How to Check if Your iPhone Has Been Hacked [+5 Recovery Steps]
![How to Check if Your iPhone Has Been Hacked [+5 Recovery Steps] How to Check if Your iPhone Has Been Hacked [+5 Recovery Steps]](https://blogapp.bitdefender.com/hotforsecurity/content/images/size/w600/2025/10/How-to-Check-if-Your-iPhone-Has-Been-Hacked.png)
f you’ve typed “your iPhone has been hacked” into a search bar, we get it – you’re already in crisis mode. While Apple’s ecosystem is built on strong security foundations and even includes threat notifications, no device remains impervious.
If you’re here to find clear answers on how to detect if your iPhone truly is compromised, what recovery actions to take, and how to prevent future threats, let's begin.
7 signs your iPhone has been hacked & how to verify it
If you suspect your iPhone is hacked, check it against these seven common traits below.
1. Your battery life is dropping fast or overheating
Battery analytics is where an intrusion can reveal itself, as malware runs continuous background processes like:
- Data exfiltration
- Using location tracking
- Accessing the iPhone's microphone
All of which are invisible at the surface but energy-intensive. So, when a mobile device warms up or drains fast even at rest, treat it as a signal of unauthorized workloads.
How to check for battery usage
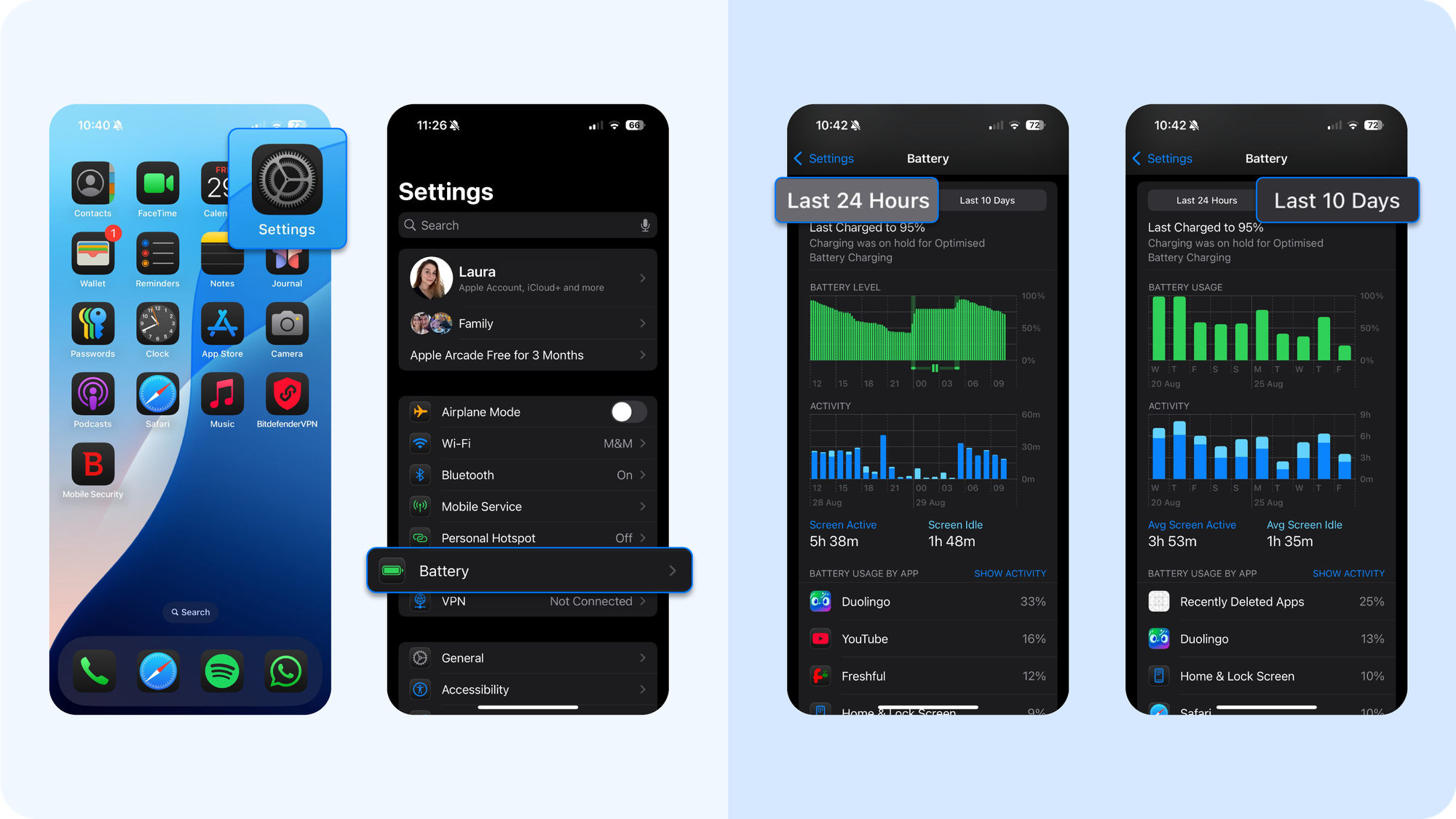
- Go to Settings > Battery
- Review Battery Usage by App for the last 24 hours and 10 days
- Look for apps consuming energy without active screen time or unfamiliar apps you don’t recall installing from the Apple store
Battery drain is a classic indicator because Apple tightly regulates resource use in iOS. Legitimate apps are sandboxed and suspended in the background; however, spyware has to circumvent this, which makes its footprint visible in analytics.
2. You have huge data usage spikes
Exfiltrating stolen data requires bandwidth. Think of photos, location history, or message logs – once malicious apps gain access to them, the upload goes silently, but internet traffic might still reveal it. A sudden jump in cellular or Wi-Fi consumption, especially when your habits haven’t changed, is a measurable red flag.
