Adware-Packed Fake Apps Still Making Their Way to Google Play
Adware is nothing new, nor will it go away any time soon, especially since it’s a legitimate means for app developers to generate revenue. When it comes to Android, “borderline legitimate” is the tagline that developers commonly abuse to smuggle seemingly legitimate applications into official marketplaces, such as Google Play.
While displaying ads is not considered malicious per se, when the app goes out of its way to hide its presence on the device, then push full-screen ads on your device even when you’re not in the app, they become less of a nuisance that you can quickly uninstall, and more of a pain that makes it difficult to have a decent user experience with your Android device.
Bitdefender researchers recently uncovered three new apps in Google Play that seem to behave a lot like Trojans or Spyware in the way they hide on devices, but restrain themselves to displaying full-screen adds every 15 minutes.
Key Findings:
- More than 10,000+ downloads each, during at least 3 months of activity
- They change their name and launcher icons in the Apps menu to impede uninstallation
- All 3 fake apps hide their presence if the device has an internet connection.
- They display full-screen ads every 15 minutes, but only starting 24 hours after installation
- If no internet connection is present after install, the apps actually perform as advertised
- Potentially the same developer behind all three
This little … app went to market
The three Android apps (com.colors.drawing.coloring, hd4k.wallpapers.backgrounds, and launcher.call.recorder) seem to have been flagged as malicious starting early May 2019, although they were present in Google Play for at least three months prior to that. Each one seems to have amassed more than 10,000 downloads, according to stats posted on their official pages (now taken offline).
While these stats don’t necessarily mean that the apps behaved illicitly from the moment they reached the official marketplace, it does suggest that, somewhere along the way, they were updated with borderline legitimate functionalities that made it past Google’s app vetting system.
Unlike other apps that display aggressive adware, these three actually have full-fledged functionality embedded – potentially signaling that they were completely legitimate when they were submitted for vetting – provided that when you first launch the app they don’t detect an active internet connection.
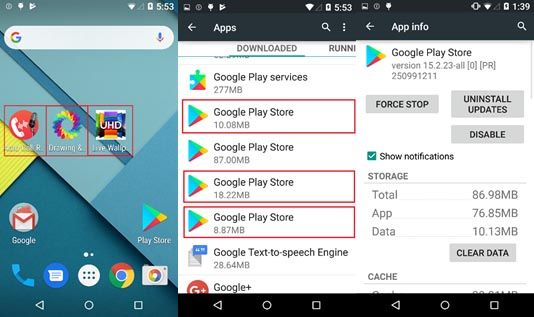
When the apps are first installed, they set their settings icon to the Google Play logo, while also changing their settings name to Google Play Store, potentially making it difficult for the untrained and not-so-tech-savvy user to spot the apps and uninstall them. This is a common practice for borderline legitimate apps seeking to ensure their persistence on the device, using names and icons usually associated with legitimate processes and applications to discourage uses to remove them.

While strange behavior for a Google Play application, the fact that it will run normally if it has no internet connection when first executed may signal that the developer intended for non-internet connected users to at least use the apps’ functionality. A user with no internet connection cannot be monetized through ads, so at least the victim might have some peace of mind.
However, if the application connects to the internet, it will hide its icon and close after 5 seconds, displaying an “Uninstall finished.” or “This app is incompatible with your device!” message. At the same time, it will open the Google Play store to an app already installed on the device, such as Google Maps, in an attempt to confuse the victim.

The app will also set an alarm with a 24-hour delay. When this alarm is triggered, a new class OneWork is executed. This class sets one alarm with a 15-minute delay and another with a 24-hour delay. The 15-minute alarm will start the class AdWorker, which starts an overlay add. From this point on, it will reschedule itself every 15 minutes, ensuring that the ads are constantly displayed on the victim’s device. The 24-hour alarm will start the class GpWorker, which will redo the referral part – possibly to make sure that referral code is not lost or flushed – and it also reschedules itself once every 24 hours.

Most ads involve other applications and games that are part of the referral service to which the developer is subscribed, enticing users to install them.

While the three apps were published under different developer names, it’s plausible they’re all the work of the same coder, especially because they share striking similarities in the way they operate and methods used to hide their presence on the device. While the three apps don’t cross-promote each other in the ads displayed, creating multiple developer accounts is not uncommon, especially when trying to push “borderline legitimate” apps in the official Google Play marketplace.
It’s difficult to tell for sure when these apps made it onto the official marketplace. We took a closer look at when the certificates for each application were generated and it’s safe to estimate that, it couldn’t have been more than a couple of months from the moment the certificate was generated until the app was posted online. In that respect, the oldest certificate for the analyzed apps seems to have been generated on April 21st 2019. While the apps have since been taken offline and the developer/developers don’t seem to have posted anything else yet, it’s likely that other similar apps will eventually make their way into Google Play.
Stay Safe
Staying safe from apps, even shady ones downloaded from official marketplaces, is a matter of installing a security mobile security solution that can detect and block such apps from being installed on devices. It’s also wise to read through commends to find out if some users have had problems with the application. Also, reporting any apps that display suspicious behavior could be considered best practice.
A full-fledged mobile security solution can also accurately protecting you from malicious apps installed from third-party marketplaces and from visiting phishing or fraudulent websites.
| MD5 | Package Name |
| f0b25652b03fbc319abc74eaeaabc330 | launcher.call.recorder |
| 0e1542aa9f6d00fd8e92d8b8154d7326 | launcher.call.recorder |
| 2b87892496de66cd6de63d8e69c370c8 | com.colors.drawing.coloring |
| fb59d70e2afd02de713489a0a0df72ac | launcher.call.recorder |
| 0d3378057340f15ce18745c06ffb2f69 | com.colors.drawing.coloring |
| 19d56b41b84acc4bb63a57ea30881390 | launcher.call.recorder |
| 99a82f0e04597976b165b20cbac86261 | hd4k.wallpapers.backgrounds |
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













