Technical Advisory: React2Shell Critical Unauthenticated RCE in React (CVE-2025-55182)

TL;DR Ransomware groups are expected to rapidly weaponize this critical (CVSS 10.0) React vulnerability to establish initial access. This vulnerability leads to remote code execution for unauthenticated attacks, and potential impact is similar to Log4j.
On December 3, 2025, a critical Remote Code Execution (RCE) vulnerability was disclosed in the React ecosystem, creating an immediate emergency for organizations. The core vulnerability (CVE-2025-55182) originates in the React 'Flight' protocol logic. While the Next.js framework is a primary vector for enterprise environments, specifically through default 'App Router' and React Server Components (RSC) configurations, it is not the sole entry point. The flaw propagates to other downstream frameworks and bundlers, most notably Vite, affecting the broader ecosystem.
This vulnerability (CVSS 10.0) allows unauthenticated, remote attackers to execute arbitrary commands on the server by sending specially crafted HTTP requests containing malicious object references. Unlike vulnerabilities requiring specific misconfigurations, this flaw resides in the core library's request parsing mechanism, exposing any public-facing Next.js application (versions 15.x, 16.x, and 14.x Canary) to exploitation.
We assess that Ransomware-as-a-Service (RaaS) groups and Initial Access Brokers (IABs) will rapidly weaponize this flaw to secure footholds in corporate networks as soon as a PoC is published. Immediate mitigation is required.
Update (December 5, 2025): The first functional PoC for CVE-2025-55182 has been published on GitHub by security researcher maple3142. Concurrently, Amazon has confirmed the first cases of active exploitation in the wild, reporting that China-nexus threat groups (including "Earth Lamia" and "Jackpot Panda") began targeting the vulnerability within hours of its disclosure.
Join our live discussion on LinkedIn about React2Shell. We'll explore additional insights and answer your questions in real time.
Note on Related Vulnerabilities: While CVE-2025-55182 affects the core React library, Next.js was tracked separately under CVE-2025-66478, which has since been rejected as a duplicate.
Why You Must Act Now
New edge device vulnerabilities, such as React2Shell, serve as a "beachhead" for rapid initial access. As shown in the attached workflow, attacks typically begin with a massive wave of automation less than 24 hours after a PoC becomes available. After bots deploy webshells to compromise the network, human operators from RaaS groups take over. This manual phase can begin hours or weeks later, depending on the target's value and the attackers' current workload. This is the standard ransomware playbook for 2025, responsible for the worst ransomware month in history.
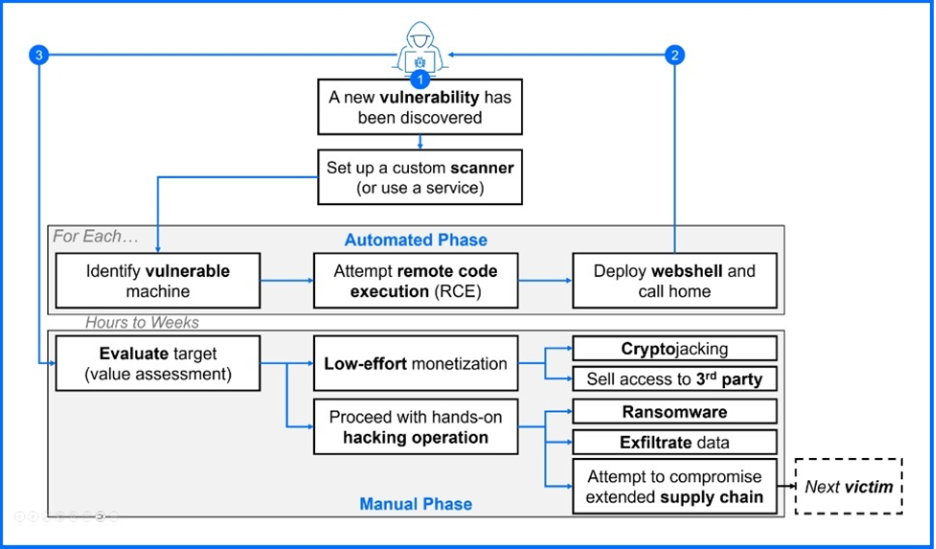
The two stages of ransomware attack initiated through edge-network devices compromise. Source: Ransomware: A Comprehensive Guide to Prevention and Response
Immediate Action Required
Organizations should treat this as an emergency situation. The gap between the automated shell deployment and the manual breakout is your window of opportunity.
- Mitigate: Patch affected systems or block traffic immediately.
- Monitor: Watch closely for lateral movement originating from the DMZ.
- Track: Stay alert for published Indicators of Compromise (IOCs).
You must consider this an emergency. Use this brief window to patch systems, block malicious traffic, and monitor the DMZ for lateral movement before the manual phase begins.