How to check for unusual data usage
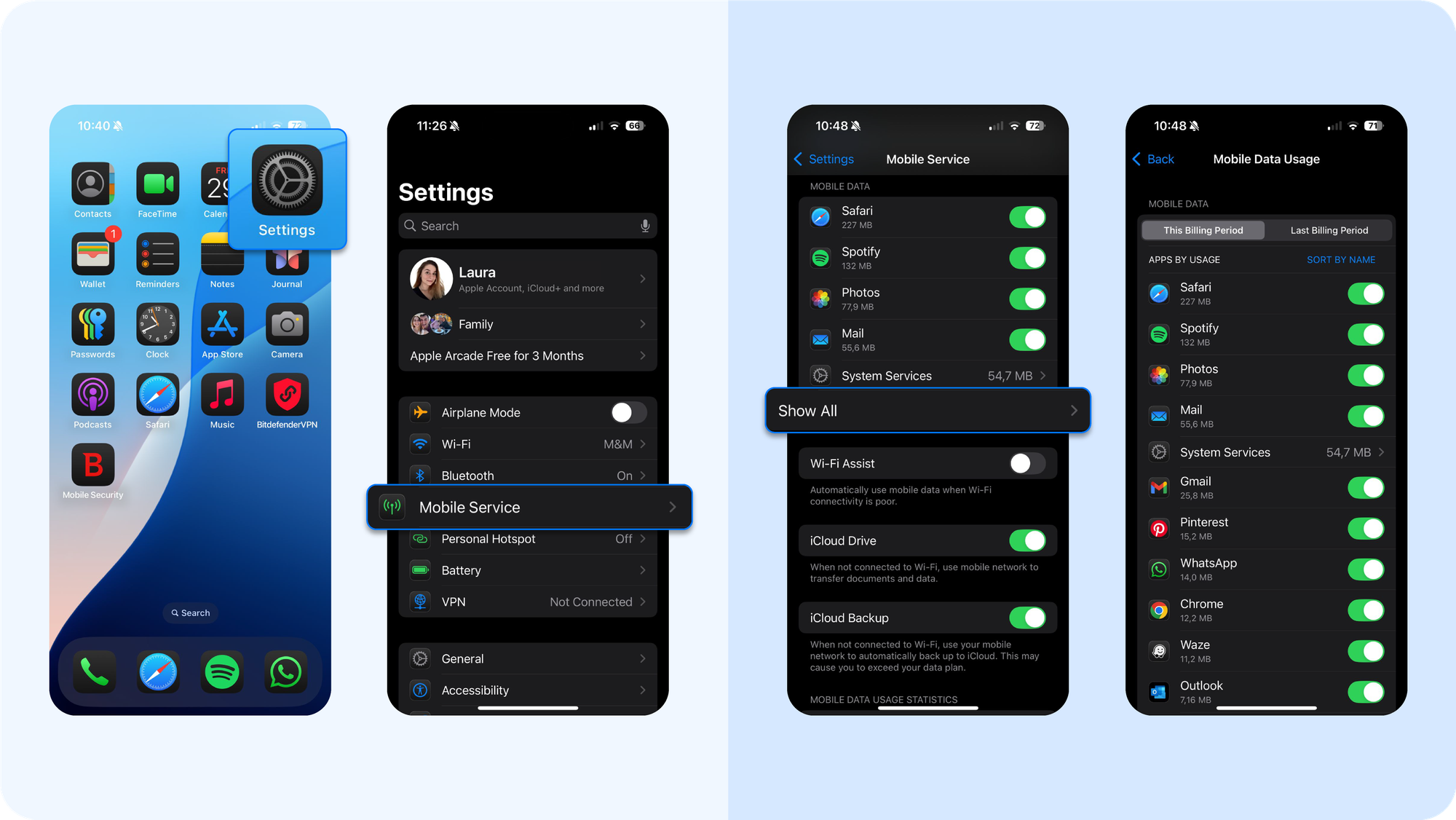
- Open Settings > Mobile Service
- Scroll down to see data usage per app (click Show All)
- Identify apps that climbed the ranking unexpectedly
Normal patterns are predictable: messaging, video streaming, browsing. Malicious software stands out because it sends short, heavy bursts of traffic at odd hours, our analysts noticed.
3. You spot unknown apps and unfamiliar icons
A malicious actor doesn't like to waste time reinventing, so they rely on sideloaded or profile-installed apps disguised as utilities. iOS’s App Store curation blocks most of these, but if attackers convince you to install a configuration profile, they can sidestep official channels. That's how you can download malware on your Apple devices without a clue.
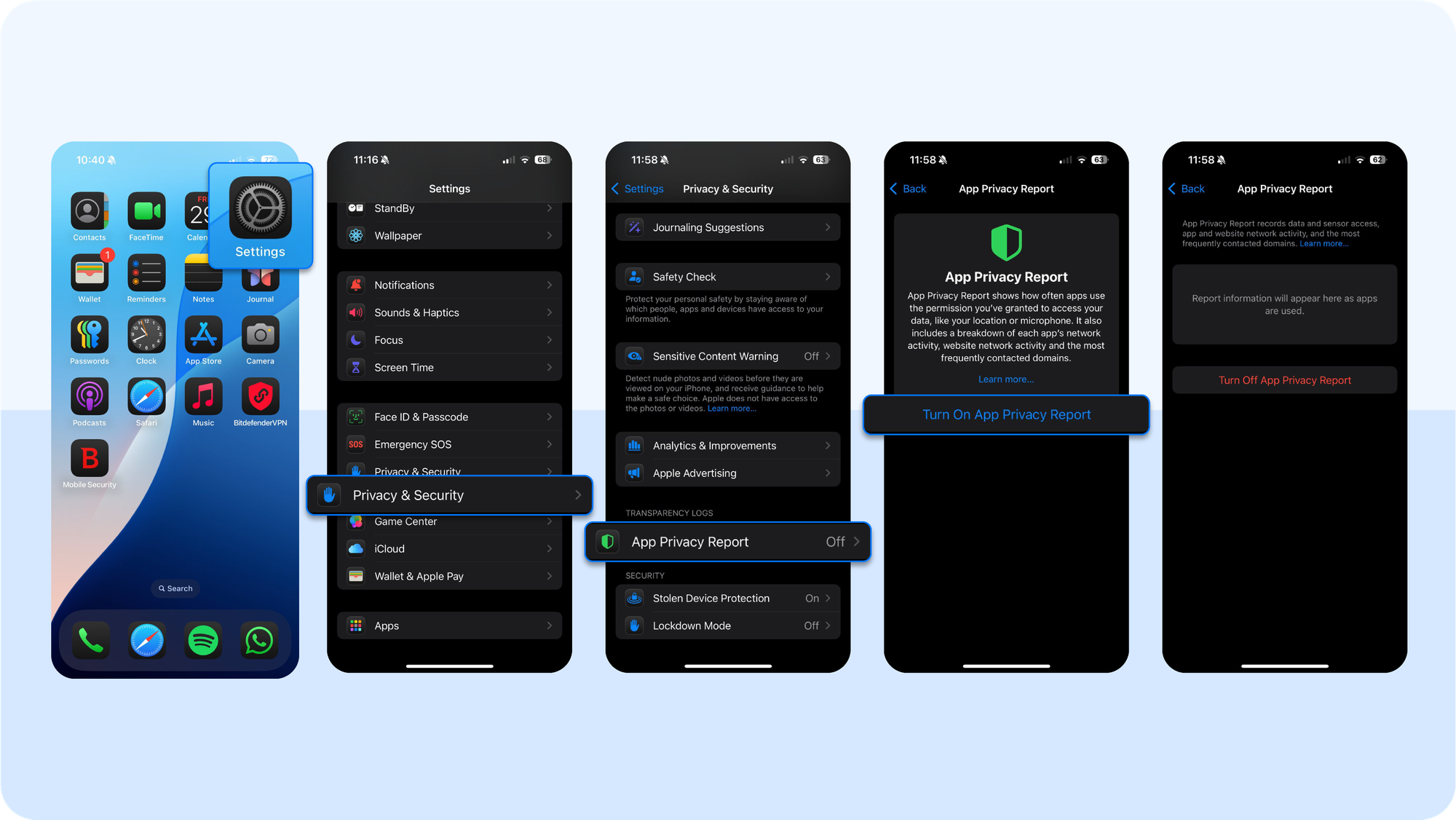
How to check for a suspicious app
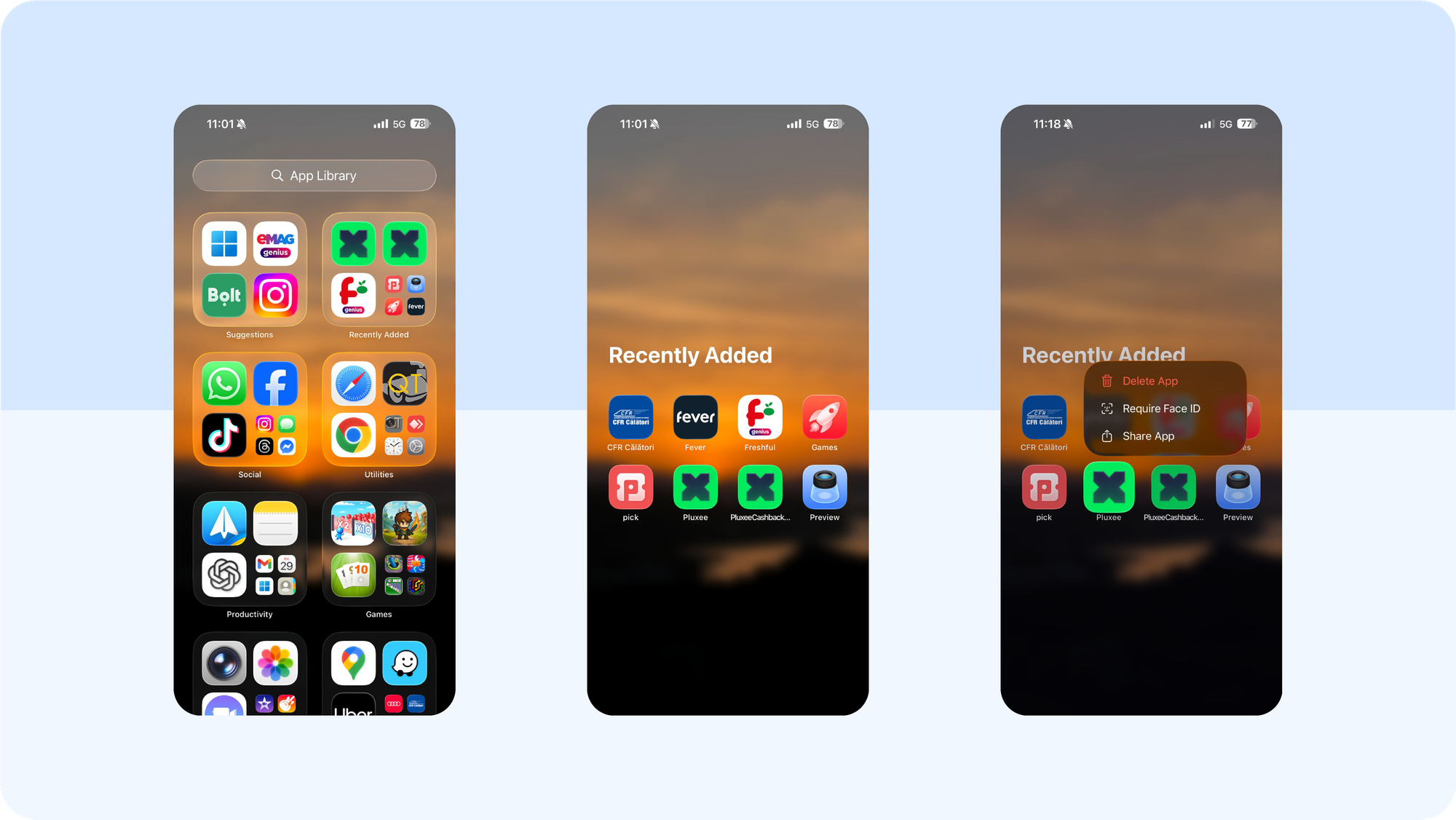
- Surface unknown apps. Open App Library (swipe past Home Screens) and check the “Recently Added” folder for anything unfamiliar. Delete any app you don’t recall installing.
- Turn on App Privacy Report. Settings → Privacy & Security → App Privacy Report → Turn On. Review which apps accessed location, mic, camera, and which domains they contacted.
- Watch the mic and camera indicators. Green indicator dot = camera in use; orange indicator dot = mic in use. If you see them unexpectedly, swipe into Control Center to see which app triggered it. You can always adjust permissions in Settings → Privacy & Security.
4. You've sent strange texts/DMs, or friends reported spam from your number
