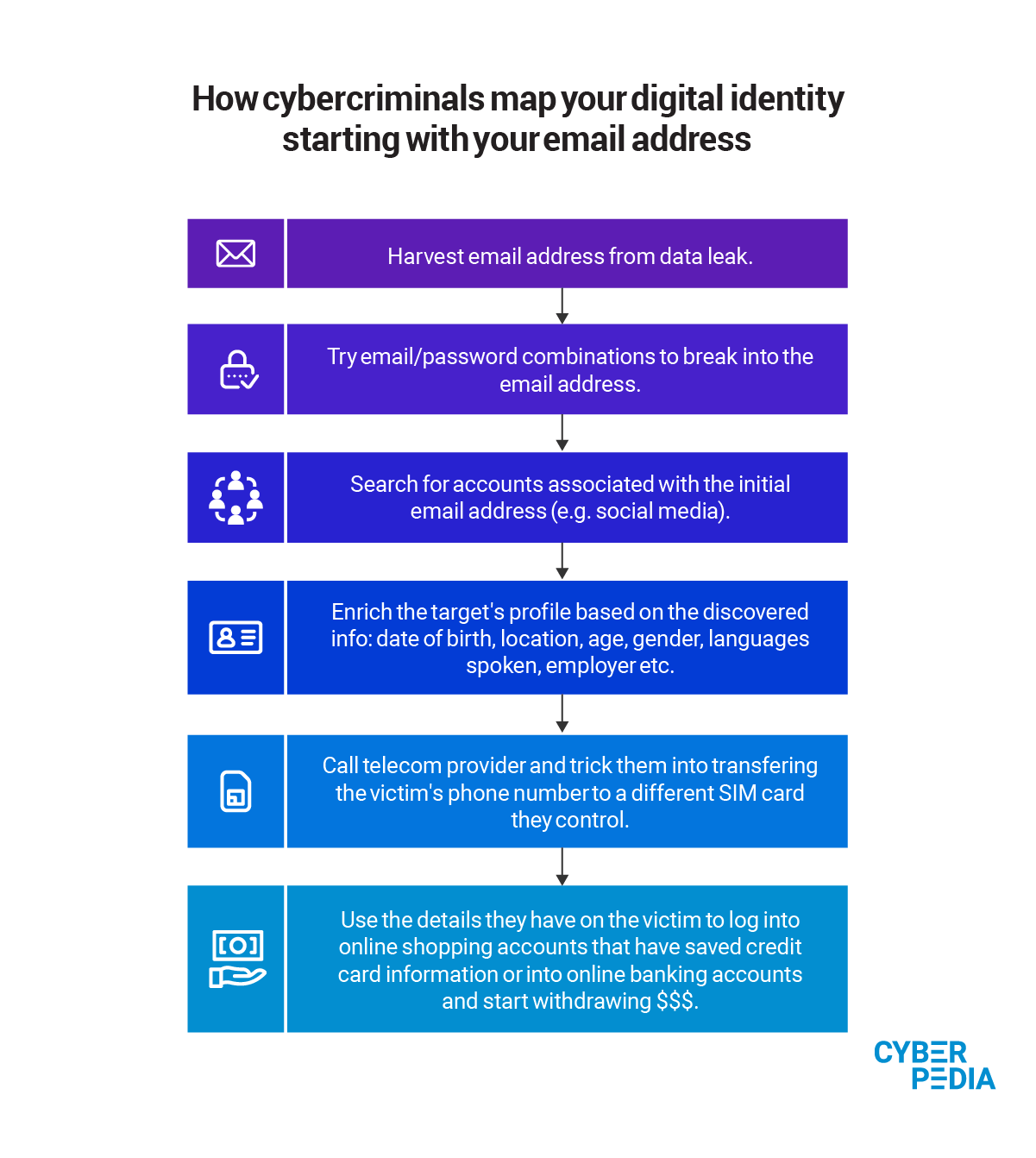
This is one of the reasons why Bitdefender experts recommend you treat any non-perishable data as already compromised. Virtually any piece of information you cannot change (SSN, date of birth or even mother’s maiden name) can be reused forever, if leaked or stolen.
Top tip from our specialists: ask your service providers (bank, cell phone carrier, Internet service provider, insurer) not to use this type of information as an authentication mechanism. If cyber-criminals compromise it once, then it can be reused over and over, because you cannot change it.
Every bit of confidential information that defines who you are, what you do, where you go, what you like and so on can become an income source for cyber-criminals and scammers. Even an empty bank account you don’t use anymore.
“For instance, you have an empty debit card and cybercriminals don’t have any money to steal from it. But they know your account number, your card number, your name on the card, expiration date, CVV and maybe the PIN number.
So what can attackers do with an empty card they know everything about? They will transfer money they’ve obtained through other illegal activities to your card and, at that point, you’re not becoming the subject of money theft but rather the subject of money mulling and money laundering. You can give cybercriminals a helping hand with your information even if they don’t profit from it directly.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
How Many Times Was Your Personal Info Exploited Online?
Mapping your digital footprint is one of the most important things you can do to protect your online privacy and safety. If you want to start now, searching for your name would be a starting point. But it is just scratching the surface. You cannot get the full picture of your digital identity with just one search, no matter how thorough it may be. That is because:
“The bad thing about running queries in a search engine is that it shows up a tiny fraction of what the Internet knows about you. The largest part of the iceberg is underneath, in what we call the Dark Web which is usually inaccessible unless you know where to look for it.
That’s where more powerful digital identity protection solutions come into effect. They aggregate data breaches and personal information leaked and traded by cybercriminals on underground forums.“
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Bitdefender Digital Identity Protection can be the right solution for your needs. This real-time monitoring service keeps you informed and guides you to act when a data breach occurs, so you can limit the damage.
You get an instant alert when your personal info is exposed online or someone else uses your identity, especially on social media. Bitdefender Digital Identity Protection monitors several email addresses, credit cards, accounts and your Social Security Number, and helps you always keep track of your digital footprint.
This way you can regain control over your online identity and personal data.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

