Unpacking RDStealer: An Exfiltration Malware Targeting RDP Workloads

In June 2023, Bitdefender Labs published a research paper about espionage operation in East Asia. This operation was ongoing since at least the beginning of 2022, showing a high level of sophistication typically associated with state-sponsored groups. Despite trying various methods, we have been unable to attribute these attacks to a specific threat actor, but the target aligns with the interest of China-based threat actors.
The most interesting discovery in this research is a new custom malware we named RDStealer. This server-side implant is monitoring incoming Remote Desktop Protocol (RDP) connections with client drive mapping enabled. Connecting RDP clients are infected with Logutil backdoor (another custom malware), and sensitive data (such as credentials or private keys) is exfiltrated.
DLL sideloading (read our tech explainer) has emerged as one of the most prevalent stealth techniques in recent years. However, the level of disguise observed in this campaign surpasses anything witnessed thus far. Multiple DLL libraries are chained together as part of the sideloading attack, chosen locations blend well into the system, and the sideloading process itself is initiated through the clever utilization of the WMI subsystem.
Both RDStealer and Logutil malware samples are written in the Go programming language. Go is known for its strong cross-platform support, allowing malware authors to create malicious code that can run on multiple operating systems. Indeed, when analyzing domains connected to this attack, we have observed references to Linux, but also ESXi, indicating that the Logutil backdoor is a multiplatform tool.
Although the concept of this attack method has been known in theory for quite some time, this marks the first concrete instance of malware utilizing it. Considering the potential for this method to be adapted for targeting various end-user computing (EUC) platforms with minimal or no modifications, coupled with the increased adoption of these solutions during the COVID-19 pandemic, we share this research to increase public awareness.
This is the summarized version of the RedClouds espionage operation research. The full research paper Exposing RDStealer - Deep Dive into a Targeted Cyber-Attack Against East-Asia Infrastructure contains additional details, including the full list of indicators of compromise and additional technical insights.
Anatomy of an attack
Based on our research, which involved analyzing passive DNS information, VirusTotal samples, and discovered artifacts, we have determined that this threat actor has been active since at least 2020. Initially, the threat actor relied on readily available tools like AsyncRat or Cobalt Strike. However, starting in late 2021 or early 2022, they shifted towards using custom-developed malware. This transition to custom malware aligns with a growing trend observed among other threat actors, who have adjusted their evasion tactics as detection tools (like EDR or XDR) have become more widespread.
The primary purpose of the attack seemed to be the theft of credentials and data exfiltration. As part of an evasion tactic, threat actors used folders that are less suspected to contain malware and are often excluded from scanning by security solutions:
- %WinDir%\System32\
- %WinDir%\System32\wbem\
- %WinDir%\security\database\
- %PROGRAM_FILES%\f-secure\psb\diagnostics
- %PROGRAM_FILES_x86%\dell\commandupdate\
- %PROGRAM_FILES%\dell\md storage software\md configuration utility\
The locations %PROGRAM_FILES% and %PROGRAM_FILES_x86% are most likely picked to mimic the legitimate software. While it is not possible to determine if the folder name was chosen randomly, we have confirmed after reviewing the hardware inventory that infected machines were indeed manufactured by Dell.
Malware was also discovered in an additional location %WinDir%\security\database, the folder that serves as a storage space for security databases in Windows. Microsoft has provided guidance on excluding specific files within this location from being scanned by endpoint security products. Threat actors may have anticipated that some administrators or security solutions would opt to exclude the entire folder instead of implementing more precise and granular exclusions.
RDStealer
The first custom malware that we analyzed specializes in data gathering, including capturing of clipboard content and keylogging capabilities. But what we found more interesting is the capability to monitor incoming RDP connections and compromise a remote machine if client drive mapping is enabled.
Client Drive Mapping (CDM) is one of the virtual channels implemented as part of the RDP protocol that allows the transfer of data between the RDP client and RDP server (other examples of virtual channels include clipboard or audio redirection).