If contacts report that you’re sending messages you never wrote, something is wrong. Attackers use compromised accounts or SIM-based exploits to spread phishing links to people you know. This tactic increases the chance that someone clicks because the message looks personal. It also signals that your Apple ID, login credentials, or another linked online account may already be under an attacker’s control.
How to check for strange DMs sent:
- Open the Messages app and scan for conversations containing strange messages or links you don’t remember sending
- Check third-party messaging apps like WhatsApp, Messenger, Instagram, etc., for the same security threats
- Ask close contacts to forward suspicious messages so you can confirm if they originated from your account
- If you see evidence of unauthorized messaging, immediately change your Apple ID password and any passwords reused across messaging apps.
In digital forensics, outgoing spam is both proof of compromise and a vehicle for further spread. If your account is being used this way, assume that the attacker has already harvested some of your data. The priority becomes containment, AKA locking them out before they escalate to other cyber threats like Apple ID resets, cloud backup theft, or financial data exploitation.
5. You clicked on, or constantly receive pop-ups, ads, or redirects
Safari should not flood you with pop-ups or constant redirects under normal circumstances. If it does, it can mean you encountered a malicious site that tried to inject a profile, push a fake “security update,” or hijack your browsing session. These tactics are designed to trick you into installing software or granting privileges that bypass your iOS device's usual defenses.
How to spot and remove persistent pop-ups:
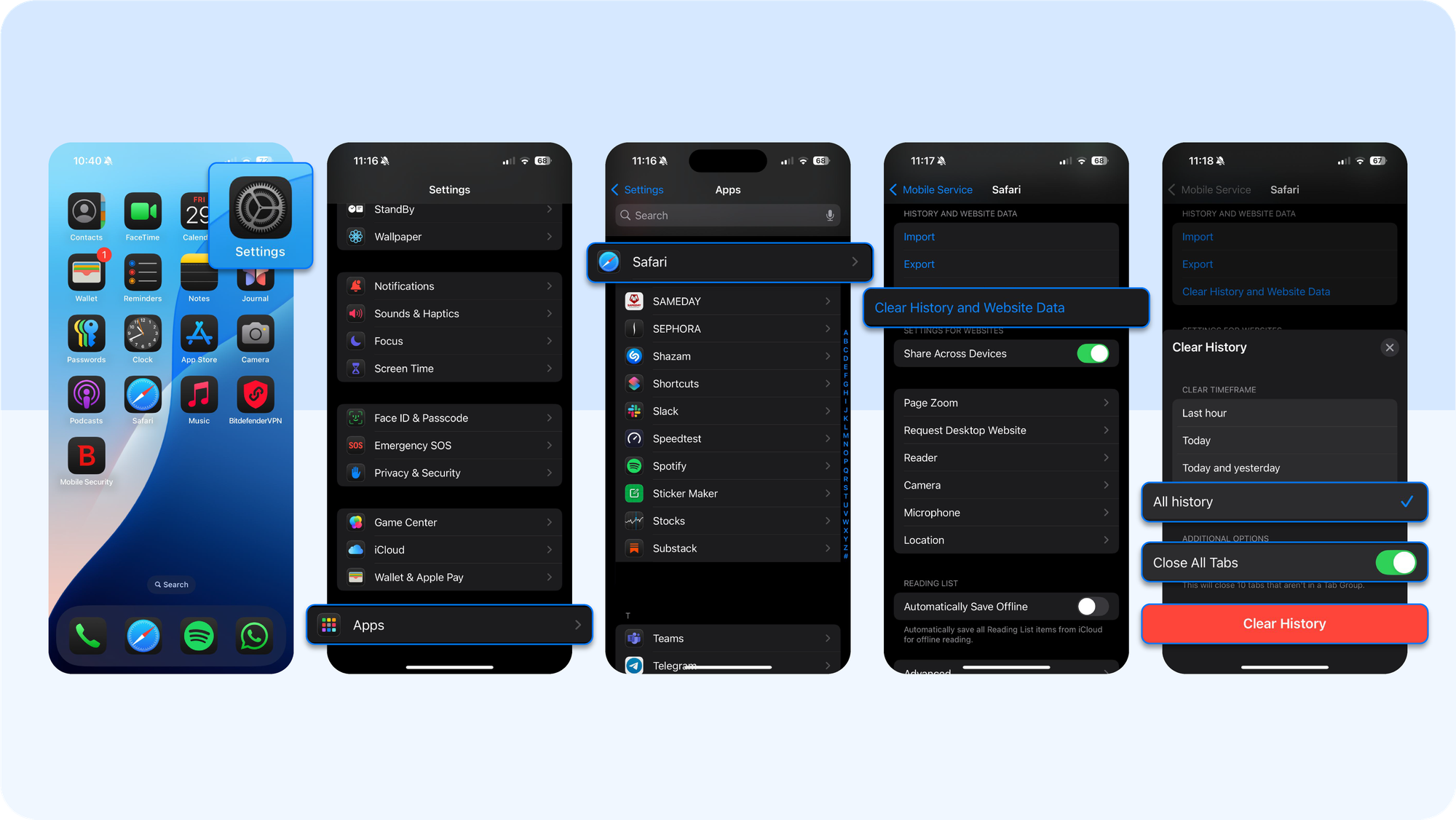
- Go to Settings → Apps -> Safari → Clear History and Website Data to wipe malicious cookies or scripts.
