Protecting Your Important - This Yearbook AI Challenge Comes with Evil Twin Android Apps

Challenges on social media are as old as the phenomenon of social media itself, and they seem to rapidly get out of hand and then blow over. The Cinnamon Teaspoon, the Detergent Pod, the Bird Box or the #InMyFeelings Challenges are just a few of the attempts to gain a moment of Internet glory at the expense of physical security. You probably get why we’re used to keeping a frowny eyebrow on the latest and greatest trends in social media.
Enter today’s trend, the Yearbook AI challenge – a new contender on the “viral” market that caters to people who want to know how they would look in a 1990s yearbook photo. We took a closer look at the risks users could face when trying to complete the challenge.
Key findings:
- During the investigation, our mobile security research team identified hundreds of “Evil Twin” EPIK samples in the wild that are illegally distributed
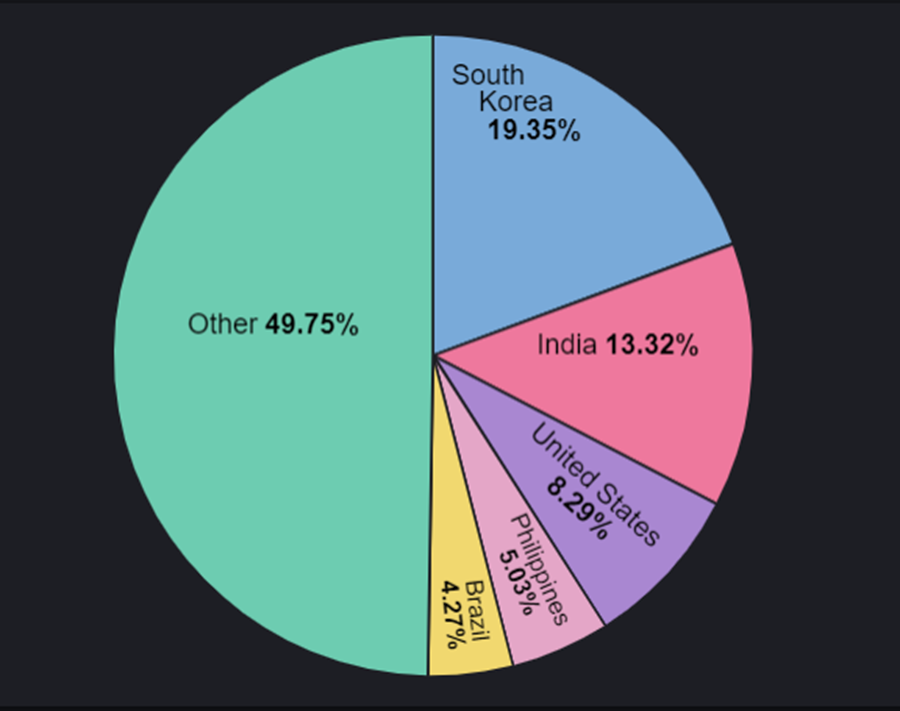
- These risky applications have been installed by users predominantly in South Korea (19.35%), India (13.32%) and the United States (8.9%)
- These applications are signed with digital certificates that have been involved in the distribution of infostealer malware in the past.
About the original app
The EPIK - AI Photo Editor is the main app people use to complete the challenge. We investigated what it does from a security standpoint and whether people expose themselves to risks when downloading and using it. The chosen platform for this analysis was Android, as it’s the most widely spread mobile operating system and it also accepts application installation from third-party sources.
Our initial research on EPIK reveals that the app does not list or ask for any permissions unrelated to its functionality and is safe to use from a security point of view.
While there is no indication that EPIK does anything it shouldn't, users should read the Terms and Conditions. One paragraph contains important information about what the company does with the collected information.
You can find these details under "PERSONAL INFORMATION WE SOLD OR DISCLOSED FOR A BUSINESS PURPOSE" in the official terms and conditions. Some of that data include your real name, alias, postal address, unique personal identifier (such as a device identifier, cookies, beacons, pixel tags, mobile ad identifiers and similar technology), phone number, email address, online activity (including browsing and search history) and more.
Evil Twin Applications
Just like any cool app, this one has gained the attention of cyber-criminals as well. Threat actors will often taint real apps, repackage them, and make them available from third-party websites. These cloned applications are called evil twins. This is more of a problem on Android, which is the only platform that allows users to sideload apps, presenting a very different set of security challenges.
Many popular apps are not free, and users must pay for the premium features. That's why the Internet is full of fake cracked apps that promise a complete experience. In reality, attackers could package dangerous malware alongside the official app.
We identified hundreds of similar EPIK samples distributed outside of official mobile markets - a dangerous and highly not recommended trend in itself. Around 20 percent of these samples were signed with a leaked certificate that has been used by a prolific cybercrime ring to install information-stealing malware in past campaigns.
Other samples were packed with np manager, which is used by threat actors in many other apps and detected by security solutions as riskware.
The map below shows the geographic distribution of victims using evil-twin versions of the EPIK – AI Photo Editor:
Conclusion
While viral treads can be a fun and engaging way to connect with others online – (at least when they don’t incite reckless behavior in the real world or personal data disclosure in the cyber-realm), they also come with several security problems.
Here are some tips to help you take part in these challenges with minimal risks:
- Make sure you understand the challenge and its potential impact on yourself and others. Do not engage in harmful or risky activities. If it does present a risk, reconsider participating, as your safety should always be a top priority. Be respectful and considerate of others – no trespassing, no bullying, no reckless attitude towards others, both online and offline.
- Never share personal information such as your full name, address, phone number, or financial details as part of a challenge. Be cautious about clicking on unfamiliar links or downloading unknown files associated with viral challenges – including mobile apps from third party sources. Scammers may use these challenges to distribute malware or phishing attacks.
- Review and adjust your privacy settings on the social platform where you'll be participating. Ensure that your personal information is appropriately protected and that only your intended audience can see your posts. If using an app, read its privacy policy to fully understand how your data will be used, processed or shared with third-party entities.
- Use a cyber-security solution such as Bitdefender Mobile Security for Android or Bitdefender Mobile Security for iOS on your devices at all times – this extra safety layer ensures that the applications you are using for the challenge are safe to use and don’t include behavior you have not signed up for.
Many thanks to Albert Endre-Lazlo for his research.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








