Essential Guide to Mobile and Security | Protect Your Devices Today

Mobile and security are not separate conversations. In 2025, your smartphone is your wallet, your inbox, your photo library, and in many cases, your access pass to every app, service, and system you rely on. That makes it both your most essential tool and your biggest vulnerability.
As mobile security threats have grown into fast, quiet, and increasingly automated attacks, the need to protect your digital footprint did too.
One careless tap on a phishing link, one download from the wrong app store, or one public Wi-Fi session without protection is all it takes to expose your sensitive data, compromise your accounts, or give attackers a foothold into your personal devices or business network.
So, in this guide, we’ll break down:
- What makes your mobile device a prime target
- How attackers exploit gaps in device security
- How to protect your phone with simple actions
- Where tools like mobile device management (MDM) and endpoint protection fit in
Let’s get into it.
Mobile device security – "nice to have" or necessity?
In 2025, assuming your phone is safe because it’s “just a phone” is a luxury no one can afford. A single compromised phone can become a gateway into your organization’s network or a gateway to exposing your personal data privacy. Think critical systems, cloud apps, and internal communications – they're all exposed.
Modern smartphones are always connected, location-aware, and frequently trusted with sensitive data including:
- Biometrics
- Payment credentials
- Business communications
- Access to cloud-based platforms
This makes them prime targets for increasingly sophisticated mobile security threats. So, is mobile security important? Yes!
From text message phishing to rogue apps sideloaded outside official app stores, attackers exploit mobile operating system gaps, insecure Wi-Fi networks, and poor device security hygiene. A single compromised phone can act as a listening device, a lateral attack vector into corporate infrastructure, or a source of leaked private information.
Worse still, because mobile breaches often go undetected, attackers have longer dwell time, which creates an ideal environment for them to breach your data security parameters without triggering alarms.
Mobile device security threats to watch out for
Mobile threats are always on the rise. To protect your data and privacy, here’s what you need to know, and exactly what to do about it.
Phishing scams – deceptive attacks that target your trust
Phishing attacks trick you into revealing sensitive information, like:
- Passwords
- Financial data
- Personal credentials
By posing as trusted sources via email, SMS, or messaging apps, phishing scams can get to you in no time.
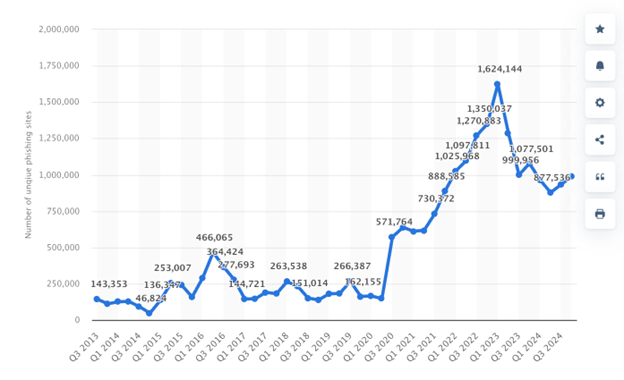
From 2013 to 2024, phishing incidents surged significantly, with a notable decline in recent quarters. While hackers are nowhere close to stopping, they might be looking for more advanced cyber attacks and online scams other than phishing, to trick savvier mobile users.
How to protect yourself from phishing:
- Verify unexpected messages and links instantly using Scamio, which detects and flags suspicious URLs and SMS messages.
- Make sure web protection is activated through Bitdefender Mobile Security to block malicious sites before they load.
- Train yourself to spot phishing attempts. Check sender addresses carefully, avoid clicking unknown links, and directly contact institutions to confirm suspicious messages.
Malware – the invisible threats
Malware, AKA malicious software intentionally designed to damage devices, steal data, or gain unauthorized access, is on the rise. Common forms include ransomware, spyware, and banking Trojans.
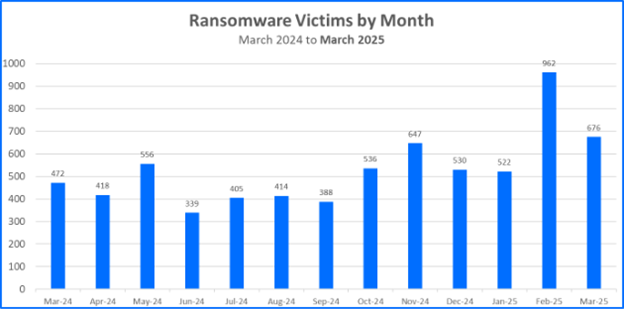
According to the April 2025 Bitdefender Threat Debrief, ransomware incidents claimed 676 victims just in March 2025 alone. Hackers get into your systems and install malware without you even realizing it, which makes this type of attack one of the most dangerous cyber threats for mobile apps.
