Academics, media, and think tanks warned of North Korean hacking campaign

North Korean state-sponsored hackers are targeting think tanks, research centres, media organisations, and academics in the United States and South Korea to gather intelligence.
The notorious Kimsuky hacking group (also known as Velvet Chollima, Thallium, or Black Banshee) are posing as journalists to steal information in spear-phishing campaigns, according to a warning issued last week.
The warning comes in the form of a joint advisory from multiple agencies within the United States and South Korea governments, detailing the recent hacking campaigns of the Kimsuky group.
Creating email addresses that closely mimic those of real individuals, the North Korean hackers send emails containing malicious documents or links that purport to be a report or news article.
However, the initial approach often will not contain any links or attachments, and are instead intended to gain the trust of the intended victim.
This initial contact may present itself as an attempt to solicit response to an inquiry related to foreign policy, conduct a survey, request an interview, ask the recipient for a resume or to review a document, or offer payment for authoring a research paper.
It is not uncommon for such approaches to flatter their intended victim by mentioning that they have been recommended as an expert source by another academic or researcher.
If posing as a journalist or broadcaster, the Kimsuky hacker may frame their message as questions regarding current events such as whether it is likely North Korea will rejoin talks with the United States, or what they may believe are North Korea's plans regarding missile testing.
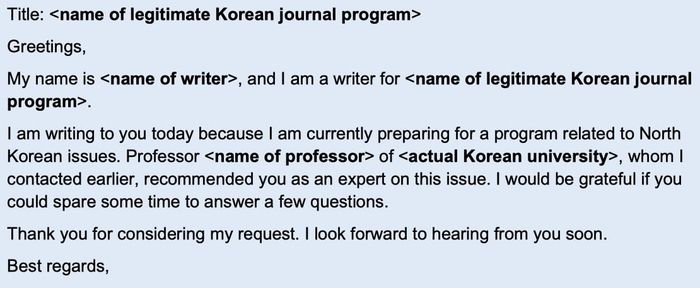
If the intended target responds to the email, they will then receive a follow-up communication which contains a dangerous link or an attached boobytrapped Word document.
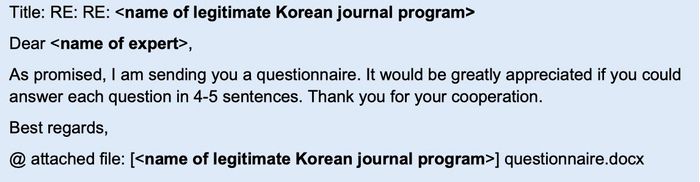
Another attack detailed in the advisory sees the North Korean hackers pose as South Korean academics, requesting responses to a survey about North Korea's nuclear plans, or requesting an email interview.
In these cases the follow-up email may contain not just the survey questionnaire, but also a payment form which contains malicious content.
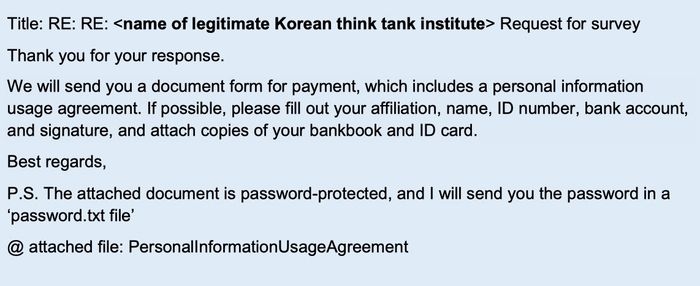
In this example the malicious file has been password-protected in an attempt to avoid detection by anti-malware software at the email gateway.
There are plenty more social engineering tactics that have been used by the hackers to respond to their emails, as described in the advisory which recommends that those at risk of attack familiarise themselves with the techniques being used by the hackers.
In addition, users are advised to refrain from enabling macros in suspicious documents, and to be wary of opening documents on cloud hosting services unless the legitimacy of the message has been verified.
The United States Department of Justice's Rewards for Justice Program offers an award of up to US $5 million for information about illegal North Korean activities in cyberspace.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








