Stream-Jacking 2.0: Deep fakes power account takeovers on YouTube to maximize crypto-doubling scams

As of October 2023, researchers at Bitdefender Labs have been actively keeping tabs on steam-jacking attacks against high-profile YouTube accounts used to conduct a myriad of crypto doubling scams.
Fast forward to 2024; our investigation into the fraudulent takeovers and usage of YouTube accounts has rendered new findings, as financially motivated threat actors meticulously evolve their attacks.
Over the past couple of months, stream-jacking attacks have steadily evolved, and our research shows how cybercriminals advance their craft to maximize the reach and efficiency of their actions with carefully engineered content that closely mimics legitimate cryptocurrency-related news or announcements.
We know that malicious actors often stay on top of popular events in Crypto, and during the last quarter they have made use of multiple announcements to potentially monetize fraudulent livestreams that disguise crypto-doubling scams under popular titles highlighted in mainstream media.
For example, attackers made use of the “SpaceX Starship integrated flight test 2” official event to launch their own fake livestreams under the name SpaceX Launch Starship Flight Test! Elon Musk gives update on Starship! on ‘verified’ compromised channels to add credibility to their ruse. Most of the livestreams we analyzed were also showing signs of artificial boosting of viewers to further increase the trust of potential real viewers.
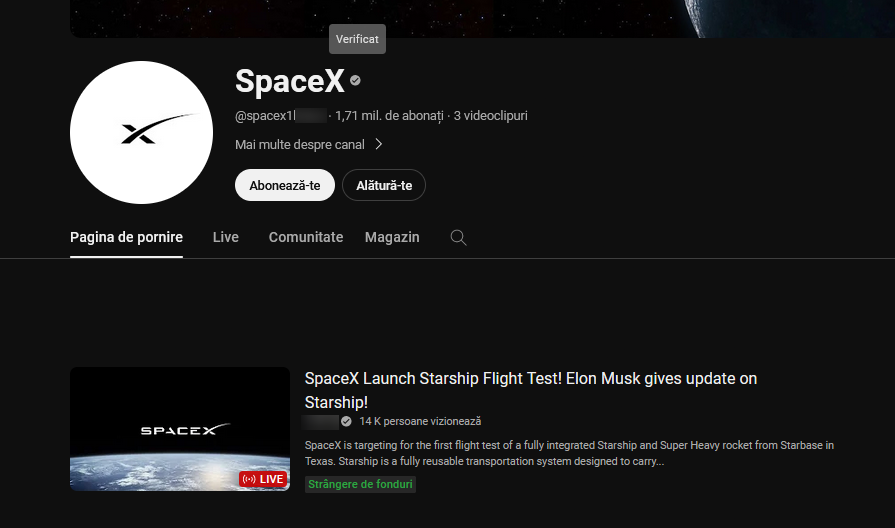
As previously stated, scammers use variants of the name of the impersonated entity on compromised accounts (instead of @SpaceX, @spacex1[..] is observed in the example above).
Other premeditated scams based on official and wide-known events we have found are the following:
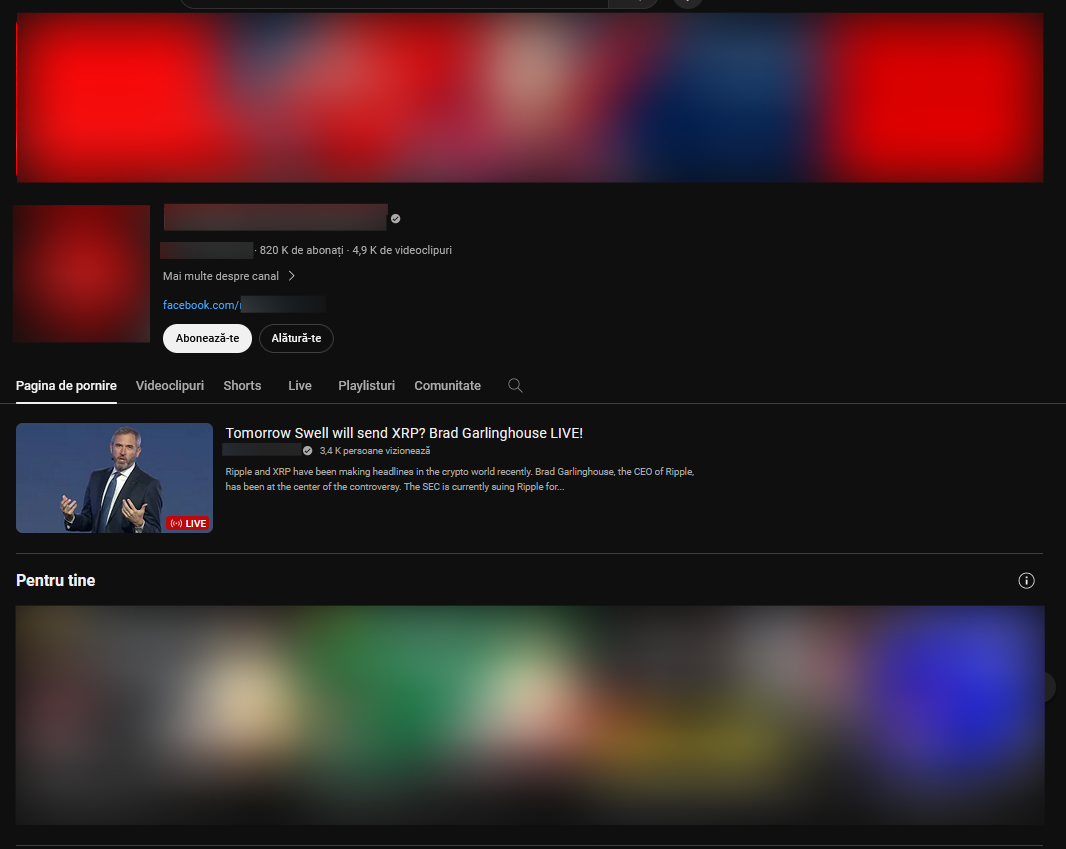
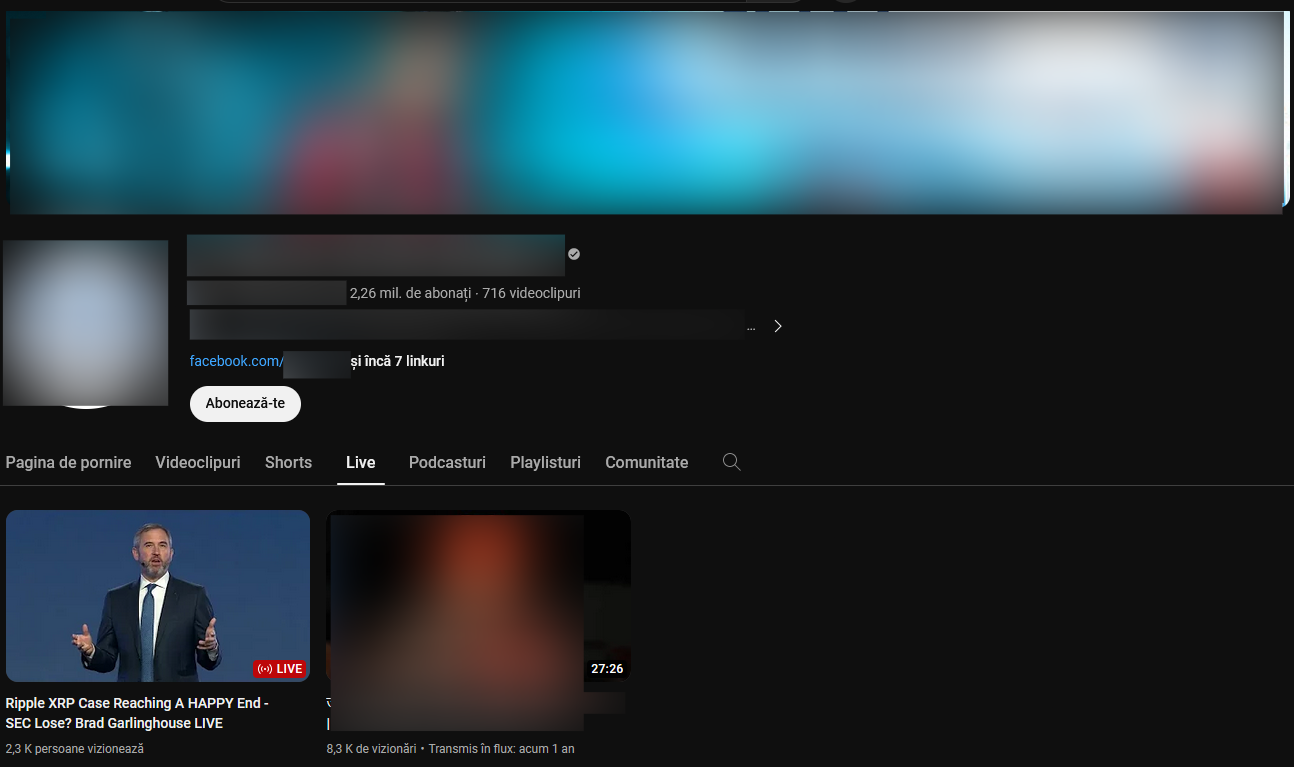
