Call Spoofing: What It Is, How It Works, and How to Protect Yourself

Call spoofing is a scam tactic threat actors use to disguise the origin of a phone call. Understanding how it works could help you detect and avoid it.
What is call spoofing?
Caller ID spoofing is the practice of obfuscating the origin of a phone call by falsifying the caller ID information displayed on the recipient's device. Threat actors use it to make a call look like it’s coming from a trusted number, such as a local business, a government agency, or even someone’s personal phone.
Though it has legitimate business uses, spoofing has become a preferred tool for fraudsters due to its ease of use and psychological effectiveness.

Thanks to VoIP technology and spoofing apps, fraudsters can impersonate almost any number with just a few clicks. This has led to a surge in phone-based scams that manipulate trust and urgency to extract personal information, financial details or direct payments from victims.
How call spoofing works
To spoof their caller ID, fraudsters use technology that lets them alter the metadata associated with a phone call. A common misconception is that, when you receive a call, the phone displays data based on the actual source of the call. However, it actually depends on the information sent through your carrier’s network.
Spoofing tools enable the customization or complete fabrication of this information.
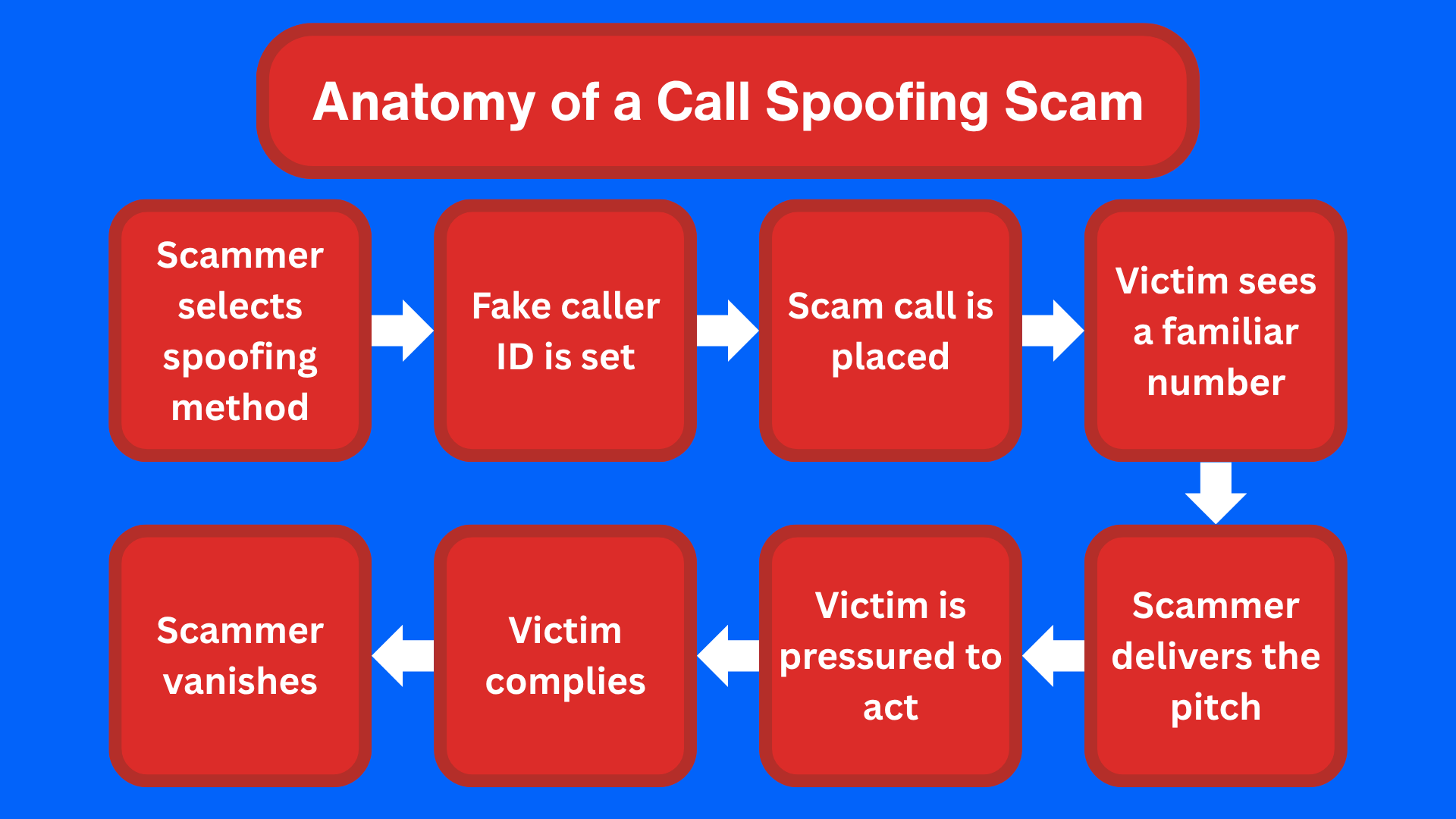
While telecom regulations and authentication protocols have been developed to combat malicious practices, spoofers often exploit international networks, VoIP carriers or unsecured systems to bypass detection. With minimal setup, someone can impersonate a local number or a known, legitimate institution and call thousands of victims per hour.