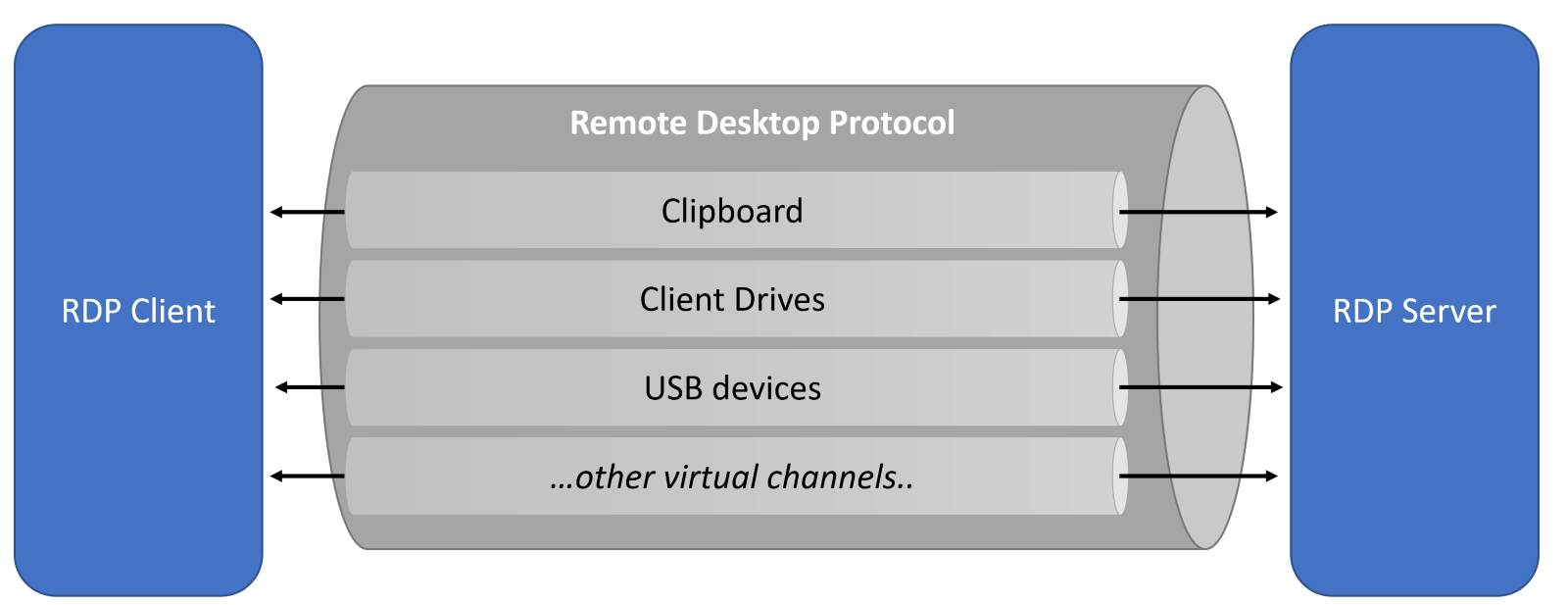 CDM specifically is responsible for displaying the local drives of the client machine (the computer from which the RDP session is initiated) within the remote desktop session.
CDM specifically is responsible for displaying the local drives of the client machine (the computer from which the RDP session is initiated) within the remote desktop session.
