Canada's 'most prolific hacker' jailed for two years

A 33-year-old man has been sentenced to two years in prison after admitting his part in a series of ransomware and malware attacks that hit more than one thousand individuals, businesses, and organisations — including three police departments.
Ottawa-based Matthew Philbert, who has been dubbed "Canada's most prolific hacker," typically launched attacks by sending malicious emails that posed as job applications, attaching a booby-trapped resume poisoned with malware.
If Philbert's intended targets made the mistake of opening the attachment their PCs would be infected by a remote access trojan horse that would allow the hacker to infiltrate computer systems and plant further malware,
Hiding his true identity with anonymous email addresses and masking his location with VPNs, Philbert gained full access over infected computers, stealing passwords, and sending emails from victims' accounts.
According to Ontario Provincial Police, Philbert didn't care whether the victims of his attacks were big or small, targeting businesses of all sizes including a private elementary school, as well as the Ronald McDonald House in Halifax which provides accommodation for parents of hospitalised children.
Audaciously, the hacker also targeted three police departments - Nishnawbe Aski Police in Thunder Bay, West Vancouver Police Department, and City of Kawartha Lakes Police Department - although none of these are thought to have lost any money.
The Royal Canadian Mounted Police, the US FBI and Europol launched a 23-month-long investigation into the cyber attacks, which culminated with Philbert's arrest at his home in Ottawa in 2021.
Ontario police discovered Philbert had $46,000 worth of Bitcoin in a cryptocurrency wallet, the apparent proceeds from four different ransomware attacks.
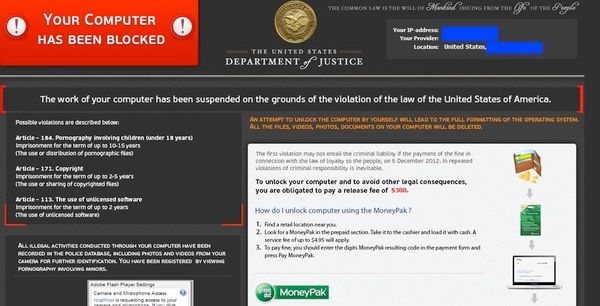
The hacker's cybercriminal activity is thought to stretch back to the 2000s, when attackers would lock up PCs and display a message claiming to come from the police saying that the computer's owner had been caught viewing child sexual abuse material. These rudimentary versions of ransomware would demand a "fine" be paid to unlock the PC and make police turn a blind eye.
Philbert pleaded guilty to fraud, unauthorized use of a computer, possessing/trafficking in computer passwords, and mischief to computer data in November 2023.
Sentencing Philbert this week, Justice Marlyse Dumel told the hacker that his crimes warranted two years behind bars because of the impact his crimes had caused.
The theft of $15,000 from one family-run business, for instance, was said to have caused significant disruption for its owners, who believed that a staff member could have stolen the money.
In March the court will meet again to discuss how Philbert will make restitution to his victims.
US law enforcement officers have also brought charges against Philbert, claiming that in 2018 he targeted computers in an ultimately unsuccessful ransomware attack at an Alaska-based healthcare organisation.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