Malware is driven by rogue apps posing as legitimate apps. Just recently, The Hunters International ransomware group (recently rebranded as World Leaks) claimed 41 victims at their peak in April 2024.
Despite publicly announcing shut-down due to law enforcement pressure, the group actively compromised 6 organizations in March 2025 by first stealing sensitive data (data exfiltration), encrypting it, and then demanding payment in exchange for decryption and data loss prevention.
How to protect yourself:
- Regularly scan your device using Bitdefender Mobile Security, which detects malware proactively and removes online threats in a timely manner (before damage occurs).
- Only download apps from vetted, official app stores (e.g., Google Play, Apple App Store). Avoid sideloading apps unless fully verified.
- Check permissions rigorously. Excessive permissions (e.g., camera access for a calculator app) are immediate red flags.
Man-in-the-Middle Attacks (MITM) are eavesdropping on your data
MITM attacks occur when cybercriminals intercept communications between your mobile device and another party via insecure Wi-Fi networks to steal sensitive information like login credentials or financial information.
Attackers set up rogue Wi-Fi networks in public places like airports and cafes. Unsuspecting users connect to these networks and fall victim to MITM attacks, meaning that their emails, passwords, and sensitive documents are intercepted
How to protect yourself:
- Always use a trusted virtual private network (VPN) whenever connecting to public or untrusted Wi-Fi networks. VPN encryption can neutralize MITM threats by encrypting your connection end-to-end.
- Disable automatic Wi-Fi internet connection settings on your devices to avoid unintentionally connecting to compromised networks.
- Monitor unusual activity or logins and use specialized security tools to receive instant alerts if your sensitive information appears in breaches or leaks.
Wi-Fi vulnerabilities are a silent backdoor killer
Public Wi-Fi hotspots or poorly secured networks are prime targets for attackers. Unencrypted data transmitted via insecure Wi-Fi is not too difficult to intercept, so it's easy for hackers to get in and expose everything from browsing history to sensitive login details.
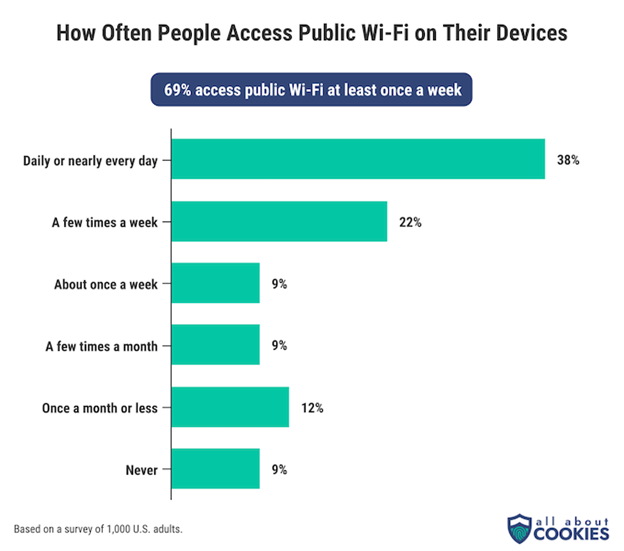
Reports suggest that one in four people experience security issues after connecting to poorly secured networks. Don't be one of them.
How to protect yourself:
- Activate VPN encryption every time you join public or open Wi-Fi networks.
- Don't access critical data, such as financial accounts or sensitive company information, on public Wi-Fi networks unless you have a secure VPN turned on.
- Regularly check network settings and remove remembered open Wi-Fi networks to prevent automatic reconnection risks.
Phishing via SMS (Smishing) is a threat living in your inbox
SMS-based phishing (smishing) campaigns lure you into clicking malicious links embedded in texts, which can compromise personal data or infect devices with malware.
How to protect yourself:
- Validate SMS links instantly through Bitdefender Scamio (our free AI-powered scam detection tool, available on WhatsApp too).
- Never share critical data via text or click on links from unknown senders, even if they seem urgent or official.
- Report suspicious SMS messages immediately to your mobile carrier and use spam filtering services.
Top strategies to consider if you want to boost your mobile security
If your phone holds your schedule, your business, your content, and your banking app, then it deserves more than screen locks and hope. Here are the actual strategies that you can implement today to combat mobile security threats.
1. Consider endpoint security (before someone else does)
Mobile devices are now full-fledged endpoints. That means they need the same level of protection as your laptop or server. Here's how to secure it:
- Install endpoint-grade protection like Bitdefender Mobile Security (for Android or IOS) to block malicious links, detect zero-day malware, and scan for threats in real time.
