Heat left by users' fingertips could help hackers crack passwords, researchers claim
Boffins at the University of Glasgow, in Scotland, have developed a system which they claim demonstrates a new type of cybersecurity threat: a "thermal attack."
According to the researchers, the falling price of heat-detecting thermal imaging cameras and advances in machine learning have made it more feasible to guess what passwords a target may have entered on a keyboard, up to a minute after typing them.
Dr Mohamed Khamis led the development of ThermoSecure, a system that used a thermal imagine camera to identify what keys were last touched by an individual, and then guessed passwords and PINs entered on keyboards and ATM keypads.
In a press release announcing their findings, the experts described a possible attack scenario.
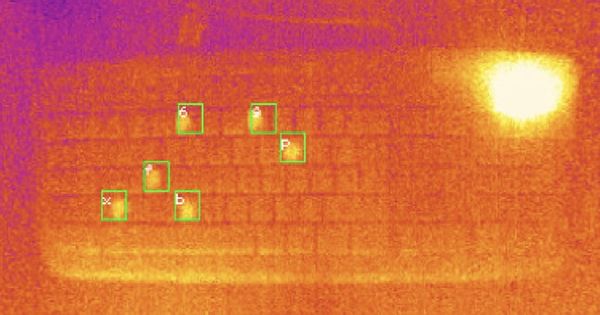
A passerby carrying a thermal camera can take a picture of a keyboard that reveals the heat signature of where fingers have recently made contact.
The brighter an area appears in the thermal image, the more recently it was touched. By measuring the relative intensity of the warmer areas, it is possible to determine the specific letters, numbers or symbols that make up the password and estimate the order in which they were used. From there, attackers can try different combinations to crack users’ passwords.
To put their system to the test, the researchers took 1,500 thermal photos from different angles of recently-used QWERTY keyboards.
The team then "trained an artificial intelligence model to effectively read the images and make informed guesses about the passwords from the heat signature clues using a probabilistic model."
According to the research, 86% of passwords were correctly revealed when thermal images were taken within 20 seconds, 76% when images were taken within 30 seconds of entry, and a still impressive 62% after 60 seconds.
As you can probably imagine, success rates increased as passwords grew shorter. 12-symbol passwords were guessed up to 82% of the time, eight-symbol passwords were guessed on 93% of occasions, and six-symbol passwords were broken in 100% of attempts..
The researchers reported that they could even tackle longer passwords of 16 characters with a 67% success rate within 20 seconds.
And there's bad news for slower "hunt-and-peck" typists who enter their passwords more slowly as they search for the right key to press. According to the researchers, non-touch typists tend to leave their fingers on keys for longer, creating heat signatures that reside for a longer period of time.
Dr Khamis believes it is "very likely" that criminals are developing systems similar to ThermoSecure to steal passwords.
"Access to thermal imaging cameras is more affordable than ever – they can be found for less than £200 – and machine learning is becoming increasingly accessible too," he said.
My advice?
- It's generally better to use longer hard-to-guess passwords or passphrases than shorter passwords - but you knew that already, right?
- If you're nervous, use a backlit keyboard. These produce more heat, making it trickier for thermal readings to be taken accurately.
- In a similar vein, the material used to make your keycaps makes a difference. ABS keycaps (made of Acrylonitrile Butadiene Styrene) retain heat for longer than those made of PBT (Polybutylene Terephthalate).
- Ensure that your accounts are secured by additional methods of authentication (such as 2FA or biometrics) rather than just a single password.
- Keep an eye open for anyone lurking nearby with a thermal imaging camera!
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








