400 Malicious Apps Disguised as Photo Editors, Utilities and Games Cut from iOS, Android App Stores
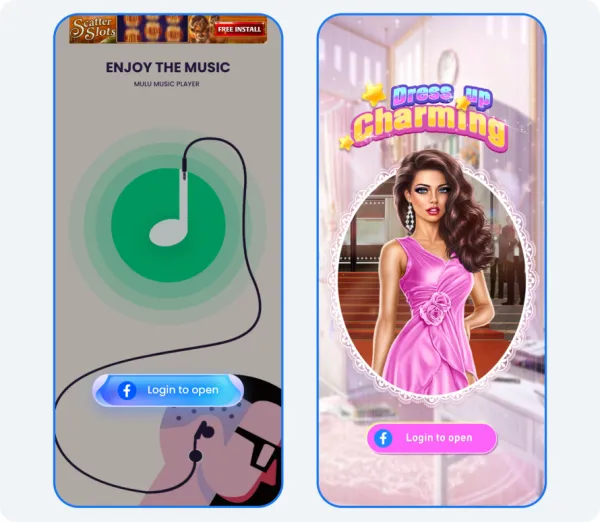
Researchers at Meta have identified hundreds of malicious apps posing as photo editors, games, VPNs, business apps and other utilities that were actually crafted to steal credentials from unsuspecting users.
“Our security researchers have found more than 400 malicious Android and iOS apps this year that were designed to steal Facebook login information and compromise people’s accounts,” Meta reveals in a post on its news blog.
A breakdown per category reveals that most of the apps, listed on the official Google Play Store and Apple’s App Store, purported to be photo editors (42.6%), followed by business utilities (15.4%), phone utilities (14.1%), games (11.7%), VPNs (11.7%), and lifestyle apps (4.4%).
“This is a highly adversarial space and while our industry peers work to detect and remove malicious software, some of these apps evade detection and make it onto legitimate app stores,” Facebook’s parent company states.
Meta reached out to Apple and Google to have the rogue apps removed from their app stores. According to the announcement, all apps had been taken down from both stores before the report was published.
However, many have already downloaded and used the apps, so Meta is also reaching out to people who may have unknowingly self-compromised their accounts and are helping them secure their accounts.
All of the rogue apps were designed to steal login credentials by forcing users to log in with a Facebook account.
“When a person installs the malicious app, it may ask them to ‘Login With Facebook’ before they can use its promised features,” Meta explains. “If they enter their credentials, the malware steals their username and password.”
The apps’ developers published fake positive reviews to cover up negative reviews by people who’d spotted the malicious nature of the apps.
Meta offers some examples of malicious behavior to help users differentiate them from legitimate apps. The report includes screenshots from some of the rogue apps, all showing the Login-with-Facebook prompt. According to the researchers, most apps would not let users enjoy any of their functionality unless they comply with the login request.
The report also includes the full list of apps taken down from the stores. If you believe you’ve downloaded one of the apps, it’s highly recommended that you reset your Facebook password as soon as possible, enable two-factor authentication (if you haven’t done so already), and turn on log-in alerts so you are notified if someone is trying to access your account.
iOS and Android users are also encouraged to report suspicious applications through Meta’s Data Abuse Bounty program. Threat indicators are also available in CSV, TSV, and JSON formats at https://github.com/facebook/malware-detection.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Few People Consider Themselves a Target for Cybercriminals, Bitdefender Study Shows
July 10, 2024
Uncovering IoT Vulnerabilities: Highlights from the Bitdefender - Netgear 2024 Threat Report
June 26, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