- Turn on web protection to stop phishing and fake login pages before they load.
- Run periodic scans to catch hidden or dormant threats.
2. Use MDM (mobile device management) like a pro
MDM systems aren't only for IT departments anymore. It’s a baseline for anyone managing multiple devices or if you need centralized control over your mobile environment.
MDM helps you keep up with security policies like complex passwords, OS-level encryption, and blocking unvetted apps. Plus, you can remotely wipe lost or stolen devices.
For growing teams or remote-first businesses, enterprise mobility management (EMM) is the next step beyond traditional device protection, as it gives you full control over how data moves across mobile endpoints, apps, and the operating systems of your network, which keeps your data safe from online threats.
3. Combat identity theft by assuming your info’s already out there
Your phone number, login credentials, and personal email are valuable assets in the hands of attackers. If they’ve been exposed once, they’ll likely be targeted again. Identity theft is on the rise, and given the rapid development of AI technology and its use in deepfakes, this scam is only growing in complexity.
“The thing about identity theft is it can have a very lasting effect. You cannot control the amount of damage it produces. However, you can mitigate it.
Many people do not realize their identity has been exposed until friends contact them, telling them they have been approached by scammers, which often happens with social network account hijacks or takeovers. Sometimes, people realize their identity has been abused when they apply for a loan for a new home or a new car and realize their credit score has plummeted.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
What to do about it:
- Use Bitdefender Identity Protection to scan for leaked personal info (emails, passwords, SSNs, etc.) across the dark web.
- Turn on breach alerts so you can act the moment your credentials are compromised.
- Change your passwords proactively and use password managers with 2FA (don't opt for an SMS, but rather an authenticator app as your second layer of protection. An SMS can be intercepted).
4. Fortify the device itself
Every layer of protection helps, from basic phone security settings to backup. Here's what to implement:
- Device encryption (this comes by default on newer iOS and Android, but check it's on).
- Secure boot and disable debug modes or developer options if you don’t need them.
- Back up data regularly and store it in encrypted environments (not just on cloud apps).
- Set lock screen timeouts, biometric logins, and long-form complex passwords.
5. Strengthen data protection like you’re running a bank
If your mobile device handles sensitive client data, contracts, photos, or documents, it needs enterprise-grade data safeguards. Here are some tactics to use:
- Turn on end-to-end encrypted messaging. Apps like WhatsApp have it on by default, while platforms like Facebook Messenger and Telegram require you to manually start a “Secret Chat” or “Secret Conversation” to turn it on.
- Always use HTTPS (Bitdefender’s web protection forces this).
- Apply access controls, so if someone picks up your phone, they shouldn’t get into your apps or cloud storage.
6. Email security is your top weapon
Email is the easiest way into your phone. One bad attachment, and it's game over. Here are some best practices to keep in mind:
- Never click links in emails you weren’t expecting, even from known senders.
- Use scam detection tools to flag suspicious attachments or fake sender domains.
- Configure your email client to use TLS encryption by default.
- Hover over or long-press on the sender’s name and links to reveal the actual email address or URL. If it looks off (extra characters, misspelled domains, or unfamiliar senders), delete it.
- Watch for urgency cues (“Act now,” “Account locked”). They’re classic phishing red flags designed to short-circuit your judgment.
- Use email preview tools (many mobile clients support this) to scan content safely before opening full messages or attachments.
Stay ahead of hackers with proactive security measures
Hackers thrive on inaction. The moment you delay an update, skip a scan, or click without checking, that’s their entry point. The good news is that you can shut that door fast. Here are some key takeaways to keep in mind to protect mobile devices:
- Mobile security threats are real, rising, and targeted. From phishing and malware to rogue apps and public Wi-Fi attacks, your phone is a prime target.
- Protection starts with awareness and ends with action. Secure your data with encrypted messaging, VPNs, identity monitoring, and smart app hygiene.
- Tools matter. Security doesn't mean installing one app and forgetting it. It means using an ecosystem that defends across every layer: device, data, identity, and network.
Take control with Bitdefender Mobile Security
Whether you’re managing personal devices or safeguarding your organization’s data, top mobile security measures help you stay ahead of common threats, not catch up to them.
Keep mobile device security threats at bay with:
- Real-time protection against phishing, scam links, and malicious apps
- Built-in VPN for secure browsing on any network
- Identity protection to alert you when your data is leaked or sold via data breaches
- Scam detection tools to verify suspicious texts, DMs, or emails received via email or social media sites
👉 Protect your phone like your digital footprint depends on it. Because it does.
tags
Author
The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsYou might also like
Bookmarks


