Bitdefender Tops the Latest AV-Comparatives Advanced Threat Protection Test

As the growth and complexity of cyberattacks increase, it’s more important than ever for organizations to employ the tools necessary to keep threat actors at bay. Bitdefender has once again proven its excellence in this area, surpassing all other vendors in the AV-Comparatives Advanced Threat Protection tests for both the enterprise and consumer markets. These results support the outcomes organizations and individuals will experience with Bitdefender. This was also demonstrated by our position as a "Leader" in the latest Forrester Wave Endpoint Security Evaluations – where Bitdefender was recognized for its effective prevention capabilities.
This article explores the latest AV-Comparatives results which speak to how Bitdefender's superior protection safeguards businesses from emerging cyber threats.
The Significance of the Tests
This year’s AV-Comparatives Advanced Threat Protection (ATP) test used the tactics, techniques and procedures (TTPs) which reflect the strategies attackers employ. These TTPs are used by cybercriminals to both gain unauthorized access to an organization’s network and remain undetected for as long as possible. Attackers, often state-sponsored or highly organized criminal entities, use a combination of methods such as social engineering, zero-day vulnerabilities, and malware to infiltrate networks. Once a foothold is established, attackers expand their footprint by using lateral movement across the network. Often, they maintain continuous access with backdoor command and control (C&C) over encrypted channels which can also be used to carefully and quietly exfiltrate data.
The success of these types of attacks often involves the threat actors exploiting vulnerabilities in software that is typically found within organizations; an attack technique typically known as living off the land. By leveraging these native or in situ resources, such as PowerShell, Windows APIs, or legitimate system processes, the attackers minimize the need to introduce conspicuous software which could risk identification of malicious activity. This makes it much more challenging for traditional security tools to identify and mitigate the threat since the activity appears to be routine operations conducted by authorized users. As this testing demonstrates, not all security solutions have the capability of detecting intrusions into legitimate software, but all eight vendors evaluated in these tests showed at least some degree of efficacy in doing so.
The relevance of the tests cannot be understated as companies of all sizes struggle to recover from devastating data breaches that are conducted using APT techniques. The average cost of breaches has risen to an astonishing $4.35 million.
The Test Methodology
AV-Comparatives performed a total of 15 different attacks that reflect the MITRE ATT&CK® framework and are analyzed using the kill chain established by Lockheed Martin's Cybersecurity Kill Chain. All fifteen attacks were performed against fully patched Windows 10 64bit systems. We suspect AV-Comparatives used Windows 10 systems and not Windows 11, as Windows 10 still represents the largest market share of operating systems.
To perform the tests, AV-Comparatives used a variety of scenarios to deliver the malicious payload. These scenarios included spear-phishing techniques, access through stolen credentials, infected removable media, and exploits involving trusted relationships. Each of these techniques mirror the initial access vectors that are typical in modern security breaches. Business Email Compromise attacks, for example – which habitually involve spear-phishing – have more than doubled in the past year.
Once initial access was achieved, AV-Comparatives used fileless attacks to compromise the security of the target system. AV-Comparatives states in the report “Since 2017, a significant increase in fileless threats has been recorded.” What makes these types of attacks particularly effective is that they run exclusively in memory, making it difficult for many security solutions to identify and thwart. Some of the ways fileless attacks manifest includes:
- Malicious scripts: Using browsers or Microsoft Office macros, threat actors trigger malicious VBS or JavaScript to install backdoors on the target system.
- Exploiting operating-system tools: By hijacking built-in Windows tools like PowerShell, WMI, and Task Scheduler attackers compromise the security of the organization to establish persistence.
- Manipulating common communications protocols: Using HTTP/HTTPS, and TCP, threat actors establish command-and-control connections to use command-line stacks, CMD/PS commands, to download malware directly into a system’s RAM.
All these fileless methods completely circumvent the need for writing to disk. The threat actor completely avoids detection by security tools which lack the ability to identify fileless attacks.
On the enterprise side, eight vendors were evaluated. They included Bitdefender, Avast, CrowdStrike, Eset, Gdata, Kaspersky, Vipre, and VMware. On the consumer side, seven vendors participated: Avast, AVG, Avira, Bitdefender, ESET, Gdata, and Kaspersky. The goal of the tests is to demonstrate the prevention capabilities of each vendor’s product, and their capacity to defeat attacks at different stages. False alarms were also tested to evaluate each vendor’s ability to detect genuine attacks while not interfering with legitimate processes.
The Test Results
Of the vendors evaluated, Bitdefender was the clear winner in both the enterprise and consumer results. While no vendor achieved a perfect score on both tests, Bitdefender was the only vendor to block 14 of the 15 attacks. Bitdefender achieved these results without the Hyperdetect feature enabled – a tunable Machine Learning engine which aggressively detects previously unknown malware.