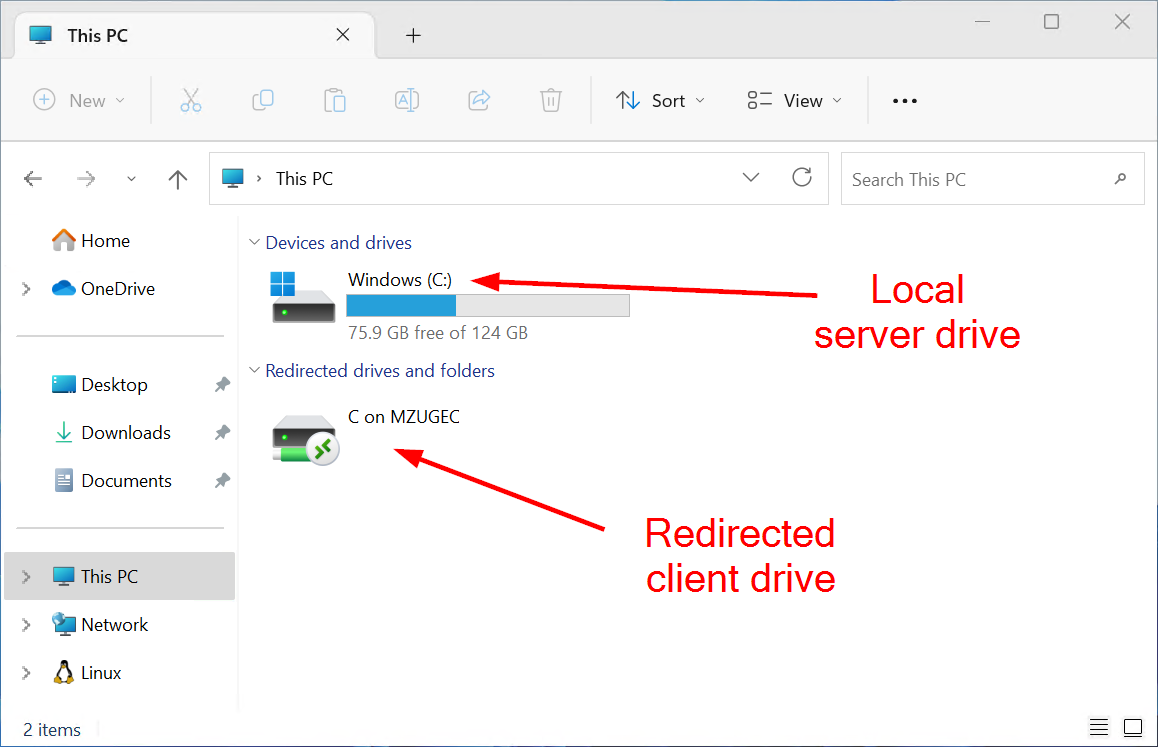
This feature enables users to access and transfer files between their local machine and the remote server or desktop they are connected to via RDP (but also other protocols). This feature is often used by administrators to transfer files between remote server and their admin workstation.
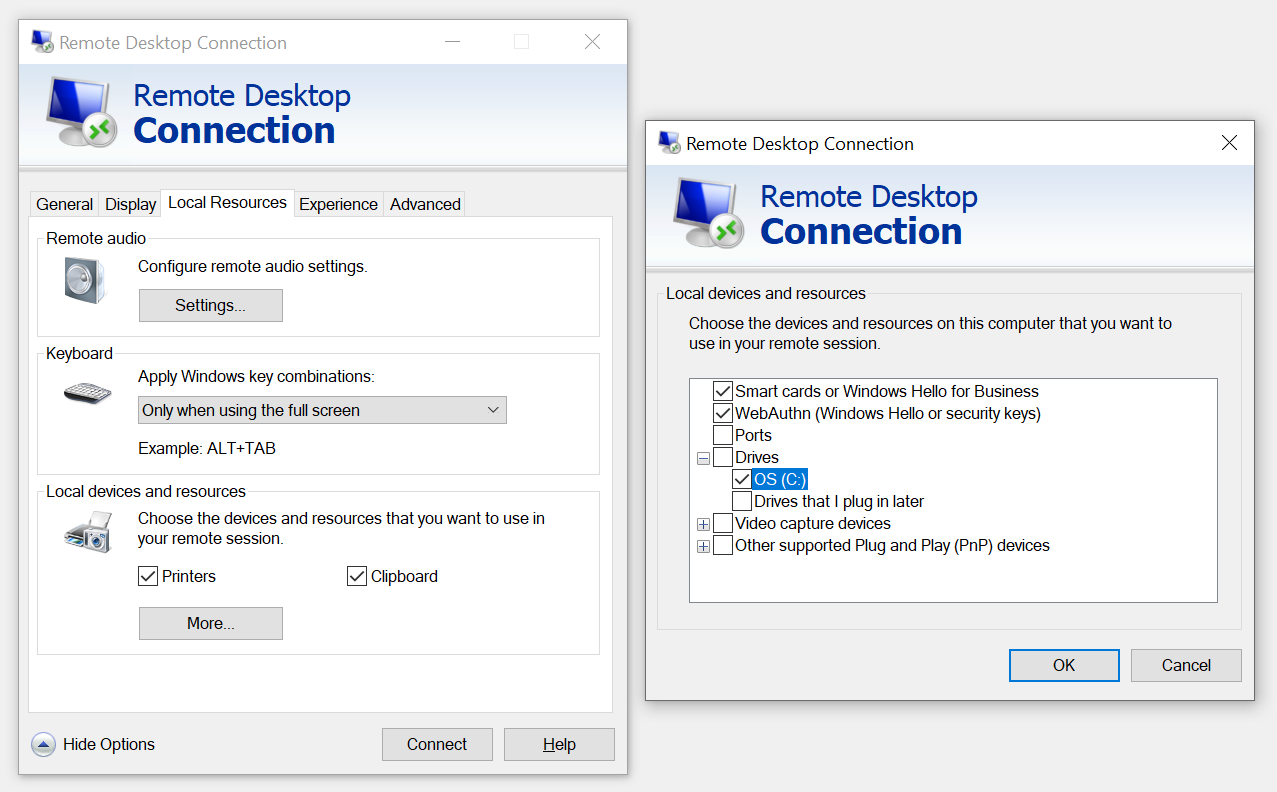
But client drive mapping is also frequently used by regular end users in end-user computing (EUC) environments for both virtual desktops and application virtualization. In the EUC use case, end users typically do not have direct control over this feature, as it is centrally configured through policies. Both the server and the client end must have this feature enabled in order to work, but it is common practice that clients (decentralized) have it permanently enabled, while the configuration is managed solely on the server end (centralized). This is a good reminder that zero trust does not involve only networks or authentication but is a more encompassing principle - servers located on an internal network are not necessarily more trustworthy than clients connecting remotely.
Although we lack specific details regarding the infection vector and cannot definitively confirm whether the compromised system was utilized for administrative access or regular user interactions, it is important to note that this technique is applicable in both scenarios. Furthermore, it is worth mentioning that other solutions employing client drive mapping may also be susceptible to vulnerabilities if they employ tsclient for host-to-client redirection. Even solutions that are not relying on tsclient but use their own implementation of virtual channels can be targeted with minimum code modifications.
On compromised machines, RDStealer was located at “%PROGRAM_FILES%\dell\md storage software\md configuration utility\modular disk service daemon.exe”. RDStealer is written in Go, and after analyzing the code, we have identified the following packages (code libraries):
|
