Bitdefender Threat Debrief | October 2025

LockBit Lives On with Version 5.0 and a New Partnership
This edition of the Bitdefender Threat Debrief covers developments that include LockBit’s return, a new Clop campaign, revived groups, and more.
As ransomware continues to evolve, our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT)—such as news reports and research—with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It is important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
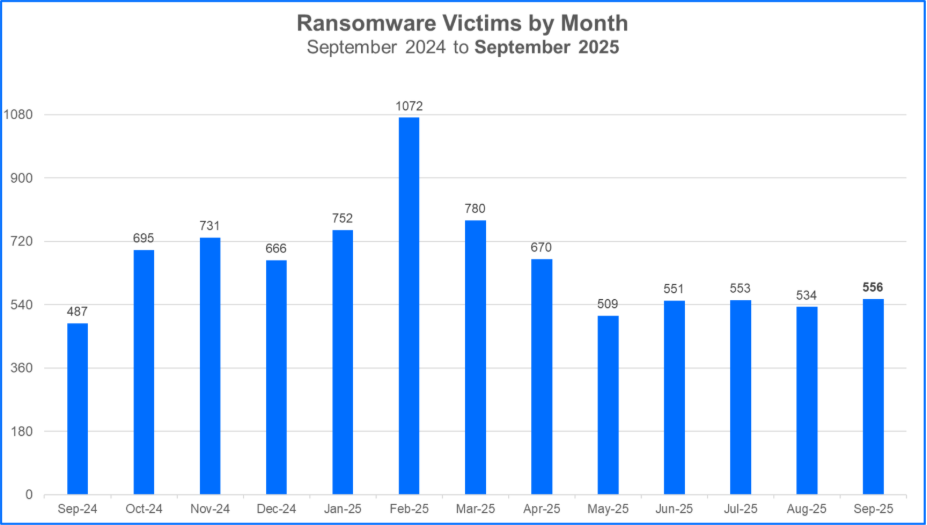
For this month's report, we analyzed data from September 1 to September 30 and recorded a total of 556 claimed ransomware victims.
Featured Story: LockBit Lives On With 5.0 and a New Partnership
After two months of inactivity and a pending announcement, LockBit has released version 5.0. The release marks a six-year milestone in LockBit’s operations and is expected to draw in the interests of other emerging ransomware groups and potential affiliates. The LockBit 5.0 ransomware is upgraded to include anti-analysis capabilities such as ETW patching. This allows the ransomware to stifle detection measures by altering logging patterns written to specific processes in memory. LockBit 5.0 is also designed to target OSes such as Windows, Linux, and ESXi.
The Platform: Access and Security
LockBit is a group that has fallen victim to past compromises. As a result, many in the security community are curious about the precautions LockBit will now take to secure their infrastructure and resources. A user must pay to register an account and access LockBit 5.0. Once the user makes a $500 payment via a Bitcoin or Monero transaction to the provided address, the user can access the platform's control panel. This allows them to create encryptors and correspond with victims.
Image: LockBit 5.0 webpage
LockBit also has a bug bounty program intended to bolster security measures for their website and connected services. However, when it comes to communications with affiliates and other groups, LockBit has allowed the use of other methods outside of the direct infrastructure controlled by the group. These actions tend to reduce the group’s operational security. This can come at a greater detriment to LockBit, especially when considering that their future recruitment efforts and other communications likely extend to sites leveraged by DragonForce.
The Recent Coalition with DragonForce
DragonForce recently opened their digital doors, starting a partnership with LockBit and Qilin. LockBit’s partnership with DragonForce may be a strategic move made to rebuild followers and the LockBit ransomware brand after events such as Operation Cronos, builder and infrastructure leaks, and the loss of staff. At the time of this release, no victims have been published under LockBit 5.0.
While Qilin continues to be an influential threat actor, DragonForce’s total number of claimed victims has remained consistently low each month. The group has averaged 20 victims over the past few months. DragonForce also continues to seek out additional partnerships and recently published the following: “Our doors are open to anyone who cares about the future of our challenging field. If you have a partnership program, feel free to reach out to us, and together we can maximize our overall income! More updates on this topic will be coming soon, so keep an eye out for news.”
DragonForce’s desire to form other partnerships may stem from a need to exert greater economic control, doubts about Qilin and LockBit’s long-term cooperation, or both. We’ve seen just how fickle group partnerships can be when examining emerging and established groups. DragonForce remains a proponent of distributing the infrastructure and weapons that groups utilize to organize and execute their campaigns. That model may work in LockBit’s favor (temporarily) or come at a cost that undermines their ability to grow without DragonForce’s support. Regardless, as this development evolves, the groups must either innovate or stagnate.
