Lovesac warns customers their data was breached after suspected RansomHub attack six months ago

American furniture maker Lovesac, known for its modular couches and comfy beanbags, has warned customers that their data was breached by hackers earlier this year, and that they should remain vigilant to the threat of identity theft.
The warning letter from Lovesac follows a claim by a ransomware group earlier this year that they had breached Lovesac's security and stolen data.
The letter that Lovesac is now sending to an unspecified number of customers claims that it became aware at the end of February 2025 of "suspicious activity" on its network.
An investigation launched by the company determined that between February 12 2025 and March 3 2025, an "unauthorised actor" had accessed Lovesac's systems and made copies of "certain files."
Reading between the lines, despite having found malicious hackers had infiltrated its network, it took days for Lovesac to secure its systems well enough to prevent the attackers from continuing to access its network.
According to the sample letter shared with the Attorney General's offices, files containing personal information such as consumers' names as well as other (frustratingly) unspecified information was breached during the attack.
The date of the breach ties in with a claim made earlier this year by the RansomHub ransomware gang on its extortion portal in early March 2025, saying that it had attacked Lovesac, and stolen 40 GB worth of data. RansomHub indicated that it would leak the exfiltrated data within days if a ransom was not paid.
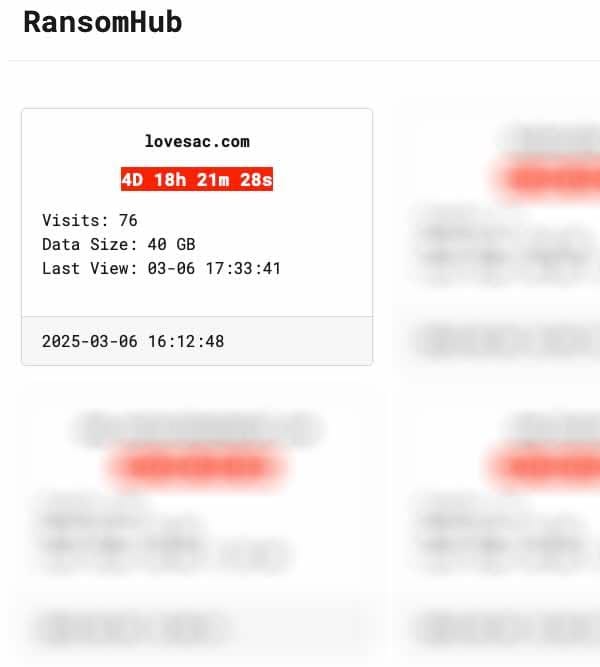
It is not clear whether RansomHub ever followed through with its threats, but now - six months later - Lovesac's customers are being warned that their data fell into the hands of criminals.
Just who the individuals are behind the RansomHub group remains the mystery.
The RansomHub ransomware-as-a-service (RaaS) operation first emerged in early 2024, and claimed credit for a series of high profile attacks against the likes of Christie's auction house, one of California's largest credit unions, the Mexican government, amongst others.
Within months, RansomHub's prolific waves of attacks was considered so significant with hundreds of victims that Bitdefender experts declared it a "prominent player" in the ransomware world.
That is not to say that all parts of the globe have suffered at the hands of RansomHub and its affiliates. In fact, RansomHub declares that it forbids affiliates from attacking "CIS, Cuba, North Korea, and China."
This is one of the reasons why researchers consider the RansomHub group to have been predominantly based in a country that is friendly to Russia, or indeed in Russia itself.
But the details of where RansomHub may be based, and who might be behind it, are of little compensation to Lovesac customers who may be now concerned that their private information could now be not just made public, but actually specifically in the hands of cybercriminals and fraudsters.
The good news is that the RansomHub ransomware operation appears to no longer be active. Its activities came to an abrupt halt at the start of April 2025, when its victim portal went offline without explanation - just weeks after the Lovesac security breach.
The bad news is that just because RansomHub went offline, we cannot be certain that the data stolen from ransomware victims like Lovesac won't have ended up in the hands of malicious parties.
Lovesac says that it has seen no indication that the stolen information has been misused as a result of the security breach, although it is hard to know how they would tell if it had been.
The firm has informed regulatory authorities, and is offering exposed customers complimentary access to 24 months worth of credit monitoring through Experian (although consumers will have to enroll for this, as it will not be be put in place automatically.) Enrollment for Lovesac customers remains open until November 28, 2025.
All users would be wise to remain vigilant to the signs of identity theft and fraud, keeping a close eye on account statements, and monitoring free credit reports for suspicious activity.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsYou might also like
Bookmarks