package name |
description |
|
cli |
Implements the capture of the clipboard content by using windows API such as OpenClipboard and GetClipboardData; |
|
key |
Implements keystroke capture alongside with window name; |
|
main |
Acts as the orchestrator and uses the package modules to perform persistence setup and start the routine for data collection if certain conditions are met; |
|
modules |
Implements different functions used for collecting and staging the data for further exfiltration; |
|
utils |
Implements encryption and decryption functions, file attribute manipulation, and log function |
After launch, the main function starts by collecting clipboard data and keystrokes from the host. This data is periodically saved into the log file C:\users\public\log.log in the form of encrypted strings. After data collection is initiated, RDStealer creates an infinite loop that calls the diskMounted function. diskMounted function is periodically checking the availability of tsclient connection and one of the C, D, E, F, G or H drives. These shares are automatically created when CDM is enabled, representing individual disks of the connected RDP client.
When one of these shares is detected, the following functions are triggered:
- main.notifyMaster - Notify command & control (C2) server that a client is connected.
- Main.DiskEnum - Start exfiltrating data from the connected RDP client.
- main.writePersist - Deploy Logutil backdoor to the connected RDP client.
notifyMaster - C2 communication
The notifyMaster function makes a GET request to another server on the same network that was designated as a proxy to communicate with the C2 infrastructure of threat actors.
The URL address where this request is send is in the format https://<Proxy Address>:7443/pdr.php?name=<Host>&ip=<Host IP Address>. This alert serves as an indication to threat actors that one of the compromised RDP hosts have made an attempt to exfiltrate data from a connected client, and data is now prepared for manual collection by the malicious actors.