Other Notable Ransomware News
Now, let’s explore the notable news and findings since the last Threat Debrief release.
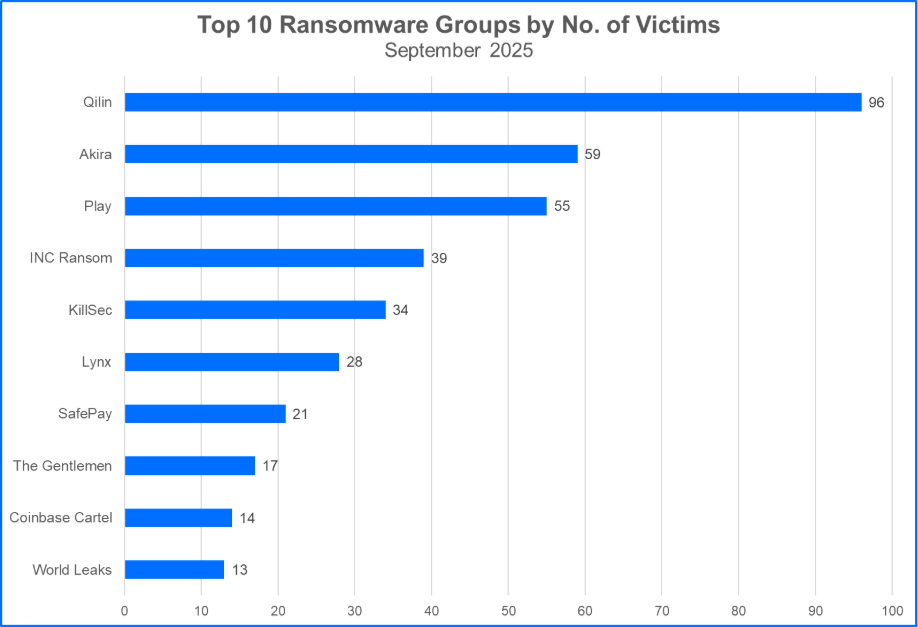
- Qilin claims the top rank for the fourth consecutive month: Nearly a third of Qilin’s September victims were organizations in Financial Services. And another group, Securotrop, continues to be affiliated with Qilin and data leak activities. Qilin’s dominance month after month has shown that even groups ranking second or third and claiming 50+ victims have fallen behind significantly.
- Clop’s extortion campaign is revealed: Clop is known for leveraging zero-day exploits and they’ve crafted an extensive campaign, sending emails to thousands of compromised accounts and demanding that affected parties pay their ransom to prevent the disclosure of sensitive data. The campaign has been active since August. The sensitive data is tied to the application Oracle E-Business Suite. Clop extorted CVE-2025-61882. Exploiting this flaw does not require credentials and allows a threat actor to remotely execute code. Organizations using an affected version of Oracle E-Business Suite, including 12.2.3 through 12.2.14 are advised to promptly update their software.
- Scattered LAPSUS$ Hunters’ movements are disrupted: The group recently published a data leak site (DLS) where they maintain posts on past and current victims. The DLS emerged only weeks after the arrests of two teens based in the U.K. that have been tied to Scattered Spider’s operations. A statement was later posted on BreachForums announcing that Scattered Spider, LAPSUS$, and others would go dark. The FBI seized BreachForums’ infrastructure in early October 2025. Their ally, ShinyHunters, claimed responsibility for two recent campaigns and has remained adamant that they will continue to post claimed victims.
- The Gentlemen and Coinbase Cartel join the Top 10: Little is known about two groups that have emerged into this month’s top 10. The Gentlemen is one group, and little is known about their motivations, and current operations. Coinbase Cartel is another emerging group. Interestingly, the group claims that they do not use ransomware, and instead they deal with data theft and disclosure. As both groups enter our Top 10, Sinobi ransomware has fallen from the list.
- Google’s AI detects ransomware, stopping Google Drive compromise: Google Drive now includes support for an AI model that has learned from analyzing millions of ransomware samples. If Google Drive syncing is enabled on a system that has executed ransomware, then Google’s AI stops the syncing process. This prevents the modification and encryption of data in synced Drive folders. Local folders and directories, however, may still be encrypted, so it’s important to ensure that any local data is regularly backed up.
- Old ransomware groups, presumed dead, resurface: The group activities of both Kawa4096 and Radar ransomware were observed last month. Radar’s infrastructure was taken down by the U.S. FBI nearly two years ago . Kawa4096 had also gone quiet but emerged again in June of this year. The group reportedly had a DLS with a terminal window that mirrored the appearance of Akira’s DLS. Their site has been down since August; however, Kawa4096’s recent activities indicate that the group may be operating under new leadership or has already been acquired by other threat actors.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware data leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
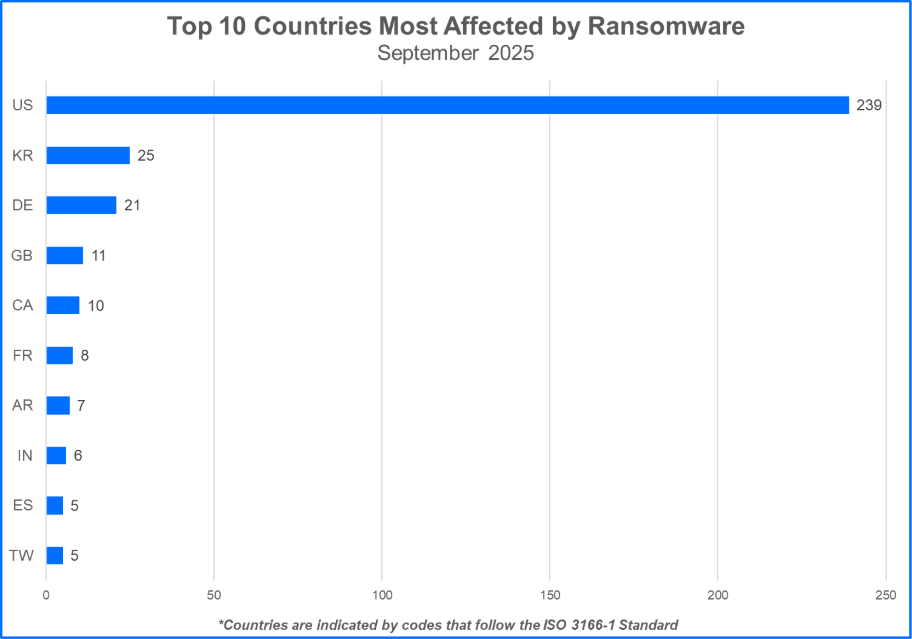
Top 10 Countries for Ransomware Attacks
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. In many cases, this means focusing on developed countries with higher projected growth rates. Threat actors may also execute strategic attacks that unfold during geopolitical conflicts or periods of social unrest. Let’s see the top 10 countries that took the biggest hit from ransomware attacks.
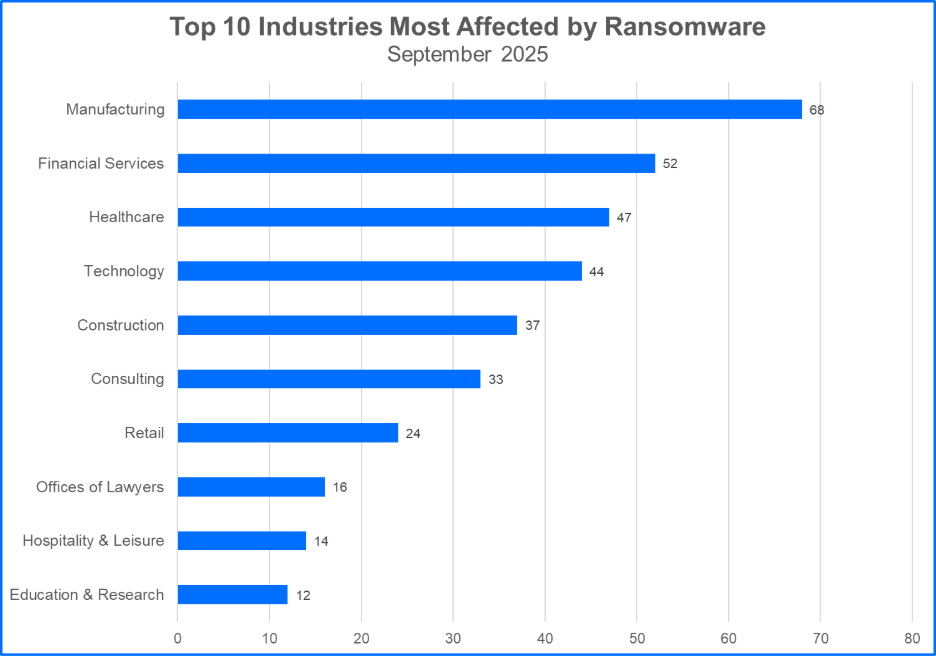
Top 10 Most Attacked Industries
Ransomware gangs may target organizations in critical infrastructure sectors, select other organizations that offer services tailored to the consumer marketplace, or choose to attack organizations that fall into both categories. Understanding the trends and ramifications associated with specific industries, and how specialized services and clientele may be impacted, is crucial to assessing risks and anticipating incidents that may occur. Here are the Top 10 industries affected by ransomware groups.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on X. You can find last month's debrief here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu for their help putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsYou might also like
Bookmarks

