Man charged with Ubiquiti data breach and extortion was employee assigned to investigate hack
A former employee of Ubiquiti Networks has been arrested and charged in connection with a hack that stole gigabytes of data and attempted to extort US $2 million from the firm.
36-year-old Nickolas Sharp, of Portland, Oregon, who was employed by networking manufacturer Ubiquiti as a software engineer in its cloud division between August 2018 and March 2021, is accused of stealing gigabytes of confidential data from the firm's AWS servers and GitHub repositories in December 2020.
The first the world knew of the security breach was in January 2021, when Ubiquiti advised users to change their account passwords and enable two-factor authentication (2FA).
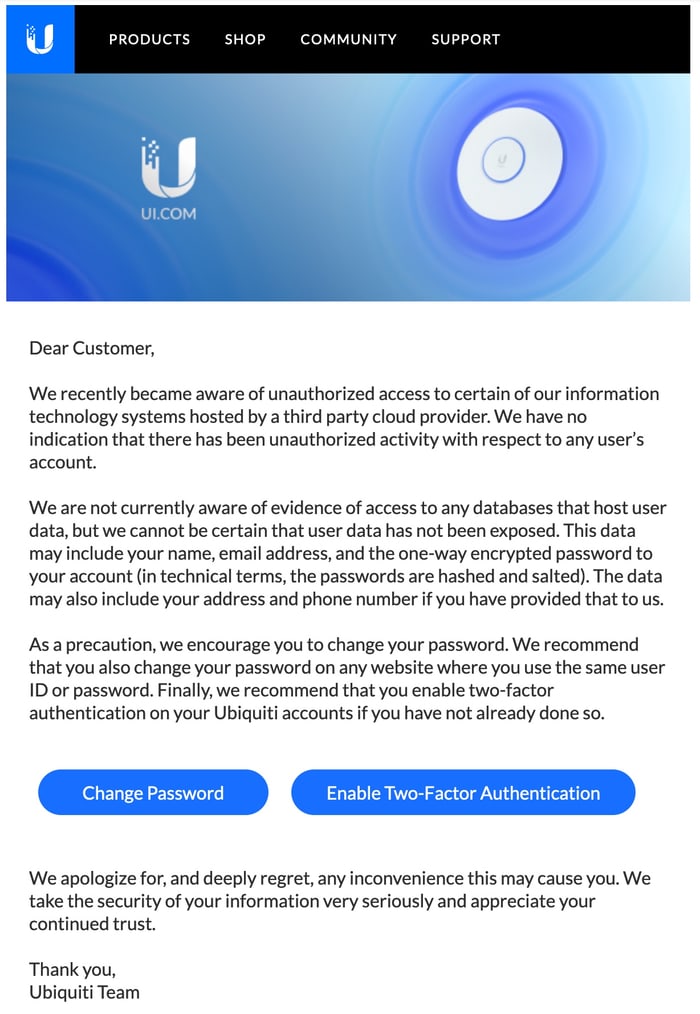
According to an unsealed Department of Justice indictment against Sharp, the software engineer is said to have used a Surfshark VPN account to hide his IP address when logging into Ubiquiti's AWS and GitHib accounts in order to steal confidential data.
After the breach, Sharp is said to have posed as an anonymous hacker, demanding a ransom of 50 Bitcoin (approximately worth US $1.9 million at the time) in exchange for the return of the stolen data and details of the vulnerability he allegedly claimed to have exploited to access the company's systems.
When Ubiquiti refused to pay the ransom, Sharp is alleged to have published a portion of the stolen files online, and attempted to damage the firm's reputation by contacting the media posing as a whistleblower, maligning its security and causing the business's share price to fall 20% - a loss in market capitalisation of over US $4 billion.
In short, the US Department of Justice claims that:
- Sharp took advantage of his privileged access as an employee of Ubiquiti to steal gigabytes of data, and delete logs that could have exposed his identity in a subsequent investigation.
- Sharp posed as an anonymous hacker to demand a ransom worth almost US $2 million be paid.
- Sharp anonymously contacted media outlets with damaging news stories about how Ubiquiti had handled the data breach, claiming a vulnerability was present in its systems.
In perhaps the ultimate irony, Sharp was assigned to the company's incident response team investigating the hack - Ubiquiti clearly unaware at the time of his alleged involvement.
According to the FBI, for "one fleeting instance" during the exfiltration of data in the dead of the night, Sharp's Surfshark VPN failed to properly mask his activity after an internet outage at his home and his real IP address was logged.
In March 2020, FBI agents duly executed a search warrant at Sharp's home, seizing computer equipment for digital forensic analysis.
Sharp faces charges of hacking, extortion, wirefraud, and lying to an FBI officer. If found guilty, he could face up to 37 years in prison.
All companies would be wise to remember that perhaps the biggest threat of all does not come from external hackers, but from the staff you have employed and trusted to operate your computer systems and interact with your data.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