DiskEnum - Data exfiltration
DiskEnum function is looking for any valuable information on the connected RDP client for data exfiltration.
The first target is a few very specific folders, including mRemoteNG (multi-protocol remote connections manager), KeePass (password manager), and history from Google Chrome. If any of these folders is found, a ZIP archive is created and saved on the RDP host machine as C:\Users\Public\Documents\<ID><timestamp>.dat.
|
Location |
ID |
|
\\tsclient\c\users\<user>\appdata\roaming\mremoteng |
mre |
|
\\tsclient\c\users\<user>\appdata\roaming\keepass |
keyp |
|
\\tsclient\c\users\<user>\appdata\local\\Google\Chrome\User Data\Default\History |
chro |
This highlights the fact that threat actors actively seek credentials and saved connections to other systems. This trend is also visible in the next step, where a client is scanned for files with specific extensions in the following locations: %AppData%, %LocalAppData%, Desktop, Documents, Downloads, %ProgramFiles% and %ProgramFiles(x86)%.
|
Files |
ID |
Details |
|
.kdb, .kdbx |
kdb |
KeePass password database |
|
confCons.xml |
mre |
mRemoteNG connections |
|
.rdg |
rdg |
Remote Desktop Connection Manager connections |
|
id_rsa |
idrsa |
SSH private keys |
|
.xsh |
xsh |
NetSarang Xshell connections |
|
.tlp, .bscp |
tlp |
Bitvise SSH Client |
|
.mxtsessions |
mxts |
MobaXterm connections |
Any located files are stored in a ZIP archive on the RDP host in the following location: C:\Users\Public\Documents\<ID><timestamp>.dat.
After data exfiltration from the remote C drive is completed, RDStealer starts looking at the drive letters D, E, F, G, and H, but with a slightly different approach. Instead of scanning specific locations, it will start scanning all folders with the following exceptions:
|
windows, datareporting, libreoffice, node_modules, all user, default user, user data, .rust, download, desktop, document, assembly, .git, microsoft, winsxs, en-us, mui, .net, dotnet, visual, cache, recycle, systemapp, driverstore, catroot, package, prefetch, installer, fonts, cursors |
As this recursive scan can take a lot of time, there is a mechanism that limits the execution to be done only once a week. The file users\public\Videos\vcache.dat is modified when data exfiltration is completed, and the last modified data is compared with the current time to determine if it’s time for another sweep of the system. It’s worth noting that this functionality does not work as intended - the location of this file is invalid, as it’s defined as a string without any drive letter or a share location. It is most likely that threat actors intended to create this file on the compromised RDP client (\\tsclient\c location).
WritePersist - Downstream compromise
WritePersist function is responsible for deploying Logutil backdoor to the connected RDP client.
First, it obtains a list of users from \\tsclient\c\users. For each user’s home directory, the following malicious files are transferred from the compromised RDP host to the connected RDP client.
|
Source |
Destination |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
For the first 4 files, we haven’t found any samples on the affected machines, but it seems that t1lnk.dat.lnk was the persistence trigger at the startup.
The last two files are the loader and the Logutil backdoor. As we will describe in the next section, Logutil is initiated by the clever utilization of the WMI subsystem, which is also hinted at by the name of function that is deploying this backdoor - WorkWithWbem (WMI is Microsoft’s implementation of WBEM).
Logutil
Written in the Go language, Logutil backdoor implements the usual capabilities that are necessary for maintaining the foothold into the victim’s network, capabilities such as file download/upload and command execution.
What makes Logutil particularly intriguing is the extent to which it leverages DLL sideloading techniques for evading detection, coupled with its utilization of WMI as a trigger for activation.
We have observed a combination of passive (standalone binaries) and active (pre-installed binaries) DLL sideloading exploits (to understand the difference, read our DLL sideloading explainer). Some samples relied on the more traditional DLL sideloading - a scheduled task launching an executable that loads a library. But the more interesting variant was abusing the Windows Management Instrumentation service (Winmgmt), leading to the execution of malicious binary bithostw.dll (=Logutil).