React2Shell Overview
CVE-2025-55182 is a logic flaw within the "Flight" protocol, the mechanism React uses to communicate between the server and client components. It affects default configurations of widely used frameworks, most notably Next.js (versions 15.x, 16.x, and specific Canary builds of 14.x).
Unlike vulnerabilities that require a specific misconfiguration, this flaw exists in the core library that handles request parsing. If an application uses React Server Components - which is the default for the Next.js "App Router" - it is vulnerable to unauthenticated exploitation from the public internet.
Insecure Deserialization
In modern architectures like RSC, the server renders components and sends them to the client browser. To do this, complex data structures (objects) must be converted into a stream of text that can travel over HTTP. This process is called serialization. When the server receives a reply or a request, it must reconstruct these objects from the text stream; this is deserialization. The process of converting text into objects is widely considered one of the most dangerous classes of software vulnerabilities ("Insecure Deserialization", categorized as CWE-502). The React2Shell vulnerability resides in the react-server package, specifically in how it parses object references during deserialization.
To understand this vulnerability, you need to understand the Event Loop - the internal system JavaScript uses to manage background tasks (asynchronous operations).
When the server uses the await command, it is effectively handing a job over to the Event Loop saying, 'Pause here and wake me up when this task is finished.' To do this, the Event Loop follows a strict protocol to identify if the object is actually a valid task: It looks for a function named .then() and executes it.
The Event Loop assumes that running .then() is the safe, standard way to register a callback for the result. The vulnerability exploits this automatic process. By attaching a dangerous system command to the .then property, the attacker tricks the Event Loop into running malicious code at the exact moment it tries to register the task.
The Normal Scenario
In a normal request, React uses "references" (like $1) to link pieces of data together. The server follows these references to build a simple data object.
files = {
"0": (None, '["$1"]'),
"1": (None, '{"object":"foo","name":"$2:fooName"}'),
"2": (None, '{"fooName":"bar"}'),
}
The server treats this as plain data. It is safe and deserializes to the following on the React server:
{ object: ‘foo’, name: ‘bar’ }
The Exploit Scenario
The attacker uses the vulnerability to reference an internal system tool - the Function Constructor (which builds and runs code from a simple text string) - and assigns it to the special .then property.
let maliciousObject = {
// The attacker forces the "then" property to be the system's Code Builder
then: Function
};
The server automatically tries to "resolve" this object because it looks like a Promise (it has a .then property).
This example uses the built-in Function Constructor to demonstrate the concept simply. While this specific method allows the attacker to trigger the system tool, it may not lead to immediate Remote Code Execution (RCE) because it is missing "argument binding" (the ability to pass specific commands to the function). However, it clearly illustrates the vulnerability's mechanism. In a real-world attack, adversaries would use other tools (such as the Node.js vm module) that can be chained together to bind malicious arguments and achieve full RCE.
While a basic exploitation probably causes a server crash (DoS), more advanced payload can manipulate this traversal to escape the object scope. By referencing global objects available in the Node.js environment, the attacker can run shell commands directly on the server.
Intelligence Warning
We have observed a rapid trend of misleading and dangerous PoCs circulating in public repositories and vulnerability aggregators. Security teams must exercise extreme caution.
- Risk 1: False Negatives (Invalid Logic) Many circulating scripts rely on the application developer having explicitly exposed dangerous functionality (e.g., vm#runInThisCntext, child_process#exec, fs#writeFile). This is not a valid test for CVE-2025-55182. The genuine vulnerability affects the core library's request parsing and does not require these manual exposures. Testing with these invalid scripts will result in a "failed exploit," leading teams to incorrectly conclude they are safe.
- Risk 2: Operational Safety (Malware) Threat actors are actively seeding repositories with fake PoC scripts that contain malicious payloads (e.g., info-stealers, backdoors, or ransomware). Do not blindly execute unverified code from GitHub or social media links, always audit the code of any third-party scanner before execution.
To avoid third-party execution scripts entirely, you can use the safe curl probe from the "Recommendations" section, which safely tests for the parser error signature without executing code or risking malware infection.
Recommendations
The window between disclosure and mass exploitation is closing. Take the following actions immediately.
- Patch Critical Components (Priority 0)
The window for mitigation is closing. You must immediately update both the core React library and the Next.js framework to the safe versions listed below. This addresses both the upstream React vulnerability (CVE-2025-55182) and the downstream Next.js implementations.
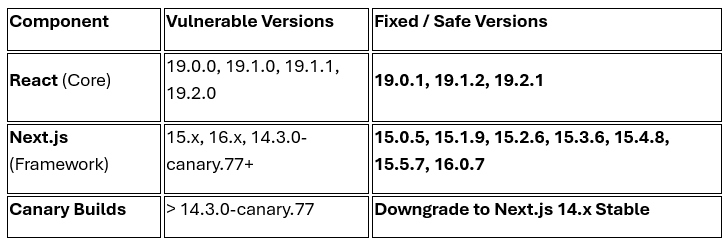
Note: Platform-specific mitigations have been deployed by Vercel, Netlify, Cloudflare and others. However, self-hosted instances (e.g. Docker, AWS, Azure) remain fully exposed and must be patched manually.
- Verify Vulnerability Status
Use the following curl command to probe your server. This checks for the specific parser error returned by the vulnerable "Flight" protocol handling.
# This probe attempts to trigger the parser error without executing code.
curl -v -k -X POST "http://localhost:3000/" \
-H "Next-Action: 1337" \
-F '1="{}"' \
-F '0=["$1:a:a"]'
- Vulnerable: Returns 500 Internal Server Error containing E{"digest".
- Patched/Safe: Returns 400 Bad Request or ignores the malformed key.
- Implement Emergency WAF Rules
If patching cannot be performed immediately, configure your Web Application Firewall (WAF) to block specific attack patterns.
- Block Rule: Deny multipart/form-data requests where form keys contain both colon (:) delimiters and reference markers ($). This pattern is characteristic of the exploit payload used to manipulate the getOutlinedModel() traversal logic.
- Network Containment
Upon successful compromise, defenders should anticipate either a C2 connection via webshell or cryptominer deployment. The former is a critical indicator of imminent lateral movement, whereas the latter primarily impacts system resources. While standard lateral movement timelines average two weeks, advanced threat actors like Akira are significantly reducing this breakout window.
- Restrict Outbound Traffic: Configure egress filtering to deny all outbound connections from web servers, except for necessary allow-listed APIs (e.g. databases, 3rd party services). This breaks the "reverse shell" connection back to the attacker.
- Segmentation: Isolate and monitor the DMZ to prevent lateral movement if the web server is compromised. Ransomware operators typically use this initial foothold to pivot to internal infrastructure.
- Assume Breach
If your unpatched server was exposed to the public internet prior to December 3, 2025, investigate for signs of compromise. Although mass exploitation typically follows the release of PoC code, sophisticated threat actors can develop private exploits immediately.
Bitdefender MDR Status: Bitdefender MDR is already monitoring for indicators across our customer base. We are monitoring all available threat intelligence sources to prepare and deploy specific packages for threat hunting.
Update (December 5, 2025): A functional PoC has recently been published on GitHub, and Amazon has reported observing initial exploitation attempts in the wild.
Update (December 8, 2025): Bitdefender GravityZone External Attack Surface Management (EASM) has been updated to automatically identify assets affected by CVE-2025-55182. Current EASM customers should review their dashboards for this specific CVE identifier to assess their remaining exposure. If you do not have a recurring scan configured, you must manually re-run a scan on your monitored assets to apply these new detection rules and to accurately assess your exposure.
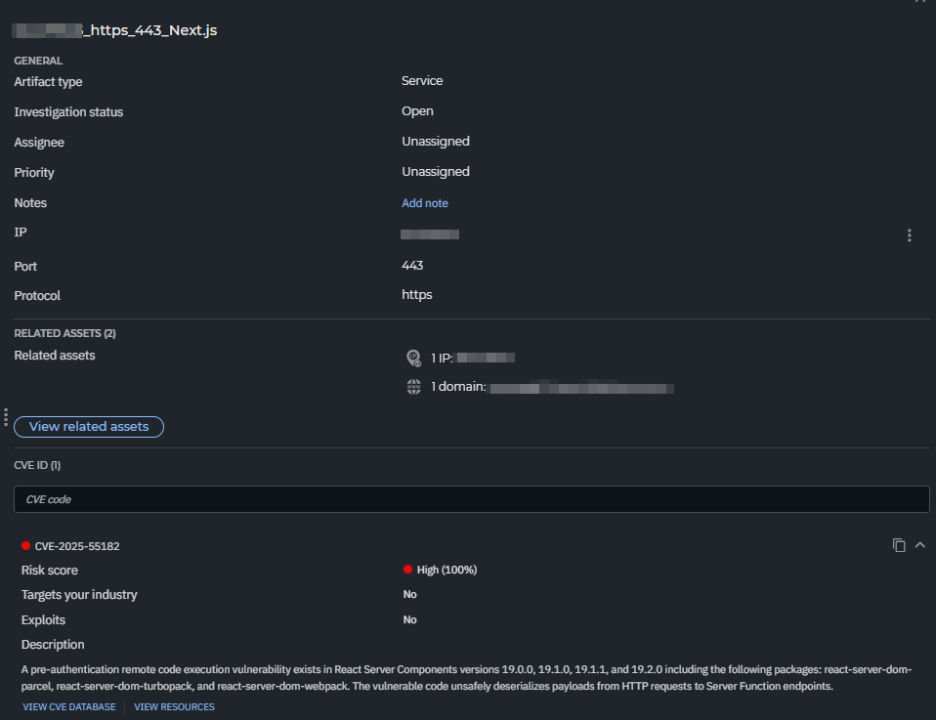
The GravityZone EASM flags vulnerable versions of React Server Components and Next.js on your external perimeter (external).