1. Nov. 30 was an important date for the SEC-XRP trial in the world of cryptocurrencies. Before, during and after that date, we noticed multiple fake livestreams with the following titles:
o Ripple XRP Case Reaching A HAPPY End - SEC Lose? Brad Garlinghouse LIVE;
o Ripple XRP BOOM! Case Reaching A HAPPY End - SEC Lose? Brad Garlinghouse LIVE
o Tomorrow Swell will send XRP? Brad Garlinghouse LIVE!
2. The USSF-52 flight
o SpaceX USSF-52 Mission Launch! Elon Musk gives update on Starship!
o USSF-52 Mission Launch SpaceX! Elon Musk gives update on Starship!
3. Changpeng Zhao stepping down from the CEO position of Binance
o Changpeng Zhao: I'm not leaving! I'm free! Today is a big event! Scan the QR code and read the rules
o Bitcoin | BTC news today | ETH price prediction 2024 | Crypto news | ETH moon | Ethereum pump x2 🚀,Changpeng-Zhao LIVE
o Elon Musk: BNB (Binance) CRASH TOMORROW, 21.11.2023",Binance Live
4. The Cybertruck Launch
o Elon Musk Live: Tesla's Cybertruck Debut and Production Insights!
o REVOLUTION: Tesla Van & Minivan - a van that combines Model 3, Model X & Model Y
5. Bitcoin ETF:
o Bitcoin ETF Will Send BTC Price to $1 Million? Michael Saylor LIVE
o Michael Saylor: MicroStrategy Buys Another 16,000 Bitcoin. This is Why Bull Run is INEVITABLE
o Ripple ETF Will Send XRP Price to $40? Brad Garlinghouse LIVE
o Elon Musk: Bitcoin ETF Will Send BTC Price to $1 Million? Tesla LIVE
o Bitcoin Is About To 100X - Michael Saylor's Genius BTC Strategy!
o Michael Saylor: Why Will Bitcoin Cost $200k?! Is Ethereum Expecting A Pump?! X100 BTCÐ
o Michael Saylor - ACCEPTED Bitcoin ETF today! What will happen to BTC in the near future?
o Bitcoin ETF APPROVED!! Bitcoin $1 Million tomorrow! Michael Saylor LIVE
It becomes more obvious that any high-profile news headlines can be used in malicious activities. Over time, the scams evolved from the simple use of the names of famous entities to the coordination of scam campaigns based on real events of interest to online communities.
