Lost iPhone? Watch Out for this Phishing Trap

The National Cyber Security Centre (NCSC) of Switzerland is warning of a surge in phishing scams targeting people with lost or stolen iPhones.
The scam preys on the anxiety of device loss and offers what appears to be a “found abroad” message. In reality, though, it’s a clever setup to steal your Apple ID credentials.
“Losing your iPhone is always annoying,” reads the scam alert in the NCSC’s Week 44 2025 bulletin. “Not only is the device gone, but your personal data may also be lost. Once the initial panic has passed, most people are left hoping that someone honest will find it. But if scammers have your phone, they may try to exploit this hope.”
How the scam works
Often months after a device has been lost or stolen, victims receive a text message or an iMessage claiming their iPhone has been found abroad.
The message includes accurate, convincing details of the missing device (model, color, storage capacity) which the attackers glean from the phone’s case itself.
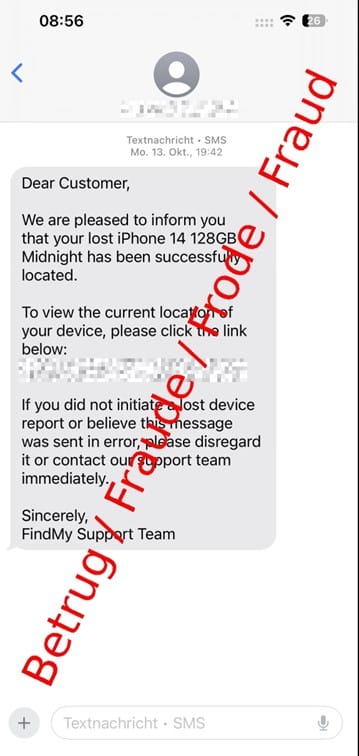
The scam SMS pretending to come from Apple
Source: NSCS
The message invites the recipient to click a link to view the device’s location. But the link leads to a fake website masquerading as Apple’s sign-in page. Entering credentials here hands control of the Apple ID to the attacker.
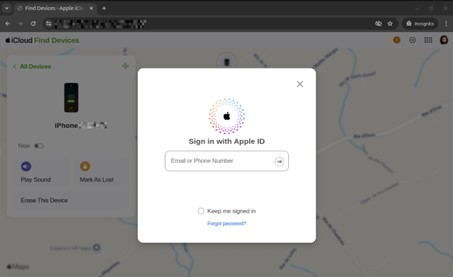
The phishing page asks for Apple ID access data and shows the alleged location of the lost iPhone
Source: NSCS
Why do they do this? Because once a criminal controls the Apple ID, they can disable the Activation Lock – the mechanism which normally prevents a lost iPhone from being reused – making the iPhone usable or resellable.
How they do it
It’s difficult to find out the phone number of a locked device, but the NSCS says one way to do it is via the SIM card that was in the phone at the time of theft or loss. This method only works if it hadn’t been protected with a PIN or it hadn’t been blocked yet at the time the attackers gleaned the number.
“Another possible route is via Apple's Find My feature: when a device is marked as lost, the owner can display a message on the lock screen containing contact details, such as a phone number or email address,” the NCSC explains. “This can be very helpful if the finder is honest – but in dishonest hands, the same information can be used to launch a targeted phishing attack.”
Why it’s so dangerous
Apple’s Activation Lock feature offers strong protection. Attackers bypass it not by technical hacking, but by social engineering. When a phone is lost, you might reasonably hope someone will find it and contact you. This emotional hook is what attackers exploit.
The presence of accurate device details (drawn from the device metadata) gives the message perceived legitimacy. Once the Apple ID and account access are compromised, broader damage can follow (personal data, linked devices, payment methods etc.).
How to avoid lost-iPhone traps
Here are some proactive steps you can take to protect your devices and accounts.
Ignore unsolicited “found device” messages
· If you receive a message claiming your Apple device was found in a foreign location, do not click any links. As the Cupertino tech titan itself stresses, “Apple will never contact you to say that your iPhone or iPad has been found.”
· The only way to locate a lost device is to manually check for its location using the Find My app on another device or by signing into iCloud.com/find. If the device beacons, you'll see its location on a map within the Find My service. You can then choose to play a sound, mark it as lost, or erase it.
· Also, legitimate notifications from Apple never ask for your password via an unsolicited link.
Enable and use Lost Mode promptly when a device is missing
· Go to iCloud.com/find, or the Find My app on another trusted device and mark your lost or stolen iPhone/iPad as lost. This locks it with your passcode and suspends Apple Pay cards and credentials.
· If your device has Stolen Device Protection, Face ID or Touch ID may also be required to unlock.
Report the missing device and update your account
· Report your missing device to your local police (you’ll need the serial number) and your wireless provider to suspend service. After marking the device as lost, if you cannot recover it, consider remotely erasing it via Find My.
· Do not remove the device from your Apple Account or Find My until all claim/lock-processes are final. Removing it too soon may disable Activation Lock.
Keep your Apple ID credentials safe and use two-factor authentication
· The general guidance on social-engineering and phishing (not just in this case) is to never share passwords, verification codes, or security information with anyone.
· Rely on two-factor authentication (2FA) on your Apple ID so even if someone guesses your password they still cannot access your account without the second factor.
Watch out for social-engineering
· Scammers often impersonate Apple and other names in Big Tech via phone calls, messages, or email. They may create a sense of urgency, use device detail knowledge, or ask you to disable security features.
· Always verify by contacting the company using official channels, not via links or numbers provided in suspicious messages.
Review what you show on your Lock Screen and protect your SIM
· If you mark your device as lost and display contact details on the lock screen, use a dedicated email address or contact point (rather than your regular number or email address) to limit the risk of social engineering.
· Make sure your SIM card is protected by a hard-to-guess PIN (not an easily guessable one like 1,2,3,4 or 0000). This prevents a thief from reusing the SIM and possibly receiving messages/calls directed to your number.
Stay safe!
The incident flagged by the NCSC shows how old problems (lost/stolen phone) combined with modern threats (phishing, social engineering) can create a formidable scam. Follow theis guidance and maintain a healthy suspicion of unsolicited claims about your devices or online accounts.
If you ever suspect something is amiss, use Scamio, our free scam-fighting chatbot, to inquire about a potential attack on your finances, security, or privacy. For peace of mind, consider using an independent security solution that can sniff out attacks on your digital life.
You may also want to read:
UK Cracks Down on Scammers Spoofing Your Phone Number
tags
Author
Filip has 17 years of experience in technology journalism. In recent years, he has focused on cybersecurity in his role as a Security Analyst at Bitdefender.
View all postsYou might also like
Bookmarks
