Defending the Defenders: Understanding and Preventing Security Analyst Burnout

Cybersecurity professionals occupy the front lines of defense in an era defined by technology and the ever-evolving digital landscape. At the core of many organizations' security is the security operations center (SOC), typically led by a team of seasoned security experts. Among these experts, security analysts act as the initial responders responsible for identifying, detecting, and responding to security threats. Succeeding in this critical field requires a rigorous, analytical, and detail-oriented mindset. Every day, you must sift through the massive amount of data generated by complex systems. It's particularly tough because there can be serious consequences if you miss a real threat or misjudge a security incident. It’s not surprising that these security professionals' strengths and skill sets often come at a price: burnout.
Understanding Burnout
Burnout is an experience that virtually everyone encounters at some point in life. Juggling family responsibilities, maintaining an active social life, fitness routines, dietary considerations, addressing the usual uncertainties of adult life, and professional commitments, all over extended periods, can lead to stress. Prolonged stress exerts a toll on physical, mental, and emotional well-being, manifesting as burnout. Symptoms of burnout can manifest in various forms, including:
- Decreased energy levels
- Reduced motivation
- Loss of appetite
- Withdrawal from social interactions
- Diminished self-confidence and increased self-doubt
- Feeling overwhelmed and unproductive
- Short temper
- Increasingly pessimistic outlook
Burnout among security analysts often stems from the immense pressure of managing investigations, delivering accurate insights, handling complex data, meeting tight deadlines, and managing high workloads. This is exacerbated by the presence of false positives, the lack of contextual information, limited resources, and suboptimal tooling, which compound the responsibilities of analysts. Such stressors are commonplace in a field that frequently attracts overachievers and perfectionists. These stressors begin to stack like a deck of cards and can affect physical and mental health. Without realizing it can cause a ripple effect throughout a security professional’s personal life and career, negatively impacting them.
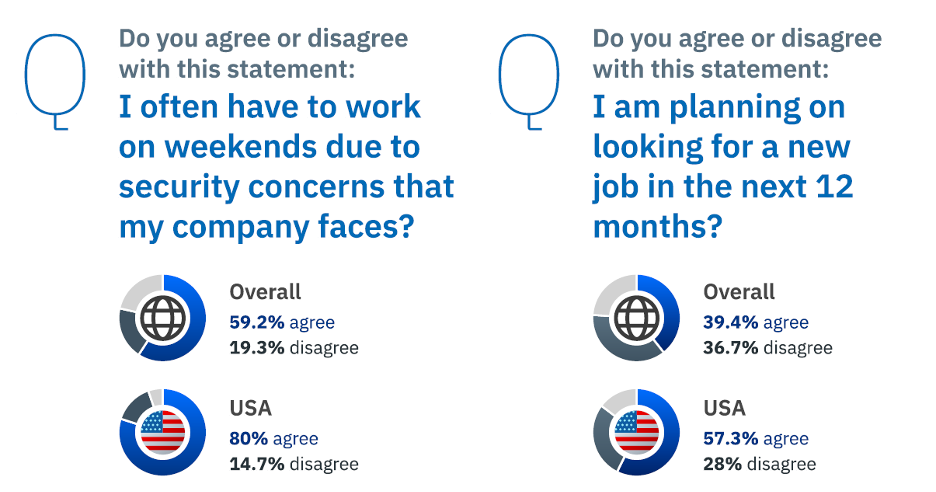
Source: Bitdefender 2023 Cybersecurity Assessment
Several factors in the daily work of security analysts contribute to feelings of burnout. These include:
- False Positives
The prevalence of non-malicious or unactionable alerts and a lack of genuine incidents can desensitize and frustrate analysts, making them feel that their work lacks value. - Technological Limitations
Inadequate or non-optimized tools hinder an analyst's ability to respond effectively to alerts. This can include a lack of automation, inadequate telemetry, and a lack of centralized investigation capabilities. - Lack of Context
Analysts are often required to make quick assessments of activities with limited or no telemetry and contextual information, often due to limitations in visibility or tool functionality. Sometimes these are exacerbated by skills or experience gaps. - Resource Constraints
Scarcity of resources may encompass insufficient tools, a lack of processes and procedures, understaffing, poor communication or support from other teams, inefficient workflows, and funding issues. - High Workloads
Analysts frequently face substantial workloads resulting from report generation, sifting through vast data volumes, false positives, and responding to internal communications.
When analysts experience burnout, their performance in various aspects of their day-to-day workflow is compromised. This can lead to subpar analysis and a failure to adhere to established processes and procedures, creating additional work for their colleagues. In a field where businesses of all sizes depend on SOC protection, accurate, timely, and appropriate analysis is of paramount importance to both analysts and customers.
Managing Burnout from an Individual’s Perspective
William James once said, "The greatest weapon against stress is our ability to choose one thought over another." This underscores the importance of our response to stress and anxiety. Recognizing the early signs of burnout, whether mental, physical, or emotional, is crucial. Once identified, strategies to alleviate burnout symptoms include:
- Scheduled Breaks:Taking regular breaks away from the screen throughout the day.
- Maintaining Sleep Patterns: Ensuring adequate and consistent sleep patterns.
- Physical Activity: Incorporating exercise into daily routines, even short breaks for stretching and walks.
- Taking Time Off: Utilizing vacation time for relaxation and rejuvenation.
- Engaging in Hobbies: Pursuing non-work-related interests to stimulate creativity and reduce stress.
- Open Communication: Discussing challenges with supervisors and exploring alternative work arrangements if necessary.
Everyone is different, and how you can reduce stress and avoid burnout varies from one person to the next. The main thing is to spot the warning signs early and find the right balance to stay in control.
From Self-Care to Organizational Resilience
Each analyst and their managers should look out for their well-being, but it's not a replacement for the whole organization being aware of and fixing this issue. Addressing pain points early and seeking improvements is essential for maintaining team morale. Some of the most cost-effective approaches to achieving this include:
- Choosing the Right Tools
The choice of security tools plays a critical role in reducing analyst burnout. Opt for tools that are highly accurate at identifying threats, minimizing false positives, and providing actionable information. Usage of consolidated platforms (such as Bitdefender GravityZone) is crucial — analysts should not have to juggle multiple consoles to perform their tasks. A unified platform simplifies the workflow, enabling analysts to focus on the task at hand without the distraction of managing disparate tools. - Automation
Automating repetitive tasks to free analysts for more value-added work, fine-tuning alerts, and training. - Process and Procedures
Regularly reviewing and adjusting processes and procedures and conducting tabletop exercises to test changes. - Training
Providing training to enhance knowledge and skills, either through internal mentoring or external vendors. - Effective Management
Proactive leadership that acknowledges and addresses team pressures, ensuring that challenges remain manageable, and the SOC continues to grow.
The Role of 3rd Party MDR Services
In the ever-evolving landscape of cybersecurity, the utilization of third-party managed detection and response (MDR) services has emerged as a strategic imperative. These services serve a dual purpose: as a full replacement for organizations lacking dedicated security experts and as a means of augmenting existing security teams. With pre-approved actions and well-defined rules of engagement, customers can exercise precise control over the workload of their in-house analysts, deciding how much responsibility they wish to delegate to the third-party MDR service.
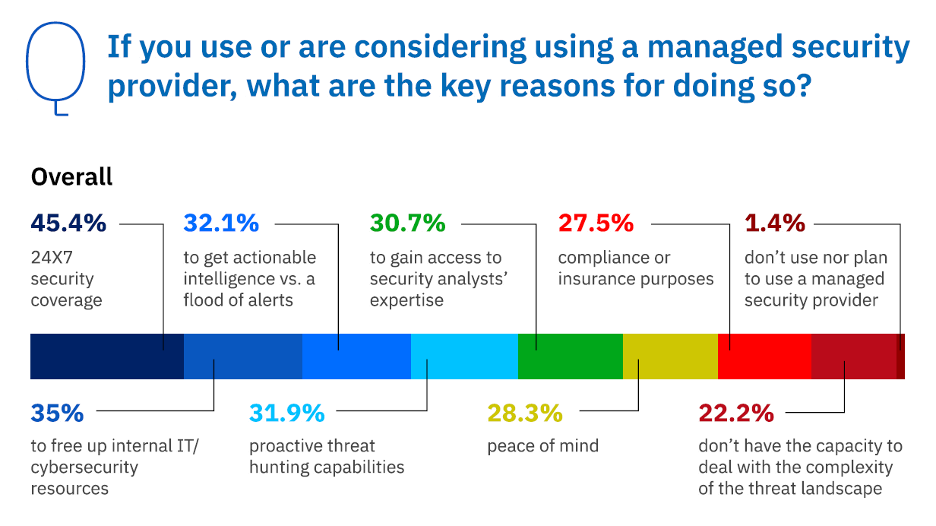
Source: Bitdefender 2023 Cybersecurity Assessment
For organizations that may not have the resources or dedicated in-house security experts, third-party MDR services offer a comprehensive solution. These services effectively step into the role of the security team, taking on the responsibility of safeguarding the organization's digital assets. This includes threat detection, response, and mitigation. By outsourcing their security functions to MDR providers, companies can benefit from specialized expertise without the need to maintain an internal security team. This option is particularly valuable for small and medium-sized enterprises, startups, and organizations operating in resource-constrained environments.
For organizations with established security teams, third-party MDR services offer a way to enhance and complement their existing capabilities. By partnering with MDR providers, these organizations can augment their in-house experts with additional resources, tools, and knowledge. This augmentation can be especially valuable during periods of high workload, such as weekends, holidays, or out-of-business hours. The MDR service becomes an extension of the internal team, providing round-the-clock coverage and threat detection capabilities. This approach empowers existing security experts to focus on strategic initiatives, while routine or high-volume tasks can be managed by the MDR service.
One of the notable advantages of third-party MDR services is the flexibility they offer in workload management. Customers have the autonomy to determine the extent of their engagement with the MDR service, ensuring that it aligns with their specific needs. With well-defined rules of engagement and pre-approved actions, organizations can precisely control which tasks and responsibilities are delegated to the MDR service and which are retained in-house.
This fine-grained control allows organizations to strike the right balance between leveraging external expertise and maintaining internal oversight. It also enables companies to adapt to changing security demands, scaling up or down as needed without the complexity of hiring, training, and onboarding additional in-house personnel.
Bitdefender's 2024 Cybersecurity Assessment report is now available.
tags
Author

Landon is a practiced Security Operations Center (SOC) analyst with two and a half years serving as a cybersecurity analyst and over six years working in technical roles. He has dedicated great effort into the research and documentation of company interview techniques for technical positions and made improving the process one of the focuses of his professional career.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










