Researchers hack robotic vehicles to underscore safety risks to humans

Researchers at the University of British Columbia have published a paper outlining several scenarios in which robotic vehicles can be hacked remotely and made to deviate from their expected behavior, potentially putting humans at risk.
Robotic vehicles (RVs) like drones and rovers are designed to allow some degree of deviation from the planned trajectory due to environmental factors such as friction or wind, according to the paper. RVs therefore have a certain threshold for flagging deviations as attack, while sensor noise and actuator defects exacerbate the problem.
Authors Pritam Dash, Mehdi Karimibiuki, and Karthik Pattabiraman decided to probe these attack “windows.” They developed an automated process to learn the thresholds and the tolerances of each system for any arbitrary RV that uses Proportional Integral Derivative (PID) control – the most common control technique.
The trio could carry out targeted attacks against the RV by controlling the deviation introduced and the timing of the attacks. They also show how the attacker can remain stealthy and avoid traditional detection techniques.
“Though the deviations may be small, the consequences of the attacks are severe as they can be performed over a prolonged period of time, and at a time and place of the attacker’s choosing,” the researchers said. “This makes them particularly insidious when RVs are used in safety-critical scenarios.”
Hardcore geeks will undoubtedly find the entire paper interesting. The more casual reader, however, will probably find section 3.2 – Attack Scenarios – most interesting. The section explains the impact of the attacks against RVs in industrial scenarios. Perhaps the most interesting is the Switch Mode scenarios, which can cause a delivery drone to crash intentionally and injure people. From the paper:
“Switch Mode The switch mode attack is a form of false data injection launched at highly vulnerable states in the RV’s mission. Knowing the current mode of operation the attacker can inject malicious code, which is triggered when the RV switches its mode of operation. For instance, when a drone switches to Land mode, a malicious code snippet will overwrite the actuator signals. This will prompt the drone to gain elevation instead of landing, or increase the rotor speed causing the drone to land harder than is safe, potentially resulting in a crash. When such an attack is launched against delivery drones, it may damage packages or may hurt the recipients of the package. Because the attack will not cause the monitoring parameters to exceed the pre-defined threshold, the IDS will not be able to detect it.”
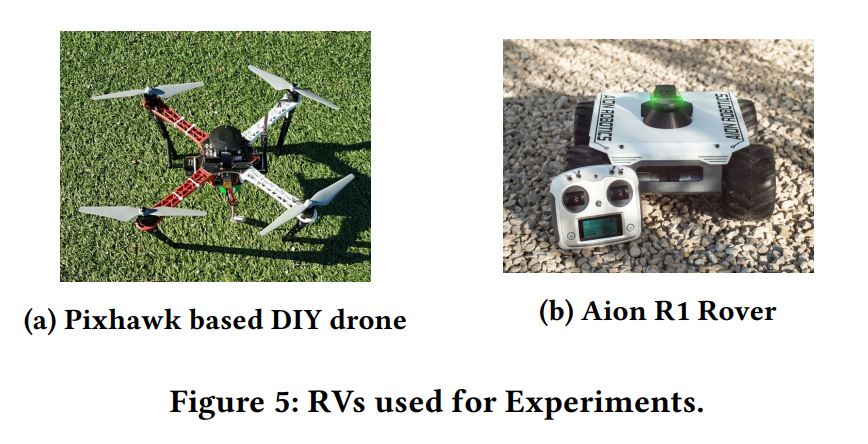
The RVs used for the experiments include a Pixhawk-based DIY drone and the Aion R1 rover, pictured below.
A portion called Countermeasures should help RV vendors looking to design future products with on-board safeguards against the attacks outlined in the paper.
Although these findings are packaged as mere proofs of concept, motivated hackers could conduct such attacks in the near future, as Internet-connected devices spread and our society becomes more automated. According to a projection by Statista, smart/connected devices will number more than 70 billion by 2025. A more conservative forecast from IDC predicts 41.6 billion “things” in 2025, generating 79.4 zettabytes (ZB) of data, which is by no means a small number either.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








