RedLine Stealer Resurfaces in Fresh RIG Exploit Kit Campaign

At the start of the year, Bitdefender noticed a RIG Exploit Kit campaign using CVE-2021-26411 exploits found in Internet Explorer to deliver RedLine Stealer, a low-cost password stealer sold on underground forums.
When executed, RedLine Stealer performs recon against the target system (including username, hardware, browsers installed, anti-virus software) and then exfiltrates data (including passwords, saved credit cards, crypto wallets, VPN logins) to a remote command and control server.
Download the RedLine Stealer whitepaper
Key Findings
- Bitdefender discovered a new RIG Exploit Kit campaign targeting an Internet Explorer vulnerability designed to distribute RedLine Stealer malware.
- If executed, the stealer exfiltrates passwords, cookies and credit card data saved in browsers, as well as crypto wallets, chat logs, VPN login credentials and text from files as per the instructions received from the C2 infrastructure.
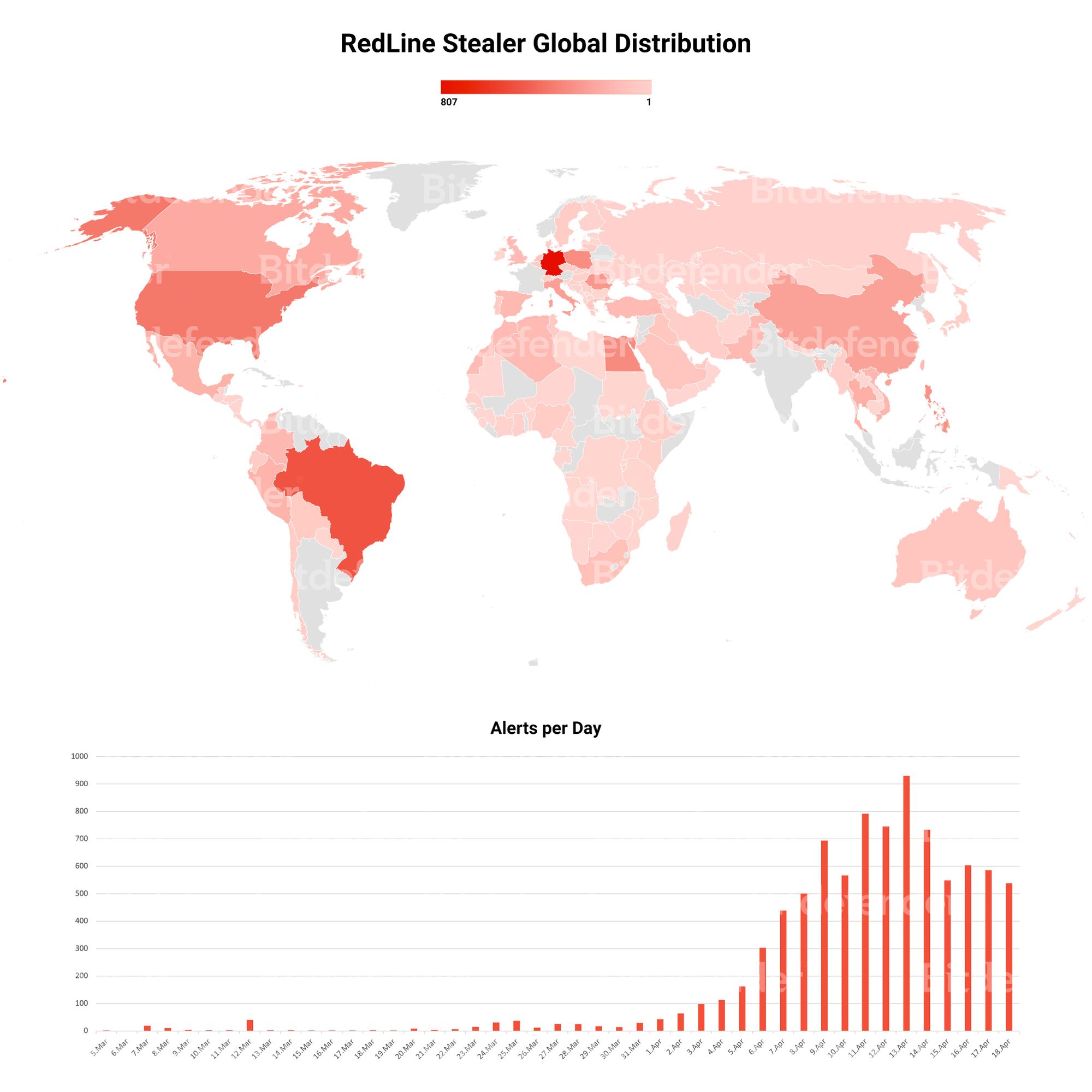
Country distribution and daily activity
Mitigation
- Ensure anti-virus and EDR solutions have exploit detection capabilities.
- Look for the indicators of compromise (IOCs) and keep operating systems and third-party applications up to date, and prioritize security fixes.
tags
Author
Passionate about reverse engineering, Mihai worked on malware analysis and detection techniques in the past. Now he is doing research on exploit detection and mitigation for Windows applications.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks












