Paradise Ransomware decryption tool

We’re happy to announce a new decryptor for Paradise Ransomware.
Paradise Ransomware, initially spotted in 2017, has been aggressively marketed as a service to interested affiliates. After infection, it checks whether the keyboard language is set to Russian, Kazakh, Belarus or Ukrainian and, if so, exits without encrypting. Otherwise, it encrypts files and deletes shadow copies to prevent the user from restoring them.
After encryption, it displays a ransom message:
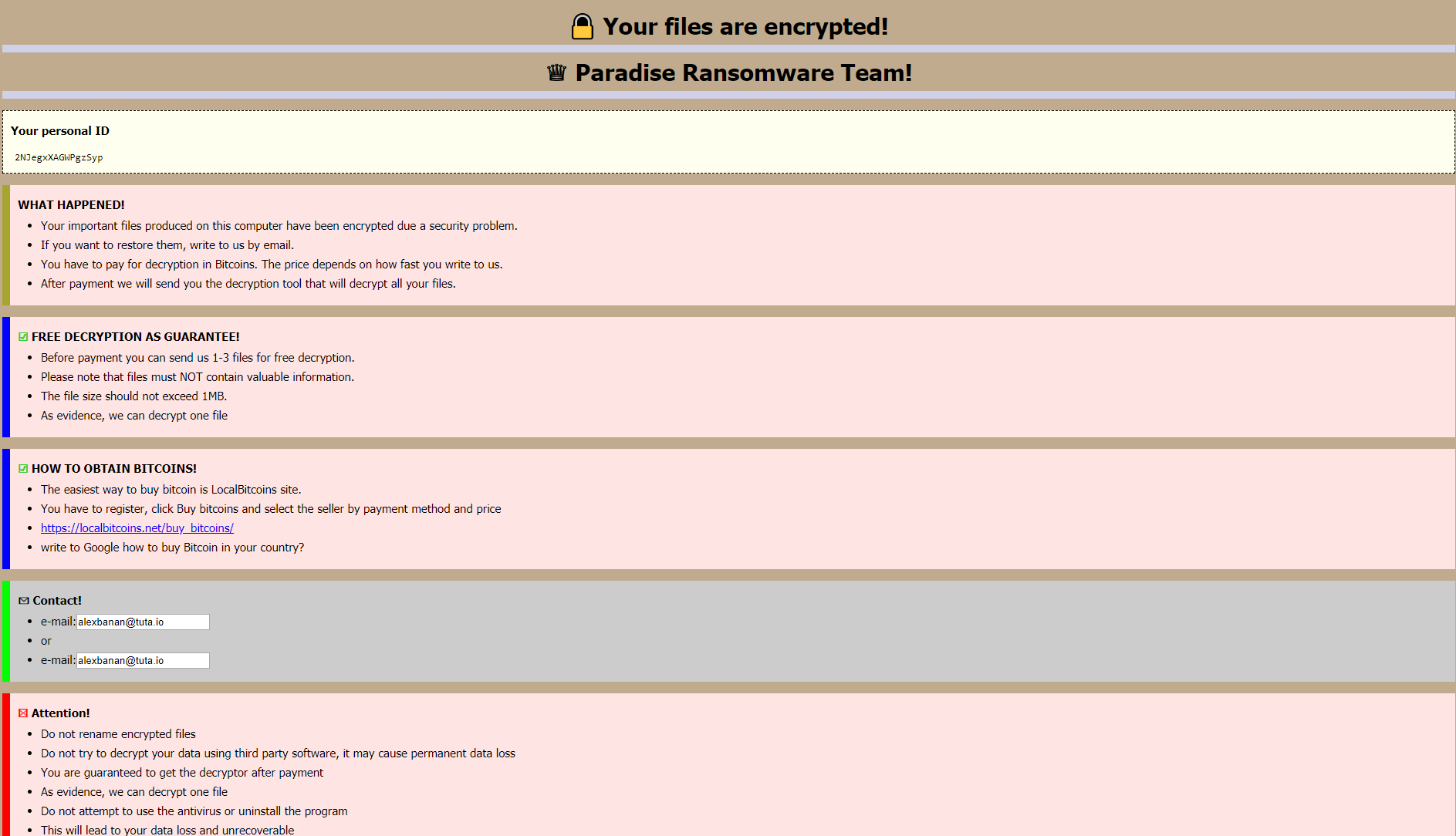
The new Bitdefender decryptor can restore the following file extensions:
. FC, . 2ksys19, . p3rf0rm4, . Recognizer, . VACv2, . paradise, . CORP, .immortal, . exploit, . prt, . STUB, . sev, . sambo
How to use this tool
Step 1: Download the decryption tool below and save it on your computer.
Download the Paradise decryptor
Note: This tool does not require an active internet connection.
Step 2: Double-click the file (previously saved as BDParadiseDecryptor.exe ) and allow it to run by clicking Yes in the UAC prompt.
