New Homograph Phishing Attack Impersonates Bank of Valletta, Leverages Valid TLS Certificate
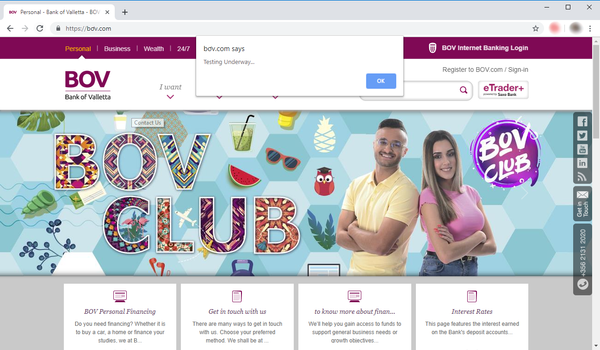
Bitdefender researchers recently uncovered a new IDN (internationalized domain name) homograph phishing attack in which attackers impersonate the Bank of Valletta, Malta. Bitdefender’s Deep Learning technologies, trained specifically to spot this type of homograph attack, quickly flagged the website for phishing. They triggered an investigation from our teams to better understand the mechanics behind it.
Key findings:
- Homograph phishing attack targeting a bank
- Uses a valid TLS certificate to generate trust
- Displays a Microsoft Account popup to harvest credentials
Quality Phishing
IDN homograph attacks are not new. They use characters that look almost the same, such as the Greek Ο, the Latin O, and the Cyrillic О, but have a very different Unicode value. For example, while “bankofamerica.com” might closely resemble “bankofamericà.com” to the untrained eye, the second has a Latin small letter “a” with grave. This means attackers can register similar-looking domains in which some letters have been replaced by homographs in another alphabet.
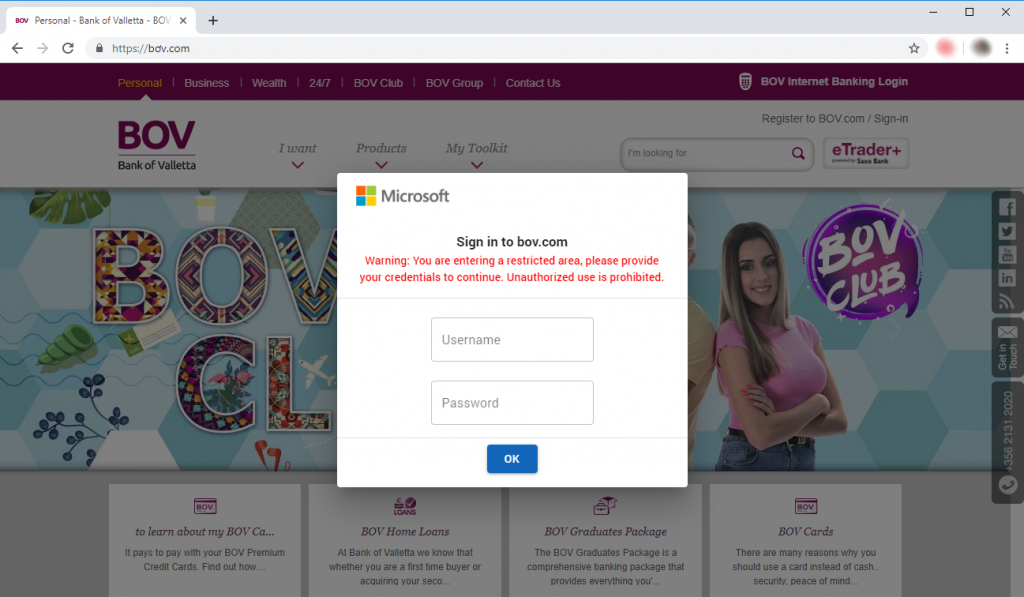
The Bank of Valletta phishing website seems to be an accurate knockoff of the legitimate website, at least when opening the main page. Shortly afterwards, users are prompted with what appears to be a Microsoft dialog box asking for a username and password to access a restricted area. While this is clearly not something the legitimate website displays, it seems attackers are using this dialog box to potentially collect Microsoft Account credentials from Bank of Valletta website visitors.
