Zerologon: How Bitdefender Protects Customers from this No-Credential Post-Exploit Technique

- Zerologon is a zero-credential vulnerability that exploits Windows Netlogon to allow adversaries access to the Active Directory domain controllers, first reported in August 2020
- “This attack has a huge impact” according to researchers, as attackers on the local network can launch this exploit to compromise the Windows domain controller with no authentication
- Bitdefender customers are protected from this post-exploit technique via our Network Attack Defense, Anti-Malware SDK and Indicator of Risk (IOR) technologies
Termed as Zerologon (CVE-2020-1472), the attacker exploits endpoint native tools to elevate privileges using the Netlogon vulnerability. Developed by researchers from Secura, it allows attackers to gain unauthenticated control of the Active Directory using Netlogon Remote Protocol (MS-NRPC) to connect to a domain controller and obtain domain administrator access.
Technical Overview
The Netlogon Remote Procedure Call is an RPC interface available on Windows Domain Controller. It is used for various tasks related to user and machine authentication using the NT (New Technology) LM (LAN Manager) protocol.
This protocol does not use the same authentication scheme as other RPC services. Instead it uses a customized cryptographic protocol to allow a client (a domain-joined computer) and server (the domain controller) prove to each other that they both know a shared secret cipher.
The cryptographic protocol used is rather unorthodox and has not been put under much scrutiny (CVE-2019-1424). A study conducted last year showed that Netlogon calls were not being encrypted when a fallback SMB occurred while a session had already been established.
In the technical overview diagram below:
- The Netlogon message parameters in the protocol are filled with zeroes
- Attacker retries the handshake a few times to set an empty password on the domain controller
- Attacker changes the computer password of the domain controller stored in the Active Directory to obtain domain admin credentials and then restores the original domain controller password
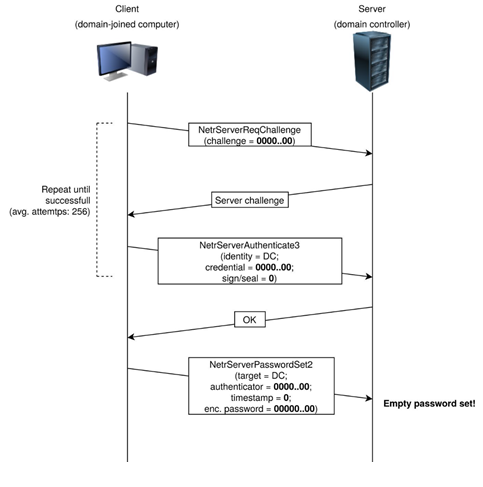 Image source: Secura CVE-2020-1472
Image source: Secura CVE-2020-1472
Protection during solution rollout
Microsoft is addressing the vulnerability in a phased two-part rollout, with a patch already available for part 1. These updates address the vulnerability by modifying how Netlogon handles the usage of secure channels. The second phase of the Windows updates will become available in Q1-2021.
Bitdefender customers are already protected by our end-to-end GravityZone breach avoidance platform which deploys heuristic models to analyze the behavior of the message requests used to compromise the domain controller hosted on the Active Directory. It prevents the adversary from leveraging “living-off-the-land" tools to make system or environment level changes.
The following Bitdefender technologies identify this vulnerability early in the attack kill-chain:
1. Identifying network exploitsBitdefender Network Attack Defense quickly senses exploit attempts such as initial access, discovery, and credential access and prevents an array of attacks from lateral movement, web-service attacks, and traffic-level attacks to privacy breaches performed via phishing attacks to exfiltrate data.
2. Advanced Anti-Malware SecurityPatented machine learning combines security capabilities required to protect against both legacy and modern attacks using technologies including:
- HyperDetect, a tunable machine learning technology, extracts meanings and instructions from command line and scripts
- Process Inspector operates on a zero-trust basis, monitoring running processes and system events
Behavior analytics coupled with event correlation allows for effective remediation actions including terminating the process and rolling back changes.
3. Indicators of RiskBitdefender provides an Integrated, Centralized Endpoint Risk Analytics (ERA) module that provides comprehensive identification and remediation of many network and operating system risks at the endpoint level.
The indicators of risk are grouped into three major categories:
- Misconfigurations
- Vulnerable applications
- Human-based risks
Patch Management creates a flexible and simplified workflow to support both automatic and manual patching for vulnerable applications.
Human Risk Analytics provides details about user behavior while preserving user autonomy to perform their jobs and retaining a measure of privacy for their actions.
If you are looking to secure your infrastructure, get a free, 90-day full product evaluation for GravityZone with our unique, limited time offer.
If you are a service provider, get a free full-featured trial of the multitenant security suite, Bitdefender Cloud Security for MSP
Bitdefender is a technology provider of choice, with 38% of cybersecurity vendors worldwide using one or more Bitdefender technologies. To maintain our high quality and accuracy of detection, Bitdefender remains committed to developing technologies in house, and to maintaining over 50% of its workforce in R&D teams.
tags
Author

Ashish is a Technical Marketing Engineer with Bitdefender. He has a Masters degree in Electrical Engineering from San Jose State University. Ashish enjoys spending his time reading up on threat reports, simulating exploits and producing high-visibility content.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









