Why Are Potentially Unwanted Applications (PUA) Considered Dangerous?

Potentially Unwanted Applications, or PUAs, walk the thin line between nuisance and malware. While PUAs mainly just hog system resources, they often also display aggressive ads, collect data without your consent, and may even perform secondary downloads that might hide actual cyber threats.
Bitdefender telemetry shows that PUAs make up around a third of all threats directed at Windows and macOS systems. PUA operators target large territories with massive user bases. The US, Europe and Latin America are bombarded the most, our data shows.
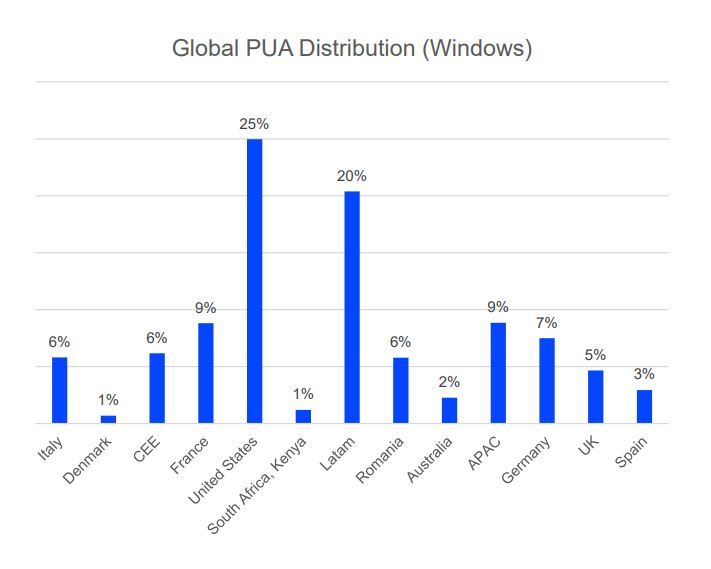
Global PUA distribution (Windows)
Credit: Bitdefender
PUAs are most commonly found as freeware, repackaged applications, system cleaners or other utilities with hidden functionality like data tracking and even coin mining. Others hijack the user’s browser, altering its functionality – like changing the default search engine and installing plugins – without consent.
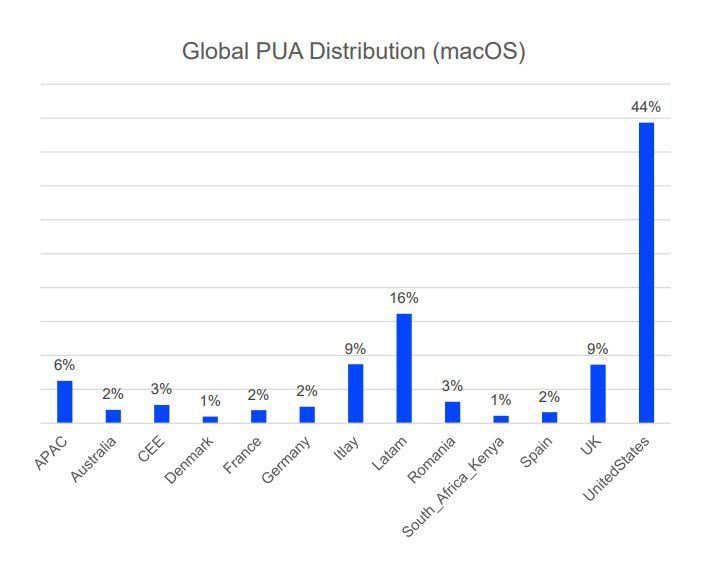
Global PUA Distribution (macOS)
Credit: Bitdefender
Some of the most aggressive PUAs can modify third-party apps, download additional software behind the scenes, or alter system settings – which can mushroom into actual security and privacy issues.
Equally nefarious are the scareware-type PUAs that display exaggerated or bogus notifications claiming the system is exhibiting problems that require immediate attention. Typically, the software claims to have a solution for the problem – but that solution sits behind a paywall. Under the hood, the software lacks the code to perform the alleged fixes. Plus, the problem it claims your computer exhibits likely isn’t even real.
Other PUAs display excessive ads, causing a fragmented experience and overall annoyance. These bad-user-experience apps typically permeate the Android ecosystem, but many can also be found in Apple’s walled garden, the iOS App Store.
Bundling PUAs are also common. They install other apps and plugins the user may not want. These PUAs are also considered quite dangerous, as they don’t disclose their real purpose or behavior upfront, meaning they might also covertly collect data and send it to some unknown server. Another telltale sign that you’re dealing with a typical PUA is a lack of conventional means to uninstall the software.
Modern security solutions are equipped to detect these undesirable experiences and can help you steer clear of shady apps. Bitdefender offers the right tool for this job on both desktop and mobile platforms.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








