Coronavirus-themed Threat Reports Haven’t Flattened The Curve
With the Coronavirus pandemic still going strong, cybercriminals have continued leveraging this crisis by pushing threats designed to compromise victims’ data and security. If during mid-March we’d already seen a five-fold increase in Coronavirus-related threats, recent telemetry shows that cybercriminals have not backed down on their campaigns. If anything, the number of threats exploiting the pandemic has increased during April, as more countries became affected by SARS-CoV-2.
Bitdefender telemetry on Coronavirus-related threats between March and April reveals that Covid-19-themed threat reports are becoming the new norm, at least until the pandemic will blow over. Daily threat reports reveal that attackers seem to scale up their campaigns during the week and throttle them down over the weekends.
Global Evolution during March and April
The global daily evolution of COVID-themed threats shows consistent effort from cybercriminals and a continued interest in exploiting fear and misinformation about the global pandemic to get victims to click on malicious links, open malicious attachments, or even download and install malware.
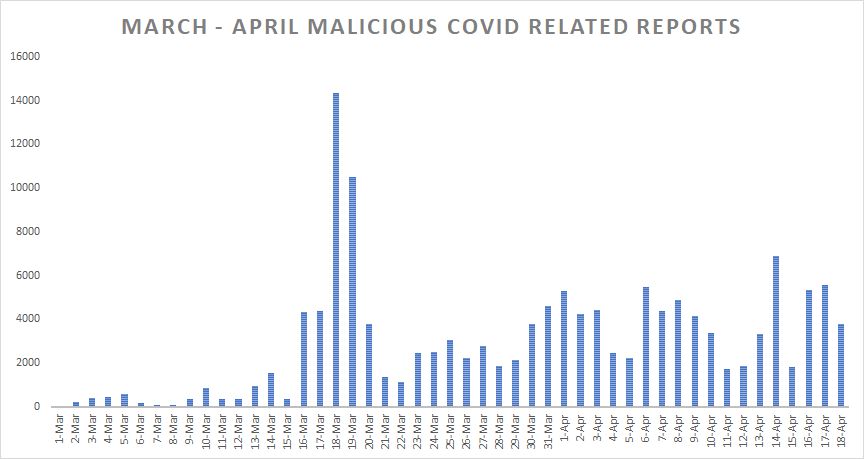
While March 18th and March 19th clearly spiked in terms Coronavirus-themed threat reports – peaking at 14350, respectively 10516 reports – there’s a certain pattern for how reports fluctuate throughout the week.
For example, during the working week there seem to be more reports, while during the weekend, especially during Saturdays, reports seem to go down. Perhaps this shows that people spend more time online during the week and choose to spend more time with the family during weekend. On the other hand, work computers are often shut down, meaning even if emails do reach inboxes during the weekend, they’re less likely to be opened. In fact, chances are they’ll be read on Mondays
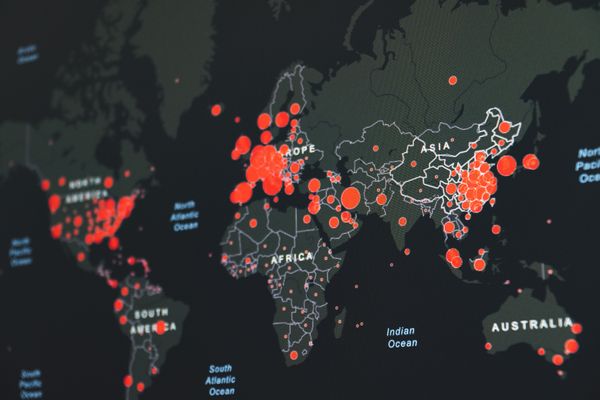
A heatmap revealing the global evolution of Coronavirus-themed reports during the entire month of March alone also reveals there’s an overlap between countries affected by the Coronavirus and those targeted by Coronavirus-themed malware.