More importantly, we’ve noticed that at the start of these planned campaigns, a considerable number of the compromised channels have many subscribers (some with more than 1 million and one with as much as 12.5 million) which makes them an ideal vector for threat actors to spread their fraudulent schemes.
The rise of deep fakes reshapes the threat landscape
While the initial iterations of the scams reported in October 2023 used looped videos of famous conference talks or other popular recordings, fraudsters have recently started using deep fake technology to create fake videos of prominent figures in cryptocurrency and adding further credibility to the scams.
A common aspect of these skillfully engineered videos is that they encourage viewers to look for a QR code, scan it and send an amount of crypto to be doubled.
Some of the observed deep fakes are of decent quality and could easily fool an untrained eye. To prevent any victims or wary community members from blowing the lid on the entire operation, the live chat section of the videos is disabled unless you are a selected member of the channel or have been a subscriber for an extended period.
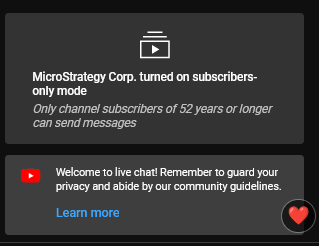
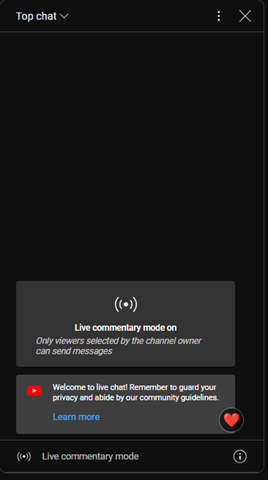
Another new commonality of these deepfakes is that they are sometimes used in YouTube ads instead of malicious livestreams, giving cybercriminals more leeway for spreading the scams (fraudsters can easily pay for these phony ads until they are banned by YouTube).
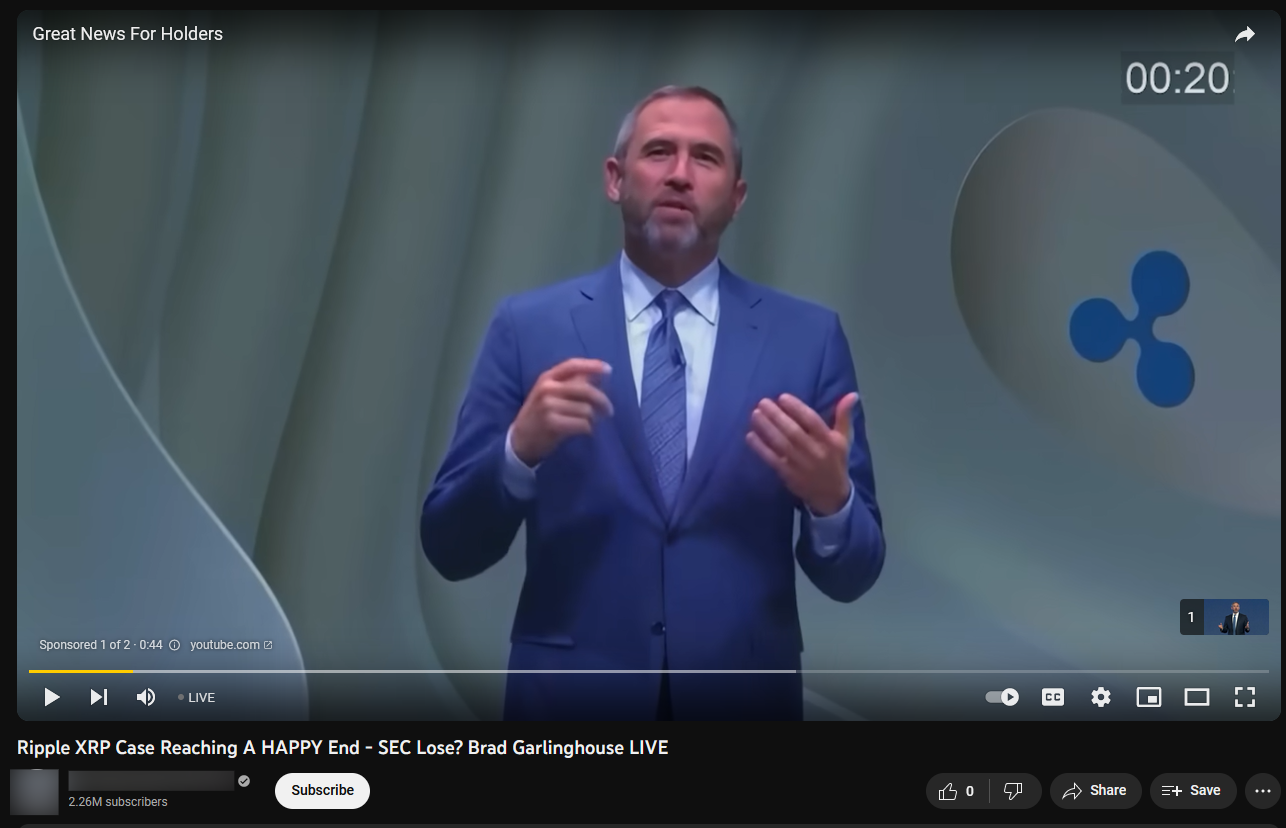
An example of a malicious stream that was also preceded by a malicious ad
While the videos are clearly crafted with deep generative models, the support chats that the malicious websites use do not seem to employ any Large Language Model to answer.
