Tor Admins Call for Calm after Research Attack Reveals 81 Percent of Users
The Tor project has called for calm despite research that shows 81 percent of users could be identified using Cisco’s NetFlow technology, according to The Register. The study revealed that powerful attackers such as nation-state hackers could reveal Tor users’ identity with a false-positive rate of 6.4 percent, while an autonomous system could reveal about 39 percent of users.
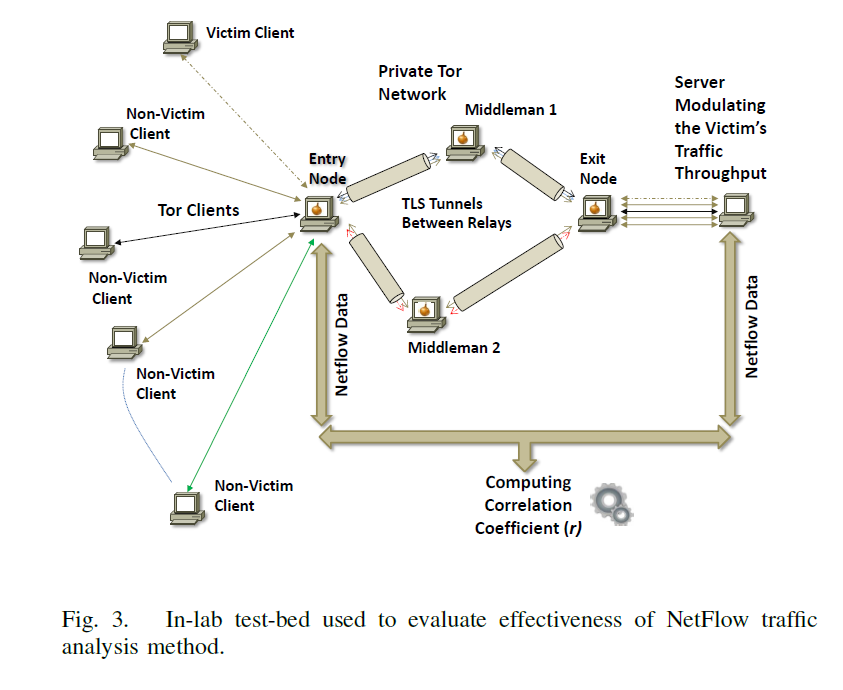
The paper On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records describes how resourceful hackers can mount traffic analysis attacks by observing similar traffic patterns at various points of the network and linking together otherwise unrelated network connections.
“Although the capacity of current networks makes packet-level monitoring at such a scale quite challenging, adversaries could potentially use less accurate but readily available traffic monitoring functionality, such as Cisco’s NetFlow, to mount large-scale traffic analysis attacks,” professor Sambuddho Chakravarty said.
 The attack method can allegedly be put into practice because of the way Tor systems preserve packet interarrival characteristics, such as inter-packet delay. The active traffic analysis method creates and monitors “deliberate perturbances” on server side user traffic, observing output on the client machines through statistical correlations.
The attack method can allegedly be put into practice because of the way Tor systems preserve packet interarrival characteristics, such as inter-packet delay. The active traffic analysis method creates and monitors “deliberate perturbances” on server side user traffic, observing output on the client machines through statistical correlations.
After the research was published, Tor admins told users they have no reason to fear their identity can be revealed when using Tor.
The discussion of false positives is key to this new paper too: Sambuddho’s paper mentions a false positive rate of six percent …,” Tor Project leader Roger Dingledine said in a blog post. “It’s easy to see how at scale, this ‘base rate fallacy’ problem could make the attack effectively useless.”
The research was run on a high-performance research server within the Indraprastha Institute of Information Technology in Delhi University, and it partially worked due to the low-latency design of Tor. Low latency allows human-unnoticeable delays between inputs and outputs, providing real time characteristics. Low latency is important for internet connections using services such as Trading, online gaming and VOIP.
tags
Author
Bianca Stanescu, the fiercest warrior princess in the Bitdefender news palace, is a down-to-earth journalist, who's always on to a cybertrendy story.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








