What Cyber Threats Do Mac Users Face in 2022?

It’s no lie that Apple customers have something of a protective veil versus Windows users. But a misconception lies at the center of this argument. It’s not that Macs are inherently more secure against cyber threats. Rather, it’s that bad actors concentrate more on targeting the much larger, more-fruitful Windows ecosystem. In fact, this difference sometimes means Mac-specific threats can be better optimized to achieve their goals.
Social engineering

Malware aside, social engineering is equally successful in campaigns targeting all platforms, including macOS. And with so many Mac users leaving their guard down due to the apparent safety net provided by an Apple product, they sometimes end up even more vulnerable than their Windows counterparts. And many of these scams actually impersonate the mother ship in Cupertino, California.
Social engineering scams targeting Mac users include:
· Fraudulent emails and other messages that look like they're from legitimate companies, including Apple
· Misleading pop-ups and ads that say your device has a security problem, inviting you to download malware
· Scam phone calls or voicemails that impersonate Apple Support, or other companies’ help desks
· Too-good-to-be true promotions that offer free products and prizes
· Unwanted calendar invitations and/or subscriptions
Watch out for these telltale scenarios and always use two-factor authentication to protect your Apple/iCloud account. Consider running a security solution too, for complete protection against the bad guys.
Malicious browser plugins/extensions

Also in the platform-agnostic department are browser threats. Specifically, malicious browser plugins or extensions. Browser add-ons are extremely useful and convenient, but they are also a lucrative attack vector.
Even though Macs come pre-loaded with the highly-polished Safari browser, many customers still prefer Google’s popular Chrome.
While browser extensions are typically vetted before they get accepted into Chrome’s Web Store, sometimes the developer ends up selling the product to a different party, who may have different intentions for that already-vetted product. And the auto-update feature will quickly install whatever intentions that new vendor has.
Extensions can also be hijacked to deploy malicious code onto trusting users. Especially popular plugins, like Chris Pederick’s Web Developer for Chrome extension. In 2017, bad actors managed to hijack the plugin, injected ads into users’ browsers, and ran malicious JavaScript code.
In this scenario, an attacker can run pretty much anything on your system, from coin miners to data-stealing malware.
Browser extensions are also commonly fielded to collect user data to sell to marketers. Data brokers have a bad reputation, to say the least, as they are almost never 100% compliant with data protection laws.
Use as few extensions as possible and carefully examine what each of them does and what data they collect before you hit install. Do away with extensions you no longer use. Don’t let them linger on your system collecting data behind your back.
Trojans