To achieve this goal, threat actors placed a malicious loader named ncobjapi.dll into a folder %WinDir%\System32\wbem. This malicious implant is mimicking the legitimate ncobjapi.dll library, which is residing in the parent %WinDir%\System32 folder, by exporting the same functions and proxying the calls to the original library. Because \wbem subfolder is checked for the existence of this library before System32, the malicious library is loaded first.
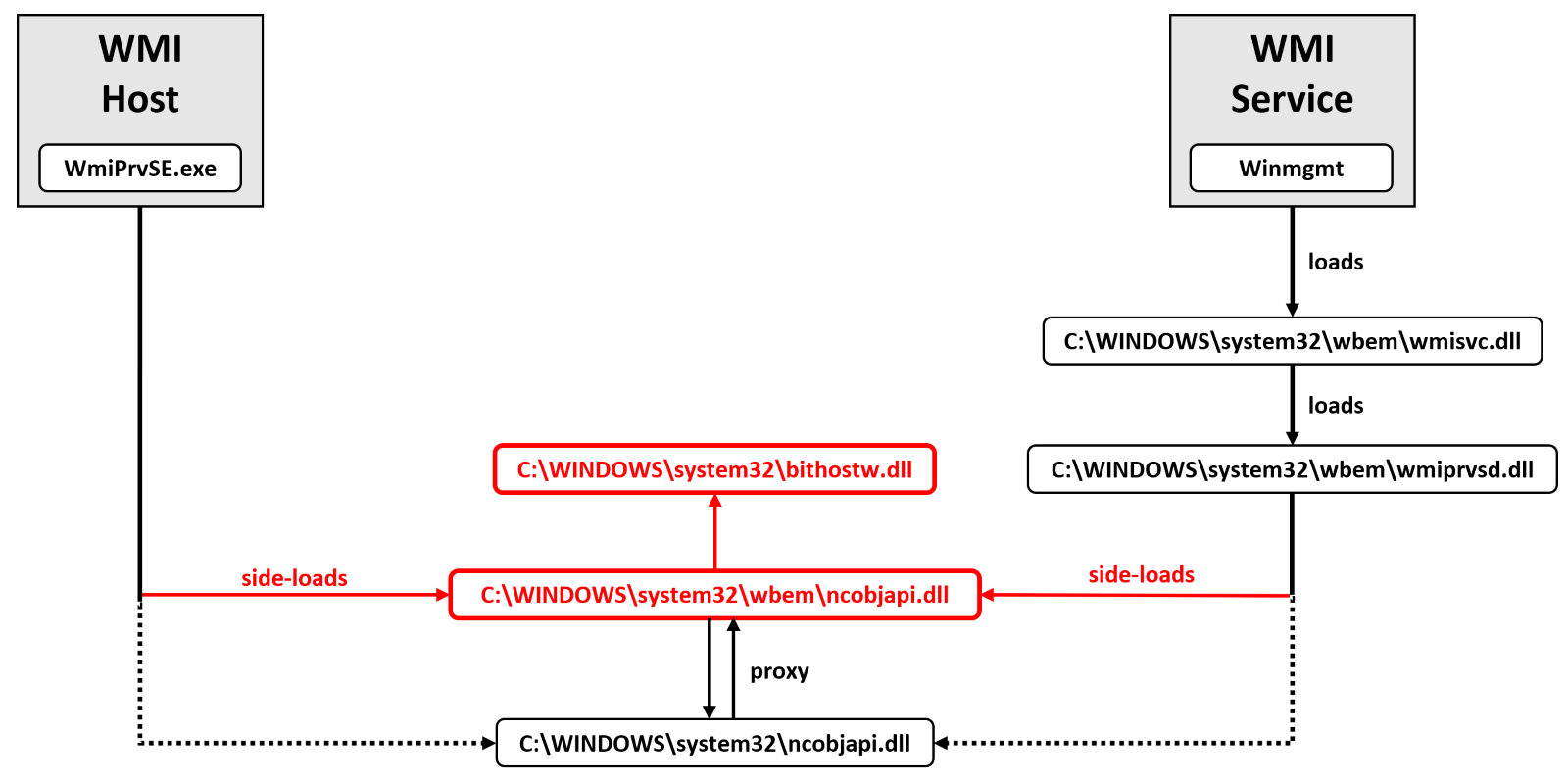
This implant is highly effective to establish persistence on the system. It can be triggered by either WMI service (automatically started with multiple recovery actions), or through WMI host process. There are often multiple instances of WMI host process (WmiPrvSE.exe) running, and there are multiple ways this process is started (including by DCOM interface for remote WMI calls). The ncobjapi.dll library has been previously weaponized by other threat actors like Lazarus group or RadRat operators, but in this case it’s just part of the sideloading chain. The real payload (loaded by ncobjapi.dll loader) is bithostw.dll (Logutil).