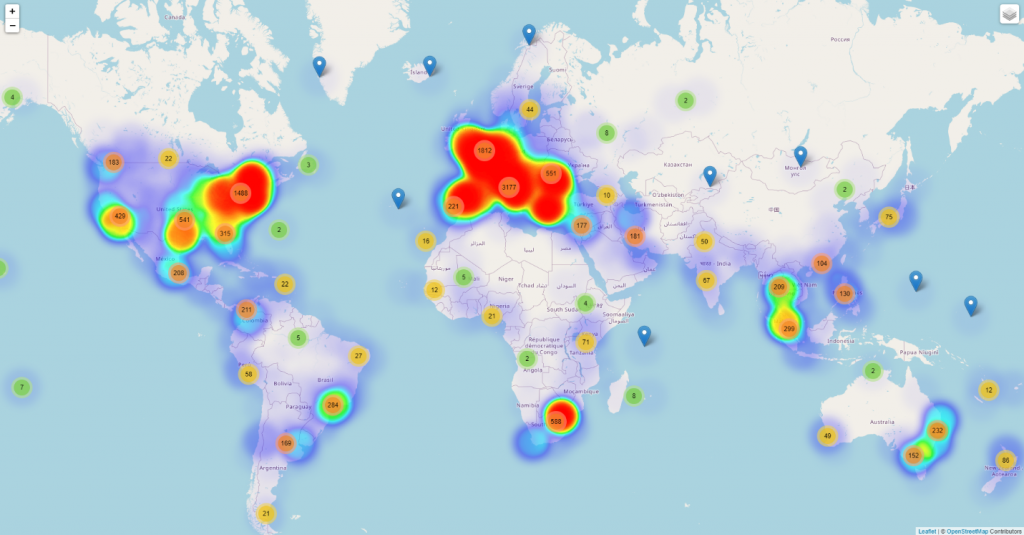
With Europe and the United States’ East Coast as primary targets, threat actors have leveraged fear, panic, and misinformation in order to get victims to click on links, open attachments, or even download malicious files.
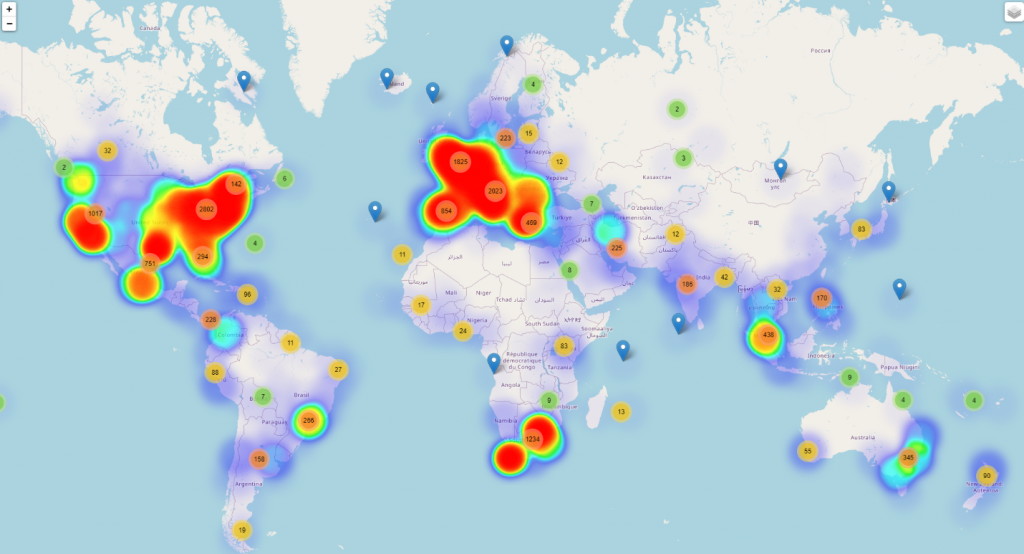
During April, the number of Coronavirus-themed malware reports seems to have intensified not just across Europe, but also across the United States and South Africa. This threat telemetry is somewhat in line with the global evolution of SARS-CoV-2, again pointing that threat actors closely monitor the evolution of the virus across the world and potentially align their campaigns in accordance, to maximize their efforts of compromising as many victims as possible.
Note: For a complete Weekly Evolution of Global Coronavirus-themed threats during March and April, CLICK HERE for a gif.
Countries Targeted by Coronavirus-themed Malware
Countries that have reported the largest number of Coronavirus-themed reports seem to have also been those hit hardest by the pandemic. For example, the top countries that reported the largest number of themed-malware reports include the United States, Italy, and the United Kingdom.
