Ukrainian Cyber Alliance Disrupts Trigona Ransomware Operations, Exfiltrates Key Data

A group of Ukrainian cyber activists known as the Ukrainian Cyber Alliance (UCA) has infiltrated and dismantled the operations of the nefarious Trigona ransomware gang.
Using a public exploit, the UCA penetrated Trigona's defenses, exfiltrating crucial data before erasing the servers, a move aimed at crippling the ransomware gang's illicit activities.
Exploiting a Critical Vulnerability
Leveraging a known vulnerability, CVE-2023-22515, in the Confluence Data Center and Server systems, the UCA members managed to escalate privileges remotely on the compromised systems.
This vulnerability had been exploited as a zero-day since Sept. 14 by at least one other malicious group, known as DarkShadow, Oro0lxy, or Storm-0062, highlighting the flaw’s destructive potential.
Breaching Trigona’s Infrastructure
Upon gaining access, the UCA mapped out Trigona's entire infrastructure undetected and established persistence in their network.
This thorough reconnaissance enabled the stealthy extraction of valuable data, including database records, source code and potentially the coveted decryption keys that could help unlock victims' encrypted files.
Exposing the Ransomware Gang
A UCA activist, herm1t, showcased the operation's success by sharing screenshots of Trigona's internal documents on X (formerly Twitter). "Trigone. The servers of the Trigona ransomware gang has been exfiltrated and wiped out by @UCA_ruhate_ Welcome to the world you created for others!," the post exclaimed.
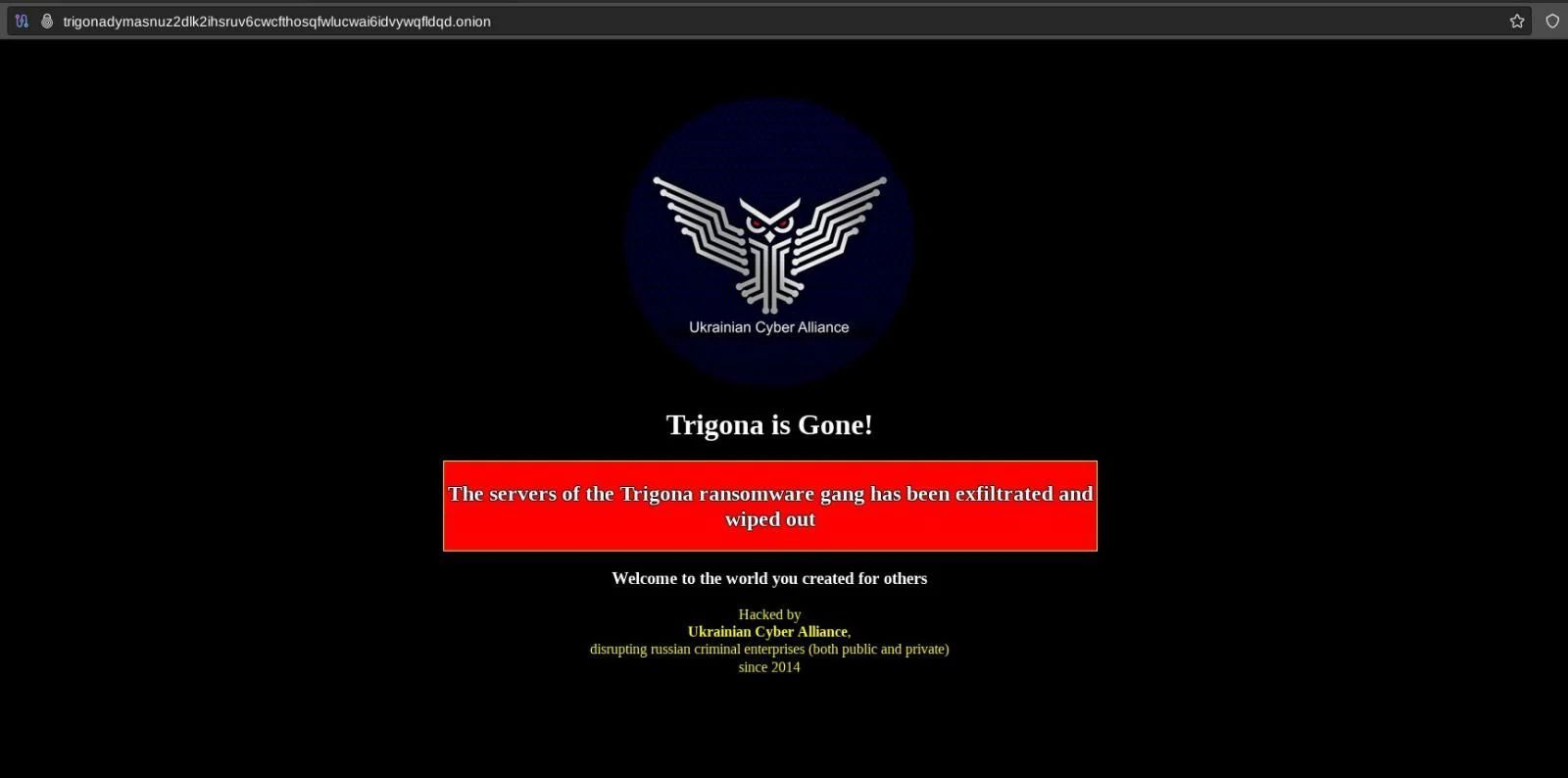
This revelation sent shockwaves through the cyber underworld, momentarily unmasking the shadowy figures behind Trigona.
Trigona’s Futile Retaliation
Trigona's frantic attempts to salvage the situation after the breach proved futile as they scrambled to change passwords and take their public infrastructure offline.
The UCA had already exfiltrated all pertinent information from Trigona's administration and victim panels, internal tools, and even their cryptocurrency hot wallets.
The Aftermath
Following the data exfiltration, UCA members deleted all information, defaced Trigona’s websites, and shared the administration panel’s key as a parting shot. The UCA also pledged to release the decryption keys, if found among the exfiltrated data.
They recovered three backups containing hundreds of gigabytes of data, likely stolen, marking a significant setback for Trigona. All of Trigona ransomware's websites and services remain offline, painting a bleak picture for the ransomware gang while signifying a decisive victory in the battle against cyber criminality.
tags
Author

Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks