The ‘Security for Apps’ Guide to Read Before Downloading

Most people don’t think about app security until it’s too late.
You tap “install,” grant a few permissions, log in, and trust the app to behave. But behind that clean UI could be vulnerable code, leaked data, or third-party trackers quietly harvesting your info. If you’re a creator, business owner, or everyday user storing passwords, financials, or private content, that puts a target on your back.
Let’s break down how app security works, why most apps get it wrong, and what you can do to protect data, mobile devices, and your identity, whether you're building apps or just using them.
What is app security, and who needs it?
App security means protecting apps from being hacked, exploited, or used to spy on you. That could mean stopping malware, blocking unauthorized access, or shielding your data from third parties.
For an app developer, this means integrating secure APIs, encrypting user data, and preventing reverse engineering. And if you're an everyday consumer, it means knowing which apps to trust and what red flags to look for on your mobile app.
Take mobile banking, for example. If an app doesn’t use secure HTTPS communication or multi-factor login, an attacker on the same Wi-Fi network could intercept your login or spoof the app itself. That’s actually happened in real-world credential theft campaigns.
How app security impacts you
According to our Threat Debrief, in February 2025, ransomware attacks hit a record high, with many of them targeted through vulnerable apps, unpatched systems, and poor security controls.
What does that mean for you? You could download what looks like a free VPN, a modded game, or a cracked app and unknowingly install malware. Hackers are now exploiting app flaws to gain access, lie low, and launch attacks weeks later using tools already on your device.
Every time you:
- Sign into an app using your fingerprint (biometric authentication)
- Share your location or camera access (application permissions)
- Sync your files to the cloud
- Store sensitive info like passwords or payment details
…you’re placing trust in that app’s security hygiene. If it’s poorly built or unprotected, you could be opening the door to identity theft, financial fraud, or intellectual property loss (for creators especially). That's why mobile application security is so important. Nowadays, losing your digital ownership can cost you everything.
Most common app security threats
When mobile apps get breached, it can be due to bad code, too much access, and weak security hygiene. Whether you're an app developer, creator, business owner, or just someone installing apps on your phone, here’s what to watch for:
1. Unsecured connections
Apps that skip HTTPS communication or use outdated encryption leave users exposed to man-in-the-middle attacks. This means that any sensitive data sent, such as login credentials, short message service (SMS) codes, private chats, can be intercepted in transit.
For example, if you used a banking app to send sensitive information (like financial data) in plaintext over public Wi-Fi, a hacker sitting in the same café could intercept your account info using nothing more than open-source sniffing tools.
What to do: Only use secure mobile applications that enforce HTTPS by default. Bitdefender Mobile Security helps detect apps using insecure network traffic even if they’re already installed.
2. Overreaching permissions
Many apps ask for access to your camera, mic, contacts, or even SMS messages with no clear reason. Each unnecessary permission creates a new attack surface and increases the chance of compromise.
For example, flashlight apps that ask for file storage, location, and microphone access clearly ask for more than their core function. Some of these were later linked to adware or spyware campaigns.
What to do: On both IOS and Android, regularly audit app permissions in your device settings. Android developers must declare requested access in the manifest, but that doesn’t mean they should be trusted blindly.
3. Cloned or fake apps
Mobile application security also means watching where you download from. Third-party stores (outside the Google Play Store and App Store) are sometimes flooded with fake apps that mimic popular tools, from WhatsApp to utility apps, but inject spyware, keyloggers, or worse.
These apps can compromise your security by hiding their icon, delaying activation, or launching full-screen phishing overlays to steal passwords. In a 2023 Bitdefender mobile app security test, tens of thousands of hidden adware apps were uncovered using anomaly detection, many of which disguised themselves as modded games or cracked VPNs.
What to do: Avoid sideloading apps from unknown sources and run regular scans with app shielding tools.
4. Code or software vulnerabilities
Even legitimate developers make mistakes. Security vulnerabilities like hardcoded access tokens, unprotected APIs, or unpatched third-party libraries are common. These flaws open the door to private data breaches, session hijacking, or remote code execution.
Web-based mobile apps often face cross-site scripting risks too, especially when rendering user input without proper sanitization, as attackers can inject scripts that run inside the app’s interface.
One software vulnerability example is the zero-day flaw (CVE-2019-3568) in WhatsApp’s video calling system, which created one of the most infamous security incidents. No download. No tap. Just a missed call and Pegasus spyware was silently installed. This vulnerability allowed attackers to execute malicious code and gain full access to messages, mic, camera, and more on their victims' mobile devices.
Meta’s lawsuit revealed that the NSO Group continued to find new ways to bypass defenses, even after being sued. One vector, codenamed “Erised,” used WhatsApp’s own servers to deliver the spyware.
Take this as a reminder that secure mobile applications depend on regular patching, secure development practices, and anomaly detection technologies like those used in Bitdefender Mobile Security.
How to test mobile app security
You don’t need to be a developer or even tech-savvy to spot insecure apps. Make mobile app security work in your favor with these tips:
1. Review app permissions
Before installing any app, check what it wants access to. On Android, this includes permissions for location, contacts, SMS, camera, mic, and more. On iOS, permission prompts appear at first on the user's device but many blindly accept. Watch how apps phrase their permission requests. If the language is vague or generic, that’s a red flag indicating that the app may be trying to hide excessive access.
Here’s what to look out for:
- A note-taking app shouldn’t ask for microphone access.
- A wallpaper app has no business reading your messages or GPS.
- A “free” VPN requesting access to your photos or call logs is a red flag.
iOS Tip: Go to Settings → Privacy & Security to audit permissions. Apple’s App Privacy Reports also show what data an app collects, how often, and where it sends it.
Android Tip: Use the “Permission Manager” in Settings to revoke unnecessary permissions. Also check “Install unknown apps” settings, as this blocks apps from third-party sites unless you override it.
2. Scan for hidden malware or behavior
Many mobile threats don’t show up until days after instal. Some malicious apps secretly collect user logs, including keystrokes, clipboard content, and app usage, to profile victims or exfiltrate sensitive data.
So, use security tools like Bitdefender Mobile Security for iOS and Android, which uncovers tens of thousands of malware samples, including fake VPNs and modded games that evade detection by mimicking legitimate apps, to keep security risks at bay.
So, if you run a mobile application security testing, here's what to do:
For Android:

- Start with Google Play Protect:
Go to Settings → Security → Google Play Protect → Scan.
This checks for known threats but it won’t catch brand-new or modded malware. - Go in-depth with Bitdefender:
Install Bitdefender Mobile Security for Android and run a full device scan.
The App Anomaly Detection feature kicks in automatically and flags suspicious behaviors like stealthy permissions, launch-hiding tactics, or encrypted payloads using the same tech that uncovered 60,000+ hidden malware apps in 2023 alone. - Installing from mod sites or beta links?
Bitdefender will analyze the app immediately after install, even if it's from outside the Play Store, and monitor it continuously in the background for behavioral red flags.
For iPhone users, Apple doesn’t allow traditional antivirus scans. But here’s how to strengthen your device and check for signs of compromise:
- Turn on Lockdown Mode:
Go to Settings → Privacy & Security → Lockdown Mode.
This limits background activity, message attachments, and code execution. It's essential if you think you’ve been targeted by spyware like Pegasus or malware of any kind. - Use Bitdefender Mobile Security for iOS:
While it can’t scan app binaries directly, it has in-depth security features that can: - Audit your privacy misconfigurations
- Monitor all network traffic from apps (not just Safari)
- Detect phishing, unsafe Wi-Fi networks, and data leakage
- Offer a secure VPN tunnel with real-time web filtering
Regardless of your mobile devices, always review app permissions after install. Ask yourself: “Does this weather app really need access to my camera or contacts?” Unnecessary access is a common indicator of malicious intent to compromise security.
3. Watch for suspicious activity over time
Malicious apps often lie dormant, then activate later. Many may not trigger antivirus alerts but can still adversely affect your battery life, bandwidth, or data privacy over time. So, to mitigate risks, watch for:
- Faster battery drain than usual
- Spikes in background data usage
- Crashes when launching common apps
- New tabs opening in Safari or Chrome without prompting
On iPhone: Use Screen Time → App Activity and Battery analytics to spot apps consuming resources in the background.
On Android: Check App Usage Access settings or install a behavior monitor to track network activity per app.
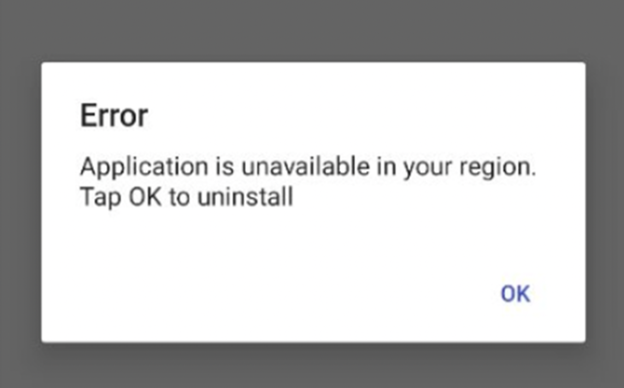
Our labs found that many adware apps avoid detection by hiding their icon, showing a “not available in your region” message after install, and triggering actions only after two hours or more. These tactics are invisible to most users unless you're monitoring behavior.
4. Use native controls to limit exposure
Even secure apps can be exploited. Limiting access reduces your risk.
- On iOS, you can toggle Precise Location off, grant one-time permissions, and limit Bluetooth access to protect background data sharing. iOS’s App Tracking Transparency lets you block tracking across other apps and websites. Go to Settings → Privacy → Tracking and disable app tracking globally.
- Android 13+ includes auto-reset security permissions, which revoke access from unused apps after a few months to avoid security issues later on.
5. Avoid apps that haven’t been updated
Unpatched apps are soft targets. Some are abandoned third-party libraries or newly discovered vulnerabilities, while some are apps without regular security patches that get exploited by attackers.
Regardless, they all pose security issues for your mobile app and mobile devices. A clear mobile security policy that highlights update frequency and developer responsiveness can be the difference between trust and exposure.
So, before installing, check:
- Date of last update
- Whether security fixes are listed in changelogs
- If the developer actively responds to reviews or issues
6. Run periodic security checks
Just like you scan your laptop for malware, your mobile devices deserve the same attention.
Set a reminder every 3 months to:
- Audit app permissions
- Delete apps you no longer use
- Check for software updates
- Re-scan for hidden threats
- Review privacy settings
Why trust Bitdefender for Mobile App Security
When it comes to mobile security, most users still treat protection like an optional upgrade, until something breaks. But attackers aren’t waiting. In February 2025 alone, Bitdefender’s Threat Debrief recorded 962 claimed ransomware victims, the highest single-month count in history (and a 126% year-over-year increase).
Most didn’t see it coming. Why? Because they trusted apps that looked clean but weren’t built to defend.
What makes Bitdefender different?

Most mobile security tools rely on known malware signatures. Bitdefender’s anomaly detection, the first of its kind on Android, flags thousands of undetected malware-laced apps, many disguised as cracked VPNs, modded games, or fake productivity tools.
- For Android, Bitdefender Mobile Security consistently ranks among the top-rated mobile security solutions in independent lab tests.
It combines powerful threat defense and privacy tools like VPN, Anti-Theft, and WearON into one high-performance app built to secure every corner of your mobile life and sensitive data against the latest security threats. - For iPhone's operating system, Bitdefender Mobile Security quietly protects what matters most, AKA your personal data, online activity, and app traffic, without draining your battery or interrupting your day. It spots risky misconfigurations, filters malicious content in real time, and keeps your browsing and app use private, even on public Wi-Fi.
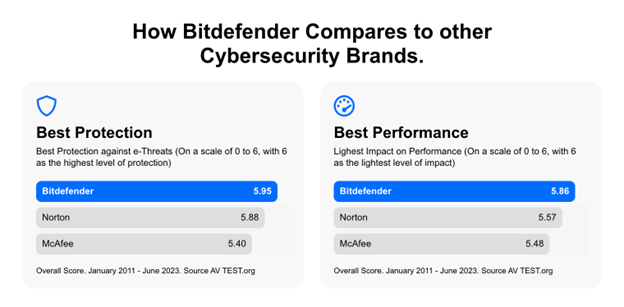
"Bitdefender Mobile Security packs a serious punch with a single subscription. You'll get a whole host of features, including anti-theft measures, and top-notch antivirus capabilities that'll work hard to keep your device safe. In fact, Bitdefender scored top marks in the latest AV-Test roundup, and AV-Comparatives (the other major independent antivirus test lab) observed a protection rate of 99.9%, which is seriously impressive." - Benedict Collins via TechRadar
Real-time defense, without draining your battery
Traditional antivirus software either slows down your phone or misses the real threats. Bitdefender Mobile Security uses cloud-based scanning so your device stays fast while it constantly monitors for shady behaviors like:
- Apps hiding their icons after install
- Programs that stay dormant for hours before launching adware
- Payloads decrypted from encrypted local storage using SQLCipher (a trick used in recent stealth adware campaigns)
Protection that fits your actual life
If you're a creator, your smartphone is your business hub. If you're a parent, it’s a vault of memories, locations, passwords, and chats. Bitdefender helps preserve that digital trust and keep it in the hands of only legitimate users, not third-party apps.
- Banking on public Wi-Fi? Bitdefender’s built-in VPN encrypts 200MB/day, so your financial data isn’t up for grabs at the airport lounge.
- Not sure if that app’s legit? App Anomaly Detection catches malicious intent, even when the icon is hidden and the behavior delayed before it compromises your device.
- Worried about your personal data leaking? The app scans for misconfigurations and suggests what to fix, whether it’s an over-permissive app or a risky connection.