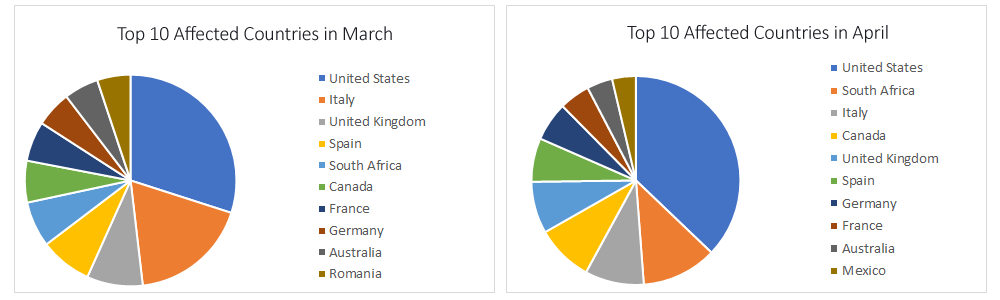
These stats are best on unique IP addresses, not number of reports, meaning that more reports could have originated from a single IP address. This is interesting as it points out that while these attacks usually have a shotgun-shell approach (in the sense that multiple campaigns can reach the same victim), attackers seem to have also tried to get to as many victims as possible when targeting these countries.
While the United Kingdom ranked fifth in April, it’s likely that threat actors focused their campaigns on countries in which the Coronavirus pandemic had started trending, hence preying on fear and misinformation to maximize their success for compromising victims.
Verticals Affected by COVID-themed Reports
The verticals hit hardest by these threats during the full month of March seem to involve Retail, Transportation, Manufacturing, Technology, and Hospitality-Leisure. While the number of attacks against Healthcare has definitely increased during the pandemic comparted to what they traditionally used to be, it cannot compete in terms of sheer numbers and volume with companies activating in Retail, Transportation, Manufacturing, or Education- verticals that are also confronted with an increase in malware related to Coronavirus.
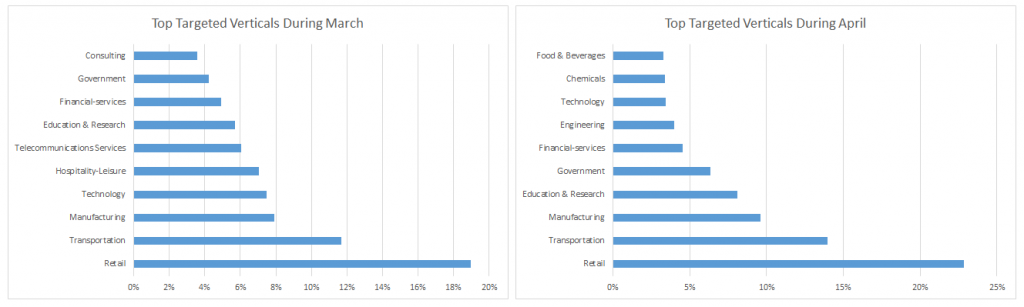
One reason why these verticals have been hit hard is the sheer number of players in these areas compared to the healthcare industry.
And since this telemetry is strictly based on Coronavirus-themed reports, it doesn’t exclude the possibility that Healthcare and other verticals may have seen an increase in other types of malware, such as ransomware.
During April, Government and Financial Services have moved up the list of targeted industries, potentially as cybercriminals realized that these institutions are also more likely to fall prey to deceptive messages as they were also interested in learning how to cope with the ongoing crisis, especially with workface restrictions in place.
Europe Evolution of Coronavirus-themed Threats
Zooming in to look at individual reports during March and April for Europe, an interesting picture emerges. With Europe in full crisis and the pandemic ripping through countries like Italy and the United Kingdom, threat actors focused their campaigns on these geographies as users were more likely to fall prey to deceptive messages.
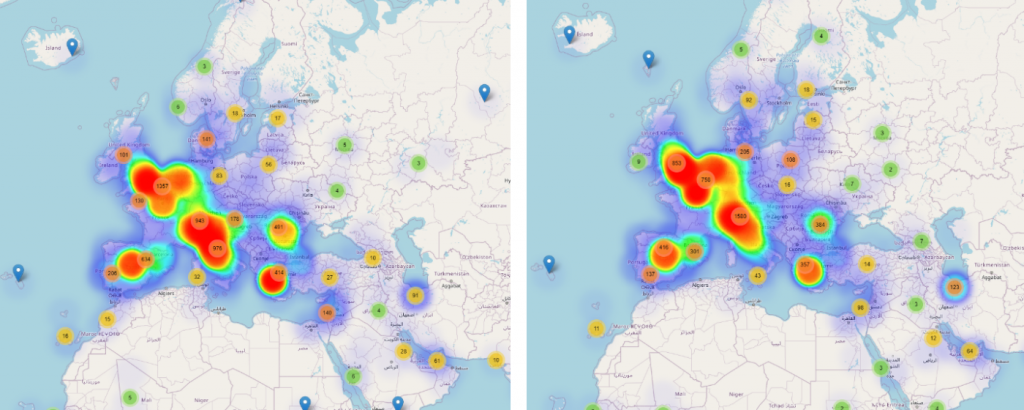
Note: For a complete Weekly Evolution of Coronavirus-themed threats in Europe during March and April, CLICK HERE for a gif.
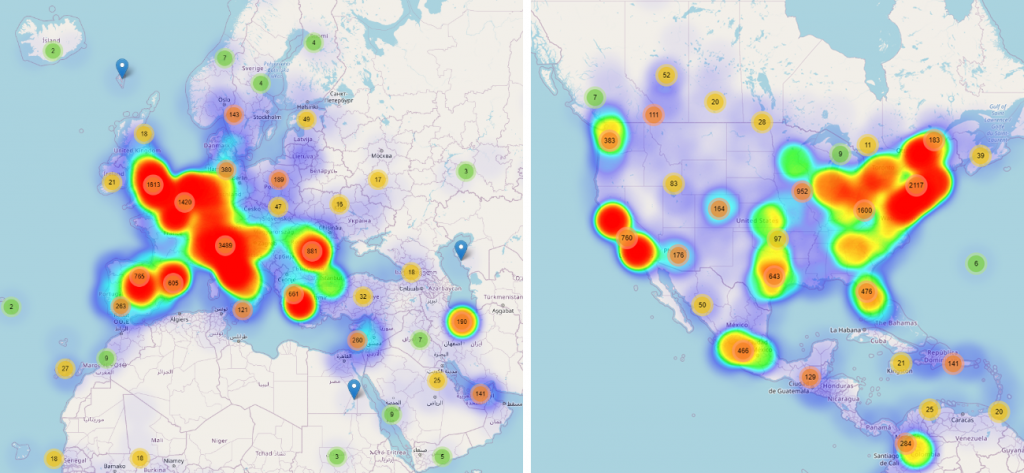
United States Evolution of Coronavirus-themed Threats
The number of reports for Coronavirus-themed threats for the United States during March and April seems to have evolved in line with the SARS-CoV-2 evolution. If during March our telemetry showed a heatmap that was partly colored, during April the number of reports has significantly increased over the East and West coast.
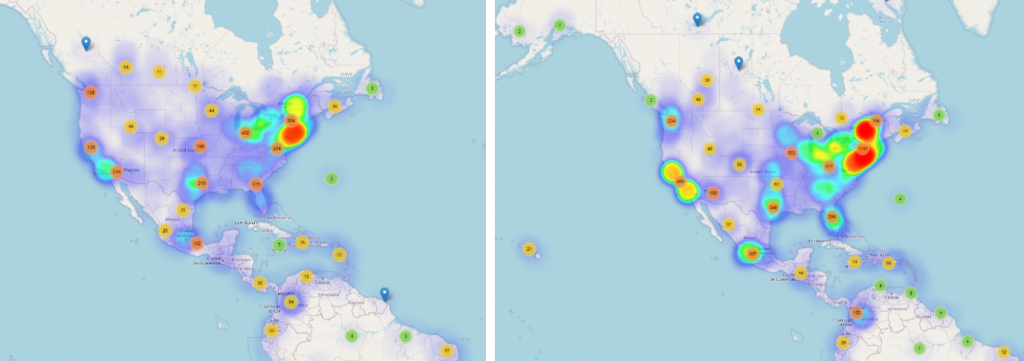
Note: For a complete Weekly Evolution of Coronavirus-themed threats in the United States during March and April, CLICK HERE for a gif.