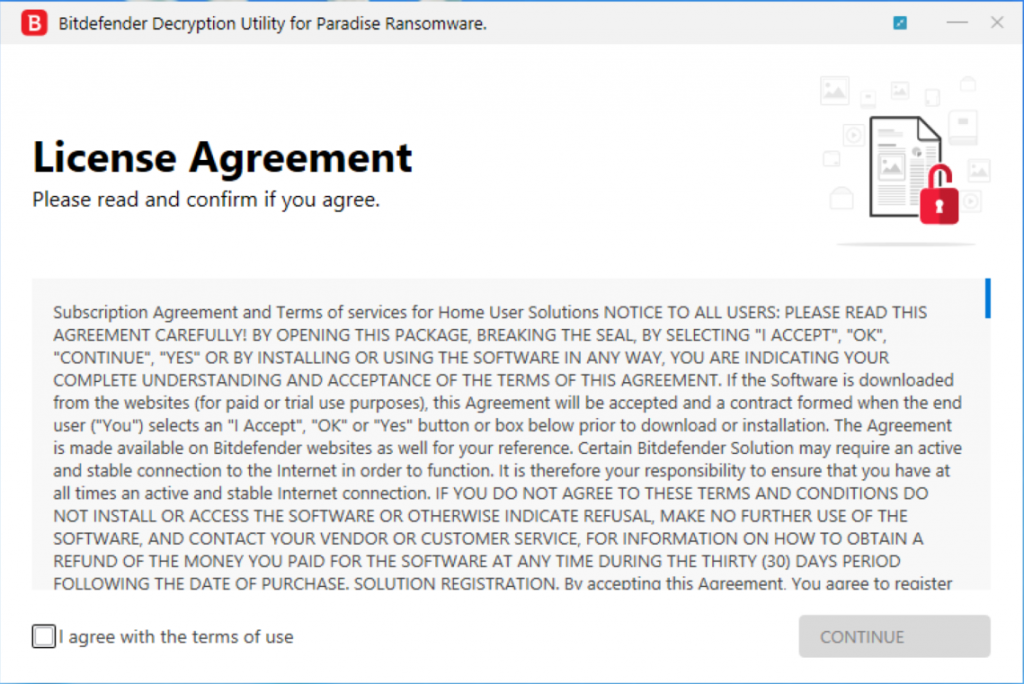
Step 3: Agree to the End User License Agreement
We strongly recommend you also select “Backup files” before starting the decryption process, in case anything occurs while decrypting. Then press “Scan”.
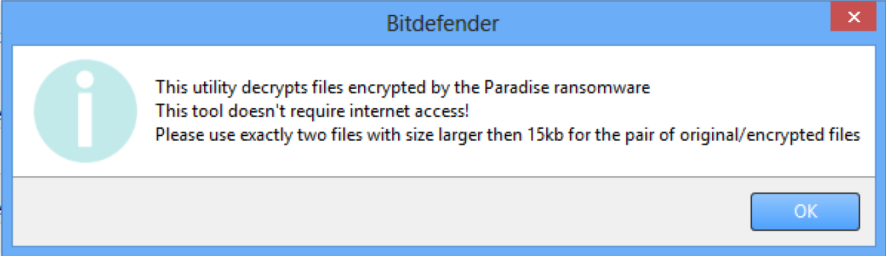
The “test folder” must contain a pair of original/encrypted files, which will be used to determine the decryption key. It is essential that this folder only contain a pair of original and encrypted files and both files should be at least 15 kb in size.
Users may also check the “Overwrite existing clean files” option under “Advanced options” so the tool will overwrite possible clean files present with their decrypted equivalent.
At the end of this step, your files should have been decrypted.
If you encounter any issues, please contact us at [email protected].
If you checked the backup option, you will see both the encrypted and decrypted files. You can also find a log describing the decryption process, in %temp%\BDRemovalTool folder:
To get rid of your encrypted files after decryption, just search for files matching the extension and remove them in bulk. We do not encourage you to do this, unless you have double-checked that your files can be opened safely and none of the decrypted files are damaged.
Silent execution (via cmdline)
The tool can also be executed silently via a command line. If you need to automate deployment of the tool inside a large network, you might want to use this feature.
- -help – provides information on how to run the tool silently (this information will be written in the log file, not on console)
- start - this argument allows the tool to run silently (no GUI)
- –path - this argument specifies the path to scan
- –test - this argument specifies the test path to a pair of original/encrypted files
- o0:1 - enables Scan entire system option (ignoring -path argument)
- o1:1 - enables Backup files option
- o2:1 - enables Overwrite existing files option
Examples:
BDParadiseDecryptor.exe start -path:”C:\” -> the tool will start with no GUI and scan C:\
BDParadiseDecryptor.exe start o0:1 -> the tool will start with no GUI and scan the entire system
BDParadiseDecryptor.exe start o0:1 o1:1 o2:1 -> the tool will scan the entire system, backup encrypted files and overwrite present clean files
Acknowledgement:
This product includes software developed by the OpenSSL Project, for use in the OpenSSL Toolkit (http://www.openssl.org/)
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks














