Oil & Gas Spearphishing Campaigns Drop Agent Tesla Spyware in Advance of Historic OPEC+ Deal

Bitdefender researchers have recently found spearphishing campaigns, either impersonating a well-known Egyptian engineering contractor or a shipment company, dropping the Agent Tesla spyware Trojan. The impersonated engineering contractor (Enppi – Engineering for Petroleum and Process Industries) has experience in onshore and offshore projects in oil and gas, with attackers abusing its reputation to target the energy industry in Malaysia, the United States, Iran, South Africa, Oman and Turkey, among others, based on Bitdefender telemetry. The second campaign, impersonating the shipment company, used legitimate information about a chemical/oil tanker, plus industry jargon, to make the email believable when targeting victims from the Philippines.
Oil & gas has been under tremendous stress in recent weeks, as the global COVID-19 pandemic lowered oil demand. Oil prices per barrel have dropped by more than half to the lowest since 2002. However, a disruptive dispute over oil production between Russia and Saudi Arabia ended with an agreement at the recent meeting between the OPEC+ alliance and the Group of 20 nations, aiming to slash oil production output and balance prices.
While the malware payload itself is not as sophisticated as those used in more advanced and targeted attacks, the fact that they’ve been orchestrated and executed during this time, and before the “historic OPEC+ deal”, suggests motivation and interest in knowing how specific countries plan to address the issue.
Cybercriminals are often opportunistic and leverage popular media topics in spearphishing campaigns that usually target large numbers of victims. However, we recently found a campaign that seems to specifically target the oil & gas sector, based on a telemetry spike on March 31st. Interestingly, the payload is a spyware Trojan that packs keylogging capabilities, and has not been associated with oil & gas spearphishing campaigns in the past.
The second campaign that impersonated a shipping company seems to have started on April 12 and targeted only a handful of shipping companies based in the Philippines over the course of two days.
Carefully Crafted Spearphishing
The spearphishing email mimics Egyptian state oil company Engineering for Petroleum and Process Industries (Enppi) and claims to invite the recipient to submit a bid for equipment and materials, as part of a project (Rosetta Sharing Facilities Project) on behalf of a well-known gas company (Burullus).
“Enppi is globally recognized as a major engineering, EPC main contractor, and management contractor, with decades of experience in onshore and offshore projects in the oil and gas, refining and petrochemical industries,” reads the legitimate company description from their website.
While the email does sound legitimate by having a bid submission deadline and even requesting a bid bond, the attached archives that should contain a list of requested materials and equipment, are rigged to drop the Agent Tesla spyware Trojan.

For extra context, the Rosetta Sharing Facilities Project is real, and linked to Enppi and Burullus. To someone in the oil & gas industry, who has knowledge about these projects, the email and the information within might seem sufficiently convincing to open the attachments.

This is not the first time the oil & gas industry is targeted with similar campaigns, as some were reported in 2017 and 2019, both using similarly constructed emails and delivering spyware such as the Remcos remote access Trojan.
However, these campaigns seem to deliver the Agent Tesla spyware Trojan instead, and beyond just the oil & gas sector, they also target other energy verticals that have been tagged as critical during this Coronavirus pandemic.
Analyzing the profile of the affected victims, we found them activating in oil & gas, charcoal processing, hydraulic plants, manufacturers of raw materials, and transporters of large merchandise.
Back to the campaign mentioned above, the two email attachments presented as .zip archives contain the same executable (B632FACEC1D71B03593F358F579C8D2F):
- BURULLUS “EPC WORKS FOR ROSETTA SHARING FACILITIES PROJECT.exe
- WEIR OIL & GAS PROJECT NO 4621-422-298-01-20.exe
However, our telemetry has indicated that the WEIR OIL & GAS PROJECT NO 4621-422-298-01-20.exe attachment was used only during this campaign and not in any previous one.
In the end, the executable will drop the Agent Tesla spyware (aa651c58050cddb948901eb277b49af2), which will collect sensitive information and different type of credentials and send them back to the command and control server smtp[:]//smtp.yandex.com:587.
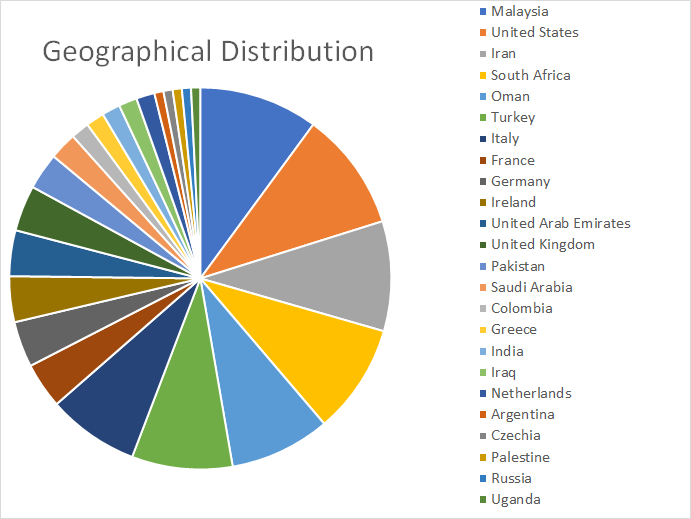
Based on Bitdefender telemetry, most of the reports involve Malaysia, Iran and the United States. These are all countries in which the oil & gas industry plays a significant role.
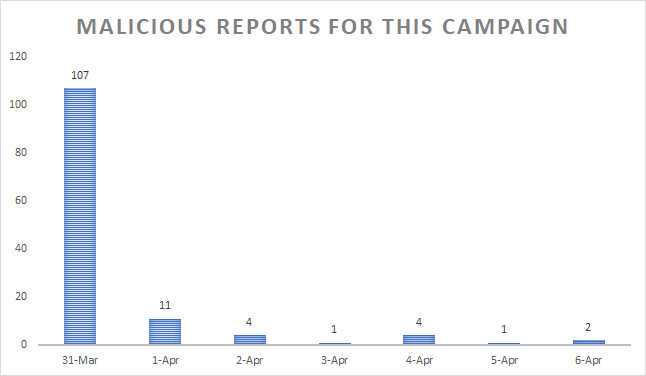
While the number of actual reports may seem low when compared to other spearphishing campaigns that take more of a shotgun approach, it’s likely whoever orchestrated it was really focused on the oil & gas vertical.
Most of the reports seem to involve Malaysia, the MENA region, and the United States. For example, the United States and Iran are among the top oil-producing countries in the world, which could hint at why oil & gas spearphishing campaigns might targeting them, especially during a global oil price drop caused by the COVID-19 pandemic.
Spearphishing with Legitimate Chemical/Oil Tanker Information and Jargon
While the March 31st event seemed isolated, only occurring for a single day, similar emails going after the same vertical and delivering the same Agent Tesla have been reported as of April 12. While the number of reports may be low, the construction of the messages and the jargon used do show the attackers have a clear understanding of their victim’s profile and use relevant language and information to seem believable and trick the victim into opening the rigged attachment.
The email below was sent on April 12 and seems to inform the recipient that he needs to send the Estimated Port Disbursement Account (EPDA) for the shipping vessel (MT.Sinar Maluku), as well as information about container flow management (referenced as “cfm” in the email).

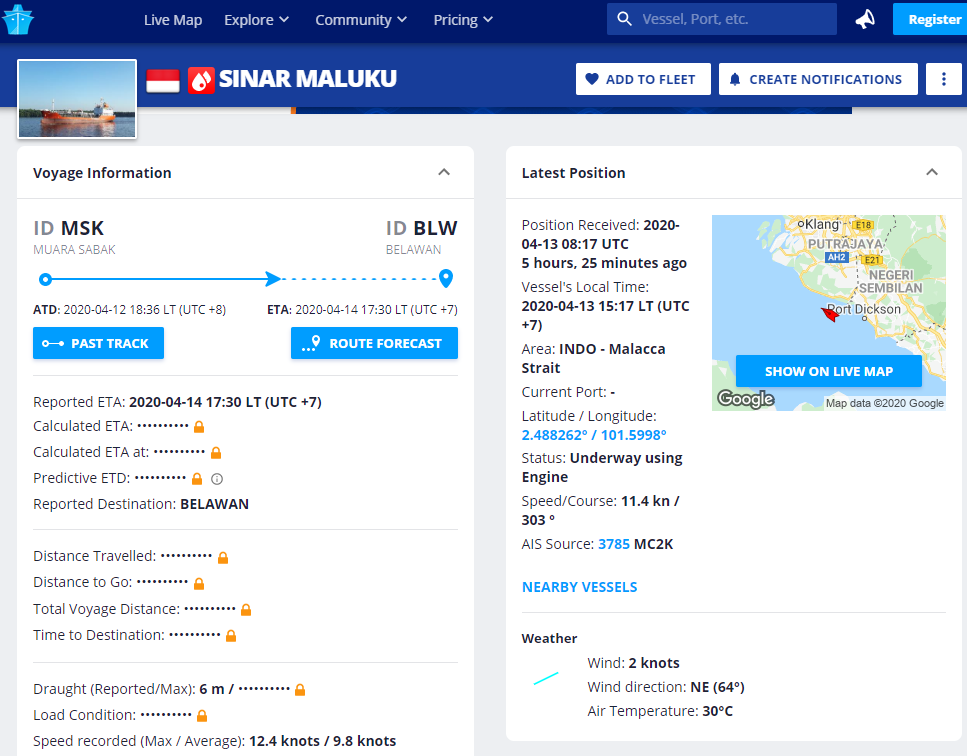
It just so happens that there actually is a Chemical/Oil tanker bearing that name, registered under the Indonesian flag, which had left port on April 12 and was expected to reach its destination on April 14.
Judging by all this information, it seems that while the number of reports coming from Bitdefender telemetry on April 13 might be low (a total of 18 reports, 15 of which from shipment companies in the Philippines), but it does point that this could be a highly targeted spearphishing campaign.
This email serves as another example of the lengths to which attackers will go to get their facts straight, make the email seem legitimate, and specifically target a vertical.
Global Evolution of cyberattacks in the Energy Industry
While the oil & gas segment might have been of particular interest to cybercriminals over the past couple of weeks, the number of malware reports targeting the energy industry has seen an increase in early 2020.
Starting October 2019, the global evolution of cyberattacks on the energy industry has steadily increased on a monthly basis, peaking in February 2020. With over 5,000 malicious reports from companies that operate in the energy industry, cybercriminals seem to have taken a keen interest in this vertical, perhaps as it has become more important and strategic after recent oil price fluctuations.
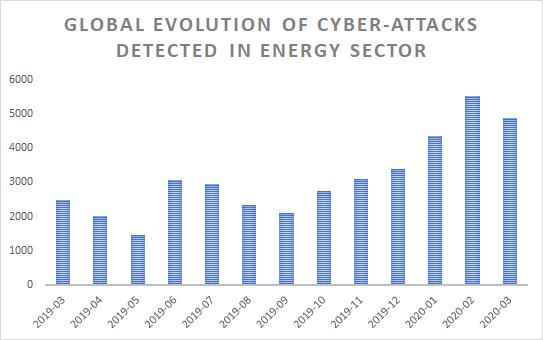
In terms of countries targeted by cyberattacks on companies that operate in the energy industry, the United States and the United Kingdom by far take the lead, with Ukraine coming in a distant third.
This Bitdefender telemetry is based on unique IP addresses that belong to organizations in the energy industry.
The Agent Tesla Spyware
The Agent Tesla spyware Trojan has reportedly been around since 2014, but has undergone constant improvements and updates. It reportedly operates under a malware-as-a-service offering, with its developers offering various pricing tiers based on different licensing models. Agent Tesla operators seem to have stayed in business for quite some time
Some of its most known and popular capabilities involve stealth, persistence and security evasion techniques that ultimately enable it to extract credentials, copy clipboard data, perform screen captures, form-grabbing, and keylogging functionality, and even collect credentials for a variety of installed applications.
Security researchers have already documented the full extent of Agent Tesla’s capabilities in various pieces of research. What’s interesting is that, until now, it has not been associated with campaigns targeting the oil & gas vertical.
Indicators of Compromise (IoC)
Below, is a list of indicators of compromise for both analyzed spearphishing campaigns.
ENPPI Campaign
Hashes: 0f67d58cb68cf3c5f95308f2542df6ff2e9444dc3efe9dd99dc24ab0f48a4756 bcb75af86d50b3dec7c1d603f2a7b9ba06eb0ce0cdf3a310b71a2c8e6c4aca29 Filenames: BURULLUS “EPC WORKS FOR ROSETTA SHARING FACILITIES PROJECT.exe WEIR OIL & GAS PROJECT NO 4621-422-298-01-20.exe C&C servers: smtp://smtp.yandex.com
Chemical/Oil Tanker campaign
Hashes: c25df2651a747220690ee62f23e4246ce37765ec5d1ef624f156af3f0f14041b 315f9a2dd00607c135498821f573414c80e52619f2faa8e2715162d318939f35 689e10eed6804131422d026781776edeaec42d42a35b65512d70acbc3631946b 9b915d2e5f70b859d8c2eafc94bd593d3e53255444a5b4b651dfb9c2523d83d7 Filenames: MT_Sinar Maluku V.04.exe vSVBfSw.exe.orig C&C servers: smtp://mail.besco.com.sa smtp://mail.shivanilocks.com smtp://mail.waman.in
Note: This article is based on technical information provided courtesy of Bitdefender Labs teams.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks