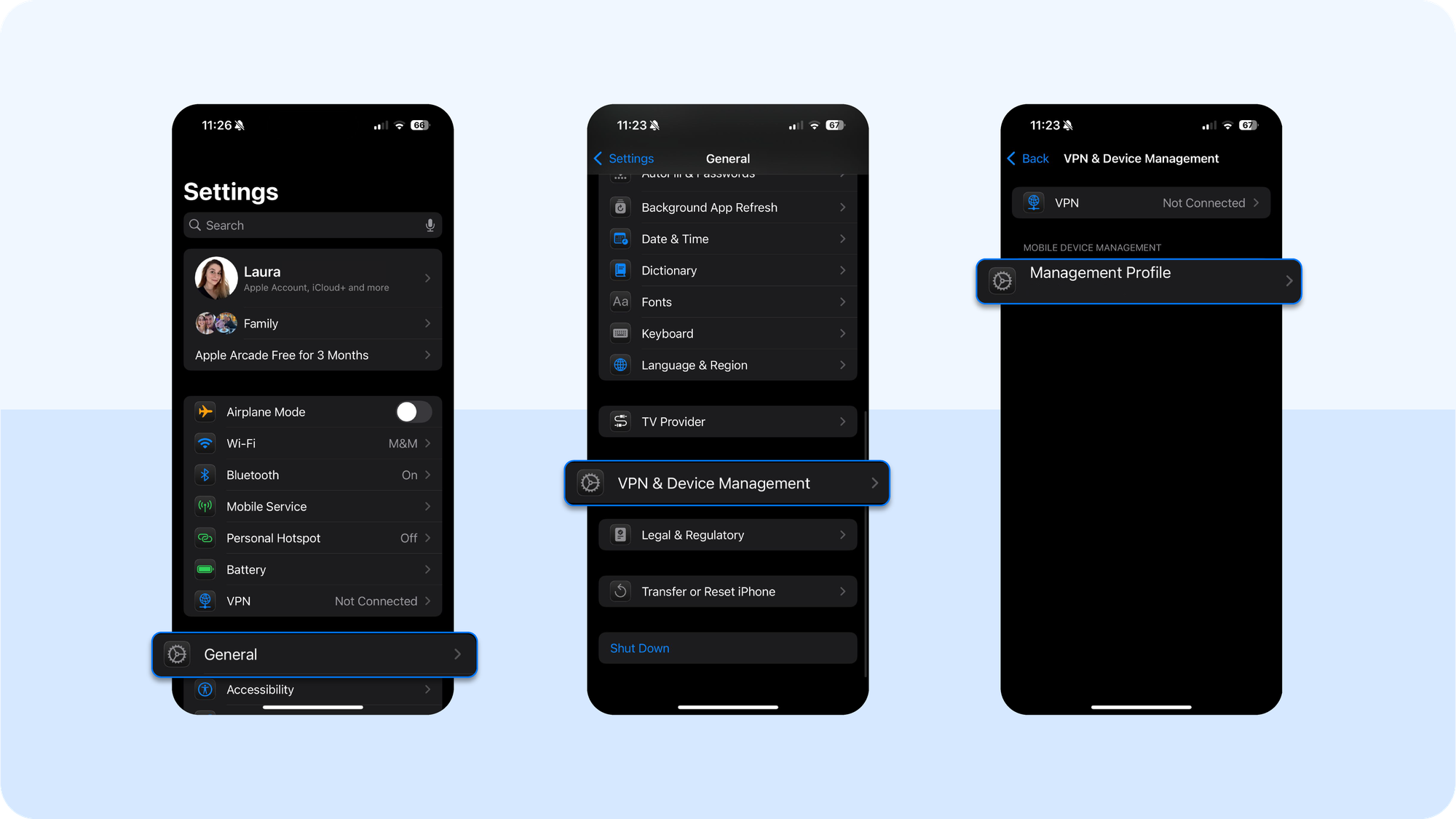
- If the behavior persists, open Settings → General → VPN & Device Management and look for unknown configuration profiles. Delete any profile you do not recognize. Doing so removes its other apps, certificates, and settings.
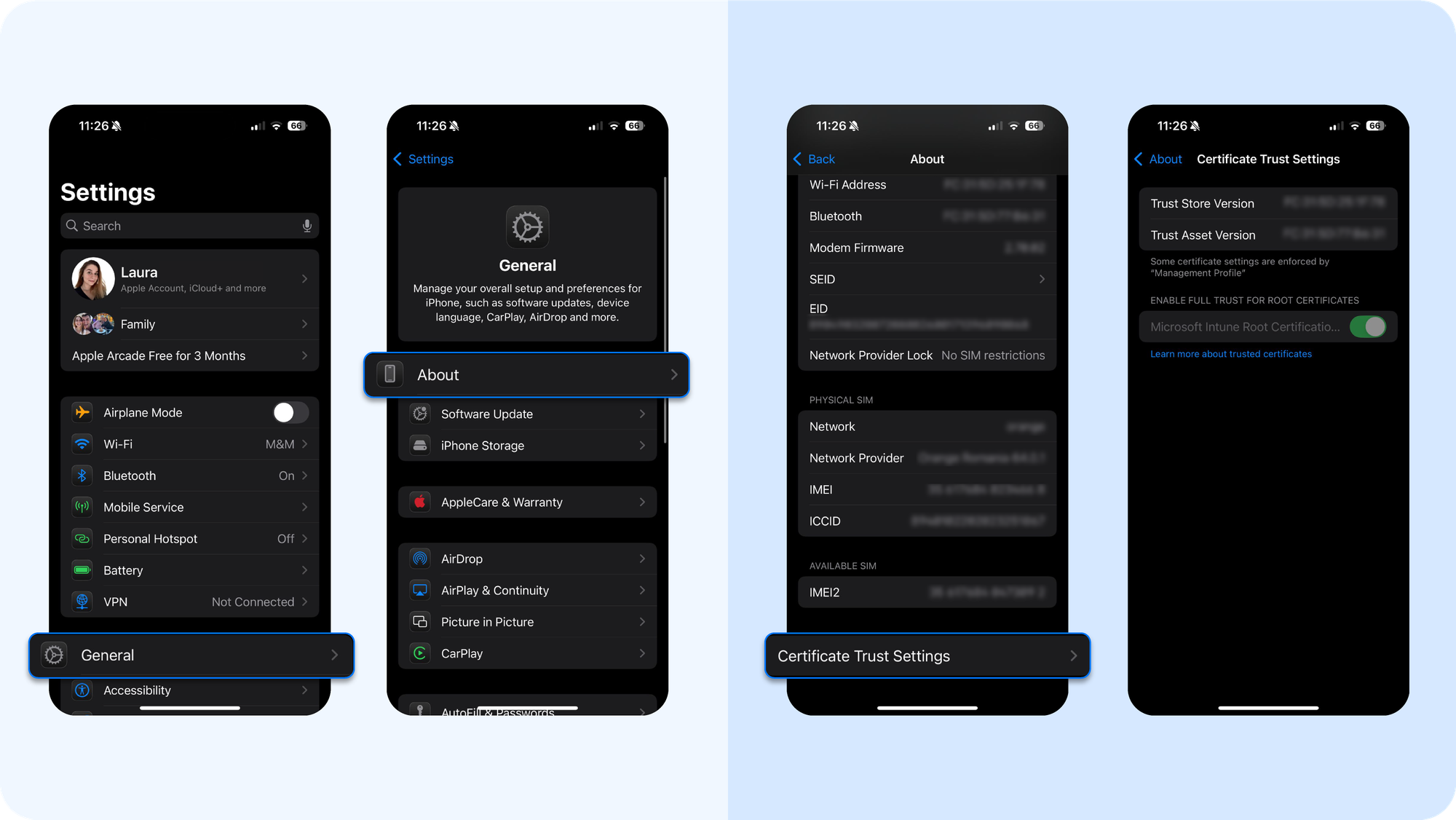
- As an extra precaution, review Settings → General → About → Certificate Trust Settings to make sure no rogue root certificates have been used.
6. You face security gaps within Apple ID prompts, session kicks, or lockouts
If your Apple ID has been hacked remotely, attackers can see your photos, erase your phone, read your backups, and access iCloud data. Unexpected password prompts, being signed out without cause, or sudden lockouts are signs that someone else may already be trying to control your account.
How to check if your Apple ID has been hacked:
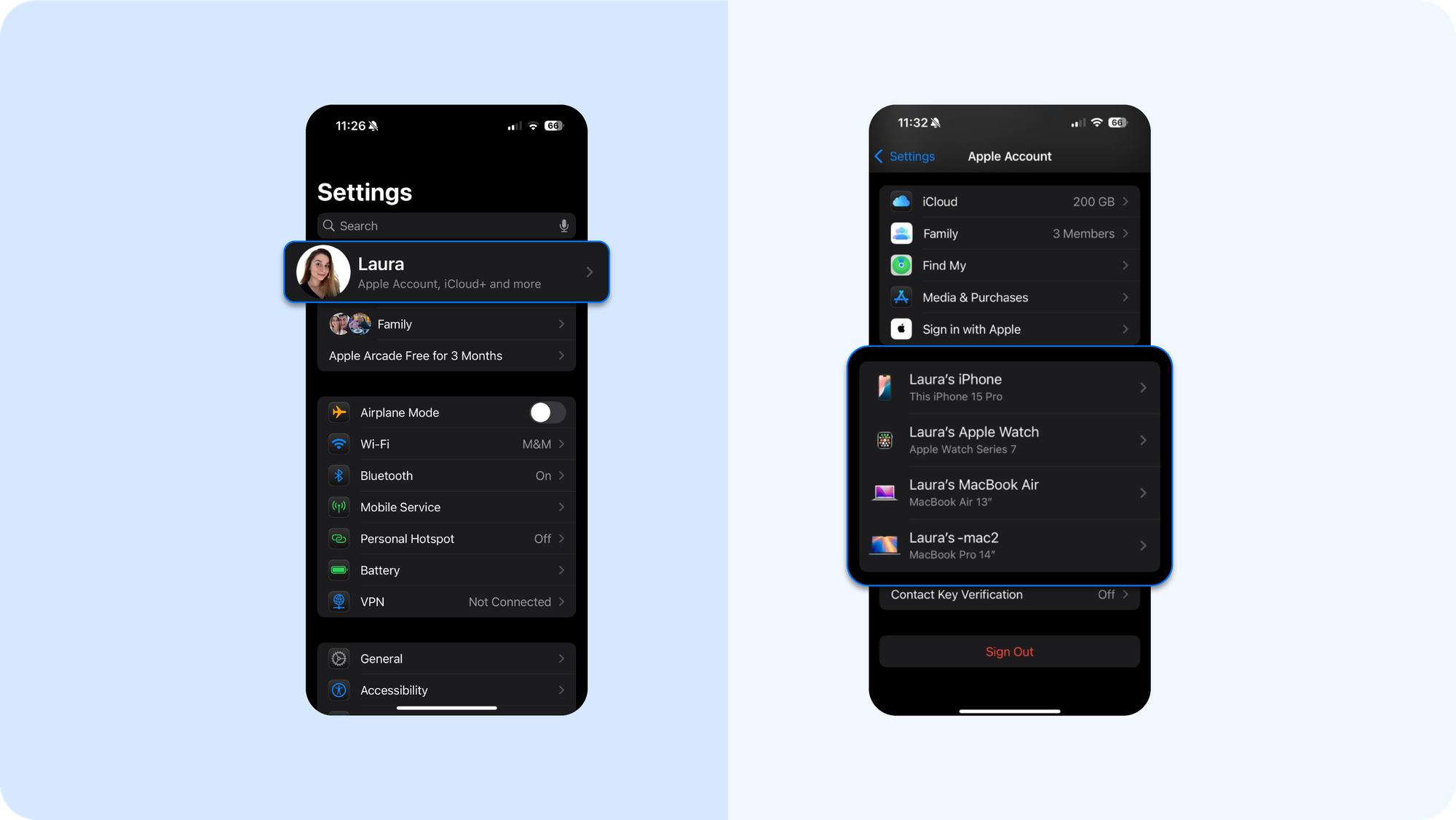
- Open Settings → [Your Name] → You'll see devices used. Carefully review every iPhone, iPad, or Mac associated with your Apple ID and remove any device you do not recognize.
- Go to Settings → [Your Name] → Sign In & Security -> Two-Factor Authentication. Review any alerts for recent sign-ins or changes to recovery information.
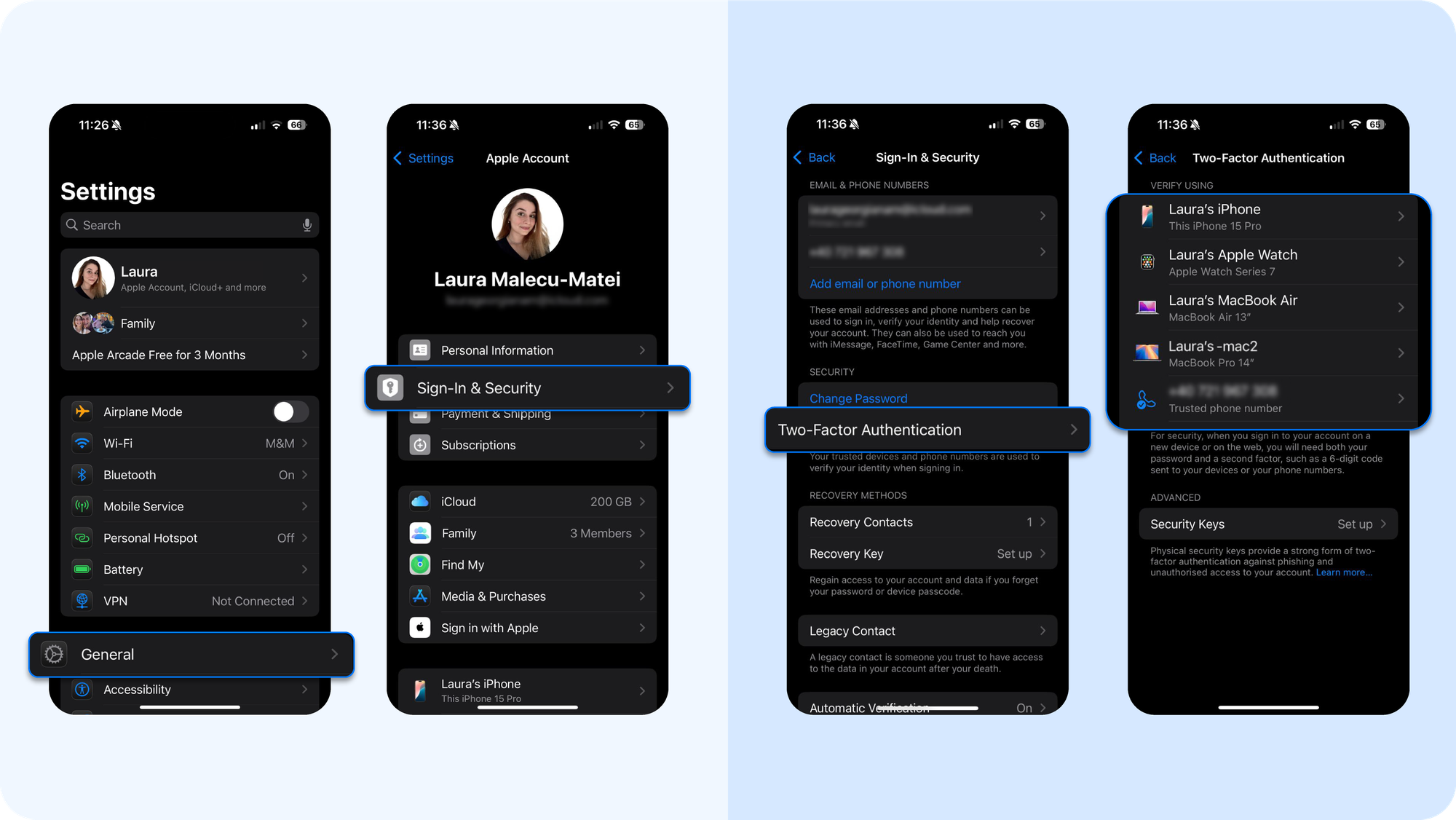
- Go to Settings → [Your Name] → Password & Security. Check the trusted phone numbers (used for 2FA) and account recovery contacts. If you see a number or contact you didn’t add, remove it.