The anatomy of YouTube account takeovers
These account takeovers are usually enabled by the compromise of YouTube access tokens with the use of various stealers. After the access tokens are obtained, the malicious actors proceed with revamping the channel, making it look like it is owned by the entity they want to impersonate. This process is most likely automated and consists of completely changing the original channel by:
- Changing the channel name and handle – even though these are operations that can be done twice every 14 days, hackers manage to do it as it is uncommon for content creators to change names that often;
- Changing the visibility of all videos to private – this is done to conceal previously existing content as it can directly lead to the discovery of the scam;
- Changing the channel avatar and banner – these are replaced with images that represent the impersonated entity;
- Changing or eliminating the channel’s description, links, featured channels and anything that might lead to the identification of the original channel. In some instances, the channel link is set to the malicious website that promotes the crypto doubling scam.
In our research, we’ve observed some takeovers live. An example of this can be seen below.
The name, handle and avatar of the original channel were changed, but previously existing content is still available despite the start of the malicious broadcast:
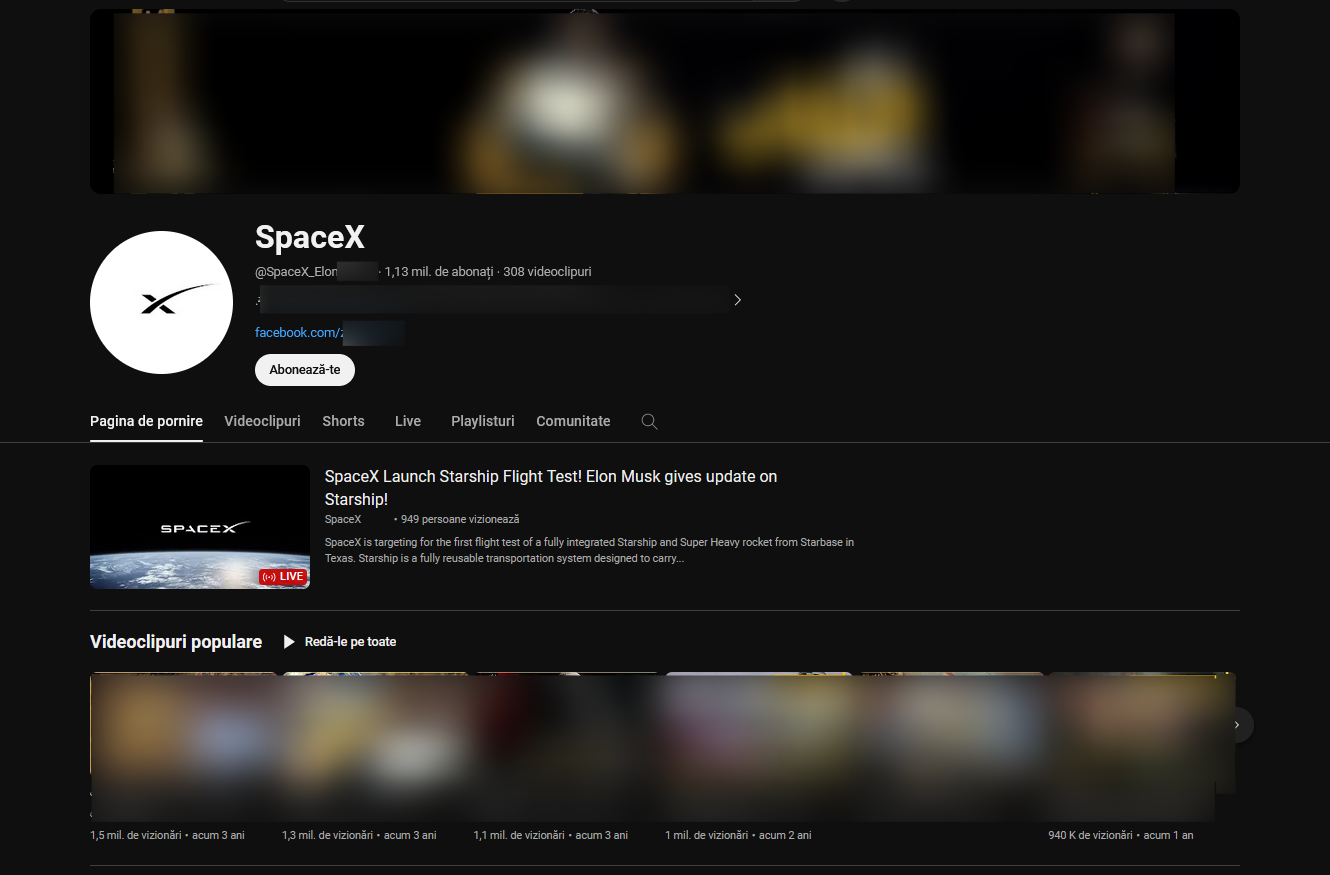
After a couple of minutes, videos were set to private and the banner was also changed, but the channel description and special videos are still displayed:
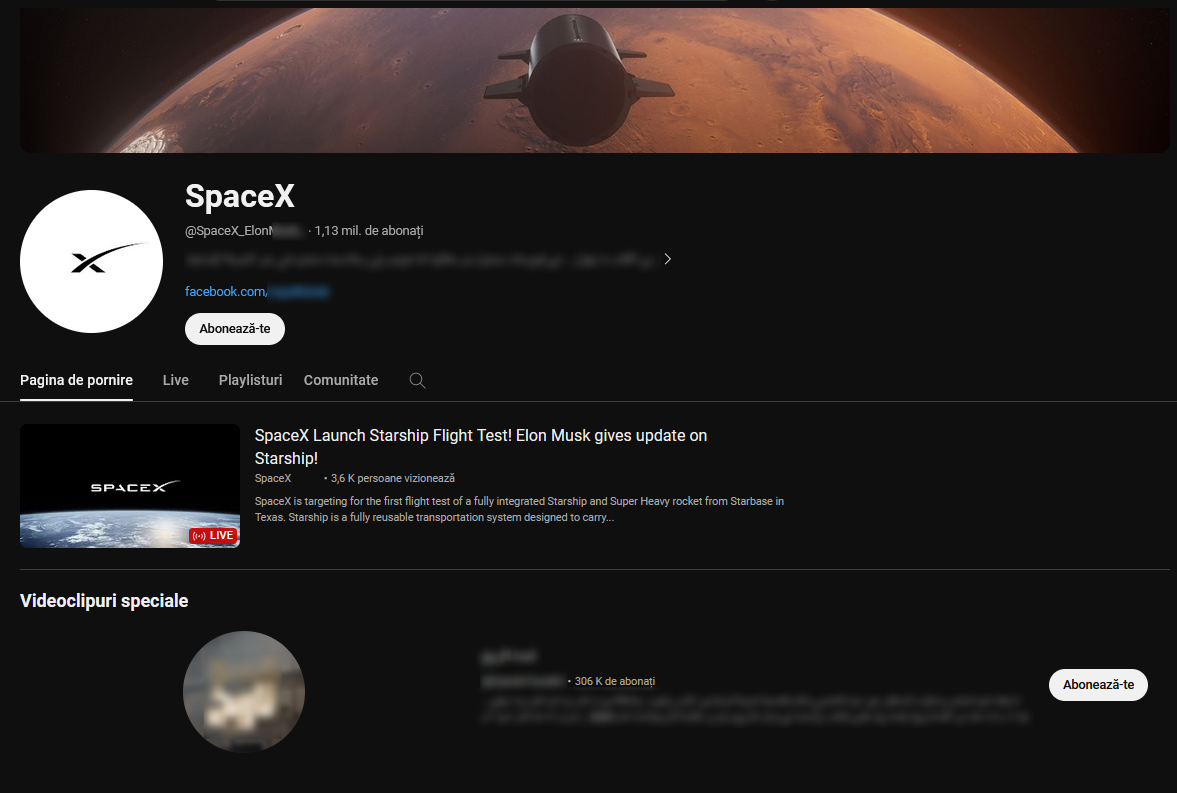
After another couple of minutes, the channel is completely stripped of the original content:
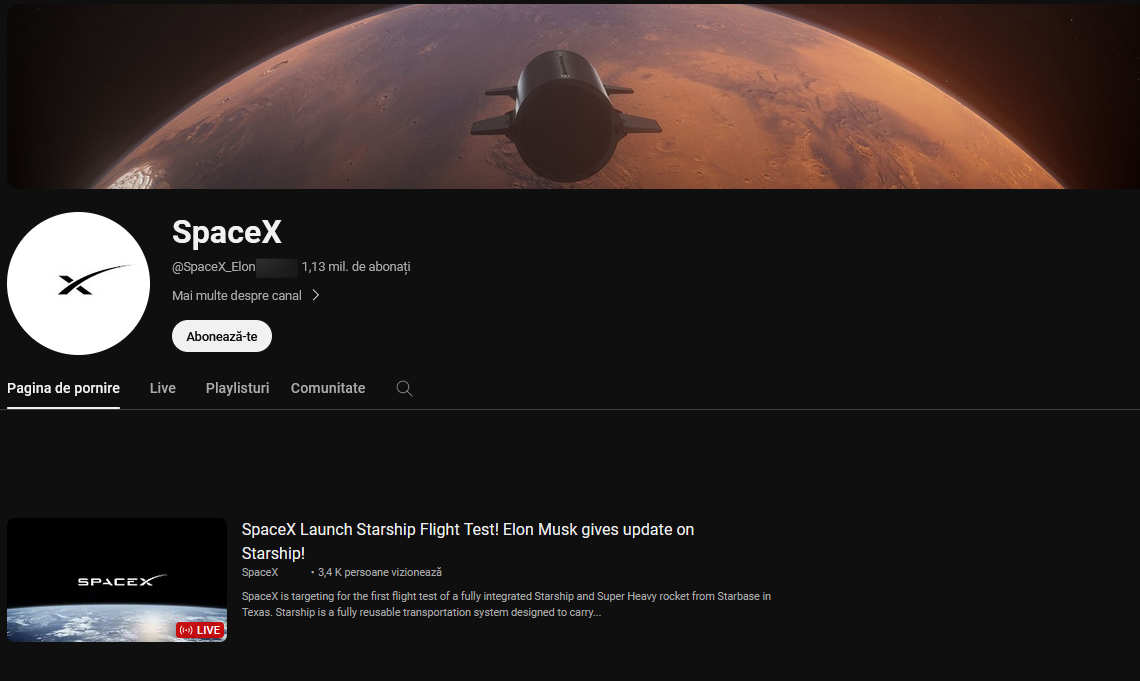
In this case, the definitive version of the compromised channel scarcely looks like the official SpaceX channel:
Sometimes, these transformative operations either take too much to happen (and the channel gets banned before it does) or do not happen at all.
