What’s New in GravityZone November 2025 (v 6.68)

During November 2025, Bitdefender rolled out new functionality in Bitdefender GravityZone, a unified cybersecurity platform that provides prevention, protection, detection, and response capabilities for organizations of all sizes. These features, consistent with our multi-layered security strategy, are intended to ease the workload of security analysts, administrators, and users.
What’s New For Security Analysts
In a dynamic cybersecurity landscape, security analysts are responsible for uncovering any signs of potential sophisticated attacks to make the invisible visible. This section describes new functionality designed to elevate the capabilities of analysts, offering enhanced tools for threat detection, investigation, and response.
Security Data Lake
Data silos and logs often exist in different formats across the IT infrastructure, making it difficult to detect advanced threats. To provide the unified, cross-platform visibility necessary for effective threat detection, we are introducing the Security Data Lake.
With the latest release, GravityZone Security Data Lake extends the unified Bitdefender platform by combining SIEM and data lake capabilities into a single cloud-delivered solution, consolidating visibility, analytics, and management. It is available as a standalone console and can be accessed directly from GravityZone, with a dedicated cluster per customer to ensure full data isolation and dedicated resources for your organization.
Security Data Lake is designed to collect and normalize event data from third-party tools, including firewalls, endpoints, cloud, and custom sources, into a consistent schema for correlation and analysis. It is delivered with ready-to-use packs for event detection, monitoring definitions, anomaly detection rules, and dashboards, providing security insights immediately. You can further customize log processing using Streams and Pipelines to build custom parsers and enrichment rules for unique log sources.
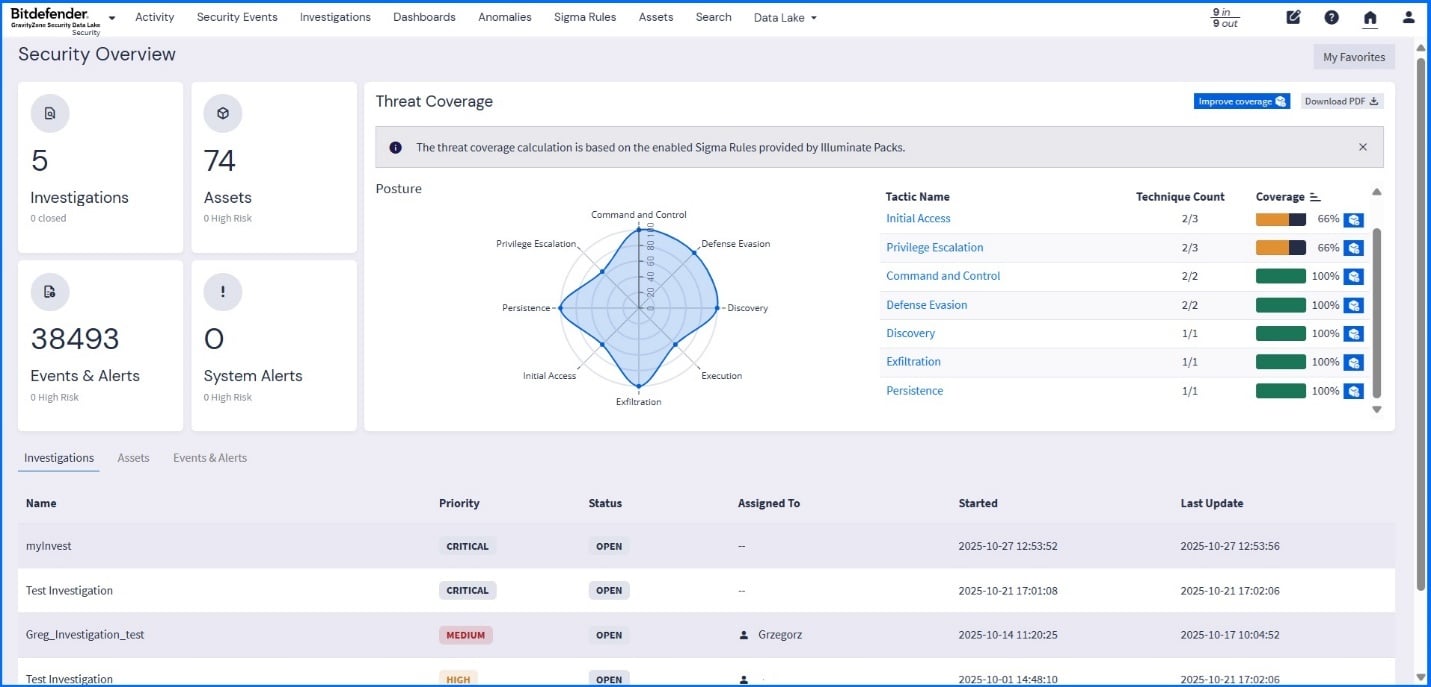 Security Data Lake provides unified, cross-platform visibility for proactive threat hunting, helping you accelerate your Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). It includes a correlation engine to connect isolated events into complete threat narratives, and advanced search with parameters for running and sharing complex queries.