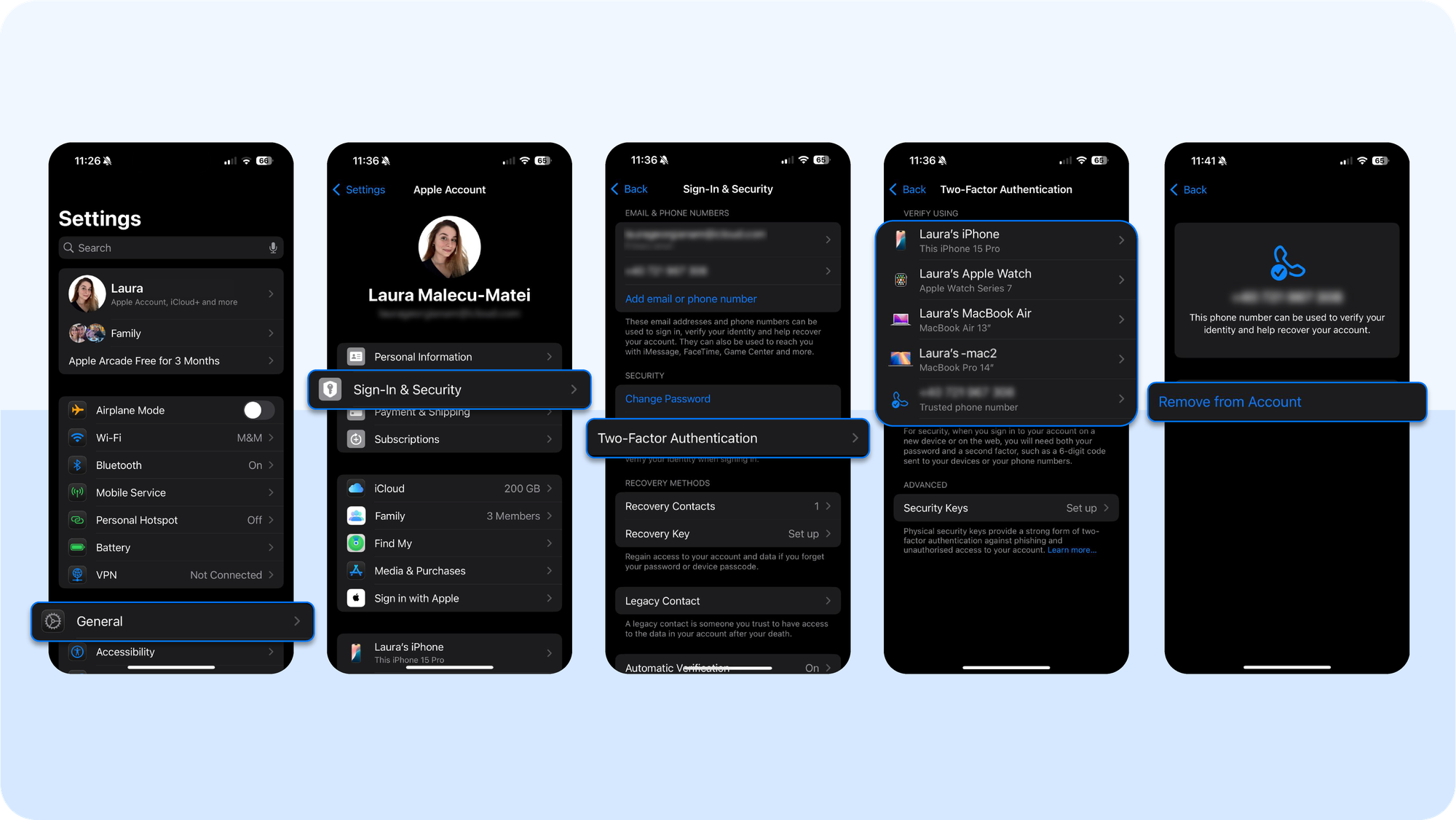
- If prompted to re-enter your password unexpectedly, change it immediately from a clean, uncompromised device.
In professional incident response, unexplained Apple ID prompts are treated as a “Tier 1 escalation.” This means the attacker has your credentials and is testing access or attempting a reset. The safest response is to contact Apple support, change your Apple ID password, and maintain good digital hygiene (e.g., always use two-factor authentication).
7. You have installed malicious configuration profiles
Companies use configuration profiles legitimately for mobile device management (MDM) to set Wi-Fi networks, install work apps, or enforce security rules on employee phones. But attackers can exploit them and silently reroute traffic, install root certificates, or force the device to trust malicious apps. Apple’s support documentation explicitly warns against installing unknown profiles.
A rogue profile can:
- Redirect your network traffic through a server they control
- Install or trust root certificates that intercept encrypted data
- Force the device to trust malicious apps that your iOS operating system would normally block
How to check if you have malicious configuration profiles installed:
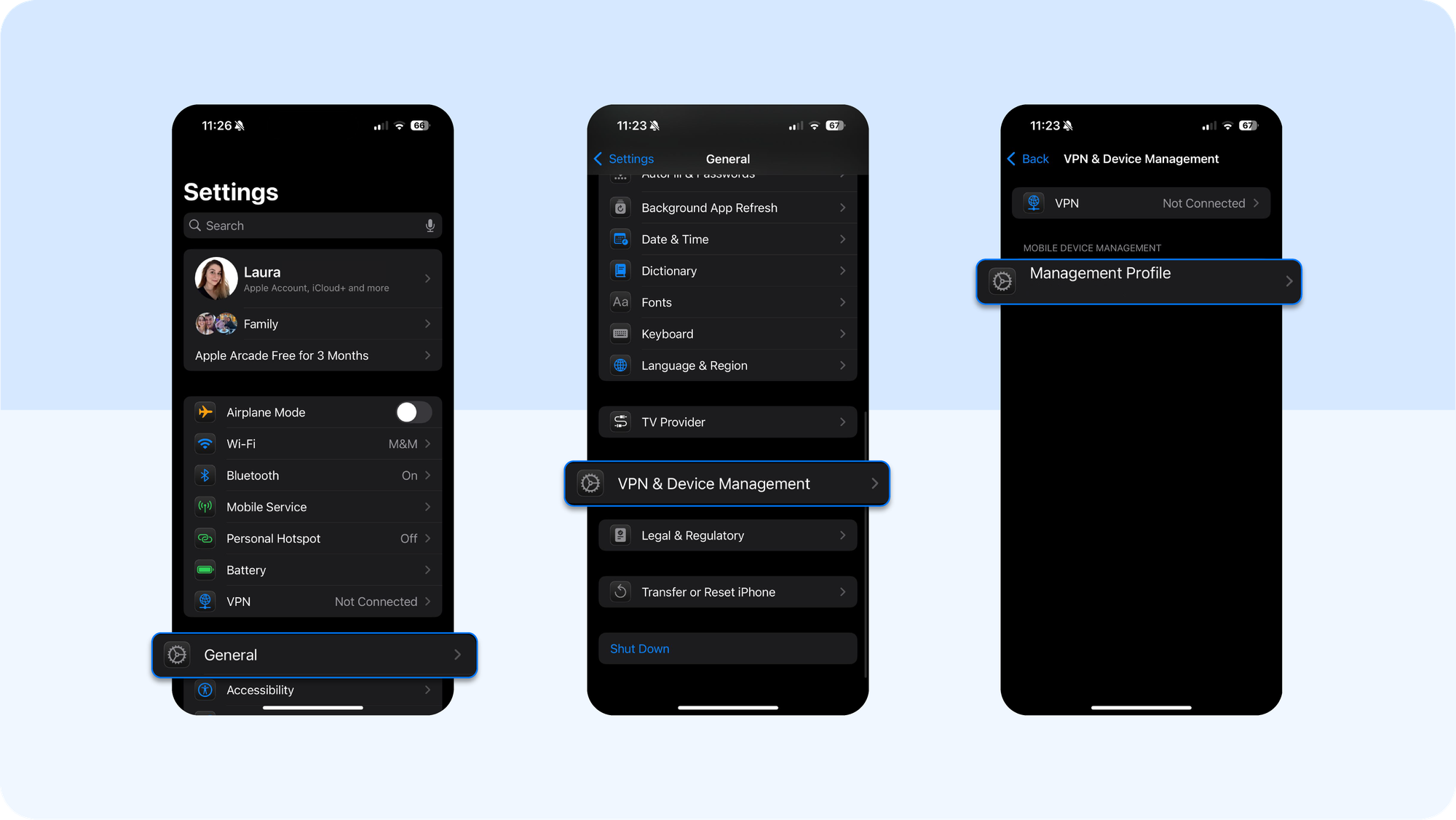
- Go to Settings → General → VPN & Device Management. If you see a profile you didn’t install as part of school, work, or a known app, delete it. Removing a profile also removes the apps and certificates it installed
- Then go to Settings → General → About → Certificate Trust Settings. Review any manually trusted root certificates. Revoke trust for anything unfamiliar
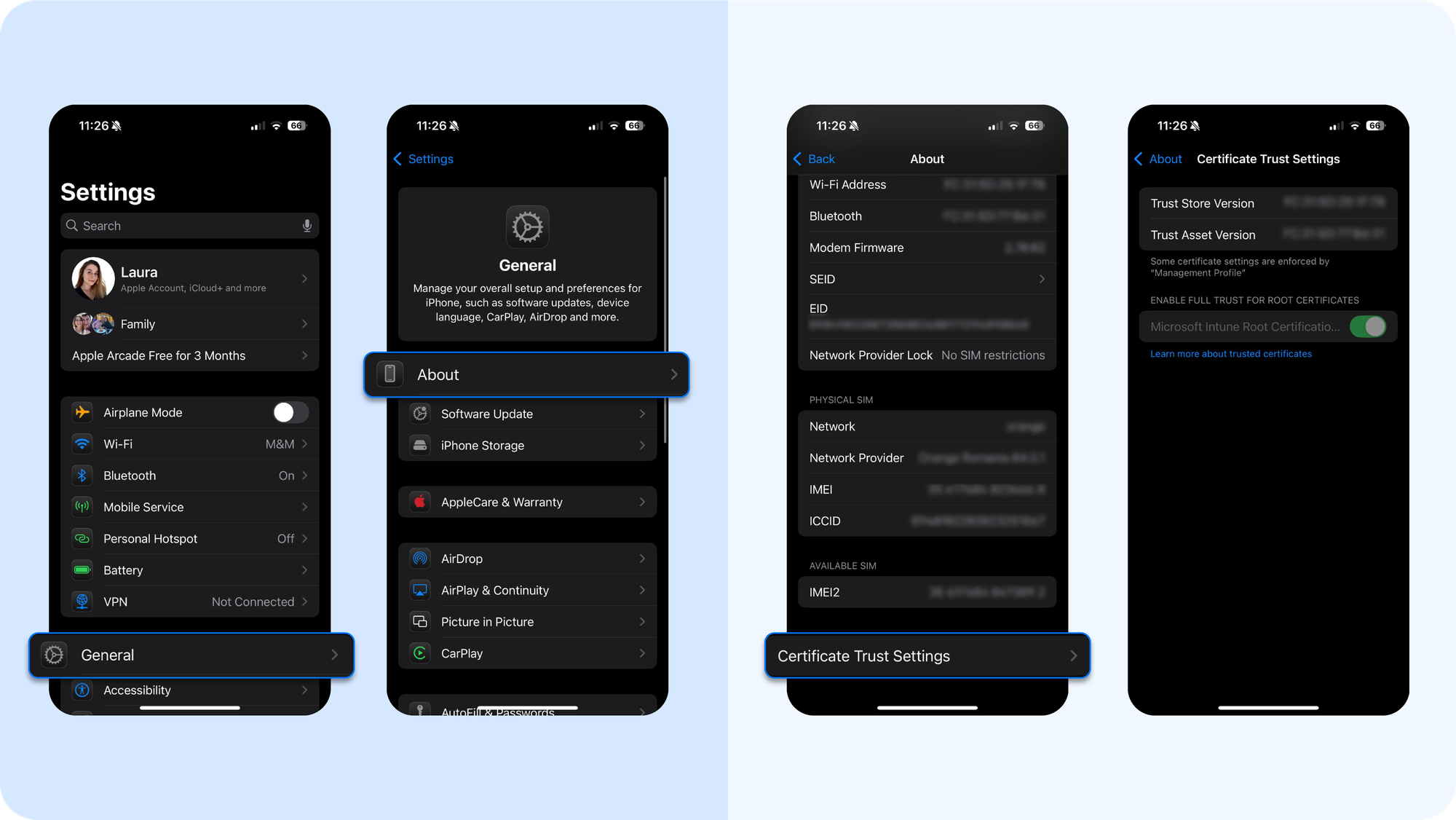
- If you’re unsure if a profile is legitimate, consult your employer or school’s IT department before deleting
Unlike a shady app, which can be deleted easily, a profile can reroute traffic and survive routine cleanups. The fact that Apple itself flags unknown profiles as a danger is a clear signal that if you find one, treat it as a high-risk compromise vector. Contact Apple directly if needed to resolve the issue.
How did your iPhone get hacked in the first place?
iPhones are resilient by design. They have a tightly curated App Store, sandboxed apps, and rapid patch cycles. Still, attackers don’t need to “break” iOS outright, as they exploit human behavior, weak identity layers, and narrow technical gaps to gain persistence. Here are the five dominant attack paths today you should know about.
1. Phishing and malicious websites

Phishing remains the most reliable and cost-effective vector against iOS. Why? Because it bypasses system defenses and targets the weakest link: user trust. In fact, Lookout’s 2024 report found iOS users faced more phishing attempts than Android users in Q3, with 18.4% of iOS devices targeted versus 11.4% of Android devices
The challenge here is that phishing pages mimic Apple’s native login prompts pixel-for-pixel. Attackers deploy SSL certificates, so users see the padlock and assume legitimacy. On iOS, where screen real estate is limited, subtle URL differences are even easier to miss.
Modern campaigns craft login pages identical to Apple’s own. These can be delivered through SMS (“smishing”), calendar invites, or fake support emails. Links can even use URL-shorteners or homoglyph domains (e.g., swapping “а” with a Cyrillic “a”). Then, you enter your Apple ID and password, believing you're logging into Apple’s system. That's when your data is captured adn sent to attacker-controlled servers.
Attackers log in immediately, sometimes from a different geography, triggering Apple’s legitimate login alerts. If 2FA codes are harvested in real time, attackers add their own device to the Apple ID for long-term access.
2. Stealer malware and spyware beyond Pegasus

Pegasus and Triangulation tend to dominate headlines, but they’re only one tier of the problem. The more pervasive risk is the growth of commodity stealers and spyware kits adapted for iOS. For example:
- Modern stealers don’t bother brute-forcing passwords when they can hijack session tokens from Safari or Chrome. With a valid token, attackers bypass MFA entirely, replaying the session to impersonate the user until it expires. This makes web app accounts like email, banking, and cloud storage particularly exposed.
- Cross-platform stealers scrape autofill data, cookies, browsing history, and saved credentials, then sync them to attacker servers. Once harvested, these credentials are bundled into “logs” sold on criminal markets.
All in all, organized crime groups deploy off-the-shelf stealers with capabilities once unique to Pegasus: credential harvesting, token replay, persistence through profiles. For people like you, the assumption that “iOS is only at risk from state-sponsored attackers” is not true.
With real-time web protection, Bitdefender Mobile Security for iOS stops stealer malware at its delivery stage, from phishing links, unsafe Wi-Fi, to rogue profiles. Get protected now.
3. Unsafe Wi-Fi and hotspots

Public Wi-Fi networks remain a hunting ground against mobile devices with auto-join turned on. Attackers don't even need to break your passwords, hijack your sessions, or have you install malware with this trick. Here's why:
- Attackers set up “evil twin” hotspots (e.g., “Airport_Free_WiFi”), then inject malicious profiles or perform SSL stripping.
- Once connected, they serve a fake captive portal urging the user to “install a certificate” or “enable VPN access” to browse.
- If you agree, a malicious configuration profile is added. The scary part is that it can persist across reboots and appear as if the device is functioning normally while all activity is monitored.
Our analysts consistently find that stolen session cookies, not passwords, are the real prize. Once intercepted, they let attackers hijack accounts without triggering MFA challenges. The solution is simple: never trust public Wi-Fi without protection. Use a reliable VPN or your own data.
That means:
- Turn off auto-join for public networks.
- Regularly check for and remove unknown profiles or certificates.
- Use a reliable VPN (included with our product) so traffic is encrypted even if the hotspot is hostile.
- Rely on tools like Bitdefender Mobile Security for iOS, which include Wi-Fi Security to alert you if you connect to unsafe networks and block phishing or proxy-based attacks before data is exposed.
How to protect your Apple ID
Here are the simplest, most effective measures to take if you want to make sure you don't deal with hacked iPhones again:
- Use a strong, unique Apple ID password. Do not reuse it across other accounts. Credential-stuffing campaigns routinely test breached passwords against Apple IDs.
- Turn on two-factor authentication (2FA). Settings → [Your Name] → Password & Security → Turn On 2FA.
- Audit your devices regularly. Settings → [Your Name] → Devices. Remove any device you don’t recognize ASAP.
- Watch for phishing prompts. Apple never asks you to verify your Apple ID via email or SMS. Instead, you receive verification codes via a notification on a trusted Apple device. Suspicious login alerts or unexpected password prompts are a signal to reset immediately.
- Deploy Bitdefender Mobile Security for iOS. Its anti-phishing and web protection block the fake Apple ID login pages that credential stealers use to harvest your password before you ever type it. This closes the most common path into your account.
- Keep iOS and apps updated. Most attacks exploit unpatched flaws, so make sure to keep your iOS constantly updated. Go to Settings → General → Software Update.
- Clear Safari history to wipe cookies, cache, and login states. Also, consider DNS filtering, so that every domain request your iPhone makes is checked against a database of known malicious addresses.
- Turn on iCloud Backup in Settings → [Your Name] → iCloud → iCloud Backup, or use Finder/iTunes with “Encrypt local backup” checked.
What To Do If Your iPhone Is Hacked: A precise playbook
If your iPhone has been hacked, follow these steps backed by our cybersecurity experts:
Step 1 — Change all your passwords from a clean device
Start with Apple ID, then email, banking, social, and any other high‑risk iPhone apps. Do it on a second device you trust so a keylogger or token stealer cannot capture the new credentials. Most breaches involve people elements like stolen credentials or social engineering, which is why you reset first and fast.
From now on, rotate passwords for accounts that receive sensitive text messages or phone calls, since attackers like to pivot through SMS resets.
Step 2 — Remove unknown devices from Apple ID and revoke access
On your iPhone, go to Settings → [Your Name] → Devices. Remove anything you do not recognize to cut off control of your iPhone remotely and reduce the chance of unauthorized purchases against your Apple Wallet or App Store account.
After device cleanup, sign out of sessions in critical services and re‑authenticate only on the clean device.
Step 3 — Scan and clean the device
Use Bitdefender Mobile Security for iOS to block phishing websites and malicious links while you triage. Then manually remove sketchy apps or rogue configuration profiles in Settings → General → VPN & Device Management.
Deleting a profile removes the settings, apps, and data it installed, which is key if an attacker used a profile to route traffic on the same network or to persist beyond reboots.
Clear Safari history and website data to break redirect loops, then re‑test pages that failed to load webpages correctly.
Step 4 — Contain risk with Lost Mode
If you suspect physical access or you cannot complete the cleanup immediately, use Lost Mode in Find My to lock the device, display a contact message, and suspend Apple Pay cards while you secure accounts. This will help minimize damage while you stabilise your iPhone security baseline.
Step 5 — Reset and restore only when needed
If indicators persist after cleanup, erase the device and restore from a known‑good backup. Use iCloud or encrypted Finder/iTunes backups so saved passwords, health data, and app data to restore safely after returning to factory settings. iCloud backups encrypt automatically, and local Finder/iTunes backups must have Encrypt local backup enabled.
Create a fresh backup only after the system is clean, as restoring an infected state defeats the factory reset.
Keep your iPhone ahead of hackers
If you’ve read this far, you already know how to spot hackers and protect your mobile device. The early warnings hide in plain sight. Think of a sudden drain on battery power, strange spikes in data usage, a new app you don’t remember installing, or repeated Apple ID prompts – these are the clues worth acting on. Even your browser history can tell the story if you look closely enough.
The fix is less dramatic than it sounds. Keep iOS and your iPhone apps updated. Use strong credentials and 2FA to shut down social engineering. Clear out sketchy apps, review permissions, and run regular scans so nothing lingers in the background.
Why not let experts take on the heavy lifting?
An antivirus software like Bitdefender Mobile Security for iOS quietly blocks phishing websites before they trick you, alerts you to unsafe Wi-Fi, and flags malicious links that could otherwise slip through. Think of it as the extra layer that keeps your online safety intact while you focus on everything else your iPhone is meant to do.
tags
Author
The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