What competitors aren’t telling you
You won’t see these features in most “top security apps” lists:
- Behavioral scanning post-install. Most tools scan once and call it done. Bitdefender watches your apps long after install, and that’s how it catches time-delayed attacks.
- Zero-trust approach to all apps. Many threats now ship through apps that pass Google Play Protect. Bitdefender doesn’t rely on trust. It analyzes what the app does, not just what it claims.
- Threat reports tied to real-world attacks. Bitdefender leads global detection, with 30+ billion threat queries validated daily and insights used by law enforcement and OEM partners worldwide.
Mobile App Security Best Practices
Follow these practices help protect data, limit attack surfaces, and secure your mobile devices.
If you're an everyday user
Even if you’re not a developer, your day-to-day habits affect your exposure to threats. Here’s what smart mobile users do:
Only install apps from official stores
Stick to the App Store or Google Play. Why? Outside official stores you'll find even more malicious mobile applications disguised as modded games, cracked VPNs, or fake productivity tools.
Always check permissions and security features
If a flashlight app requests access to your microphone, or a calculator wants your location, something’s off. Don’t grant permissions unless they’re essential to the app’s core functionality. When downloading mobile applications, take a moment to read through the app’s security features, protocols, and certifications (if any). Check for peer reviews via communities of forums, in the review section, or on reputable review sites like G2, Capterra, Trust Pilot, etc.
Use MFA, even on apps that don’t force it
An app without multi-factor authentication (MFA) leaves you exposed. Turn it on manually via the app’s settings wherever possible. MFA blocks 99.9% of account compromise attempts, according to Microsoft.
If you're a developer
Building mobile apps? App security doesn't mean passing app store reviews. Your responsibilities also include protecting users from real app security threats. Use this checklist to account for mobile app security from day one:
Use hypertext transfer protocol (HTTPS) for all communication
Every API request, login, content update, or file sync should be encrypted using HTTPS. Use the latest TLS protocol and reject any fallback to older versions. Misconfigured endpoints are still one of the most common ways attackers intercept data or launch man-in-the-middle attacks.
You can implement a web application firewall to inspect requests in real time.
Run security scans before launch, not after
Before your app ever hits the store, run mobile application security testing. Open-source tools like Mobile Security Framework (MobSF) let you scan for issues like SQL injection, insecure permissions, or data leaks to help you identify vulnerabilities in your code and any embedded SDKs or libraries. Security scans can help uncover application vulnerabilities early before they become exploitable in post-application development phases.
Never hardcode secrets in your app
Hardcoded tokens and API keys are low-effort goldmines for attackers. Avoid storing anything sensitive in the source code, app assets, or local storage. Use environment-based secrets and encrypted storage where necessary, and make sure keys are rotated regularly.
Audit your third-party libraries and keep them updated
Your runtime environment, from mobile OS to installed libraries, can be probed for weaknesses unless you use controls that actively monitor it during execution.
Every dependency you add brings someone else’s code (and potential bugs) into your app. Use vetted, maintained libraries only. Tools like Snyk can help you track known vulnerabilities and get alerts when updates are needed.
To stay ahead of code injection and reverse engineering threats, modern apps can implement runtime application self-protection (RASP), which detects and blocks tampering while the app is running.
Treat security as part of the user experience
To make an app secure is to make it trustworthy. It protects user privacy, prevents data breaches, and reduces liability. But more than that, it builds customer loyalty, especially now that data leaks make headlines every week.
If you’re building mobile applications or updating them to the latest security patches, you’re also building the trust infrastructure they run on. Make security visible. Make it continuous. Make it non-negotiable.
Mobile app security is not an afterthought
We don’t live in a world where you can install an app and forget about it. Not when modded apps come laced with hidden malware. Not when even the App Store can host apps with poor data hygiene. And certainly not when attackers exploit runtime flaws and leave no icon, no warning, no trace.
If you're developing apps, managing a business on mobile, or just living your life through your phone, mobile application security is non-negotiable.
To secure applications and your online behavior, make sure to review your app update habits. Rather than pressing ok for each auto-update, monitor which apps get updated often and which haven’t seen a security patch in months. A neglected app can bring in multiple security issues.
Make mobile app security work for you, not against you
The bottom line is:
- If it’s connected, it’s exposed.
- If it’s ignored, it’s exploitable.
- If it’s protected, you’ll never even notice the mobile security threats you avoided.
Bitdefender Mobile Security helps make sure of that
Whether it’s phishing links, zero-click spyware, or stealthy app behavior, it detects the unknowns that slip past traditional scans. Quietly, in real-time, without draining your battery or complicating your day.
🔐 Protect your phone like your life is on it, because these days, it probably is.
Get Bitdefender Mobile Security for Android and iOS →
tags
Author
The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsYou might also like
Bookmarks