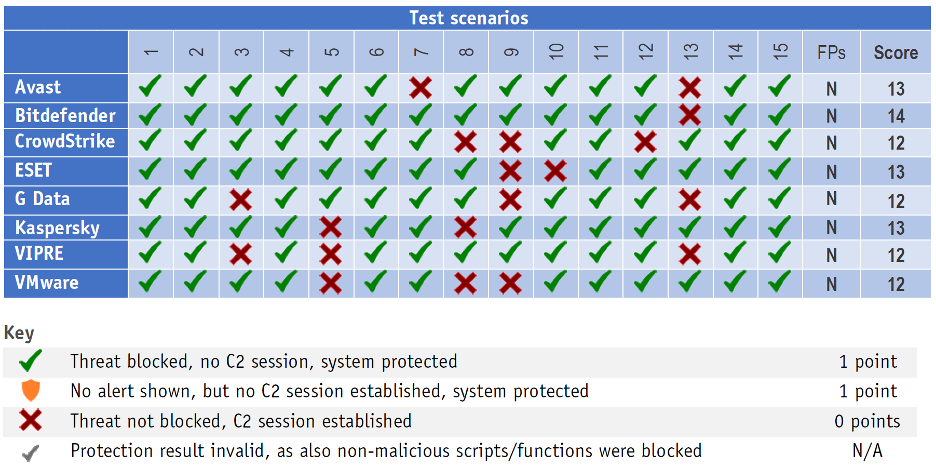
Figure 1: On the Enterprise tests, eight vendors were evaluated and only Bitdefender was able to block 14 of the 15 attacks.
More importantly, Bitdefender blocked the attacks more often than any other vendor at the pre-execution stage. This means Bitdefender defeated attacks before they could activate any part of their malicious payload. By doing so, Bitdefender significantly reduced the risk of data loss, system compromise, or operational disruption. This preemptive approach protects critical assets at the outset and minimizes the need for costly and time-consuming remediation efforts that would be necessary if an attack were to proceed undetected. As AV-Comparatives themselves succinctly put it, “A good burglar alarm should go off as soon as someone breaks into your home. It should not wait until they start stealing.”
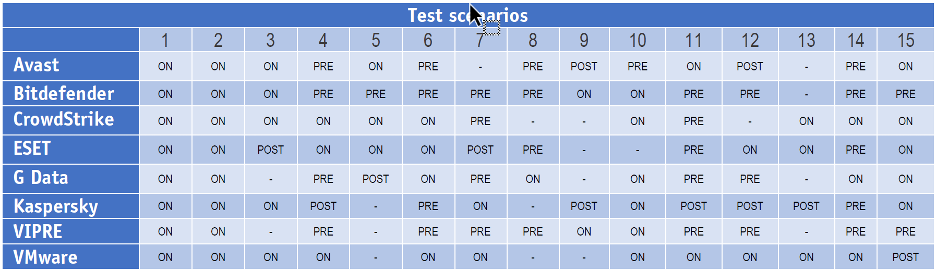
Figure 2: Bitdefender stopped the attacks at the pre-execution stage 9 times out of 15, the highest among all vendors.
Beyond the test results, the fact that Bitdefender excelled in both the enterprise and consumer markets should not be understated. The digital transformation has given rise to the era of hybrid work, and all the nuances of this arrangement have not gone unnoticed by cybercriminals. Threat actors have their sites focused on both employees and high-ranking individuals within organizations, and they are keen to pull the trigger using any available method to gain access to work and non-work systems alike. Around 70% of the incidents the Bitdefender MDR team investigates originate from unmanaged devices. As AV-Comparatives observes, “Attacking the home computers of businesspeople is also an obvious route into accessing their company data."
Conclusion
As 2023 unfolded, we witnessed an alarming surge in both the sophistication and frequency of cyberthreats. These threats have posed more significant risks and have incurred higher costs for organizations around the world. The emergence of cloud computing, hybrid work, AI, and increased reliance on trusted relationships has increased the attack surface of organizations. The consequences of a security breach are also more devastating than ever.
As organizations accelerate along this sometimes-precarious digital path, Bitdefender results of achieving the highest marks in AV-Comparatives Advanced Threat Protection tests for both enterprise and consumer segments is not just commendable for a security vendor—it's essential for the security of organizations which put their trust in Bitdefender. Our unwavering and proven capability to defeat attacks before they do harm sets us apart. We compliment this powerful prevention with world-class detection and response capabilities, proactive security services, and industry-leading threat intelligence in a consolidated platform. Organizations which are serious about security have a single answer to the question, “How do we best protect ourselves from modern cyber-threats?” The answer is Bitdefender.
tags
Author

My name is Richard De La Torre. I’m a Technical Marketing Manager with Bitdefender. I’ve worked in IT for over 30 years and Cybersecurity for almost a decade. As an avid fan of history I’m fascinated by the impact technology has had and will continue to have on the progress of the human race. I’m a former martial arts instructor and continue to be a huge fan of NBA basketball. I love to travel and have a passion for experiencing new places and cultures.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