Security Data Lake provides unified, cross-platform visibility for proactive threat hunting, helping you accelerate your Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). It includes a correlation engine to connect isolated events into complete threat narratives, and advanced search with parameters for running and sharing complex queries.
When integrated with our Managed Detection and Response (MDR) service, the Data Lake grants MDR SOC analysts access to this expanded third-party telemetry, including initial support for Palo Alto Networks, Check Point, Cisco ASA, Fortinet, Juniper, pfSense, and SonicWall firewalls.
This context allows the MDR team to run precise queries, correlate activity across the entire infrastructure, and identify threats earlier in the attack chain by reducing noise through risk-based prioritization.
For detailed information about the Security Data Lake solution, read Bring Every Signal Into Focus.
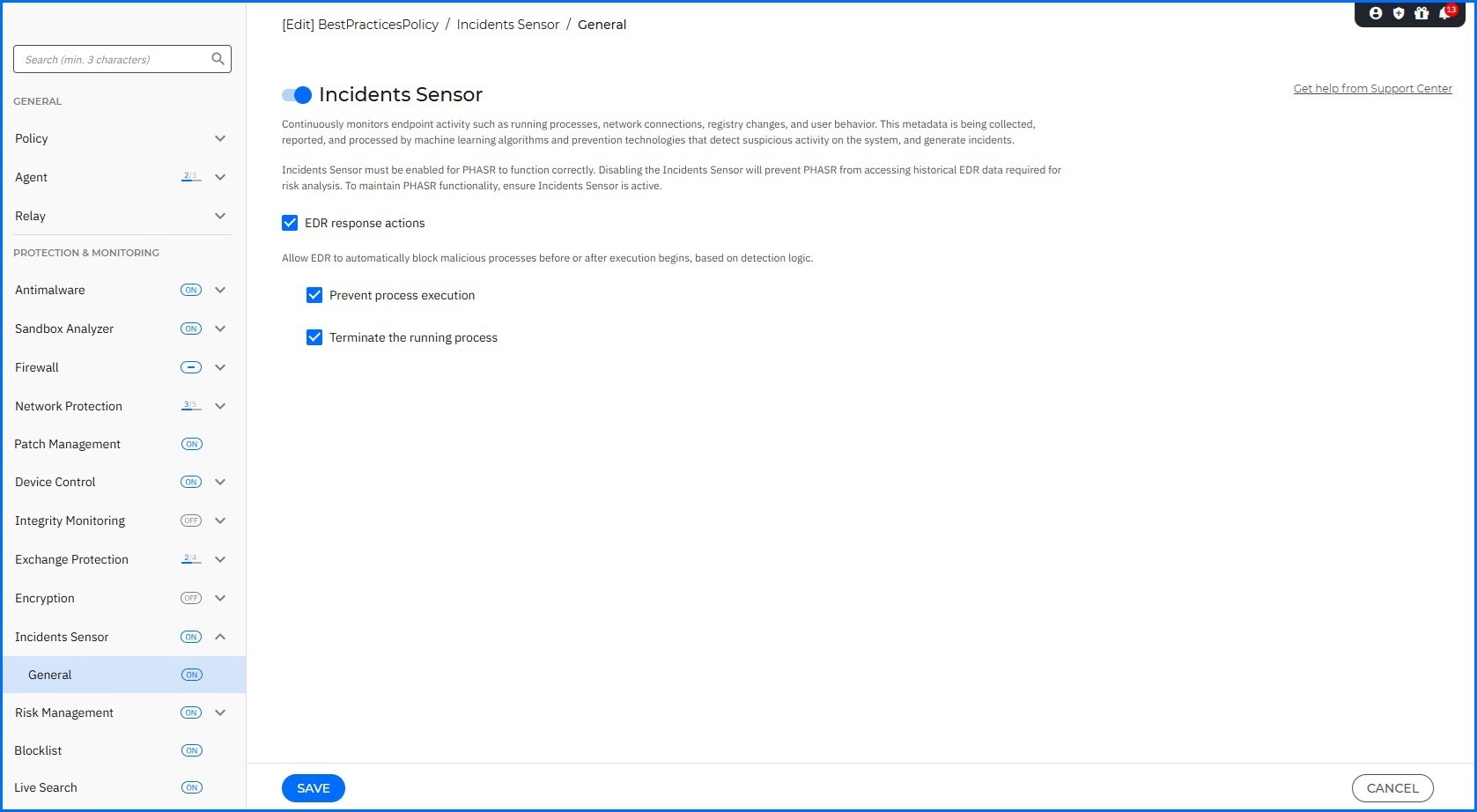
EDR Sensor Blocking Action
Endpoint Detection and Response (EDR) expands visibility for security analysts by gathering data from all endpoints. The correlation engine, together with anomaly detection, identifies incidents that manage to bypass prevention and protection technologies, often originating from unmanaged devices.
With the new release, the EDR Sensor has response actions. A response action is generated based on the correlation engine, which identifies relationships between events and consolidates them into incidents.
Imagine three events: an AD dump made with the ntdsutil system LOLbin, file archiving, and sending archival files across the network through SMB. With the correlation engine, these theoretically unrelated events are processed to identify relationships between them and consolidate them into a single incident that can be blocked.
You can activate EDR response action in the GravityZone Control Center under Policy > Incident Sensor configuration.
You can choose whether you want to Prevent process execution or Terminate the running process on Windows endpoints. All actions are visible and traceable in the Incidents grid and the Incident Response tab, as well as locally on the BEST agent.
 For comprehensive insights into EDR, we invite you to watch our masterclasses here.
For comprehensive insights into EDR, we invite you to watch our masterclasses here.
Office 365 Sensor Delete File Action
The Bitdefender GravityZone Office 365 Sensor integrates directly with Microsoft 365, utilizing Mail and Audit sensors to ingest data about email traffic, content, and all user/admin operations. It proactively identifies suspicious activity, empowering you to take immediate action via the GravityZone console.
With the current update, we extended the Office 365 Sensor response action, adding the possibility to perform the Delete file action in the alert details panel and in the Response tab of the Incident. This new action allows you to remove malicious or unwanted files directly from OneDrive and SharePoint Online. To activate this new action type, modify your existing Microsoft Entra application by adding the Files.ReadWrite.ALL permission.
Detailed information about Office 365 sensor configurations can be found at our Bitdefender Support Center here.
AWS Sensor Enhancements
The Bitdefender AWS Sensor monitors activity across your cloud environment by establishing a baseline of normal behavior to detect potential security compromises at any stage of the attack lifecycle. It proactively identifies suspicious activity, allowing for immediate response actions via the GravityZone console.
With the current release, the AWS Sensor supports AWS Control Tower environments, integrating with the Management and Log Archive accounts to enhance visibility and threat detection across all organization accounts. You can disable and remove access keys for a compromised IAM account only in the Management Account from the GravityZone Console via the alert details panel and in the Response tab of the Incident.
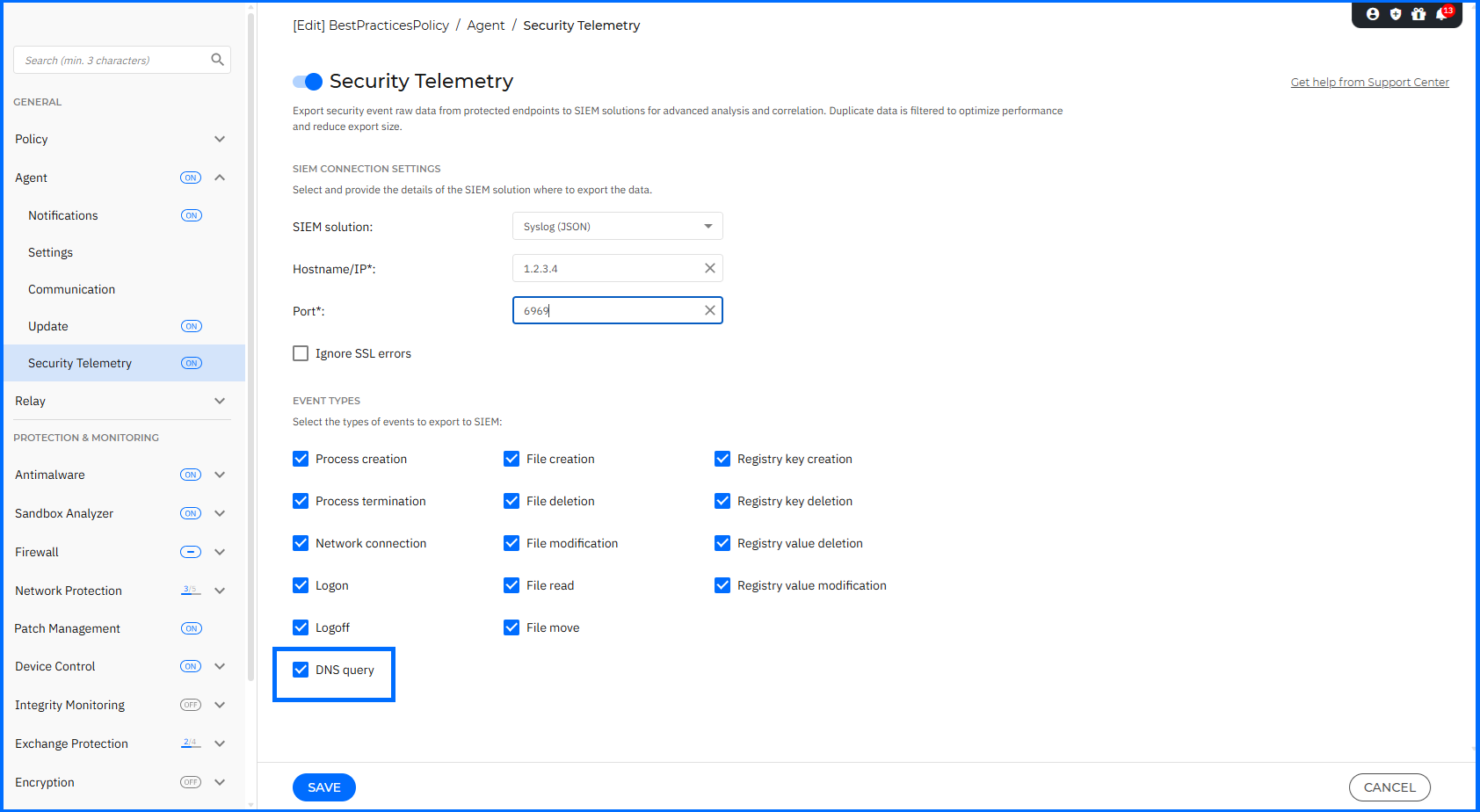
Security Telemetry Enhancements
Security Telemetry is the raw, detailed event data collected by endpoint sensors, including process activity, file operations, registry changes, user access, and network connections.
With this release, the Security Telemetry mechanism was enhanced to support collecting DNS queries. This telemetry can be sent to a 3rd party SIEM and MDR pipeline. It is supported on Windows and macOS. This telemetry can be correlated with other events to enable faster incident response and to comply with standards such as NIST or ISO 27001.
MDR New Licenses
Bitdefender's Managed Detection and Response (MDR) services provide 24/7 continuous threat monitoring and expert-driven incident response, essentially acting as your outsourced security department. MDR significantly augments your existing security capabilities by offering specialized expertise, around-the-clock coverage, and access to advanced threat intelligence.
With the latest release a two new yearly MDR licenses are now available:
- Bitdefender MXDR: Includes all features from the Bitdefender MDR license with functionality provided by Bitdefender XDR Sensors: Productivity, Identity, and Network. The MDR Cybersecurity Breach Warranty is available as an add-on
- Bitdefender MXDR Plus: Includes all features from the Bitdefender MDR Plus license with functionality provided by Bitdefender XDR Sensors: Productivity, Identity, and Network. The MDR Cybersecurity Breach Warranty Plus is available as an add-on
Both licenses can be assigned to customers when creating or updating a company. When Bitdefender MXDR or Bitdefender MXDR Plus is removed from a customer, the Breach Warranty add-on, if present, will also be automatically removed.
For comprehensive insights into MDR we invite you to watch our masterclasses here.
API Enhancements
Bitdefender Control Center APIs enable developers to automate business workflows. These APIs are exposed via the JSON-RPC 2.0 protocol, and you can find usage examples and documentation in our Support Center, here.
With this release, the API has been enhanced with the following updates:
- The incidentsSensor.general.incidentsSensor.preExecution and incidentsSensor.general.incidentsSensor.postExecution parameters are now available for the setPolicyModulesState method. These parameters make it possible to enable or disable the settings available in the EDR Response actions policy section.
- The contentControl attribute under the settings object returned by the getPolicyDetails method now includes information about the policy’s Custom Pages configuration.
Following the Office 365 sensor enhancements, we have updated the Incidents API to support file deletion actions:
- The type attribute returned by the getResponseActionStatus method now returns a new value: 10 - delete an Office 365 file
- The actionType parameter used in the createResponseAction method now has a new possible value: 10 - delete an Office 365 file
For comprehensive insights into automating workflows with the Control Center API, we invite you to watch our masterclasses here.
Bitdefender Threat Intelligence for Splunk
Bitdefender Threat Intelligence processes massive quantities of Indicators of Compromise (IoCs) in real-time from multiple sources including live systems in our Bitdefender Global Protective Network (GPN). This network safeguards hundreds of millions of systems, consumer devices, the technology of licensing partners from the OEM ecosystem, and more, processing an astounding 50 billion daily threat queries from these systems.
The latest update introduces Bitdefender Threat Intelligence for Splunk v1.1.0, which provides seamless integration with your Splunk environment, enhancing your existing security information and event management capabilities.
The solution includes:
- Real-time ingestion of IoCs (domains, IPs, URLs, file hashes, CVEs)
- Actor and malware family attribution correlated to IoC
- Confidence and severity scoring for prioritization
Prebuild dashboards, such as Operational Feeds Overview, Operational Feed Details, Reputation Feed Details, and Correlation Alerts, provide immediate context on active threats. Furthermore, integration with Splunk Enterprise Security allows you to create custom correlation searches and alerts, enabling faster incident response.