Types of spoofing and related attacks
Although the focus is often on voice calls, spoofing affects other channels of communication as well. The most common types of spoofing include:
- Neighbor spoofing: Mimics a local area code and exchange (e.g., 212-555-XXXX) to seem familiar
- Impersonation spoofing: Appears as a known brand, government agency, or even someone in your contacts
- SMS spoofing: Sends texts that look like they’re from trusted numbers or shortcodes, often containing phishing links
- Email and domain spoofing: Fakes the “From” field in emails or websites to trick users into sharing data
- AI voice spoofing: Uses deepfake technology to clone voices, making social engineering attempts far more convincing
Each form of spoofing is just one part of a broader scam strategy meant to build credibility and provoke emotional responses.
Real-life call spoofing scenarios
Spoofing techniques are as diverse as the scams they support. Notable examples of call spoofing in real-world scenarios include:
- Tax agency impersonation: A caller pretends to be from the IRS or another tax authority, demanding immediate payment under threat of legal action
- Grandparent scam: A fraudster claims to be a grandchild in distress, often needing bail money, and spoofs the grandchild’s number or that of a local police station
- Bank fraud alerts: After spoofing your bank’s phone number, the scammer pretends to be from your bank’s fraud department, warns of suspicious activity and asks for verification information
- Tech support scams: Threat actors spoof the phone number of reputable tech companies, such as Apple or Microsoft, and call their victims, claiming their devices have been compromised. The con artists offer to fix the issue but demand remote access and sometimes a credit card for payment in exchange for their services
- Business executive scams: Deepfake voice and spoofed caller ID are used together to impersonate high-ranking company executives, requesting urgent wire transfers or sensitive data from employees
These scenarios are only a few of the most common ones used by scammers. In real life, the creativity and cunning of con artists know no boundaries. In using them, perpetrators exploit trust in institutions, familiarity, urgency and fear.
The scale of the issue
Unfortunately, spoofing-related scams continue to plague the cybersecurity landscape, posing a significant threat in both scale and sophistication. Imposter scams, many of which begin with spoofed calls, cost Americans nearly $3 billion in 2024, according to the US Federal Trade Commission (FTC). Globally, telecom-related fraud losses are estimated to exceed $40 billion annually.
Advanced spoofing now incorporates AI-generated voices and robocall campaigns that can dial millions of numbers using customized scripts. This industrial-scale fraud operation shows no sign of slowing, especially as spoofing tools become easier to access and scams grow more convincing.
Regulatory and industry response
Governments and telecom providers are stepping up their response to the spoofing epidemic. In 2020, the US Federal Communications Commission (FCC) implemented the STIR/SHAKEN protocol, which digitally signs calls to verify that the number shown is actually the number dialed.
This system helps filter out spoofed numbers, though it’s most effective within domestic networks and still limited across borders. Legal frameworks such as the 2009 Truth in Caller ID Act prohibit spoofing when used to defraud or cause harm. Other countries, such as Canada and the UK, have passed similar regulations and continue to pressure telecom providers to increase transparency and filtering capabilities.
Private-sector solutions – including AI-based call detection, blocking, filtering, blacklisting systems, and consumer call-screening apps – also play a crucial role. However, the fight remains an arms race between fraudsters and defenders.
How to protect yourself
While regulations and tech solutions are evolving, the most effective defense starts with individual awareness and a skeptical eye. Here are some practical ways to protect yourself from spoofing scams:
- Don’t trust caller ID at face value: If something feels off, even if the number looks familiar, don’t assume it’s legitimate
- Hang up and verify independently: Always call back using a known, official number (from a website, bank card or bill) rather than redialing the incoming number.
- Avoid sharing personal or financial information over unsolicited calls: Legitimate organizations rarely, if ever, demand sensitive details out of the blue over the phone
- Report suspicious calls: In the US, you can file reports with the FCC or FTC; in other countries, report to equivalent consumer protection or telecom authorities
- Use call-blocking and spam-filtering tools: Most mobile carriers and smartphone platforms offer features to reduce spam and identify likely spoofed calls
- Educate family members (especially seniors): Many scams target seniors and other vulnerable categories of people using emotional manipulation and urgency
- Stay informed: Be aware of the latest scam techniques, especially emerging threats like deepfake voice impersonation
- Use Bitdefender Scamio to assess suspicious calls: You can describe the call scenario to Scamio, including the caller’s claims, requests and tone, and it will analyze the situation’s perceived legitimacy
- Take control of your calls: Bitdefender's new Call Protection feature for Android helps you detect and block spoofed numbers before you even answer
Adopting a cautious mindset and taking proactive steps can help you significantly lower your exposure to call spoofing and other types of scams.
Looking ahead
As spoofing tactics evolve, driven partly by AI and automation, our defenses must keep pace. Emerging voice verification systems and biometric protections are on the horizon, but scammers are already adapting. For now, personal vigilance, institutional security protocols and industry-wide verification frameworks like STIR/SHAKEN are the cornerstones of our defense.
Unfortunately, call spoofing isn’t going away any time soon. However, understanding what it is, how it works, and taking simple yet smart precautions can thwart scammers.
Frequently asked questions about call spoofing
What is phone call spoofing?
Call spoofing, also referred to as phone call spoofing or caller ID spoofing, is when a caller intentionally obfuscates their identity by altering the data relayed to your caller ID display.
Is it illegal to spoof a call?
According to the 2009 Truth in Caller ID Act, intentionally relaying inaccurate or misleading caller ID information to defraud, cause harm, or steal valuable assets or information is prohibited by the FCC. Illegally spoofing can result in penalties of up to $10,000 for each violation.
Can spoof calls be detected?
Spoofed calls can be easily detected by taking a simple action. If someone calls you and asks for your personal information or credit card details, or you feel something is off during the call, hang up, look up the number using trusted sources (such as the official website or contact list), and call. This way, you can easily see whether the caller was scamming.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