After clicking “OK”, users are left with a seemingly legitimate website, unless they start clicking through links and menus. Once users decide to leave the home page, a message saying “Testing Underway…” is soon displayed, preventing users from ever reaching any other content apart from the content displayed on the phishing home page.
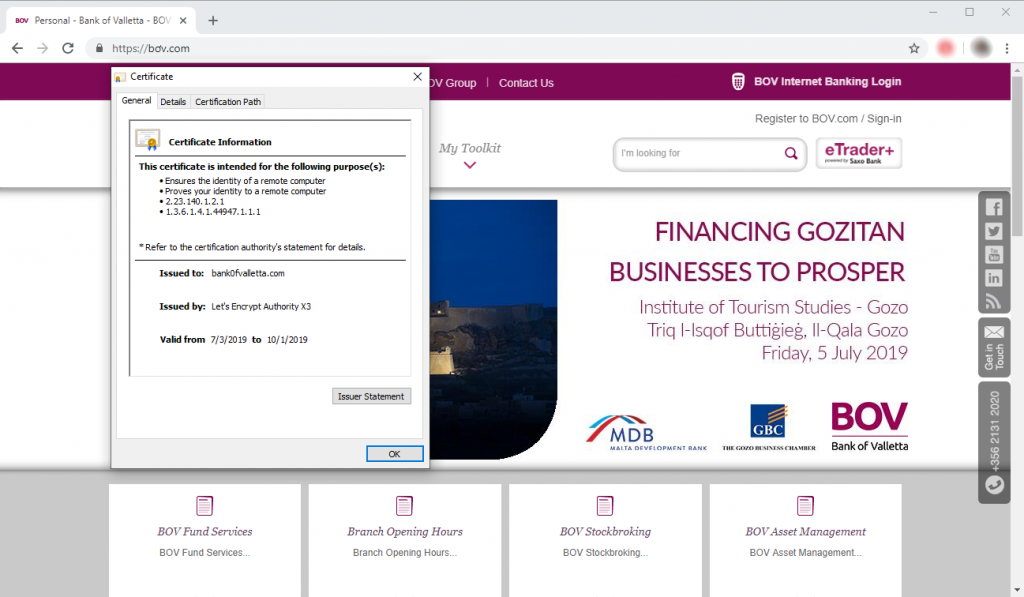
Interestingly, the phishing domain also bears a valid digital certificate issued by Let’s Encrypt that seems to be valid until October 1st 2019. The CA (Certificate Authority) authority usually issues free certificates that are valid for a limited time, usually around 90 days, indicating that these scammers want to seem legitimate without investing too much or giving away any information that can be traced back to them.
Adding a valid certificate to a domain is also a good way to eliminate any security warning displayed by browsers when visiting unencrypted websites or to trick less-tech-savvy users into believing the website is indeed legitimate. Abusing a legitimate CA (Certificate Authority) and using a legitimate certificate to run a phishing website may suggest that attackers could be aiming for a qualitative attack rather than a quantitative one.
While the valid certificate might expire in 90 days, this may be enough time for attackers to test and plan their spear phishing attack before they get reported.
When searching for domains related to the one found in the certificate, our team found four others that share the same homograph attack scheme:
DNS Name: bank0fvalletta.com
DNS Name: www.xn--bv-2ya.com
DNS Name: xn--bv-2ya.com
DNS Name: xn--ov-blb.com
Conclusions and Recommendations
What makes this phishing website interesting is that its domain name is perfectly similar to that of the legitimate bank – users might dismiss the grave on top of the “ơ” as a smudge on their screen.
The use of valid certificates is yet another interesting aspect not usually associated with mass phishing campaigns. This might suggest that attackers are narrowing down their victim pool to a handful of “candidates”, potentially to hijack their Microsoft Accounts.
To steer clear of these types of attacks, users are strongly encouraged to install a security solution that can look beyond the telltale signs of a phishing website and prevent them from accessing fraudulent, phishing, or malicious websites. It’s also recommended to exercise caution when clicking on URLs – even though they might seem legitimate – and submitting data that could be considered critical.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








