How to Protect Against Threats Abusing File Sharing Protocols
Whenever you have a network of computers, you’ll always want to transfer files between them. This process is called “file sharing,” and all operating systems have built-in services that enable it. While there’s obviously more than one of these network communication protocols, one of the most popular is SMB (Server Message Block).
The SMB protocol provides shared access to files, printers, and serial ports between computers sharing the same network. For example, if you wanted to copy a file from a network location or print a document on a network printer, the SMB protocol can help you achieve that.
While originally developed for use within local networks, it was extended to work on subnets across the internet, effectively allowing users to access files stored anywhere in the world. Over time, various updates were brought to the protocol, and it’s currently at version 3.1.1.
Because SMB was built into the Windows operating system and enabled by default, threat actors actively used the protocol to smuggle malware onto victim machines. The most notorious example of an SMB vulnerability abused by hackers is the WannaCry ransomware outbreak in May 2017, where more than 200,000 computers across 150 countries were infected.
While Microsoft quickly issued a patch that fixed the vulnerability in the affected SMB protocol (SMBv1), it also disabled the communication protocol from Windows 10. Of course, as it is with most security updates, not everyone around the world instantly installed it, and many still haven’t.
Of course, this is not the only way hackers abuse the SMB protocol. This is why Bitdefender introduced a new technology called Network Threat Prevention that’s built-into Bitdefender 2019, specifically designed to tackle threats abusing SMB, and more.
What is File Sharing?
File sharing is a means for making a computer file available to other network users. Everything from documents and pictures to applications and multimedia files can be made available from one computer to many clients. Of course, access to those files can also be restricted only to specific individuals or unrestricted for all.
Imagine a desk in your home that all family members share. If, for example, your dad wants everyone to check out the latest family picture, he’ll simply leave it on the desk for everyone to grab. However, if he has work files around, he’ll probably keep them in a locked drawer that only he and your mom have a key too.
Network file sharing is similar, in the sense that someone that has a file choses with whom to share it and under what circumstances.
The internet is basically a huge network and plenty of file sharing protocols, such as SMB and FTP, exist to allow applications and users to access and download files from any location around the world.
One of the first network file sharing protocols is the SMB protocol, which is still being used, although it went through several versions and enhancements.
How Hackers Abuse the SMB Protocol
Naturally, threat actors have become increasingly interested in abusing the SMB protocol as it allows them to easily place commands within tampered documents that automatically instruct victims to download files via the SMB protocol from attacker-controlled servers. If you thought that opening a document you received as an email attachment is harmless, think again.
For example, one of the most popular ways of infecting victims is through spearphishing emails that contain rigged attachments. Once opened, those attachments contain instructions to automatically and covertly download a file onto the victim’s computer.
Hackers will often abuse the SMB protocol to download executable files in critical locations. The most popular ones are “AppData\Local\Temp” and “\System32\” as average users will rarely check the contents of those folders, and those that do would be discouraged from removing or deleting any files stored there for fear of corrupting the operating system and causing irreparable damage.
One reason hackers still abuse the SMB protocol is that it’s a command line tool. Basically, there’s no user interface, just commands executed in the background. From a user perspective, you won’t see any commands being typed in a command line window. However, those commands will be executed in a flash.
Other attacks that abuse the SMB protocol involve rigging PDF documents to automatically leak the victim’s Windows password (hashed, not plain-text password) to attackers. This attack doesn’t involve exploiting a vulnerability in the protocol, but rather a legitimate feature that hackers abuse. We’ve covered similar examples of attacks that involved the loss of personal information in a previous article, except it’s worth noting that the SMB protocol can be abused as well to lead to credential theft.
Where Does Bitdefender Step In?
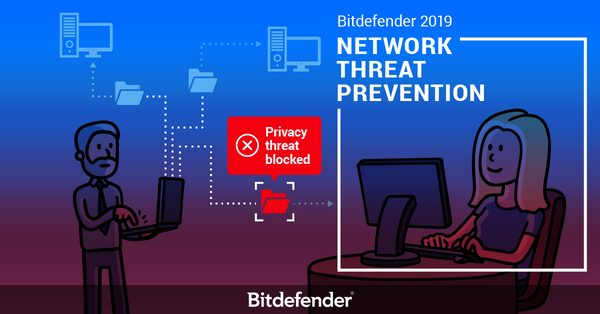
Bitdefender 2019 has introduced a new Network Threat Prevention technology that can tell whether the SMB protocol is being abused to download malicious executable files in restricted locations. Since most of these malicious files involve exploiting some vulnerability to compromise your privacy, the message displayed by our Network Threat Prevention technology will be “Privacy threat blocked”, followed by a more detailed description of the blocked threat, such as “An attempt to access a system location was made by a suspicious executable file: . We blocked the access to prevent the file from altering critical system data.”
The new Network Threat Prevention technology protects against a wide range of online threats to keep your data and your privacy secure. For more information about the capabilities or this new technology, check out some of our previous materials.
tags
Author

Bogdan is living his second childhood at Bitdefender as director of threat research.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