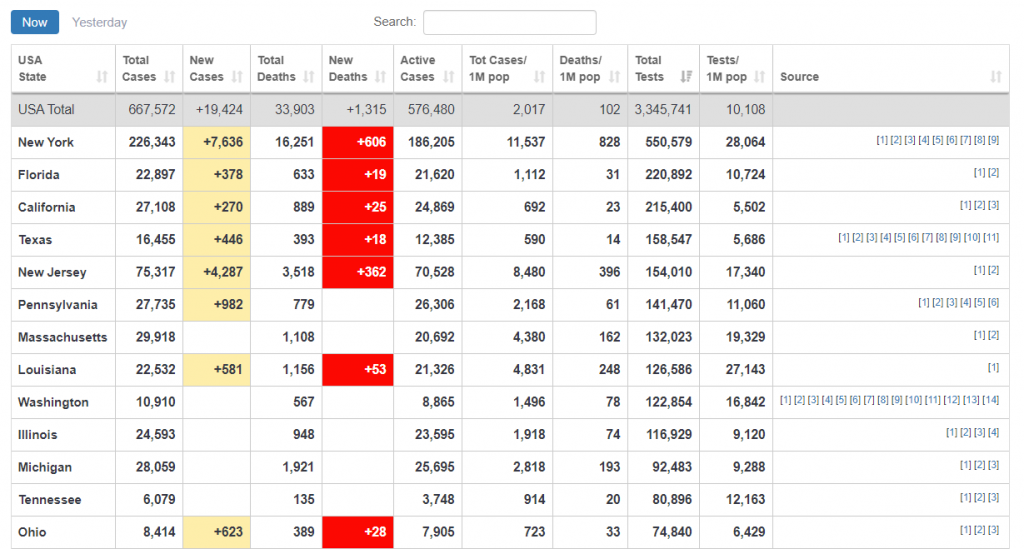
Interestingly, as April took a turn for the worst for the United States in the sense that the pandemic reached a record-high number of infections, with an alarming number of people from both the East and West Coast reporting infections, we’ve noticed an interesting correlation between the total number of new tests for each state and our coronavirus-themed malware telemetry.
Based on Bitdefender telemetry during March and April regarding Coronavirus-themed threats, the top affected US states seem to have been California, Texas, Florida, New York, and Ohio. This telemetry is based on the number of unique IP addresses that have reported such themed malware.
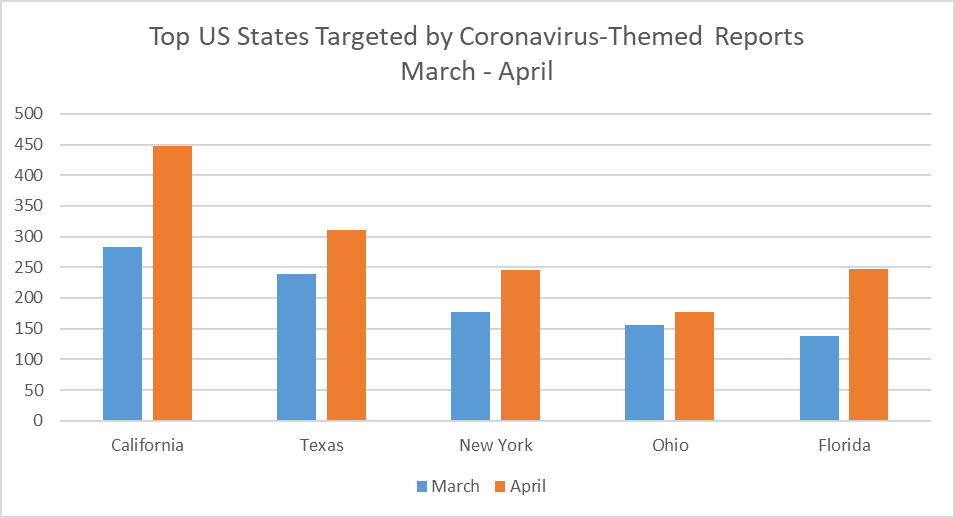
When applying this telemetry with real-world statistics about the Coronavirus, we noticed a correlation between the total number of new Coronavirus tests for each state and our coronavirus-themed malware telemetry. It may or may not be a coincidence. But we can safely infer that people who get tested are interested in learning more about potential treatments, medicine, medical best practices, and maybe even other patient’s experiences. Therefore, those spending more time online looking for information about COVID-19 are more likely to fall prey to scams and malware related to Coronavirus.
Considering that these top states also rank amongst the top states with the highest population, it’s likely that there’s a higher chance for contracting the SARS-CoV-2 infection. Therefore, as more people get tested and are more interested in learning more how to deal with the infection, they’re more likely to fall prey to scams and malware.
Receiving an email claiming to have new and interesting information about the pandemic with more exclusive information embedded within the attachment is the perfect lure. That email attachment is likely tainted, with threat actors preying on everyone’s fear in order to convince them to open it. Most of these emails usually claim to be from WHO, NATO, UNICEF, or other global legitimate organizations, according to our findings, hence making people more curious and therefore more vulnerable to these attacks.
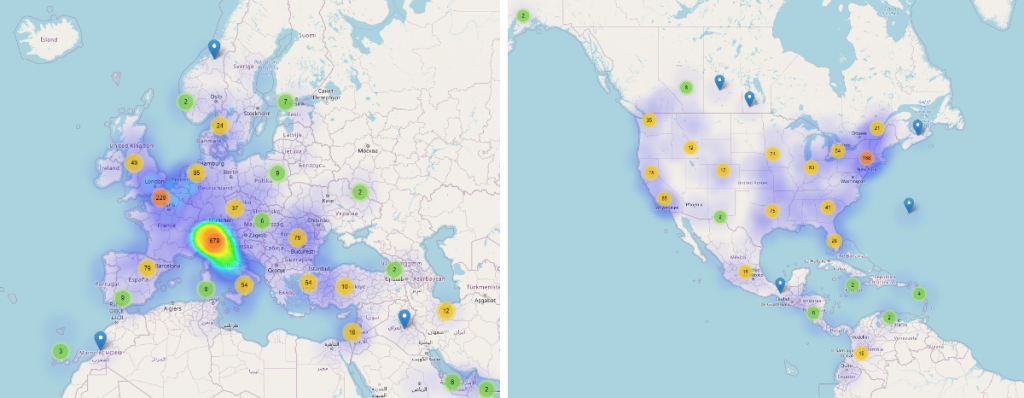
Another interesting fact is that if we are to compare the evolution of Coronavirus-themed threats between Europe and the United States on a weekly basis, US threat reports seem to evolve with a one-week delay.
For example, if during the same time interval, in Europe we can clearly see that Coronavirus-threats were hitting Italy hard, in the United States attacks seem to have been more scattered and not focused on a specific state.
The same trend seems to have applied in the following weeks, with the United States lagging behind Europe in terms of Coronavirus-themed threats, trailing about one or two weeks behind. As seen in the images below, after another week during which these threat campaigns have spread across Europe, affecting the United Kingdom and Germany, the United Sates heatmap barely starts lighting up.
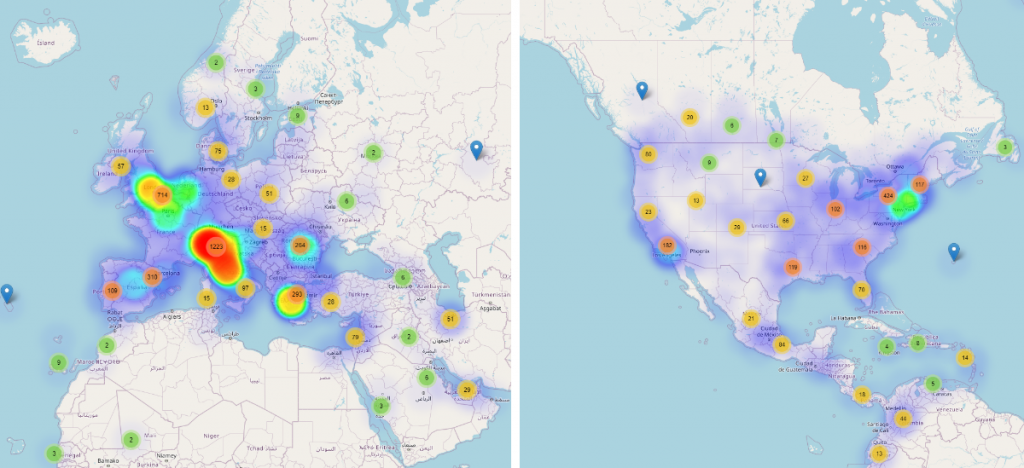
This pattern seems to apply throughout our weekly telemetry reports and potentially indicates that the United States reaction to the global pandemic was different than Europe’s, in the sense people were potentially not aware of the full risks associated with the infection, and hence less likely to seek out or read information about SARS-CoV-2. As the threat became clearer and the number of Coronavirus infections spread across the United States, it’s likely threat actors exploited that lack of information and panic to increase the success of their Coronavirus-themed threat campaigns, as they did with Europe.
By April 18th, our telemetry heatmaps for Europe and the United States seem to have aligned, in the sense that while Coronavirus-themed malware campaigns have consistently been targeting most European countries that have also been affected by the pandemic, in the United States the same hotspots that have reported the highest number of SARS-CoV-2 infections are also the ones that have been hit hardest by cybercriminals with Coronavirus-themed malware.
Asia and Australia Evolution of Coronavirus-themed Threats
Covid-19 themed threats have also impacted countries in Asia, attackers following the same global trends during March and April. For example, the number of reports have increased in April, potentially as people became more aware of the pandemic and more curious of learning more about how to protect themselves and where to seek help in case of an infection, as the pandemic reached their borders.
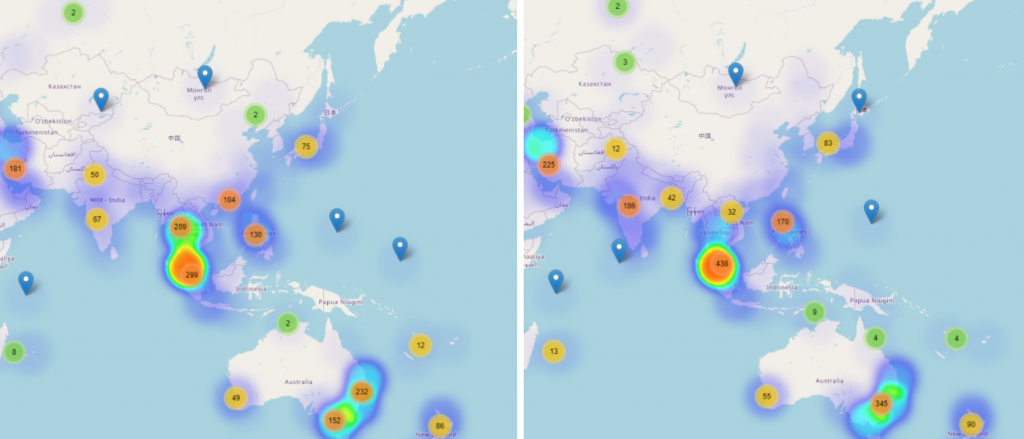
While the heatmaps may not be as dramatically different from March to April as in other regions, this could be indicative that threat actors have been focusing their efforts on regions that have traditionally been more susceptible to cyberattacks and consequently have more valuable information to lose as a result. Europe and North America are both two regions with a highly dense population, and a high purchasing power parity per capita, meaning attackers have more to gain in terms of personal and financial data by compromising users within these regions.
Final Thoughts
The SARS-CoV-2 (COVID-19) global pandemic is not going away any time soon and it’s likely that cybercriminals will continue exploiting and leveraging the crisis to their own advantage. Coronavirus-themed threats will likely continue under the form of spearphishing emails, fraudulent URLs and event malicious applications, all exploiting fear and misinformation in order to trick victims into unwillingly giving away personal, sensitive or financial information.
It’s likely these campaigns will plateau in time, but as long as the threat of infection with SARS-CoV-2 is real, cybercriminals will keep exploiting the topic, enticing victims with vaccines and miracle cures.
If staying safe from the SARS-CoV-2 infection implies social distancing and adhering to best practices in terms of personal hygiene, the same rules apply in the cyberworld. Don’t believe anything you read online and try to check the legitimacy of any information by consulting legitimate sources, always have a security solution installed on all your devices, and be sure to avoid opening attachments or clicking on links especially if they’re unsolicited or from unknown parties.
Note: This article is based on technical information provided countersy of the Bitdefender Labs teams.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