The last wave of scams: MicroStrategy and the Bitcoin ETF
Taking advantage of the heavy news coverage of the Bitcoin ETF, malicious actors started broadcasting scams with the same topic in late December 2023. These scams have MicroStrategy (business intelligence company) and Michael Saylor as central figures, and use titles that refer to the Bitcoin ETF potentially reaching high values to gain traction. Hundreds of malicious broadcasts were observed in the last couple of weeks, qualifying it as one of the most intensive scam campaigns we’ve seen so far.
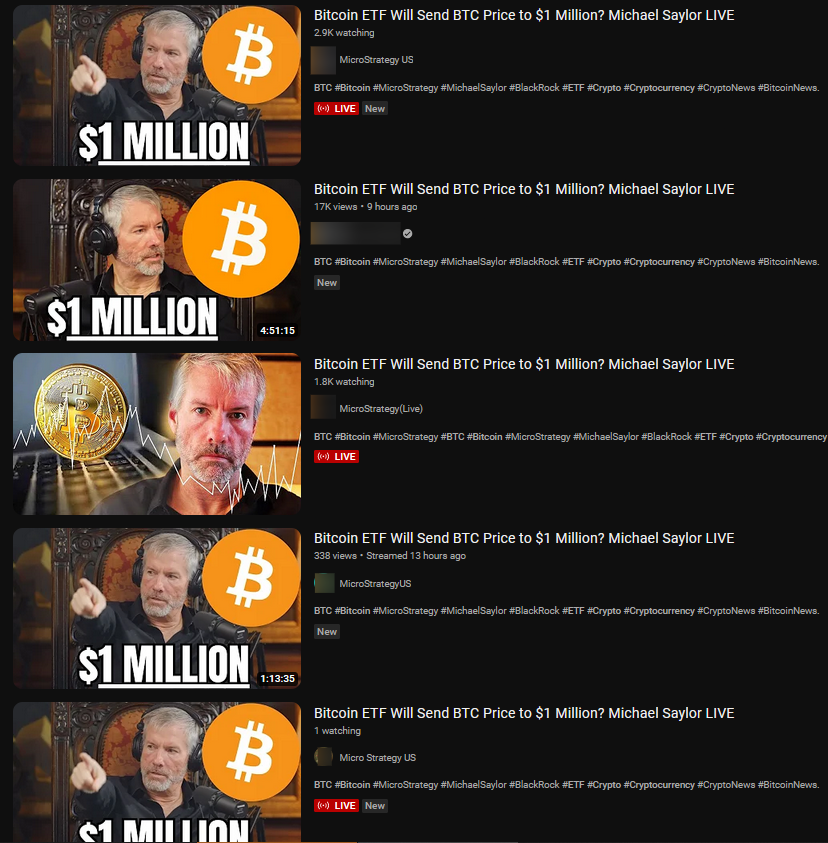
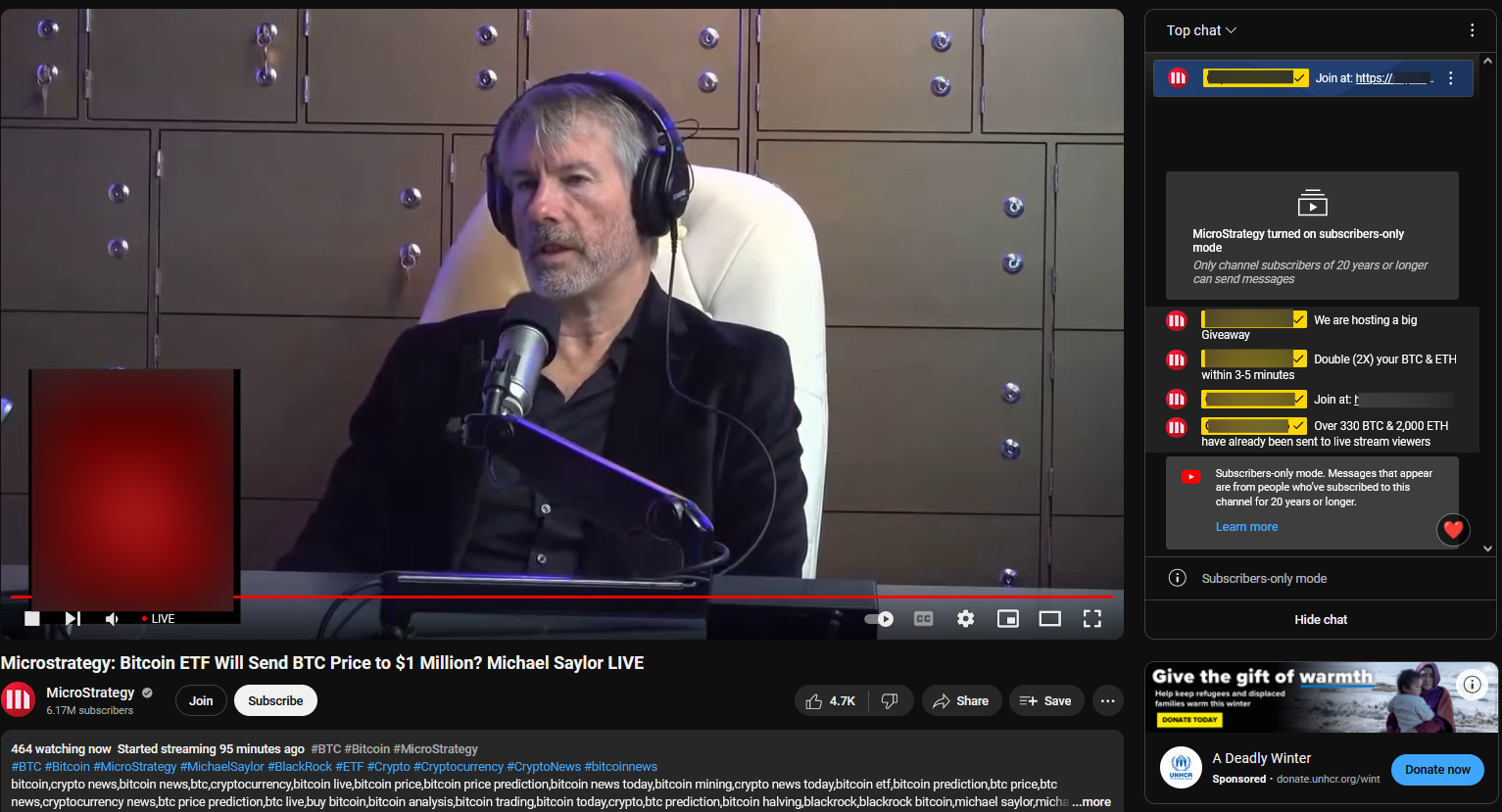
Most of the broadcasts use looped deep fakes in which MicroStrategy’s former CEO encourages the community to “participate in the giveaway” by scanning the QR code and following the instructions found on the website.
The compromised channels use variations of the official MicroStrategy logo as the avatar and the official banner, and some refer to the playlists of the official MicroStrategy channel to boost credibility. The thumbnails of the videos are also common between instances, with limited diversity. The most common name after the takeover is MicroStrategy US and other discovered names are: MicroStrategy, Microstrategy, Microstrategy US, Microstrategy Live, Micro Strategy. The names might include trailing spaces and parentheses (rounded or square) around the US and Live keywords.

The phony websites are usually hosted on domains that resemble the name of the impersonated company or its former CEO, or simpler domains that include the symbols of the cryptocurrencies used in the fake giveaways, along with multipliers such as 2x or x2. These websites also host animations that give users the impression that multiple transactions are taking place live. While it may seem legitimate, these are in fact randomly generated.
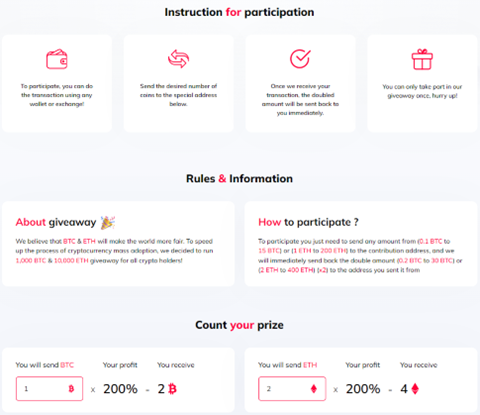
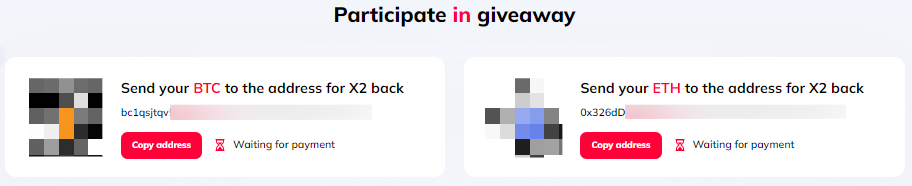
Here are some key insights about what the deepfake Michael Saylor tells viewers in the looped video:
