Hackers Use XLL Add-ins and Excel to Deploy CABINETRAT Malware in Ukraine

Russian hackers are trying to exploit human trust to spread malware, according to the Computer Emergency Response Team of Ukraine (CERT-UA). A group known as UAC-0245 launched a new campaign late last month targeting the Ukrainian government and defense organizations.
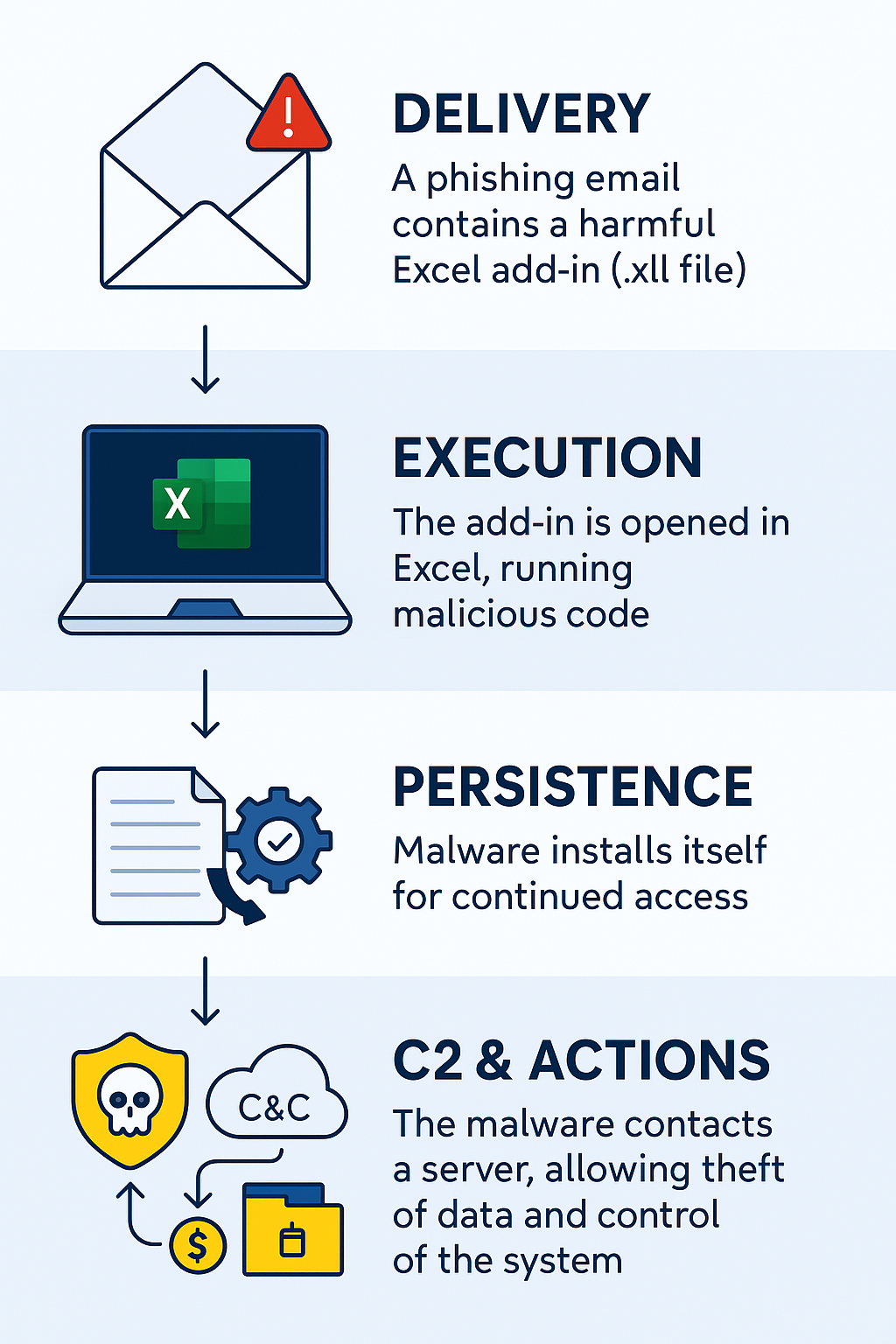
The attackers distributed phishing emails with highly relevant subjects disguised as official military communications.
Hackers are trying to persuade victims to open an attached ZIP file that they say contains important documents. Of course, the ZIP file actually has a malicious Excel add-in file (.XLL) built to deploy the CABINETRAT backdoor.
How the infection takes place
An XLL add-in is a type of plug-in that runs native code inside Microsoft Excel. While this sounds like the more popular method involving macro-based attacks, it’s actually a very different approach. These add-ons don’t rely on VBA scripts or PowerShell.
When the victim opens the file, Excel automatically loads and runs the malicious function xlAutoOpen, giving the attackers immediate control. Moreover, it doesn’t act like a dropper for other malware. Everything needed in the attack is in the ZIP file.
When the victim runs the file, the add-in quietly places a few hidden files directly into the user’s profile folders, such as:
%APPDATA%\Microsoft\Excel\XLSTART\
%APPDATA%\Microsoft\Office\
The malware continues to install itself for persistence by modifying registry keys and by adding entries that let it launch every time Excel or Windows starts. No administrator rights are needed for this attack to succeed.
How CABINETRAT works
Unlike other types of malware, this CABINETRAT (C-based remote access trojan) is built for maximum stealth.
After the system is infected, it starts working in the background. It can:
- Collect and send system information
- Steal files and take screenshots
- Execute remote commands from its operators
- Download or delete files on demand
Communication with the attackers’ servers takes place through custom TCP channels, sometimes using multiple ports in sequence to avoid detection. The transmitted data is compressed with MSZIP, making the traffic harder to analyze.
The lure: fake messages about detained soldiers
CERT-UA’s analysis also shows that the phishing emails exploited sensitive and emotional themes. In one message, the attackers made it look like it was coming from the Ukrainian Military Law Enforcement Service (VSP) and claimed several soldiers had been detained while crossing a border.
As more companies have implemented macro restrictions, the attackers have increasingly used XLL add-ins to bypass security measures. Fortunately, the use of XLL add-ins is also being curtailed by Microsoft, and Excel is blocking untrusted XLL add-ins by default.
How to protect against XLL-based threats
Consumers and organizations can reduce risk by taking the following measures:
- Avoid opening .ZIP or .XLL attachments from unknown or unexpected sources, especially emails
- Disable automatic add-in loading in Excel’s settings
- Keep Microsoft Office and Windows up to date
- Utilize security solutions that can detect all types of attacks, including the latest ones.
- Always verify urgent messages through official communication channels
The full CERT-UA advisory, including technical indicators and file hashes, is available on its website.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