What’s new for Administrators
With administrators constantly juggling numerous tasks and responsibilities, tools that make their daily work easier are highly appreciated. This section describes new functionality designed to facilitate the management of features responsible for prevention, protection, and detection in a defense-in-depth security architecture.
Custom Pages for Block and Warn Messages
GravityZone Web Content Filtering allows you to control which websites your users are allowed and not allowed to visit by scanning both HTTP and HTTPS (after enabling Intercept Encrypted Traffic).
With the latest release, you can configure your own block web page that is displayed when an end-user is accessing blocked web content, and a warning message in the BEST agent.
Start the configuration by adding your custom page in the Configuration Policies section under the main menu in the WAC Custom Pages tab. You can add your own logo and modify the block message in the web browser, as well as the warning information on the BEST agent. All the links included on the block page are not clickable for the users. The custom page can be assigned to a Policy in the Network Protection > Custom Page section.
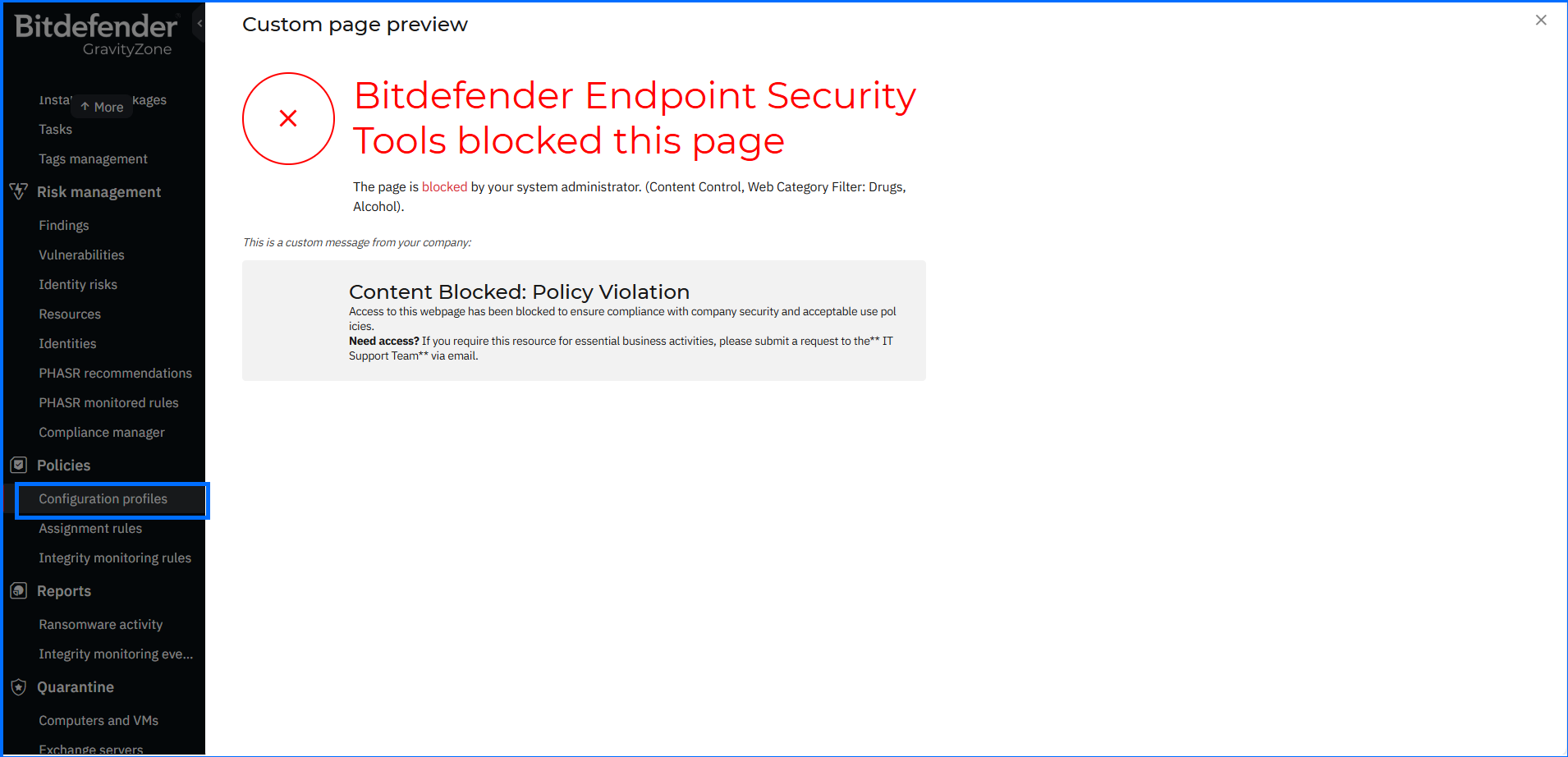
All the modifications taken in the configuration can be reviewed in User Activity as a Web Access Content Control Pages action
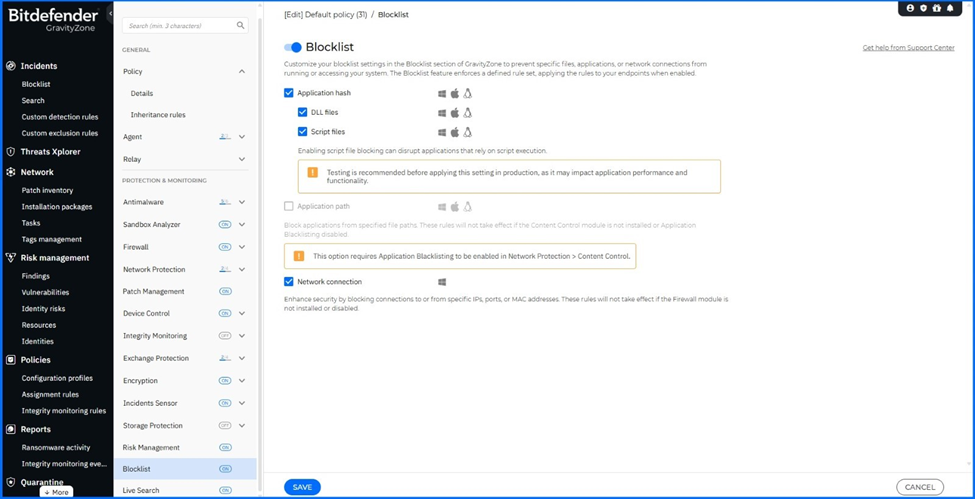
Blocklist Enhancements
The Blocklist functionality allows you to create rules to prevent specific files, applications, or network connections from executing on or reaching your systems.
The Firewall module no longer needs to be explicitly enabled in the policy. When using only Blocklist, the Firewall now runs in a lightweight mode that supports this functionality without overriding or interfering with the Firewall’s full behavior.
With the current release, Blocklist is automatically enabled as a service prerequisite for all MDR-managed endpoints, overriding any policy setting. The DLL and Script options remain configurable for local administrators.
Summary
Bitdefender GravityZone platform stands out from the crowd, offering a unified solution for all your organization's security needs. As the digital landscape evolves, Bitdefender remains proactive, providing prevention, protection, detection, and response capabilities to ensure the ongoing safety of organizations of all sizes worldwide.
To learn more about the Bitdefender GravityZone platform, contact us or a Bitdefender partner for more information. You can also start a free trial by requesting a demo here.
tags
Author
Grzegorz Nocon is a graduate of the Faculty of Physics at the University of Silesia. With over 16 years of experience in the IT industry, he currently works as a Technical Marketing Engineer at Bitdefender. A strong supporter of a holistic approach to security and passionate about solving security problems in a comprehensive and integrated way. Outside of work, an avid CrossFit enthusiast and a lover of fantasy literature.
View all postsYou might also like
Bookmarks

