Fake Ransomware Campaign Targets WordPress Site Owners with Scary Ransom Note
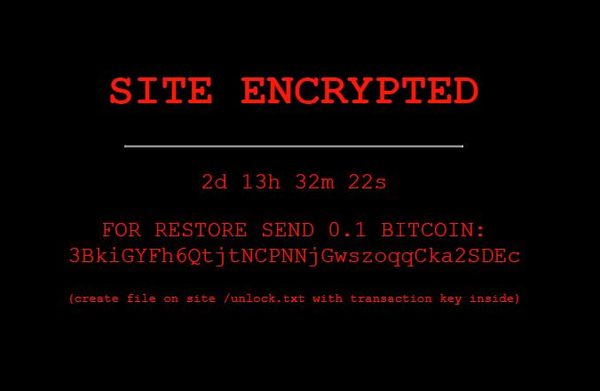
Researchers have stumbled upon a new ransomware campaign that only uses scare tactics – not actual file encryption – to trick WordPress customers into believing their website has been hacked.
Since at least Nov. 12, web security researchers have identified almost 300 WordPress sites targeted by the bogus ransomware infection. Using compromised credentials, obtained either by brute-force or the black market, the attackers hacked their way into the target sites as administrators and edited key WordPress files to block site functionality and display a scary ransom note (pictured above).
While the extortion sum is certainly low compared to typical ransoms these days, it can still earn criminals a pretty penny should several site owners fall for the trick. At the time of writing this piece, 0.1 Bitcoin amounts to around $6,000. No small amount for small site owners, either.
The attackers reportedly accessed and edited HTML parts of an otherwise legitimate Wordpress plugin to make it appear as if the site had been encrypted and all content rendered inaccessible. Then they used somePHP wizardry to feed a countdown timer into the ransom note, creating a sense of urgency typical of ransomware attacks.
Fortunately, affected site owners had the sense to seek help, investigate and eventually uncover the scam. Sucuri researchers explain the bogus campaign in detail on their blog.
To keep such scams at bay, site owners are advised to:
· Review admin users on the site, remove any bogus accounts and update/change all wp-admin passwords
· Secure the wp-admin administrator page
· Change other access point passwords (database, FTP, cPanel, etc)
· Place the website behind a firewall
· Keep regular backups of site content in case the site ever suffers a real ransomware attack
On the even brighter side, at the time of writing the scammers’ digital wallet had no digital currency to its name. While cunning, the campaign seems to have had zero success duping WordPress clients.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