With about 15% of the desktop market, Apple’s Mac operating system has a large enough share to attract cybercriminal groups.
Unlike Windows, which dominates the desktop market and faces a plethora of malware threats, the macOS environment enjoys less variance in terms of malware. However, this doesn’t make Macs less vulnerable. The gap between these two ecosystems means that malware tailored to Macs is actually better suited to its goals.
Trojans, disguised as legitimate programs designed to give attackers access to the target system, constitute the biggest single threat facing macOS, with a 48% share. Potentially Unwanted Applications (PUAs) make up 30% of the threats targeting Macs, followed by Adware with a 14% share, and CoinMiners, with 7%.
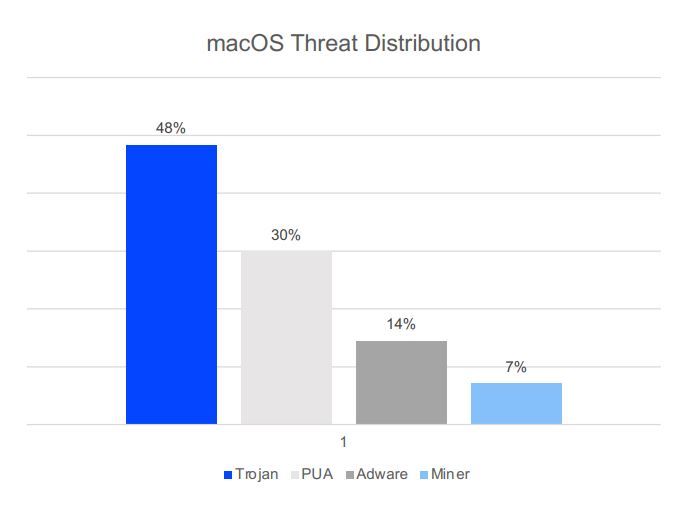
Attackers find it easy to sneak a Trojan onto a victim’s computer, as most Trojans look and act like legitimate applications. In fact, PUAs and Trojans share many similar traits as far as antivirus detections go (more on this below).
Attackers deliver the malware through social engineering techniques like spam and phishing or via infected websites and scams leveraging the victim’s favorite social networks. Trojans also infect many Macs through warez and torrent sites – hotbeds for pirated downloads.
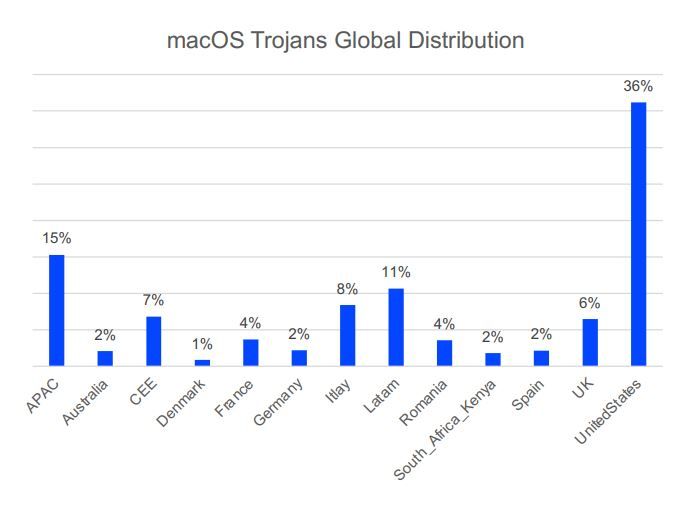
Trojans harbor many sub-threats, including the occasional ransomware, like the infamous ThiefQuest.
Many shady apps classified as PUAs actually stem from Trojan infections. Not surprisingly, Trojan activity closely matches PUA activity when we track the two threats side by side across the Mac install base over a 12-month period, as the charts below show.
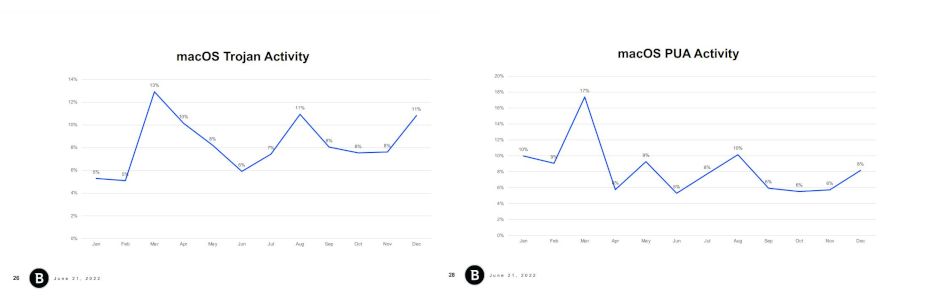
One could conclude that the two threats combined make for a larger share of malware designed specifically to infect Macs. But since it’s hard to determine the exact number, we’ll leave speculation aside.
Looking at two years’ worth of Trojan detections across the Mac user base yields an interesting trend. 2020 accounted for 39% of all attempted Trojan infections globally, while 2021 accounted for the remaining 61%.
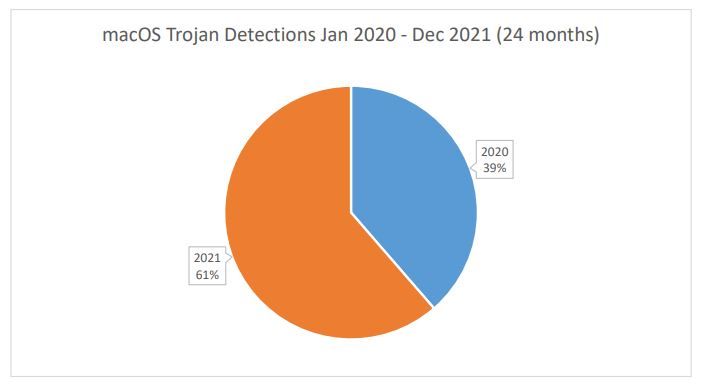
This marks a 56% increase in Trojan activity from one year to the next.
In conclusion, malware-wielding cybercriminals are clearly investing more time and effort to target consumers with malicious code that runs natively on Macs. It’s becoming increasingly important for users to run a dedicated antivirus/security solution on their Apple computers.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








