ASVEL basketball club slam dunked by NoEscape ransomware gang, data stolen

A high profile French basketball team has fallen victim to the NoEscape ransomware-as-a-service group, who claim to have stolen 32 GB of data including sensitive personal information about the club's star players.
Lyon-based ASVEL, owned by former NBA star Tony Parker, has issued a press release confirming rumours that spread earlier this month that it had been hacked.
ASVEL says that the first it knew of a potential security breach was on October 12 when it was approached by members of the press who had spotted references to a hack of the basketball club on NoEscape's dark web leak site.
We have 32GB of data such as:
Players' personal data!
Passports and ID cards!
Finance, taxes, insurance, budget, banking. legal documents, reports, confidential letters!
Contracts for searching for players as well as confidential agreements and contracts, NDA!
Client documents and letters, as well as tens of thousands of other confidential and important documents stolen from your servers and PCs.
NoEscape is threatening to publish the stolen data unless ASVEL is prepared to negotiate a ransom payment. The cybercriminal group says that it has emailed instructions to the club about how negotiations can begin:
We advise the LDLC ASVEL management to make the right decision and contact us. Otherwise, if you do not contact us, all data will be published and the storm of problems that will await you will be destructive!!! Letters with instructions have been sent to your corporate emails, use them and we will help you solve this problem. Assign a person to the position of negotiator, and tell him to contact us, we will explain everything and help you solve this problem. Time is running out.
ASVEL, which has brought in third-party experts to help with its response to the ttack, says that its club activities have not been disrupted, and that - so far - it has not seen evidence that fans' payment information has been compromised.
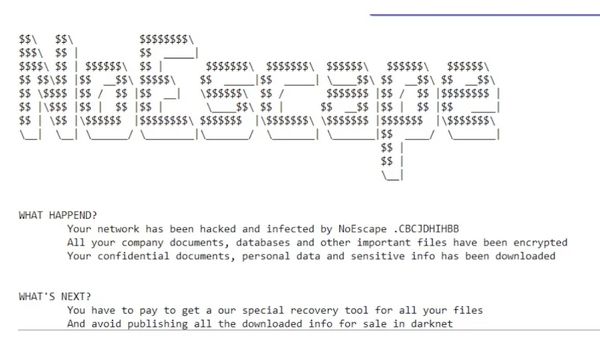
The NoEscape ransomware first appeared in May 2023. It is generally believed to be a successor to the Avaddon ransomware group that was disbanded in 2021, and has recently been in the news after warnings were issued about the gang's targeting of the healthcare sector.
The NoEscape ransomware group appears to not be keen on targeting organisations based in former Soviet countries, offering a free decryptor if companies within Russia's sphere of influence are breached. One imagines that the operators of the ransomware have adopted this policy in an attempt to reduce the chances that they will find themselves at odds with local law enforcement agencies.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