Update (December 10, 2025): We have updated the Bitdefender GravityZone Endpoint Risk Analytics (ERA) to automatically detect CVE-2025-55182 across your entire infrastructure.
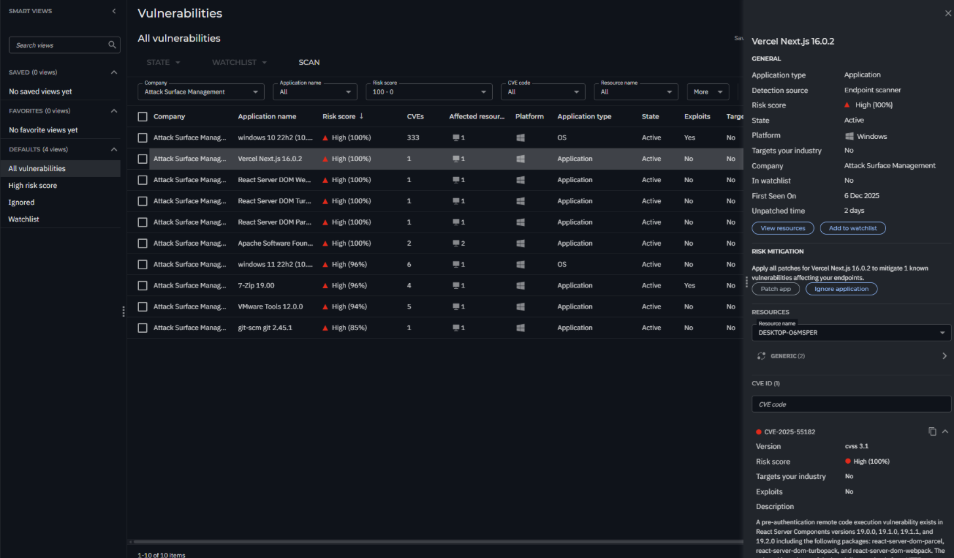
The GravityZone ERA flags vulnerable applications on managed endpoints (internal).
Update (December 10, 2025): By combining telemetry from our enterprise sensors with a report from our colleagues in the consumer business unit, we have compiled a consolidated table of Indicators of Compromise (IOCs) to assist in immediate threat hunting. Following the deployment of a dedicated signature to our Network Attack Defense module for this CVE, we recorded over 14,000 specific exploitation attempts in a single 24-hour period. It is important to note that these figures reflect the volume of blocked attacks rather than vulnerable systems. Analyzing the intended payloads from these intercepted attempts, we observe an expected split in opportunistic activity: actors are attempting to deploy commodity cryptominers (XMRig) or install webshells to establish a persistent backdoor, allowing them to return to the compromised environment at a later time.
The important behavioral finding from this dataset is the prevalence of the whoami in over 90% of the analyzed attack chains. While this is a benign tool on its own, its execution context provides a high-fidelity signal. Security teams should prioritize alerts where whoami is spawned directly by web server processes (such as node.exe, or httpd.exe).
Indicators of Compromise (IOCs)
For our OEM partners and integrations, access to our threat intelligence data is primarily provided programmatically. We also offer a user interface, the IntelliZone Portal. This is where partners find more ways to interact with our data, like an operational dashboard of threats targeting their industry. A full breakdown of this research can be found on the platform under ThreatID BDs7zjeguz:
https://intellizone.bitdefender.com/en/threat-search/threats/BDs7zjeguz
Public IOCs on GitHub
We are now hosting Indicators of Compromise (IOCs) from this and all future research on a public GitHub repository to improve accessibility and collaboration with the security community:
https://github.com/bitdefender/malware-ioc/blob/master/2025_12_10-react2shell-iocs.csv
Ctrl-Alt-DECODE Newsletter
Receive just-in-time security advisories via Ctrl-Alt-DECODE. Our newsletter delivers immediate notifications on critical threats and original research from Bitdefender Labs and MDR.
https://www.linkedin.com/newsletters/7371216616015036416/?displayConfirmation=true
Ctrl-Alt-DECODE LIVE Discussion
Join our live discussion on LinkedIn about React2Shell as we share additional insights and address your questions in real time.
We would like to thank Bitdefenders Adrian Schipor and Bogdan Zavadovschi (sorted alphabetically) for their contributions to this advisory. This is a rapidly evolving threat. Bitdefender will continue to monitor the situation and provide updates as more information becomes available.
tags
Author
Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsYou might also like
Bookmarks