- You don’t need to register on any website. You need to watch the live broadcast online, keep an eye out for the QR code that will appear on the screen and scan it with your phone.
- You don’t need to register on the website to make a Bitcoin deposit. Once you’ve accessed the platform, you’ll be prompted to deposit any amount of Bitcoin.
- After you deposit, our system will automatically send back double the amount of Bitcoin you deposited.
- We’ve ensured that the entire process is smooth and hassle-free to those who are new to the world of cryptocurrencies.
- Our technical support team will be available during the broadcast to assist with any queries or guidance
- Unlike traditional giveaways that rely on chance, our mode is based on a guaranteed outcome. When participants deposit Bitcoin, they automatically receive double.
- The sooner you participate, the better your chance is, as the offer is time sensitive and depends on the availability of the funds allocated for the giveaway.
Updated numbers on the phenomenon
· Maximum number of subscribers of a hijacked account: ~12,500,000 (for one account)
· Maximum number of views of a hijacked account: ~3,869,224,308 (total views/one channel)
· Subscribers count median value: ~3955
· View count of channel median value: ~449,159
· Total number of subscribers from the top 10 hijacked channels: ~62,930,000
· Total number of views from the most viewed 10 hijacked channels: ~17,447,370,155
· According to our analysis, cybercriminals targeted a variety of content creator accounts, including the US (96 accounts), Brazil (75 accounts), India (74 accounts), Indonesia (49 accounts), Mexico (21 accounts), Turkey (15 accounts), Peru (14 accounts), Vietnam (13 accounts), Columbia (12 accounts), the UK (11 accounts), France (9 accounts), Spain (8 accounts, and much more. The number of compromised accounts does not include any accounts already banned by YouTube following malicious/fraudulent broadcasts
All metrics have grown since our last report on the topic, while some even come close to doubling. The alarming growth indicates that this phenomenon is far from eradicated.
Top 10 most subscribed hijacked channels
Channel name when discovered | Subscriber count |
[REDACTED] | 12,500,000 |
Tesla Official | 9,990,000 |
MicroStrategy US | 8,810,000 |
[REDACTED] | 7,700,000 |
[REDACTED] | 6,170,000 |
Tesla (US) | 4,900,000 |
Tesla [Us] | 4,040,000 |
MicroStrategy US | 3,450,000 |
[REDACTED] | 3,120,000 |
Tesla Motors | 2,250,000 |
Top 10 most viewed hijacked channels (total channel views)
Channel name when discovered | View count |
[REDACTED] | 3,869,224,308 |
[REDACTED] | 3,643,275,137 |
MicroStrategy US | 2,438,389,285 |
Tesla [Us] | 1,534,420,831 |
Tesla (US) | 1,486,112,673 |
MicroStrategy US | 1,133,574,051 |
MicroStrategy | 939,742,813 |
Tesla [Us] | 885,682,783 |
ARK Invest | 799,950,043 |
Tesla Official | 716,998,231 |
Top 10 most common channel names after hijack
Channel name | Occurrence count |
Tesla US | 239 |
MicroStrategy US | 158 |
Tesla Live | 149 |
MicroStrategy | 99 |
Tesla (US) | 59 |
Tesla News | 43 |
Tesla [US] | 42 |
SpaceX | 38 |
TESLA [US] | 35 |
TesIa OfficiaI | 32 |
Note: all tops changed drastically after the MicroStrategy-themed campaign started.
Just how profitable are crypto doubling scams?
A crucial question arises after observing the surge of these continuously evolving crypto scams: How much do cybercrooks earn that it is so motivating for them to sustain these scams?
The only possible financial gain is the actual amount of cryptocurrencies that are received in the promoted crypto wallets. As such, we began an investigation of a subset of malicious domains (focusing on the latest trends – XRP, MicroStrategy, SpaceX and Binance) that were promoted in livestreams to get an idea of the actual “profits.” After extracting the identifiers of the promoted crypto wallets, the associated transactions were analyzed, with the following insights:
· Over 10 ETH (Ethereum, having a value per coin between ~$2180 and ~$2690 since January 1,,2024) and 12 BTC (Bitcoin, having a value per coin between ~$42,200 and ~$48,700 since January 1, 2024) were sent to the malicious wallets;
· Most of the wallets had no transactions. This can also be related to the fact that their date of creation is quite recent, so it is likely that the numbers will grow in the future;
· Hackers use well-known measures of passing the tokens through a series of other wallets to complicate future analyses;
· The highest amounts received are almost 6 BTC and 2 ETH.
In total, potential earnings amount to ~$528,200 and ~$600,500 (depending on what date the coins are evaluated), making these malicious operations highly profitable for threat actors. While the analysis solely relies on the transactions received, it is unclear if these transactions are from the actual victims or transactions from other wallets used in this kind of scam. Nonetheless, the numbers are alarming, and the need to raise awareness of such frauds is paramount.
Fighting fire with fire. How Bitdefender’s AI-powered scam detector can help keep users safe from deepfake crypto scams and more
While cybercriminals continue to use technological advancements and AI to create more legitimate-looking messages and videos to defraud internet users, steal personal data and take over their digital lives, we’re working to level the playing field.
Bitdefender Scamio, powered by leading-edge AI and Bitdefender threat protection and detection technologies, acts as a personal scam detection chatbot that can help you defend against fraud attempts you come by via emails, texts, links and even QR codes that may pop up in cryptocurrency livestreams that promise huge returns on investment.
Bitdefender Scamio is extremely easy to use and can be accessed via web browser or Facebook Messenger following the quick setup of a Bitdefender account. It’s completely free and can help individuals immediately counter fraud attempts.
Good cyber-hygiene and vigilance can also boost your online safety. We recommend installing a security solution and always inspecting videos with click-bait messages that encourage immediate Bitcoin deposits for double or triple returns and never scanning QR codes you see in videos or ads promoting cryptocurrency giveaways.
You can read more about how to keep YouTube accounts safe from hijackers and preventing crypto doubling scams in our dedicated guide.
If you ever observe content promoting giveaways or other events from well-known companies, always make sure to double-check the promotions on official websites. The ones discussed in the present material are the following:
· https://www.microstrategy.com/
And the associated YouTube channels:
· https://www.youtube.com/@microstrategy
· https://www.youtube.com/@BinanceYoutube
· https://www.youtube.com/@SpaceX
· https://www.youtube.com/@Ripple
· https://www.youtube.com/@tesla
Always keep an eye out for the identifier of the channel – if it contains unexpected characters or misspellings, it is almost certain that it is the case of an impersonation. Always report observed scams to aid in keeping the phenomenon under control. Also, keep an eye on various social media feeds, as these scams are usually denounced and detailed there – for example, Twitter/X posts about the MicroStrategy YouTube scams are common.
tags
Author

I'm a software engineer with a passion for cybersecurity & digital privacy.
View all posts
With over a decade of cybersecurity experience both developing and leading developers, and a passion in building things from scratch, I always look forward to the next challenge to sharpen my skills.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