Logutil can communicate with the C2 infrastructure directly, or through another proxy server on the same network. The commands from the C2 are obtained by making an HTTP GET request to https://<host:port>/info address. Below is the list of commands that can be retrieved from the remote C2 server:
|
command |
parameter |
details |
|
set |
<key>=<val> |
Sets the value (<val>) of the environment variable (<key>) on the compromised system |
|
load |
<Dll path> or <base64 fileless string> |
The DLL library to be reflectively loaded into the memory |
|
c |
<command> |
Executes command with output capture (using a shell object) |
|
s |
<command> |
Executes command without output capture (using a shell object) |
|
t |
<filepath1>,<filepath2> |
Touch operation that sets the file attributes of the first file to the second one |
|
d1 |
<hex encoded data> |
Calls CryptUnprotectData on the received data, and send the result back |
|
fu |
|
Uploads the file in chunks to the victim |
|
fd |
|
Downloads the file in chunks from the victim |
|
idle |
|
Sleeps for an increasing amount of time; The sleep time starts with 6 seconds and increases each time with a random integer value between 0 and 4; |
|
sleep |
<int> |
Sleeps for indicated number of seconds |
|
ls |
<path> |
Performs a recursive listing of the folder |
|
info |
|
Sends information about the implant like the amount of time it is running and the assigned id |
|
exit |
|
Exit |
Conclusion
Cybercriminals continually innovate and explore novel methods to enhance the reliability and stealthiness of their malicious activities. This attack serves as a testament to the increasing sophistication of modern cyberattacks, but also underscores the fact that threat actors can leverage their newfound sophistication to exploit older, widely adopted technologies. The full research paper, published by Bitdefender Labs, contains additional details, including the full list of indicators of compromise and additional technical insights.
The best protection against modern attacks remains the defense-in-depth architecture. This approach involves employing multiple layers of overlapping security measures that are designed to protect against a variety of threats.
The first step in adopting a multi-layered strategy is mastering prevention capabilities. Try to limit the exposed attack surface and minimize the number of entry points that threat actors can use. Identify and correct weaknesses by implementing patch and risk management solutions before threat actors can exploit them. Consider the impact of compromised VDI or RDS host on the connecting clients, and if needed, review and update your access policies.
While this case is focused on the client drive redirection, all virtual channels are capable of transferring data and can be potentially weaponized. Automated protection controls should be deployed to all potential entry points exposed to threat actors (including work-from-home laptops or roaming employees). This includes next-generation antivirus, but also seamlessly integrated IP/URL/Domain reputation, and protection against previously unknown threats. This gives you the capability to detect and block most security incidents before they can do any harm.
Despite your best efforts, it is still possible that modern threat actors will make it past your prevention and protection controls. This is where your detection capabilities come into play. Whether you get these capabilities as-a-product (EDR/XDR) or as-a-service (MDR), the purpose is to minimize the time when threat actors remain undetected.
Finally, for all these capabilities to effectively reduce security risks, you need to maintain response capabilities across all of them. Whether it means applying patches before vulnerabilities can be exploited, investigating a potential security incident, or damage control after a security breach, security operations play a critical role in reducing security risks.
The use of multiple layers of security creates overlapping barriers that an attacker must overcome, which can reduce the likelihood of successful attacks, limit the scope of an attack if one occurs, and provide early warning of potential threats. Ultimately, preventing security incidents from becoming security breaches.
We would like to thank Victor Vrabie, Cristina Vatamanu, Alexandru Maximciuc and Clay Blankinship for help with putting this advisory report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks